Unwanted ads are one of the most common problems that site owners ask us to solve. Recently, we’ve noticed quite a few requests to remove intrusive “shorte st” ads that they never installed on their sites themselves. My colleague Denis Sinegubko of UnmaskParasites helped to investigate this case.
Shorte[.]st is a service that hijacks links, forcing visitors to view a page containing ads before they can visit the link they clicked on. Site owners usually install the script themselves and earn money for exposing site visitors to the (often deceptive) ads.
However, this time webmasters denied installing the “shorte st” ad script. Moreover, some said that the “shorte st” ads replaced ads from other providers they used for site monetization.
In addition to interstitials for clicks on links, full-screen ads are displayed when a visitor comes to the website for the first time.
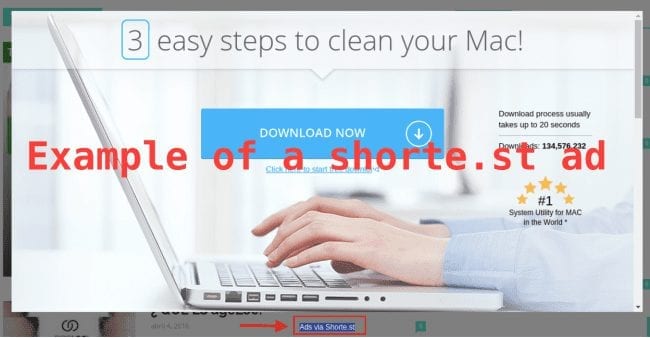
The ads vary for visitors from different countries, browsers, and operating systems. In general, the content of the ads is questionable. Sometimes, instead of seeing the ads, visitors see an empty rectangle or a full-screen block displaying a database error. Needless to say, this unwanted behavior significantly compromises the user experience for these sites.
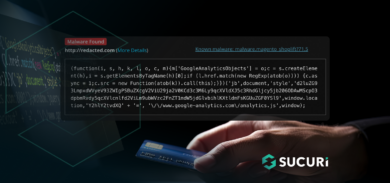
In each of the cases, infected web pages contained the following injected code:
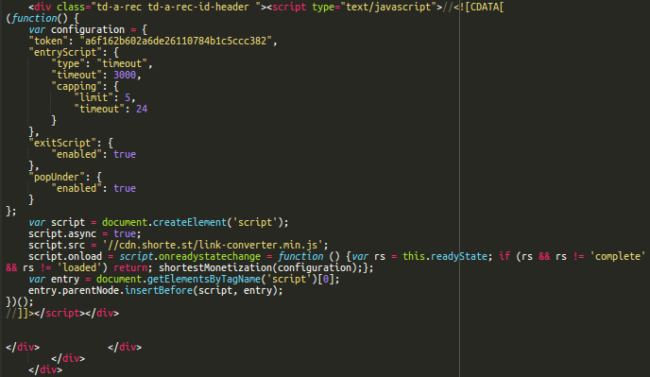
Newspaper Theme Under Attack
The code was injected into the wp_options table of WordPress database. Shortly after, we noticed that the infected sites were using a popular premium theme called Newspaper (and its sibling Newsmag or its derivative). The theme had been sold to over 40 thousand users, not counting pirated copies.
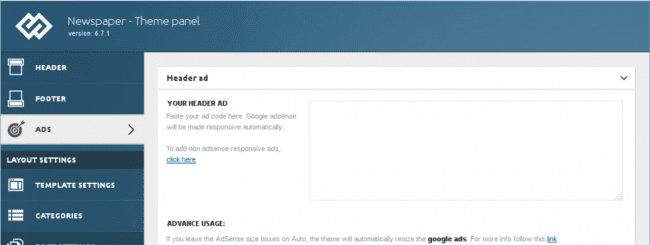
The injected ad code corresponds to the theme’s “header ad” that site administrators can modify in the theme panel of the WordPress admin interface.
At this point, it appeared that there was a major problem with this particular theme. It turned out that versions 6.x of this theme had a serious vulnerability that allowed attackers to modify arbitrary WordPress options.
One way to exploit this vulnerability was disclosed a year ago. The security hole was quickly patched in version 6.7.2 of the theme, but as it often happens, quite a few sites didn’t update the theme. One year later, all the affected sites still used vulnerable versions 6.4 – 6.7.1.
Logs Showing Shorte St
To prove that this old vulnerability was indeed connected with the “shorte st” ad injection, we decided to scan logs of our website firewall that protects sites of thousands of our client’s websites.
It was easy to do because the injected code had the following unique “shorte st” tokens:
" token ": " a6f162b602a6de26110784b1c5ccc382 " " token ": " 8f1bc5aa7e697f9829c057cfd305bd64 "
We discovered an ongoing attack that tried to inject the “shorte st” script passing it in the td_ads[header] parameter of admin-ajax.php POST requests. We reconstructed the requests on our test servers and confirmed that the attack exploited the old vulnerability, and updated versions of the Newspaper theme 6.7.2+ are protected against it.
Cleanup and Hardening
It’s easy to remove the injected “shorte st” ads. You just need to remove that code from the Newspaper theme panel’s “header ad” block in WordPress admin interface under Newspaper > Theme panel > ADS > YOUR HEADER AD. You can also replace it with your original ad code.
However, please don’t stop here. If you don’t do anything else, your site will be reinfected because the security hole is still open and the attackers already know that your site is vulnerable. We have reports that the unwanted ads return within a couple of days if the site is not hardened.
To prevent reinfections you need to update your theme to the latest version (patched in 6.7.2). We realize that sometimes theme upgrades are not that easy, especially if for some reason the theme has been heavily customized. In such cases, you should consider using a website firewall that can virtually patch the security hole.
Conclusion
This “shorte st” ad injection is not the only possible way to exploit the Newspaper theme vulnerability. Not only can the security hole be used to inject more malicious code, it also allows hackers to completely take over the blog (e.g. inject a script that would steal admin user cookies or enable user registrations that change the default role of new users).
Please take your website security seriously. Patch the vulnerability and then inspect your blog for a presence of suspicious users. Our free SiteCheck scanner can detect a number of security issues that show up in a browser. Test all settings, change passwords, and scan your server for backdoors that hackers could have left if they really broke into your site.