There’s no one specific topic or target or audience when it comes to website security. But when you clean enough hacked websites, you start to see trends and techniques emerge in the landscape.
In my last presentation at WordCamp Europe, I dove into the latest findings from our threat report to highlight the major themes and key takeaways for compromised websites. You can watch the recording below.
Too Long; Didn’t Watch
For those looking for a quick recap of my presentation, I’ll lay it all out for ya here.
Outdated Plugins & CMS
In 2021, we saw that plug-ins and extensions accounted for far more compromises than outdated core CMS did. The shift has been gradual, but when we review the breakdown over half of websites were out-of-date at the time of cleanup. This means that a large chunk of websites were maintaining their CMS with the latest security patches and updates but still found themselves infected with malware.
Let’s briefly consider the comparison across different platforms.
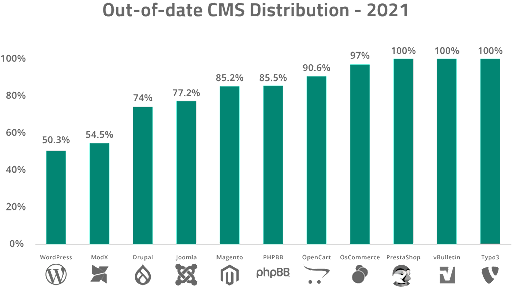
For vBulletin, nearly every single installation was out-of-date at the point of infection. On the other hand, 50% of WordPress installations were found to have an updated core version.
While our intuition might have us believe that keeping core CMS updated will help mitigate risk for a website, the truth is that it’s just as important to keep plugins, extensions and other third party software up-to-date — outdated components were found to be responsible for a large percentage of hacks in 2021.
Agencies or web professionals who manage older websites in shared environments are especially vulnerable to attacks that target outdated software. These might include clients who are reluctant to update or patch for fear of breaking their site, or maybe maintain old, customized legacy code on their site.
For example — Tim Thumb was ranked #2 in our top 10 vulnerable plugins for 2021 but happens to be a vulnerability that our research team has been tracking for over 10 years, highlighting the number of websites that continue to use vulnerable software.
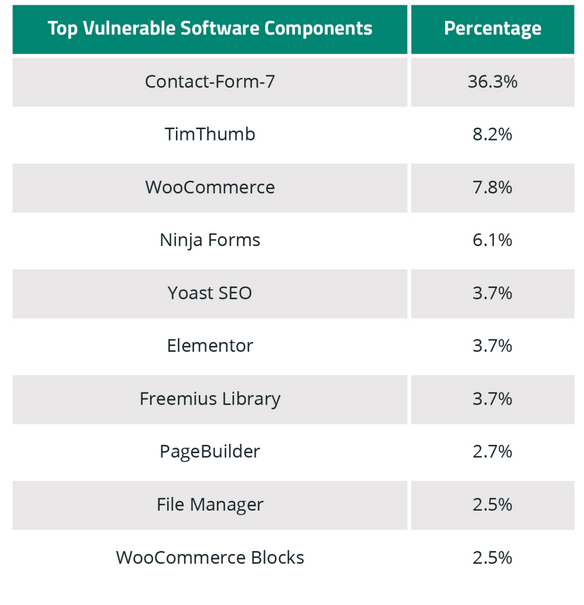
Attackers look for the widest net to target the largest volume of sites possible. So if you’re using an extremely popular plugin or theme and are using an insecure version of the software, you’re much more likely to be targeted in an automated attack that seeks to exploit that particular vulnerability.
To mitigate risk, you’ll want to ensure that all software used on your website is up to date, and not only your core CMS. That includes server, PHP versions, third party plugins, etc. Also consider isolating well maintained websites from those who are reluctant to patch to avoid issues with cross-contamination in shared server environments.
