On December 6th, 2023, the WordPress plugin Backup Migration received a critical security patch for a remote code execution vulnerability. Details were released five days later after users were given an opportunity to install the patch, although the official CVE is still locked down in “reserved” mode.
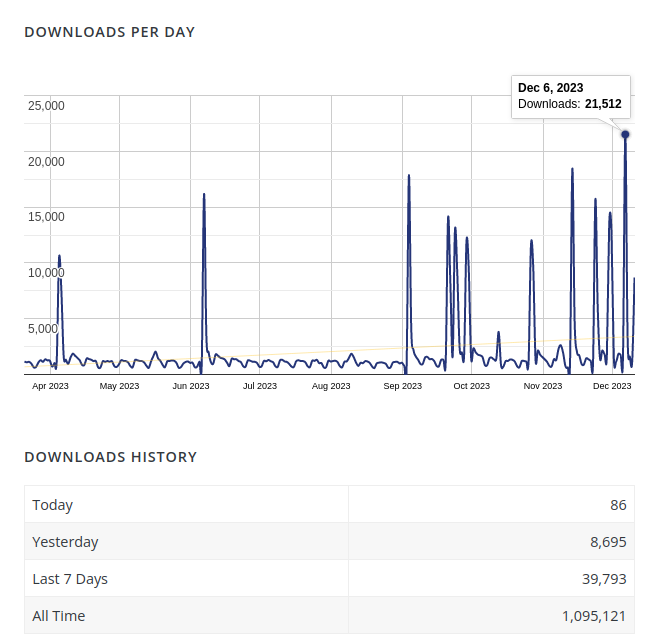
Website administrators are advised to update to the most recent version 1.3.8 which contains several crucial security improvements. The vulnerability is ranked as 9.8 on the CVSS scale, so it’s about as bad as you can get. The plugin is in use by some 90,000 websites. Download statistics from the WordPress repository indicate that some 30-40,000 website owners have downloaded the patch, meaning that over half of the websites with this plugin installed are still vulnerable.
Clients using the Sucuri Firewall are patched and virtually protected against this vulnerability.
Vulnerability details
The vulnerable code within this plugin contained a remote code execution vulnerability which allowed unauthenticated attackers to execute arbitrary code on the victim server. It allows for complete website takeover with very little difficulty from the attackers.
In line 118 of the Backup Migration plugin file ‘/includes/backup-heart.php’, the script attempts to include and evaluate another file bypasser.php from the BMI_INCLUDES directory.
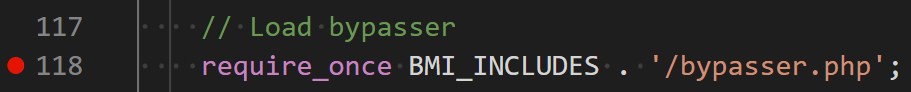
The BMI_INCLUDES constant is defined in line 64 by the combination of BMI_ROOT_DIR, and the word ‘includes’.
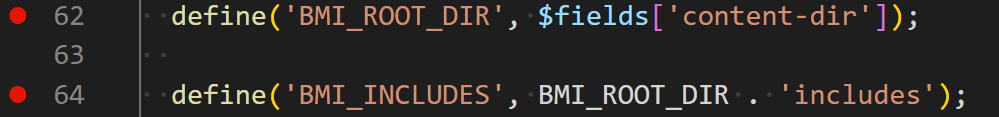
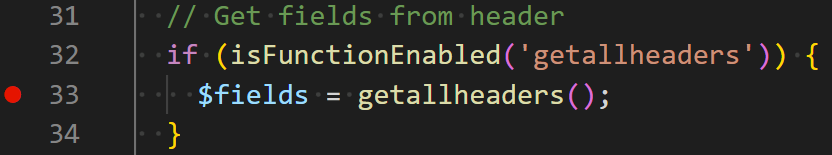
It’s important to note that the value of BMI_ROOT_DIR is defined by an HTTP header named content-dir (Line 62), which is a value controlled by the user.
The issue was reported to WordFence in their new bug bounty program by a seemingly new group known as Nex Team.
