Over the past few months, our security operations group have identified and mitigated an increasing number of DDoS attacks tied to extortion attempts from different cyber crime groups, including DD4BC, Armada Collective and a few more unnamed ones. These DDoS extortion attempts are starting to exploit smaller websites that may be less able to defend themselves.
DDoS Ransom Email
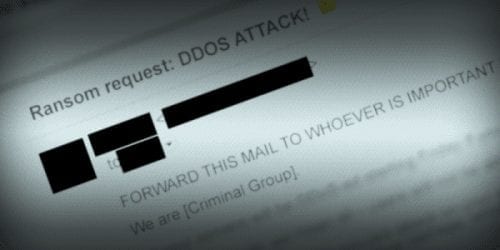
It all starts with an simple email similar to this one:
Subject: Ransom request: DDOS ATTACK!
FORWARD THIS MAIL TO WHOEVER IS IMPORTANT IN YOUR COMPANY AND CAN MAKE DECISION!
We are [Criminal Group].
All your servers will be DDoS-ed starting Friday if you don’t pay 2 Bitcoins @ [BITCOIN ADDR]
When we say all, we mean all – users will not be able to access sites host with you at all.
Right now we will start 30 minutes attack on your site’s IP (victims IP address). It will not be hard, we will not crash it at the moment to try to minimize eventual damage, which we want to avoid at this moment. It’s just to prove that this is not a hoax. Check your logs!
If you don’t pay by Friday , attack will start, price to stop will increase to 4 BTC and will go up 20 BTC for every day of attack.
This is not a joke.
This ransom email is followed by a small scale DDoS attack that can last from 30 to 60 minutes. After 24 hours, if the ransom is not paid, the attacks increase and can last many hours.
DDoS for Bitcoin
This type of extortion activity started last year (around Jun of 2014) and focused mostly on Bitcoin exchange sites and financial institutions. They were a rare occurrence with an attack every couple of months.
The ransom prices were high at around 40 Bitcoins ($14,000 USD) to stop the attacks.
By the beginning of 2015, these DDoS extortion campaigns picked up steam with a group called DD4BC (DDoS for Bitcoins) attacking many properties in a small period of time. They got a lot of media attention and some interesting analysis was done by the Arbor and Akamai teams on their activities and tactics:
- https://www.stateoftheinternet.com/trends-blogs-2015-07-dd4bc-exortion-campaigns-update-and-faq.html
- http://pages.arbornetworks.com/rs/082-KNA-087/images/ATIB2015-04DD4BC.pdf
It Won’t Happen to Me
Even though the media and security companies were already talking about this DDoS extortion threat, for most webmasters it felt like a foreign threat only affecting very large institutions and financial websites.
However, over the course of the last couple of months, we started to see an increasing number of extortion attempts against more average-sized sites. Everything from forums, small e-commerce and even some online gaming properties started receiving the threats and being DDoS’ed.
The price to stop this new wave of attacks also went down significantly, to just 2 Bitcoins ($700 USD). We are seeing these new DDoS ransom attempts more and more from what seems like an unnamed copy-cat group. They send a similar email threat:
Subject: DDoS
Hello!
All your servers are going under attack unless you pay 2 Bitcoin.
Pay to [BITCOIN]
Please note that it will not be easy to mitigate our attack, because
our current UDP flood power is 200-300 Gbps.Right now we are running small demonstrative attack on 1 of your IPs: [REMOVED]
Don’t worry, it will not be hard, since we do not want to crash your
server at this moment, and will stop in 60 minutes. It’s just to prove that
we are serious.We are aware that you probably don’t have 2 BTC at the moment, so we
are giving you 24 hours to get BTC and pay us…
This is followed by a SYN flood and layer 7 attack against the site.
After 24 hours, the attacks generally increase in size and can reach up to:
- 3-4 million packets per second – Syn Flood
- 400-500 HTTP requests per second – HTTP Flood
- 20-25 Gbps – UDP Flood
Most of the time we see all variety of DDoS attack types happening at the same time. That’s generally more than enough to take most sites down and get null-routed by hosting providers.