Key Takeaways
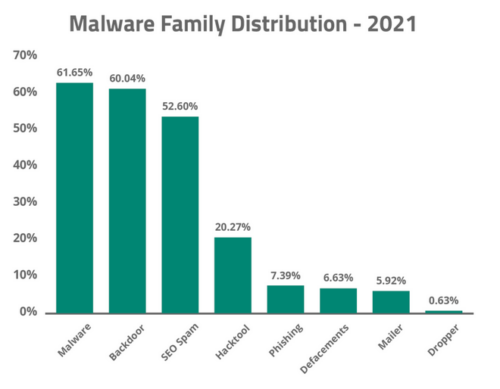
Hacktools have become increasingly popular with attackers. In fact, a fifth of all websites were found to contain at least one hacktool at the point of infection — and the number of hacktools found on hacked sites has doubled in the past two years.
Some of these tools include features that make it easy for the attacker to create mass defacements, DDoS attacks, create and manage botnets, or even mine for cryptocurrency.
One of the most common hacktools found on client sites was AnonymousFox, which is an especially significant threat to WordPress websites that use cPanel — but the infection can impact any CMS. Its suite of automated tools is used to target victim’s websites and is packed with features that make it easy to identify victims, hack the environment, and exploit resources.
To summarize what an attack sequence with AnonymousFox usually looks like — attackers leverage the tool to identify a target, exploit a known vulnerability, upload a malicious web shell, modify the cPanel credentials, send a password reset and obtain unauthorized access. They might even add in a handful of secondary accounts for their use, just in case. And once a foothold has been established, they’ll upload a fake malicious plugin or two which may contain credit card skimmers or spam mailer scripts.
In these cases, visibility is key. We strongly encourage webmasters to employ website monitoring and detection services to help identify any indicators of compromise and suspicious changes on a website.
Credit card skimmers fall under the Malware category and are essentially scripts used to steal or “skim” sensitive credit card information from e-commerce websites — and in 2021 we saw more and more exploit kits running on compromised WordPress websites.
Since most attacks are financially driven, the trends that we see are for attacks that are most profitable for bad actors. Regardless of whether the attack is for a fake ransomware threat, credit card skimmer, or SEO spam — you’ll be sure the attacker is working hard to get the most ROI for their malware campaign.
With a market share as large as WordPress’, it’s not surprising that credit card skimming malware has seen an uptick for this CMS. Data seen from our SiteCheck remote scanner revealed that skimmers have become increasingly prevalent in WordPress environments. WooCommerce has a ~40% plurality of market share in ecommerce platforms, so it was really only a matter of time before attackers shifted their focus to it.
2021 Summary & Forecast for 2022
Here’s a recap of the summary from 2021.
- The Log4J vulnerability was easily one of the most serious vulnerabilities affecting a large majority of the web in 2021. This critical server vulnerability impacted any website, application, or hardware device using the software. Server administrators all over the world scrambled to identify and patch affected or potentially vulnerable systems before the attackers were able to compromise them.
- Vulnerable plugins and extensions accounted for far more website compromises than out-of-date, core CMS files.
- Default configurations of popular website software applications remain a serious liability.
- Credit card skimming is on the rise!
- Backdoors and malicious admin users remain the backbone of many compromises. Backdoors were extremely common, with 60.04% of infected environments containing at least one website backdoor.
The forecast for 2022 is all about financial gain. We expect attackers to spend more time crafting malware for ecommerce environments — and they’re likely to include more complex features, obfuscation techniques, and other functionalities to evade detection.
Since attackers have more to gain financially from a credit card skimmer than other types of infections, we expect this to be the focal point in 2022 and beyond. And the longer an attacker’s skimmer is able to hide, the more they can harvest from the compromised environment.
Unless major changes are made to the default security configurations for popular CMS’ — for example, multi-factor authentication enabled by default in for WordPress or no default administrator URL enabled for Magento 2 — we expect unprotected admin pages will continue to be a primary attack vector.
If you’re interested in the latest data and trends, check out our SiteCheck Q2 report which analyzes the most prevalent malware infections, blacklisting, injections, and trending malware campaigns seen with our remote scanner in the past quarter.