The plugin developers at BackupBliss acted quickly and released a patch within hours, and roughly a week was given to website owners to install the patch before the vulnerability details were made public.
Patch details
In comparing the old and new versions of the vulnerable file we can see how it was addressed:
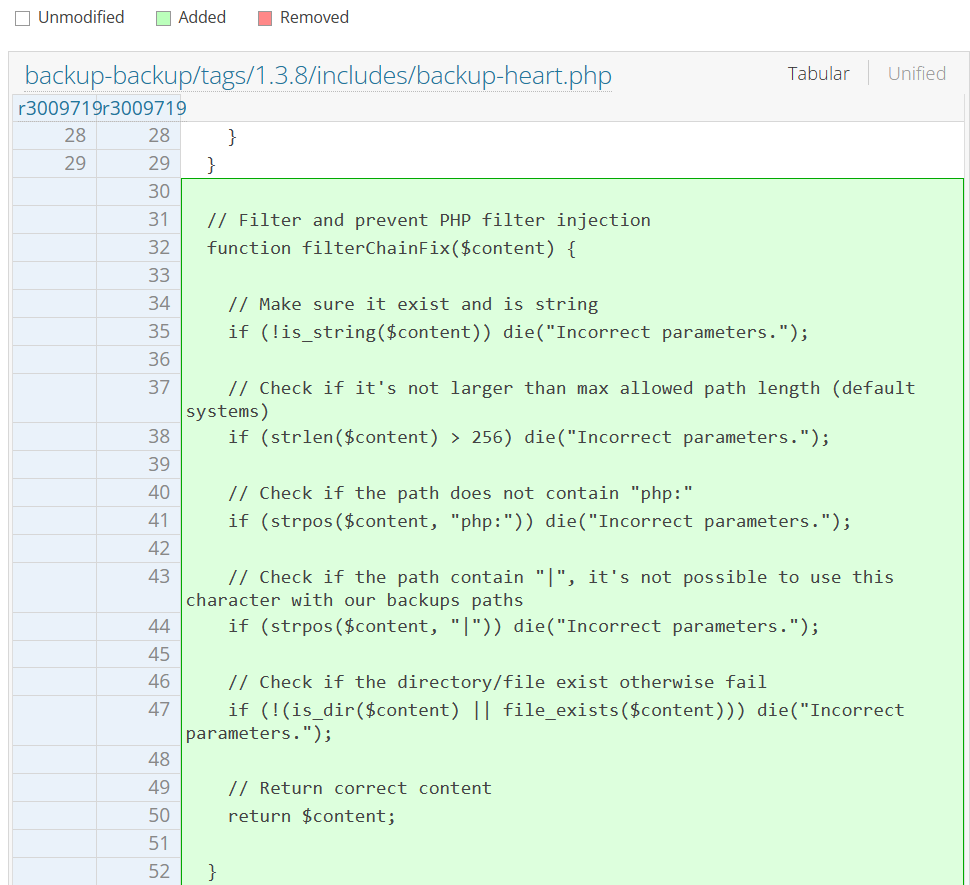
The patched version of the file includes several security improvements to address the issue, most importantly improved input validation with ‘filterChainFix’ function – this validates the input from the headers by ensuring the value it’s a string, limiting length of input, preventing PHP stream wrappers and its variants, and verifying the existence of the specified file or directory.
These changes show a clear focus on input validation and sanitization, which are crucial for preventing injection attacks and ensuring that the script operates securely with user supplied data.
Importance of auto-updates and website firewall
Vulnerabilities do happen from time to time. Fortunately in this instance, the plugin developers acted very quickly and a patch was released soon after the issue was found. However, the fact that many website owners have still not installed the security patch is a testament to how important it is to have automatic plugin updates enabled.
The time frame between when a vulnerability is released and when attackers start to exploit it is very small, so the best way to mitigate this is to have your website automatically apply the patch.
If you are unable to patch and update in a timely manner, consider using a website firewall to virtually patch your website and mitigate risk.











