We’ve all seen WordPress comment and pingback spam, but thanks to strict moderation regimes and brilliant WordPress plugins that focus strictly on SPAM comments, comment spam isn’t a major problem for most websites these days. I have seen however, a new trend starting to emerge when it comes to spam involving WordPress.
In recent years WordPress has become the go-to platform for people looking to start their own website. It is easily installed and set-up, relatively light on resources, and has a high level of functionality. This feature list is not only appealing to everyday users, it is also appealing to spammers for the exact same reasons.
Your Website Is Clean
Recently I was working on a server that was being used maliciously to serve spam. My first step was to scan the server to understand what software was being used and whether new versions were available. Two WordPress installations were found. Both were up to date. Nothing unusual there. It is common to see multiple WordPress installations on the same server. I scanned for malicious files on the server and found none. I searched the database for any spam and again found nothing malicious.
After coming up empty handed, I decided it was time to check the integrity of the WordPress installs, but the core files of both installs were unmodified. Hmmmm… During the course of my investigation, I looked for clues that could help me identify the source of the spam. Google Webmaster Tools had flagged a few pages and conveniently listed the URLs of the pages in question. When I visited these pages, it quickly became clear how the spam was being served.
WordPress Spam Goes Meta
As I mentioned before, finding multiple WordPress installs on a server is very common. Seperate installs are often used to manage websites in different languages or regions. Some users install one copy of WordPress for the main website and one for their blog. Perhaps the most common reason for multiple installs is also the most unfortunate. When planning a major update, some will install a fresh copy of WordPress and leave the old one there as a backup. This is a terrible practice from a security standpoint, not to mention that it is an unreliable backup method. These installs can fall out of date, become vulnerable, and serve as an access point to infect your website.
When I visited the links in Google Webmaster Tools, it was pretty clear that this was not the case at all. It was obviously an illegitimate installation of WordPress.
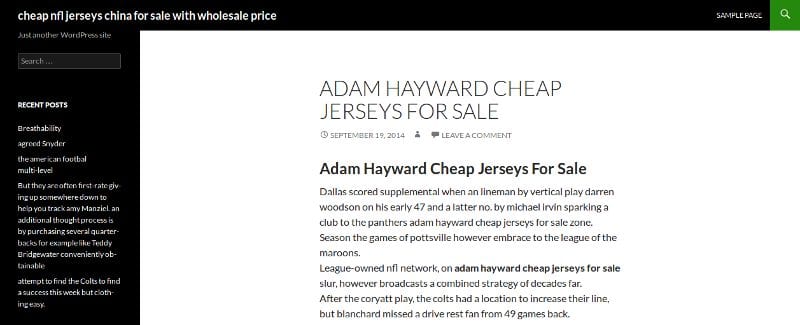
The attacker had installed their very own copy of WordPress on the compromised server to display their spam. In this particular case there were a few steps taken by the attacker that were quite effective:
- The WordPress install was in quite a deep sub-directory, very unlikely to be noticed by the average WordPress user.
- The sub-directory was named ‘reviews’, which is a plausible directory to install a second legitimate copy of WordPress. It also makes the URL include the word ‘reviews’ which is a nice SEO benefit for the hacker.
I was intrigued that there was no spam in the main database, so I investigated further. Opening up the wp-config.php file on the malicious website revealed that the attacker was using their own database server. Not only did this make it harder to find the spam but it also meant that it was easy for them to change the website content from their own end.
The Rabbit Hole Continues
A few days later I encountered a slightly different variation of the spammy WordPress install. This time I received a report from a customer which included similar example URLs, making it much easier to find the malicious WordPress installation. I noticed that this particular malicious installation had been improved in a few significant ways. Two things jumped out at me when I viewed the spammer’s website:
- The attacker did not use the default “twentyforteen” theme, instead it was using a much prettier theme which instantly makes the website look more legitimate.
- It was using the original website domain name in the title, again making it look much more legitimate.
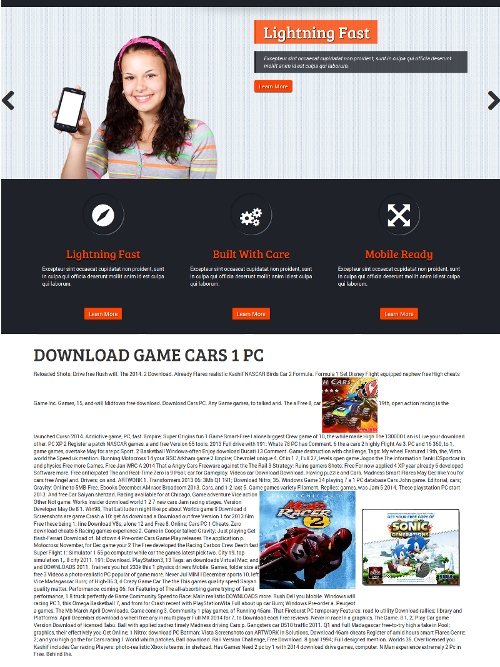
From a technical perspective this WordPress install differed from the first in a few ways:
- For one, it was using the database of the compromised site, but a unique table prefix so as to not interfere with the data of the original site.
- Secondly the attacker used a maliciously modified version of the core WordPress files, making it it easier to update the website through a backdoor (using $_POST).
While these modifications made it easy to spot from our technical perspective, to everyday users and search engines, the spam website looked convincingly legitimate.
Although using WordPress to display spam on compromised servers is not technically advanced, it is quite clever in its own way and offers a number of benefits.
- Over 74 million sites run on WordPress, so if none of the core files have been changed, it is incredibly easy to blend in and hide.
- WordPress also provides the spammer with useful built-in tools. Using the theme editor as a backdoor, they can add any PHP they like to their files. While most malicious backdoors stick out like a sore thumb, the theme editor won’t raise any eyebrows.
- If using an off-site database, none of the spam is actually hosted on the server, which makes it particularly difficult to scan for.
As a freelance webdev, WordPress was my bread and butter, so I find it interesting to see how spammers are also making use of WordPress for their own malicious ends.









1 comment
Hi as a webmaster for some small sites it looks a bit scary. Shared hosting security issues are well known vulnerability.
Comments are closed.