Updated 20160914
This post is very specific to one type of infection, there are many different types of infections and symptoms, do not be discouraged if the scenario does not fit your situation.
A more detailed guide on how to address a hack in WordPress was released in 2016.
If your site got hacked on the last mass infection of WordPress sites out there, we have a simple solution to clean it up.
For Network Solutions users:
If your site is at Network Solutions, and you have that “virtual-ad.org” malware, the solution is simple.
Login via FTP and remove the file cgi-bin/php.ini. That’s all you need to do to protect your users.
You will still have some “.nts” files in there (which you can remove later), but they will not be executed without the php.ini.
Via SSH:
If you have SSH access to your server, run the following commands on your web root:
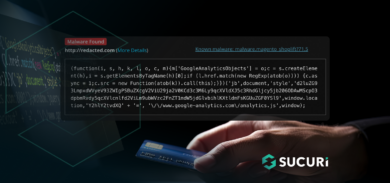
$ find ./ -name "*.php" -type f | xargs sed -i 's#<?php /**/ eval(base64_decode("aWY.*?>##g' 2>&1
$ find ./ -name "*.php" -type f | xargs sed -i '/./,$!d' 2>&1Via web:
If you don’t have SSH access, download this file to your desktop:
http://sucuri.net/malware/helpers/wordpress-fix_php.txt and rename it to wordpress-fix.php.
After that, upload it to your site via FTP, and run it (using your browser) as: http://yoursite.com/wordpress-fix.php
This script will take a few minutes to complete, but will scan your whole site and remove the malware entries.
Once you are done, go back to your site and remove this file.
That’s it and you should be clean again.
UPDATE: If your site is not getting cleanup after you run it (or you are getting extra empty lines on the top of your files), it means that the script didn’t finish to run properly. Try running it again. It it doesn’t help, upload it to some sub directories (like wp-admin, wp-content and wp-includes) and run directly from there. For example:
http://yoursite.com/wp-admin/wordpress-fix.php , http://yoursite.com/wp-content/wordpress-fix.php , etc.
That should fix it!
As always, if you are having difficulties getting your site cleanup, send us an email at contact@sucuri.net or visit our site: http://sucuri.net. We can get your sites clean up right away.
Also, consider checking out our site security monitoring. We will monitor your sites 24×7 and alert you if it ever gets infected with malware, hacked or blacklisted.








176 comments
This cleaned up all the code on the top of each .php page. But it didn't remove the actual script just above the body tag.
How do I get rid of that?
Adam:
The script is generated by that big PHP code on the top of your pages. If the malscript is still there, maybe you have your pages cached (clean your wpcaches) or our script didn't completed properly (some PHP pages may timeout while running –depending on your host config).
OK, I'll wait a bit and see if that clears itself up. I was able to run the script on the rest of my sites and it works great. Thanks so much!
I went and manually deleted the lines in the cgi-bin/php.ini mentioned in the first post today on my NS shared host account. Deleted all cached pages and now my NS sites are scanning clean. Should I still run this fix as well?
After that, upload it to your site via FTP, and run it (using your browser) as: http://yoursite.com/wordpress-fix.php
Upload it to where? Root?
Just to follow-up. I ran this script several times today. It worked flawlessly on most sites, but on one blog I eventually had to manually remove the malware script from the index.php file in the root folder.
Kudos on this fix!
Thank you very much! you are much helpfull then godaddy can do on it.
my site is also hacked by a php code in the head of the file.
Hi all,
My site was also hacked. But it was a Joomla (1.5.15) site (no word press).
The fix of course helped. The server was "godaddy shared hosting".
I believe all my chmod settings were correct (644 or 755).
No idea how they got in. But it looks like they did not change anything else.
So if I put this in the root, it'll also scan all subdirs?
God Bless you Sucuri. This word sounds like Romanian. If you are a Romanian (Sa-ti dea Dumnezeu sănătate)
it works fine!
Many many thanks!
Ramses: yes, it will scan all subdirs. If your site is too big, the PHP may timeout in the middle, so you may need to run it again.
Ioan: Brazilian 🙂 All latin languages, so easy to mix it up .
Heads Up from NS.
May 8, 2010
We received alerts of a new type of file inclusion on our customers’ websites, whereby a “.nts” file is added to folders of customers’ hosting accounts. Visitors to affected websites will receive a “website cannot be found” message and may be infected with malware. This “.nts” file addition is occurring mostly within the structure of customers’ WordPress installations, however the issue is not with WordPress. We ask that you please remove all files with the extension “.nts” in order to resolve this issue.
Still can not access my account through SFTP since yesterday.