This increase in DDoS-for-ransom is concerning, as it seems that webmasters are often paying them. These attempts would just fade away if they were not financially lucrative. If you ever get such a threat, do not pay for them!
Fighting Back
Again, do not pay these ransom requests. Instead of sending the money to the criminals you should reach out to your ISP or security provider to see if they can help you. If you have to spend the money, do so to protect yourself, but understand they may still attack you even if you pay the ransom. Like with all ransomware, your best option is to have backups and protection in place before your website is attacked.
You can also contact us and we will help you navigate through this experience. Plus, sites behind our Website Firewall (CloudProxy) are already well protected against these threats.









6 comments
Another very insightful article! I really love seeing this perspective about what is happening in cyber-security in real-time.
I’m curious, though, what happens when the attackers overwhelm YOUR WAF resources at Sucuri? We all know that large-scale attackers have some serious botnets they can utilize. If you make your WAF a literal target by protecting sites that are targeted, then aren’t you going to end up with a problem for your non-targeted customers? Well, I’d guess you can make sure the non/targeted users are attributed to specific proxy servers. Do you partner with Akamai or other CDNs to help?
Myself, I just try to stay too poor to be able to pay anyone, lol. Definitely never give in to any kind of extortion. After all, if you ever do, besides compounding the problem for everyone, they will come back to take more bites out of YOU!
That’s a solid technique 🙂 Real freedom only comes when you do not have anything to lose.
As far our WAF, we try to have more bandwidth, more pipe and more servers (+ an optimized hardware/network) than the attackers manage to get. That allow us to handle all types of attacks out there without affecting any of our customers experience. We also have a Anycast Network, so every attack gets broke down into regions and each of our datacenters only get a % of the attack. Divide and conquer.
Hope it clarifies.
thanks!
Well, it’s a technique with a few drawbacks, lol.
Anyway, good to know you haven’t had any problems so far. I am very interested in your service, though couldn’t deploy it right now, due to some little issues that you guys are working on (mostly just Apache 2.4 support in the WP Sucuri plug-in, but also official and well-tested IPv6 support, which never seemed quite ‘right’ to me in some cases, but it may have just been me).
I’ll likely give you a go in a few more months. Just as an extra safety. I appreciate very much your support for HTTP/2, and Spdy before that, BTW!
They have an impressive amount of bot traffic. What methods do they use to acquire so many bots? If its from viruses on personal computers maybe we should raise awareness about it and educate people on how to avoid viruses.
I would actually like it if internet providers could be able to detect DDoS traffic coming from their customers and limit their customer’s internet speed until they fix the issue.
I think the security industry, which is pure fear-driven, has definitely dropped the ball by providing the ILLUSION of security, when, in-fact, their real-world malware detection rates are less than 50%, else we wouldn’t have this problem. That illusion of security makes people feel safe, then they don’t act safe.
Users who are simply careful about their online browsing habits can do without a huge security suite that slows their PC down 10x to do real-time scanning. So, we definitely could and should educate users better, and recommend OS reinstalls bi-yearly at least. Even then, there will still forever be huge botnets in the world because people will always ‘risk it’ to get something for free – whether it’s cracked software or porn.
Heck, these days, you could drop a cheap Rasberry Pi at a friend’s house (or other compromised/known WiFi AP) and use it as a bot. Oh crap, I probably just gave people an idea. That said, open or insufficiently secured WiFi is another big part of the problem.
LASTLY, if all that wasn’t enough, it’s very easy to provision a new Amazon AWS server instance on a stolen credit card and be up and running with serious resources in no time.
actually, alot of these guys DO NOT RENT BOTNETS. as someone whom has been in the game, and researching these types of things far longer than you have daniel, that may have been how things worked in the early 00’s, however alot of these guys do not rent out shit as far as their resources go. they simply utilize as many vuln servers/routers as they can get their hands on to carry out their ddos attacks.
you should face the reality that there are countless amounts of resources they can utilize to map out and acquire lists of vuln hosts easily, shodan, censys, many more services that provide them lists of ips that they just have to feed on to the scripts they have popping the vulns and dropping their bots for them. from there its fair game.
Comments are closed.