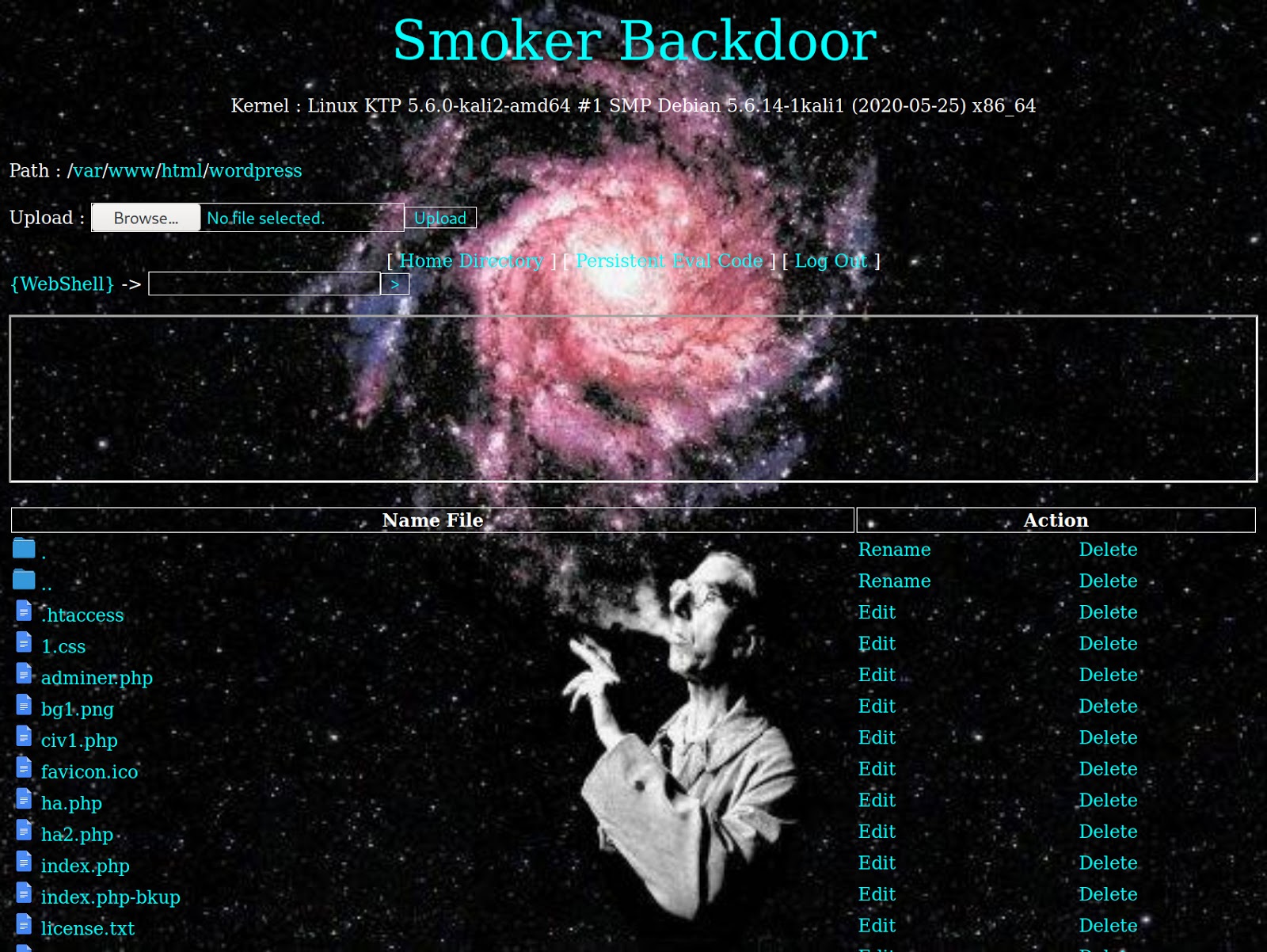
“Smoker Backdoor” is a PHP webshell backdoor that uses hexadecimal and decimal obfuscation in conjunction with the PHP function goto to evade detection from malware scanners.
The hexadecimal/decimal obfuscation is clear to see when viewing the file’s PHP code. For instance, this section of the PHP code is obfuscated using this method:
if ($_GET["\x72\145\156\x61\155\x65"] == "\164\x72\x75\x65") { echo "\x3c\146\157\162\x6d\x20\145\x6e\143\x74\171\x70\145\75\x22\155\165\x6c\164\x69\x70\141\x72\164\57\x66\x6f\162\155\55\x64\141\x74\141\x22\40\155\x65\x74\x68\x6f\144\x3d\42\160\x6f\163\x74\x22\76\xa\x20\40" . htmlspecialchars($_GET["\x66\x69\x6c\145"])
As with many webshells, it allows the user to set a password to control access to the webshell.
Backdoor Behavior & Obfuscation
The goto function works by allowing the code execution to “jump” to the designated target point. In this webshell, it’s first used right after the $passwd variable that holds the password to access the webshell.
$passwd = "najwa"; goto E0nyK;
This function tells the code to jump to the section of code containing the string E0nyK;, which is where the webshell stores the code responsible for blocking unwanted user agents — for example, web crawlers that may be able to detect and report on its existence.
$user_agent_block = "/Google|WhatsApp|Telegram|bing|Bing|yahoo|Yahoo|MSNBot|Slurp|PycURL|facebook|ia_archiver|crawler|Yandex/";
Using the goto function helps to conceal it’s malicious activity by allowing the malware to store the code out of order. It can simply use the goto function to jump to whichever section of code is necessary to run.
Once all of the PHP code has been parsed correctly by following the code’s different goto functions, it loads the final result: a basic PHP web shell.
Conclusion
Backdoors can be tricky to locate and remove — especially if more than one of them has been planted within a website’s environment.
To detect backdoors and other security threats, you can implement a file integrity monitoring solution to monitor core files. If changes, additions, or deletions to the environment are detected, you’ll be notified immediately.