Can't say I blame NS at this point for sealing access off.
It is however getting a little frustrating.
Omg WordPress is sending a 503.
"Goshdarnit!
Something has gone wrong with our servers. It’s probably Matt’s fault.
We’ve just been notified of the problem.
Hopefully this should be fixed ASAP, so kindly reload in a minute and things should be back to normal."
Maybe it's four million people wondering what to do now that a hacker's attacked their site and damaged it?
Should you run this although you have already cleaned your site?
I guess it can't hurt but I am wondering if it would take the site down temporarily or something?
The first 'find' command line appears incomplete..(I don't see a closing quote/brace)…am I missing something?
Hey man, thanks so much for this script you saved my ass!
I can't thank you enough for this free script!
Melissa
I too would like to say thanks for the script. I went slow so it took me more than 10 minutes, to be sure I did everything right – but it worked.
For info purposes, also on Godaddy – I had latest version and secure pw's. I also did not have all of the lines in the source code, but did have the indesign one – everything is good now.
Many thanks, it fixed it.
my site was hacked by this too.
Godaddy shared hosting.
Watch Out . . I was attacked instantly when I checked out this story.
Mass Shared Host Website Hack
Ghacks Technology News – 1 hour ago
These servers host multiple websites by different users. Affected web hosting companies are Go Daddy, Bluehost, Media temple, Dreamhost and Network …
An intrusion attempt by www1.firesavez7.com was blocked
Risk Name HTTP Fake Scan Webpage 5
Attacking Computer www1.firesavez7.com (209.212.149.20, 80)
Attacker URL www1.firesavez7.com/107a9dcdafc2f5304469e3e909971c691f503009011.js
THANK-YOU so much!!! I wish I'd found this post on Friday night. Now all I have is a index.php error at the top of my site, which I think I can fix on my own…
Kim, please tell me how you fixed the index.php error. I'm getting it everywhere including admin areas so cannot log into the the admin area currently, but do have ftp access to the files.
Ghacks Technology News
Current Registrar: GODADDY.COM, INC.
The Plugin AntiVirus for WordPress can detect the virus
http://wpantivirus.com
Thanks so much for this!
I've no idea how my site got hit but looks like this did the trick to clean it up. Wp antivirus plugin did not detect this for me. I'm also on godaddy shared hosting.
@Anonymous
Wp antivirus plugin check your theme files only.
It is a new development in 2009 that the #1 cause of website hacking is the webmaster's personal computer being infected by malware that steals FTP login information and sends it to remote computers which then inject the victim website's pages with JavaScript or hidden iframes pointing to malicious websites such as gumblar.cn, martuz.cn, and a growing list of others.
Make sure everyone who has password access to the website does at least one, and preferably two, antivirus and antispyware scans on their local computers, using two different scanners they don't normally use, to find threats that got past the AV scanner they were using. Some free scanners are at: Trend Micro Housecall, Kaspersky, Malwarebytes, Symantec (Norton), BitDefender, Windows Live OneCare, Computer Associates, McAfee, F-Secure.
i cant't find cgi-bin/php.ini nor any files with .nts in my files
where to find it?
I've ran the script you've provided it's removed the infection from my forum but it's still within my wordpress setup. Also I've edited the footer.php of my theme myself, this is all new to me and i'm not sure how to remove it fully.
i cant't find cgi-bin/php.ini nor any files with .nts in my files . . where to find it?
…………………..
That's a commonly asked question that is not being addressed. Considering many customers on shared hosting are not techies, but creators of content.
"Run this script" doesn't help much if people do not know where and how to run it.
Thank you, thank you, thank you! This saved me alot of time.
The fix works like a charm. Thank you so much for helping!
Thank you guys so much. I have a GoDaddy shared server site that was attacked as well. GoDaddy has been absolutely worthless. The via web script you provided worked GREAT and everything seems to be running smooth once again. I can't believe after the amount of time I spent with GD you were able to provide such a quick solution.
My site was running phpBB3 by the way.
Folks, another way to stem off the attacks is to install our free wordpress plugin: http://wordpress.org/extend/plugins/wp-secure-by-sitesecuritymonitorcom/
I am a computer consultant helping my local paper deal with the attack and, more importantly, giving advice to computer users who may have been infected.
As the attack occurred for us Sunday, for Windows users, I will suggest restoring the computer to Saturday.
Does anyone know if Mac computers were affected? If so what advise should I give them?
Thanks!
Francoise
Thank you so much! GoDaddy was worthless and made me wonder why I pay for them! I was up and running in less than 10mins. I have a GoDaddy shared hosting with WordPress MU.
