Update 11/03/2017:
If you want to learn how to secure WordPress, you can read all about it in our new guide.
As WordPress continues to grow in popularity, so does its library. New and experienced developers are creating themes and plugins – which creates diverse directories. While this is useful to the WordPress community, the nature of mass creation can account for coding errors and vulnerabilities. Even premium themes have security issues. We often find code that is developed with good intentions but without taking security measures into consideration. For that reason, many people often wonder if their site is hacked when they begin receiving complaints from their users.
Email Functions Within a Theme
During a routine cleanup investigation, we found an issue with a PHP script in a theme that was using mail capabilities. While many themes include email functionality, this particular one was troublesome because the script was written without any security checks or direct access prevention. Without the proper security functions in place, this script can easily be exploited to abuse features and send mass email spam.
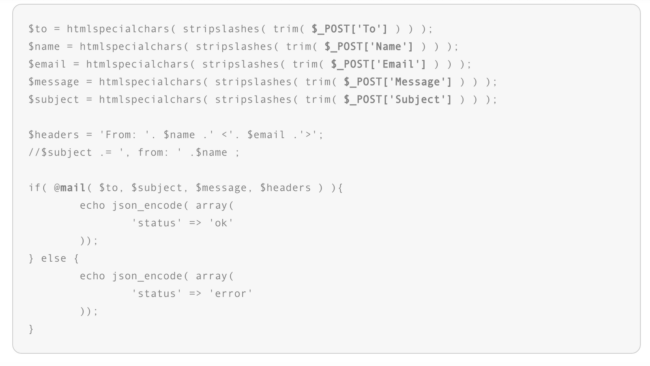
This script we identified is part of a premium WordPress theme. Here is a snippet of it (with comments removed):
As you can see, it sends emails using the data provided in POST parameters. Although it is meant to work as a part of the theme, it can also easily be used as a stand-alone script, bypassing all security checks made in other theme files.
Same Vulnerability, Multiple Themes
Upon further investigation, we discovered that attackers have been exploiting this issue under the radar for quite a while. The lack of security checks in that particular file allows the attackers to send as many emails as they would like, only limited by the server’s configurations.
As we had feared, the code was not used exclusively in one theme. We found this script throughout different themes developed by the same company.
The issue (located within the file functions/theme-mail.php) can be found in old versions of the following premium themes:
- bretheon
- doover
- fingerprints
- kora
- lawcenter_two
- mfl
- pindol
- tisson
- almet
- caffeine
- nollie
- limuso
The consequences of using those old versions vary from having your website suspended by the hosting company or getting the mail server blacklisted.
Preventing Direct Access to Files
If you identify the snippet above within your theme, we highly recommend adding the following code after your opening PHP tags to prevent direct access to the file and further exploitation.
if ( basename($_SERVER['PHP_SELF']) == basename(_FILE_) )
{
die('Access Denied');
}If you develop themes or plugins and they include files that shouldn’t be used outside of the original theme or plugin, consider using this trick to prevent direct access to the files.
Protect Your Site From Poor Coding
This post demonstrates just one of many security issues caused by poor coding practices. Extension developers should always remember that if their software becomes even moderately popular, hackers will immediately start looking for ways to abuse it. WordPress users should also keep these issues in mind and employ preventative measures such as a Web Application Firewall (WAF).
If you’re a customer using the Sucuri Firewall, you are already patched via our virtual patching engine. If you think that your site may be hacked, check out our guide on fixing hacked WordPress and, as always, please reach out directly to our team!