Exploitation Level: Very Easy/Remote
DREAD Score: 7
Vulnerability: Persistent Cross-site Scripting
Patched Version: 1.10.29
Icegram is a plugin that helps you collect email addresses for your newsletter. Other features include light-box popup offers, header action bars, toast notifications, and slide-in messengers.
Versions 1.10.28.2 and lower are affected by a persistent Cross-Site Scripting in the admin area. This plugin has over 40,000 installations and any attacker with a subscriber account can leverage this vulnerability.
We are not aware of any exploit attempts currently targeting this plugin, but all of our clients behind the website firewall are already protected.
Disclosure / Response Timeline:
- June 06, 2019: Initial contact attempt.
- July 09, 2019: Patch is live.
Technical Details
Using the check_for_gallery_items function, Icegram retrieves all of its gallery data from the official site: icegram[.]com.
Once collected, part of this data is serialized and stored with the option name ig_cat_list, as described in the function save_gallery_data:
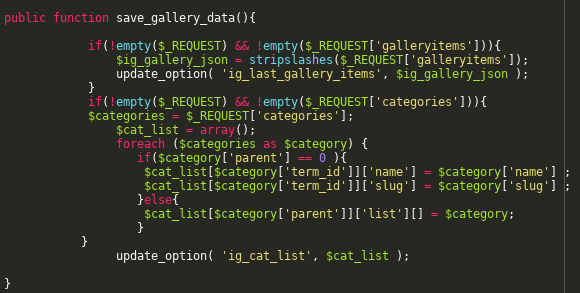
To ensure that the gallery data is fully loaded, the code allows two options to gather the information from an external resource.
When the first option fails, an AJAX function is executed making use of the already defined action “save_gallery_data”.
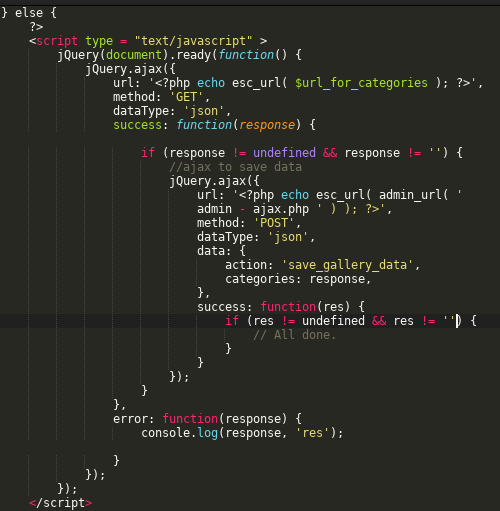 As we can see from the first picture, the function save_gallery_data lacks permission checks on plugin settings update. This allows any registered user to arbitrarily import data inside the plugin option ig_cat_list.
As we can see from the first picture, the function save_gallery_data lacks permission checks on plugin settings update. This allows any registered user to arbitrarily import data inside the plugin option ig_cat_list.
By providing an array with arbitrary data as categories, an attacker will be able to execute malicious JavaScript code in the admin area.
Update as Soon as Possible
Cross-site scripting (XSS) is a widespread vulnerability that allows an attacker to inject malicious content into a site. We’ve seen multiple malicious campaigns making use of this vulnerability for years now.
We strongly encourage Icegram users to update their plugin to version 1.10.29 as soon as possible. Users that are unable to update immediately can leverage the Sucuri Firewall (or equivalent technology) to virtually patch the vulnerability.