After I started getting page not found errors on my siet, Paul at NSI pointed me to a file named .htaccess. It wasn't there before. I found another – nts.php, both deposited 5/10/2010. After renaming .htaccess access worked fine; also renamed the nts.php. Not running WordPress.
Bad when the top-tiers like NSI are getting hacked, but with one exception I've had great support from their phone reps.
if you look at the source: view-source:http://zettapetta.com/js.php (in Firefox) you will see that it looks for a PhpMyAdmin Cookie. That PhpMyAdmin software is likely vulnerable, based upon the Cookie name used in various PhpMyAdmin themes. So they probably found a zero-day in PhpMyAdmin on the looks of it.
Goodluck.
-Skyphire.
hi, i wrote a php script that looks up for all php files and deletes that nasty piece of junk…
http://www.luminux.cl/clean.zip
Mine was hit on a Drupal backbone… will this fix work for other things besides WordPress?
This was incredibly helpful. Without your brilliant code I'd be up a river without a paddle. Many thanks.
Should I be getting a page not found error when I run the fix?
thanks – quick fix – much appreciated.
It even fixed the malware on my joomla page! Thanks! Hope this dreaded code doesn't come back in a few hours! I first downloaded Avast anti-virus and it found a file on my computer that malwarebytes didn't find. Then I used this php script and it found and erased the junk from my wordpress and joomla pages.
My site seems to have become reinfected.
I would like to say thank you very much. I have about eight wp blogs on Go-daddy that each make a small fortune everyday. I have suffered attack after attack, uploaded new files everything.
I just used your script and had a one hundred per cent result of removing the malaware from my code.
You have saved me loads of time and effort.
Well done and a huge big pat on the back. I wish I could buy you a few beers.
Terry
What about MySQL infection and/or unknown users and/or installed backdoors? What should I be doing to protect myself vis-a-vis these (potential) issues?
The result showed malware removed, but my wp dashboard is still messed up. It ends at post. I can't access the plugins, appearance and other functions. Is this an attack?
I ran the script on my Joomla site and now cannot login on the backend.
This worked perfectly.
Funny thing is, yesterday I set up a Brand New WordPress site through Godaddy [they installed it] and it was hacked as soon as I logged in for the FIRST time. I had to have been the first visitor.
Their support told me to install the newest version of WordPress…which uhhh…they had just done! That was their only suggestion. Four other WP sites of mine on the server were also hacked. Plan on fixing them asap.
Thanks Sucuri, you saved me!
It appears that this fix (Web version) is adding whitespace to the PHP files. I'm having problems with all WordPress and Joomla sites after running it.
Anyone have any ideas?
I am having the same problem with the person above. I am getting errors on most of my site with a message similar as follows "Warning: Cannot modify header information – headers already sent by (output star……"
It seems there is a white space on the top. I looked at the script and it seems it was supposed to remove the white spaces, but it doesnt look like it has. Also, I have over 25,000 files on our host, so i'm not sure if it ever finished running or timed out.
Same here, it is leaving one row of blank space at the top of every single file.
Gregg, i think i figured out what is happening. the script is timing out before it can finish. I just figured out how to get it fixed by running the file in each of my folders separately. I had over 25,000 files from within my root directory, but running the script in each sub folder made sure the script didn't time out.
Thanks for this fix! It is a life saver! Now we just need to figure out how this all happened.
Any ideas if the infection can or will come back again?
Maybe run this first to check if you actually have it before running a command that edits files?
# grep -lr 'base64_decode("aWY' ./ | grep *.php > base64.txt
What is this looking for?
sed -i '/./,$!d' 2>&1
Thanks a bunch, I reposted this on my site with a link back because one of my clients had this problem today!
I'm going to be honest, I don't know how to "Run as…(using your browser)" I go to that URL and it gives me a 404 error. I open the file with my browser from the folder and it just opens up the location in my folder with the text and does nothing.
Please be more detailed regarding how to run this. Not all of us are tech whizzes.
Nevermind, I figured it out just now on my own. You have to upload it to the '/' directory on your FTP server so that 'example.com' is the root. Then go to 'example.com/wordpress-fix.php' and it'll work.
Hope that helps anyone else who had the same questions.
That said, the virus is apparently still blocking my RSS feed. I'll try running it again, but I hope this isn't a seperate issue.
Having problem with (web version) ran fix in all sub directories after I enter fix in browser and hit enter it takes me to my site and I see (whatever your looking for is not here)..Help please or am I running script wrong? I am using filezilla to upload fix.php to directories
I updated my Gumblar script to remove this malware, too:
http://www.danielansari.com/wordpress/2010/05/holasionwebcom/
This uses a regular expression that does NOT leave any blank lines at the top.
