Security Risk: Dangerous
Exploitation Level: Easy/Remote
DREAD Score: 7/10
Vulnerability: SQL Injection
Patched Version: 2.2.0
As part of our regular research audits for our Sucuri Firewall, we discovered an SQL Injection vulnerability affecting the YITH WooCommerce Wishlist plugin for WordPress. This plugin allows visitors and potential customers to make wish lists containing products in the WooCommerce store and is currently installed on 500,000+ websites.
Are You at Risk?
This vulnerability is caused by the lack of sanitization of user-provided data in versions below 2.2.0. An attacker (with at least a subscriber account) could leak sensitive data, and in certain configurations, could compromise your entire WordPress installation.
Please note that this is easily exploited in servers running MySQL versions before 5.7.
The interesting part of this vulnerability – and the reason we wanted to generate this security advisory – is that free “user registration” is usually enabled on sites using this plugin in order to allow user preferences (i.e. wish lists) to be stored and accessible for later use.
Technical Details
The vulnerable code is seen in line 523 of includes/class.yith-wcwl-shortcode.php in version 2.1.2. This code is part of the function get_products() which basically returns all wishlist elements for a specific user:
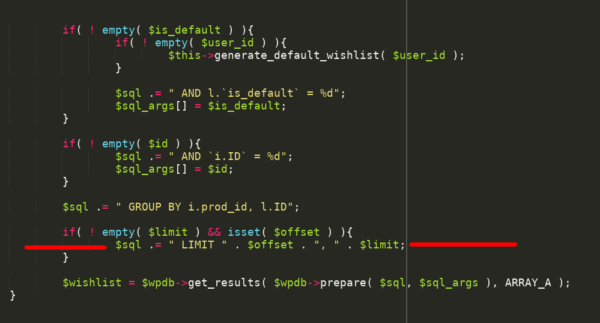
If attackers are able to set arbitrary values for the variable $limit they can modify the query in a way that can lead to a full compromise in several servers out there. One should not underestimate what can be done with an SQLi, nor how many servers allow attackers to get more than just encrypted hashes and user emails.
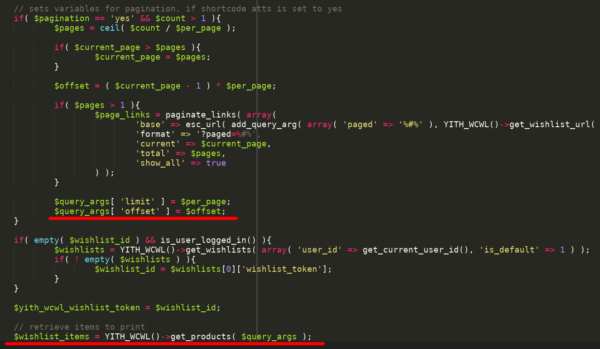
In order to reach the vulnerable query, an attacker will have to craft the request with the following parameters:
- pagination value has to be “yes”
- count variable has to be > 1 (this variable store the number of wishlist elements for a specific user)
- limit variable has to be set
The attacker can then fulfill all of these conditions via the shortcode yith_wcwl_wishlist defined in includes/class.yith-wcwl-shortcode.php:
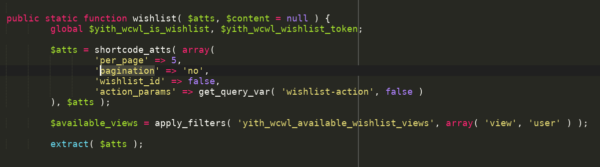
The only thing an attacker needs to do at this point, is create a user account and call the vulnerable shortcode as we described before in some of our posts.
Update as Soon as Possible
If you’re using a vulnerable version of this plugin, update as soon as possible to version 2.2.0!
In the event where you cannot do this, we strongly recommend leveraging the Sucuri Firewall or equivalent technology to have the vulnerability patched virtually.