During a recent investigation, we found an infected website was redirecting to YouTube after its main index.php file had been modified to include the following line of HTML:
<meta http-equiv='refresh' content='2;url=https://youtu.be/fsqzjDAO2Ug'>
This technique works because it’s possible to use HTML within .php files — as long as the HTML is outside the PHP code tags.
In this case, the HTML is the only code that exists, so there are no PHP tags to avoid.
What’s interesting is that this redirect goes to a YouTube video of a person playing a guitar, but if you view the channel page that hosts the video then you can see that it is operated by an Indonesian “defacer”.
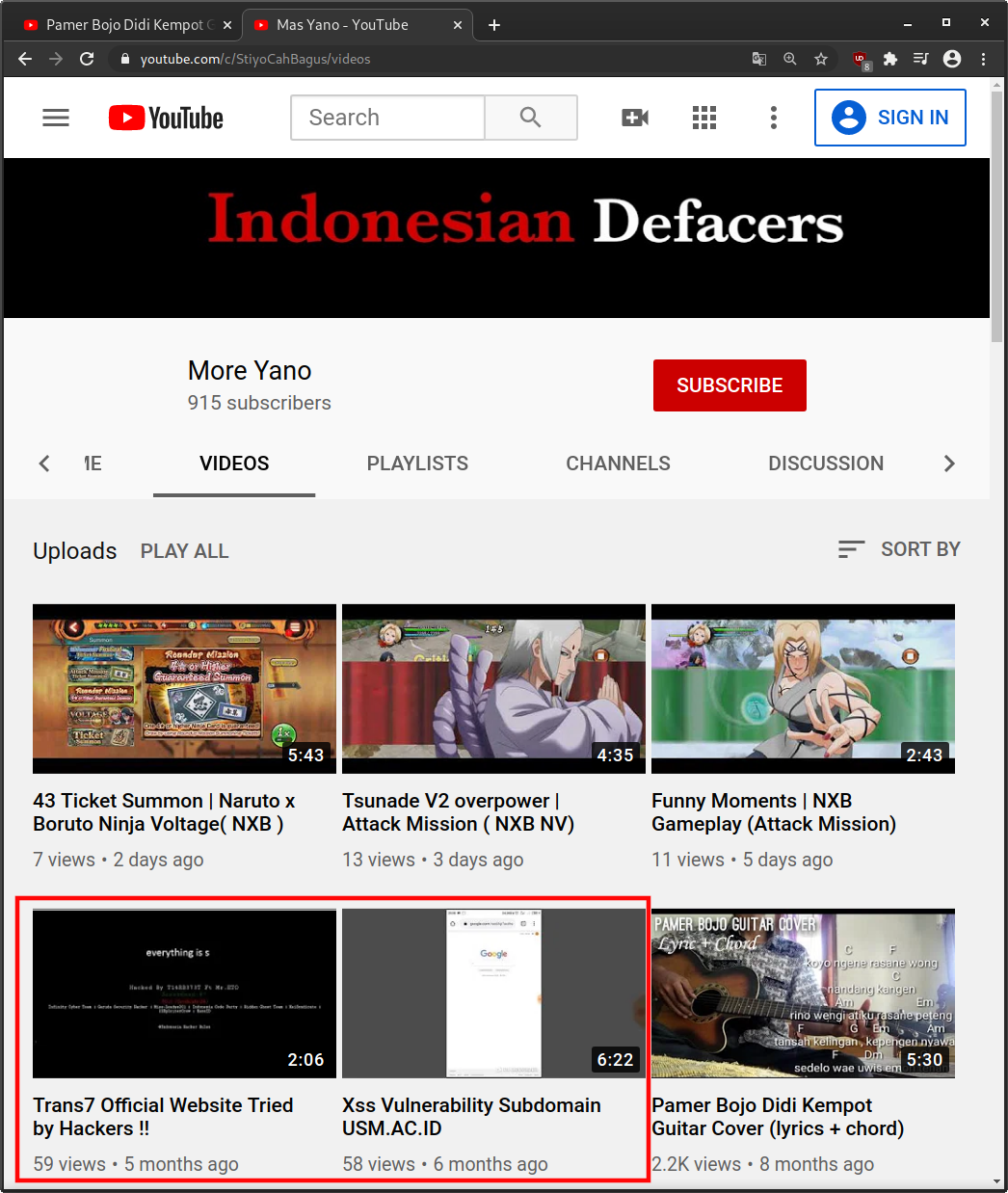
It’s also unusual for an attacker to use their personal YouTube video channel as a form of malicious redirect. The channel itself has 41 videos that go back over 2 years, so it seems silly for them to expose their own YouTube account this way.
Scripts that execute malicious redirects can exist anywhere on a website — from infected databases to third-party scripts. The best way to mitigate risk, detect malicious behavior, and prevent website blacklisting is to leverage a website security monitoring service.