Thank you. Fix worked great. Much appreciated by myself and my clients.
3
THANK YOU!
Worked perfectly – and not reinfected yet.
Thanks for the fix!
I just want to say a big thank you. In my case, my site was fine but i got redirected to a malware site when i tried to log into my wordpress blog. luckily my antivirus system blocked the attempt. I therefore had to run this from my wp-admin folder and the scrambled looking wordpress dashboard is now looking normal! thanks a ton!
Warning: Unexpected character in input: '' (ASCII=92) state=1 in /home/content/d/a/i/dailyotaku/html/wordpress-fix.php on line 4
Parse error: syntax error, unexpected T_STRING in /home/content/d/a/i/dailyotaku/html/wordpress-fix.php on line 4
am getting this all time what do I do to fix it
Thanks much for the info and script. Has anyone figured out what the vulnerability is here, though? Getting my site back up is one thing, figuring out how to stop this same attack from happening is a different ballgame.
What about for SimpleMachineForum (SMF) website? Are there any way to detect and clean the same virus?
Thanks a lot for your marvelous help.
I felt free to translate your help in french on my blog
http://ddl2ouf.blogspot.com/2010/05/hack-wordpress-nettoyer.html
fixed my site – thanks
Thank you so much! This worked beautifully!
Godaddy host, infected my Magento installation as well as my straight php files. Very frustrating.
Thanks for this fix. It doesn't seem to be working for me though. It looks like this line of code:
[code]
$rmcode = `find $dir -name "*.php" -type f |xargs sed -i 's###g' 2>&1`;[/code]
gets broken at the '*?>#' part. At least it looks that way in my php editor…
plus it hasn't fixed my files…
If the script is timing out on you, or the status messages "Malware Removed" or "Empty Lines Removed" does not appear chances are your script is not getting a chance to run to completion. I added:
"ini_set('max_execution_time', 300); //300 seconds = 5 minutes"
to the top of my script and it worked like a charm. Thanks for the fix, it saved my ass. down w/ godaddy
Reported the problem to godaddy and they still continue to deny it's a security issue with them, not wordpress or PHP. unbelievable. After 2 hacks in less than a week.
I just fixed my site with this amazing script – thank you so much. I have a WordPress Mu blog hosted by GoDaddy (I know – they stink)…Anyway, I wanted to know if anyone has experience with either of these plugins:
http://wordpress.org/extend/plugins/secure-wordpress/
or
http://wordpress.org/extend/plugins/wp-secure-by-sitesecuritymonitorcom/
I don't want to load more stuff on my blog unless I know the 'security' plugins are secure themselves. Any thoughts? Thanks!
Who can I give a big kiss to?? Thanks a million!!
It is very important articles! A friend of mine suffered from this virus.
With your permission, translated into Russian and published in his blog.
Luck to you!
Thank You very much! I was searching for solution to this problem from hours, and your script wordpress-fix.php fixed the problem within 1 minute.
Thanx a lot again!
The link to http://sucuri.net/malware/helpers/wordpress-fix_php.txt seems to be to a missing file! What happened to it?
Thanks alot !!! this works very well i can clean my forum ( i don't use wp and i reinfect too ) I moveout from godaddy
Works for phpbb too, fixed my phpbb3 site. Thank you, such a simple bit of php code and regex, surprised godaddy was too slow to give it to their customers on day one.
Thanks a ton! Worked like a charm on my site!!
Thank you so much for this script. I added it to my root directory. I can't believe how quickly everything was cleaned.
This is the 2nd time I was infected in a month and the 3rd time in 5 months (if I remember correctly). Time to change hosts.
Just like last time… worked like a charm.
Thanks fellas. This is getting a little ridiculous… but I'm glad someone is offering a very quick, convenient, FREE solution.
Perhaps if I can convince my webmaster to spend the money… we'll invest in your monitoring… that way we lose LESS visitors anyways… by catching this BS a bit sooner!
thank you very much! simple and effective! My sites were hacked twice. What can i do in order to avoid a third hacking? Thank yo again
Thank you so much. This completely saved my sanity, especially after GoDaddy denied it was on their end, and blamed me when I let them know about it (virus, crummy passwords, etc). My PC is clean, completely spotless I just have no real clue as to how they got in (secure password, while I do use FTP / shared hosting).
I've cleaned up about three times at this point, and hopefully this will help more (if it happens again too).
Thank you soooo much for the clean-up script. I had already spent hours doing what GoDaddy recommended (back-up files, restore to an earlier date and re-install WordPress and delete old WP files) and was re-infected. Your clean-up script worked perfectly. So far so good – no re-infection.
