Exploitation Level: Very Easy / Remote
DREAD Score: SiteGround Optimizer – 9.4, Caldera Forms Pro – 7.4
Vulnerability: File Inclusion / Code Execution
Patched Version: SiteGround Optimizer – 5.0.13, Caldera Forms Pro – 1.7.7/1.8.2
While investigating the SiteGround Optimizer and Caldera Forms Pro plugins we have discovered a critical privilege escalation vulnerability.
It was not being abused externally and impacts over 500,000 sites. It’s urgency is defined by the associated DREAD score that looks at damage, reproducibility, exploitability, affected users, and discoverability.
A key contributor to the criticality of these vulnerabilities is that it’s exploitable by any user (it’s not restricted to privileged users – e.g., admins) and is easy to exploit remotely.
Current State of the Vulnerability
SiteGround and Caldera have both fixed their respective vulnerabilities.
SiteGround Optimizer
SiteGround Optimizer is a plugin intended for users of SiteGround hosting services. It helps improve improve the performance of WordPress instances by using a number of unique optimization techniques.
All customers that use this plugin in the SiteGround environment have been automatically updated. No additional action is required for these users.
If you use the plugin outside of the SiteGround environment, you will need to take manual action to update the plugin immediately to version 5.0.13. If you are no longer using it, we recommend that you remove it.
A successful attack on the SiteGround Optimizer would allow bad actors to store backdoors on vulnerable sites.
Disclosure / Response Timeline:
- Jan 14th – Initial contact attempt;
- Jan 15th – Vendor answers;
- Jan 15th – Sucuri provides details;
- Jan 16th – A patch is live, updates applied to customer sites.
Caldera Forms Pro
Caldera Forms Pro is a WordPress plugin used to create modern forms on a site.
If you use the Caldera Forms Pro plugin, you will need to confirm you are using version 1.7.7 (for the 1.7 branch) or 1.8.2 (for the 1.8 branch). This vulnerability only impacts Pro versions of this plugin.
The Caldera Forms Pro vulnerability would allow attackers to read arbitrary files such as wp-config.php and leak database access credentials.
Disclosure / Response Timeline:
- Mar 1st – Initial contact attempt;
- Mar 1st – Vendor answers;
- Mar 1st – We send them the details;
- Mar 2nd – Vendor plans update for March 5th;
- Mar 4th – Agree on ~1 week embargo before publishing the full details, leaving time for Caldera to inform its own users first;
- Mar 5th – Patch is ready to be pushed on wp.org, planned to be released on the 6th;
- Mar 7th – The patch is live on wp.org.
Technical Details
Both plugins leverage the WordPress REST API to provide new features to their customers. Some of the API endpoints failed to restrict sensitive functionality behind authentication controls.
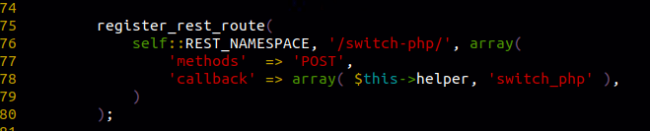
Endpoints registered with the register_rest_route function should use the permission_callback attribute to specify a method to do all their access control routines.
The screenshot above shows that it only used the callback attribute.
The switch_php method is responsible for critical functionality. Abusing this method would allow attackers to store malicious PHP code on the server (i.e., backdoors).
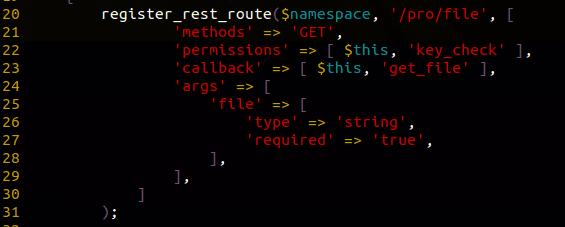
The Caldera Forms Pro plugin tried to apply privilege checks on that endpoint, however; the errors comes in the use of permissions attribute instead of permission_callback. The issue is that the REST API specifications only defines the latter. This means it will ignore the permissions attribute, making the endpoint publicly accessible to any visitors.
As you may understand from the callback method’s name, this made it possible to download any internal files from the site. It may also escalate this bug to a PHAR unserialization vulnerability if certain very specific conditions are combined.
In Conclusion
As the REST API gains in popularity among plugin developers, we believe more vulnerabilities like these will continue to surface.
If you are using vulnerable versions of these plugins, updating them should become your priority. Users of the Sucuri Firewall were protected from these issues from the very beginning.










