Online bad actors tend to take advantage of tragedy for their own gain – and the coronavirus is no different.
While we would hope that cybercriminals would be sympathetic during a global health crisis, it already appears this may be a pipe dream. As the virus spread across the world causing shutdowns and quarantines, cybersecurity analysts began seeing coronavirus and COVID-19-themed cyberattacks in the wild. In the Czech Republic, a hospital that was a designated testing center was hit with ransomware.
It’s a very unfortunate situation, but the truth is that quarantines won’t stop these bad actors. With so many people in their homes either under quarantine or isolation, it is almost certain that bad actors will be targeting more institutions, businesses, and even individuals.
As a result, we wanted to take a look at some of the potential phishing and malware campaigns already appearing to take advantage of this global crisis.
Fake CDC emails for phishing campaigns
Cybersecurity researchers already expected phishing campaigns to be on the rise in 2020. So when the coronavirus pandemic began looking like a reality in February 2020, it’s not surprising that phishing attempts began appearing. We’re expecting them to continue, especially with more businesses working remote in the coming weeks.
The most common goal of phishing campaigns to obtain financial information. Hackers are hoping to get credit card or banking credentials, or even for you to send money to them. In a time of economic uncertainty, falling victim to one of these scams would be especially devastating.
Here is an example that our parent company GoDaddy shared with their employees. It’s an email masquerading as a bulletin from the Centers for Disease Control. Take a close look at the red highlights.
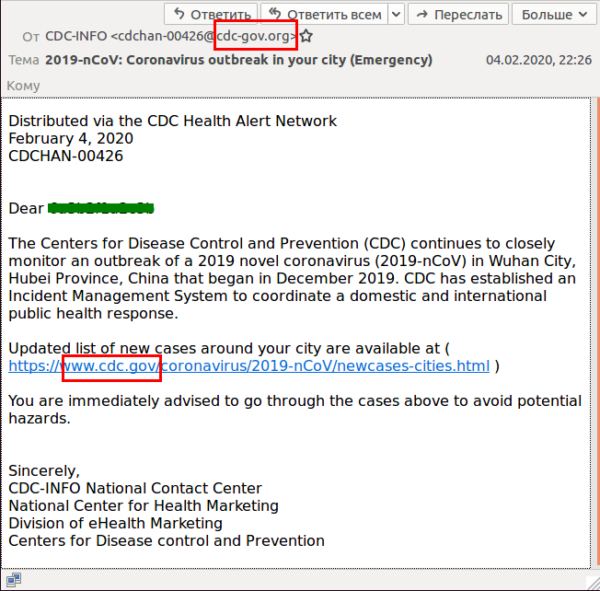
Signs of a phishing campaign
Email address
Take a look at the email address. It’s not from a .gov domain, which would signify a US government organization. Instead, it’s a fake domain of cdc-gov[dot]org. The creator of this phishing campaign was hoping the receiver would not notice the discrepancy.
Suspicious links
While the link in the body of the email is listed as a .gov address, remember that link text and link destination can differ. In fact, it’s probably the easiest trick in the hacker’s arsenal. Anyone with a basic email client can do it. As an example, another bogus CDC email had a link that led to a malware installation.
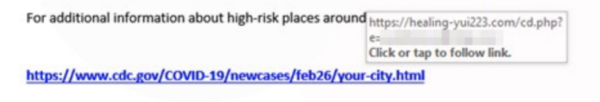
Be very cautious about any emails you receive relating to the coronavirus pandemic. We highly recommend brushing up on how to recognize phishing emails during this time.
Suspicious SMS links and social media posts
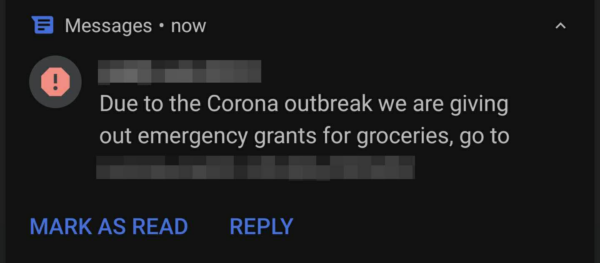
Our team has also seen reports of SMS messages with apparent phishing attempts. One that was submitted appeared to be an alert offering emergency grants for groceries. But the link was a fraudulent attempt to steal bank account information.
However, not all of the bogus posts we’re seen have even been directed toward trying to phish or steal information. For example, here is a Facebook post from a fraudulent page that appears to be associated with a national grocery store chain offering an hour-long shopping spree during the pandemic. It’s only if people show up at a specific time.
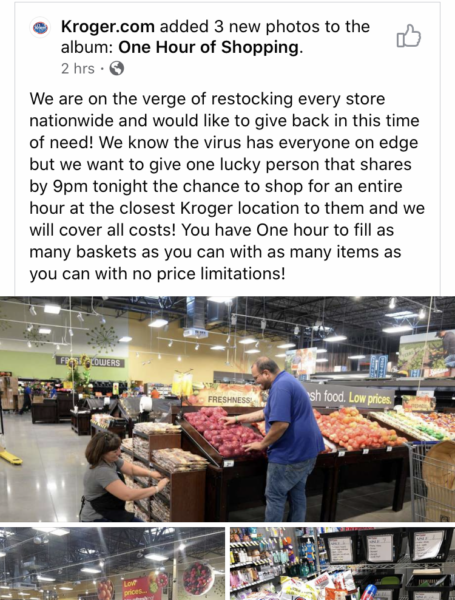
The thing about this post was that the national chain had also announced shorter store hours. The store would have been closed at the 9 p.m. time advertised, causing potential havoc and unnecessary travel. It’s very likely whoever created this just wanted to create chaos and confusion – two things we desperately do not need any more of right now.
Fighting against phishing campaigns
We have seen that bad actors are not going to stop taking advantage of vulnerabilities during this crisis. We also know people will be spending more time online. It is very important to keep an eye out for phishing campaigns – as well as misinformation in general. Learn how to recognize a phishing campaign to avoid becoming a victim.
Just as handwashing and social isolation are our best weapons against the spread of coronavirus, everyone will also need education and diligence to fight the spread of phishing and other forms of malware. Sign up to our blog feed and be on top of what is happening in the cybersecurity world.
Stay safe, everyone!