Just to confirm that this also works on Joomla sites. Although, there were some errors after cleaning with extra space before opening PHP tag, which was easily solved by deleting that space…
I have x-cart on my domain and it has been affected again after I cleaned up. It is on Godaddy. X-cart version is not latest.
What do I do now?
This virus attacked a MODx site on BlueHost. I deleted the code from the top of the index.php and all seems to be good now.
I refuse to believe this. This is too good to be true?!
…it removed all of those strings extremely quickly & easily… but will my site stay safe from malware? Or will I have to constantly use this script daily? Great work though! I signed up for a full year of Sucuri security too!
What's the fix for Joomla users?
Hi. downloaded and ran wordpress-fix.php
It didnt work . tried it in blog directories too.
Still didnt work.
Base64 code still at top of php pages.
Hi,i am not a techi in this
Kindly help me fix my website as it's been infected with the dreaded http://holasionweb.com virus
script src="http://holasionweb.com/oo.php
I downloaded and ran wordpress-fix.php. But I got the status messages "Malware Removed" or "Empty Lines Removed". The website problem still remain the same. Can I know anything i did wrongly in the process of running wordpress-fix.php. How to solve it?
AMAZING! Worked perfectly. You saved me so much time. All things good come to you!
I'm having an issue with Movable Type blog. I've run the commands you thankfully posted and cleaned up several WP blogs and it appears to have cleaned the php files for my MT blog. But strange things are happening.
I will load a page on my blog and after a few minutes it attepts to redirect (I'm using Mac and Safari) and i get this error:
Safari can’t open the page “http://www.qooglesearch.com/?source=rmac&said;=2060&ref;=http://worldrider.com/blog/archives/2006/08/worldrider_in_t.php” because Safari can’t find the server “www.qooglesearch.com”
In looking at the source of this page, I find at the bottom:
scripttt src="http://zettapetta.com/js2.php">
(I've edited this to validate this comment
My guess is that Safari tried to redirect it to the phony GoogleSearch page but on other browsers maybe the script tries to install malware.
I'm not sure how many pages this script is on, but running your commands cleans the garbled code but this is actually plain and simple and nothing trying to hide it? Thoughts?
This is a follow up to my post just a few minutes ago.
I tried running these commands via ssh again and I get an error on the first one and the second one just seems to hang:
[xx]$ find ./ -name "*.php" -type f |
> xargs sed -i 's###g' 2>&1
[xx]$ find ./ -name "*.php" -type f |
-bash: : command not found
[xx]$ xargs sed -i '/./,$!d' 2>&1
I keep getting the following error messages when running the script, can someone please help me?
Warning: Unexpected character in input: '' (ASCII=92) state=1
Parse error: syntax error, unexpected T_STRING
Hello Guys,
I am also a victim.My suggestion is that if you are using any plugins like javascript and CSS optimizer then remove it. It's and RFI attack.Hope you all be happy with this.The attacker first distribute free program (open source) which working fine but he puts a security hole init for later use.He win the faith from us and then attack.
Thank you so much!
If you are on Media Temple, i had 5 blogs, found wordpress templates infected. I suspect my laptop was the fist victim via malware, although not sure. Cleaned that up. Then used script from here. Cleaned it each time, but every day i would see somehow the hackers had reuploaded new exploit-laden akismet plugins onto the server. My latest discovery was that in the folder etc if you login in using ftp, they infected my php.ini file. You need to remove the last line on that file and then delete the sample.php.ini file which hosted malware. Now all clean again, but waiting for a few days to see if they come back (wish me luck!)
Thank you so much for the Quick Fix! So far everything looks good but will keep an eye on it.
i run this script and i find that i get an error:
-bash: : command not found
running this:
$ find ./ -name "*.php" -type f | xargs sed -i 's###g' 2>&1
My recent post iOS4 iPhone 4 Release Day Apple Store
My WP was hacked on bluehost (3 sites). I ran the script but still see suspecious Java script in my footer when view the page source in the browser. You can see at internetincomeformula.com I have viewed the theme editor in the admin looking for this code in the footer. It is nowhere to be found. But when I view the page source code in my browser I can see this java script. How do I remove it?
i ran this on 5 WP sites, only to then find them all white-screened. i was able to find the malicious code on a couple of them, but it's not showing up on one in particular. if anyone has any suggestions, they would be much appreciated.
Seems like everyone has got it to work but i am having so much problem. I keep getting a 404 or
Warning: Unexpected character in input: ” (ASCII=92) state=1
Parse error: syntax error, unexpected T_STRING
Appreciate any help
good, but if you have installed nextgenGallery remove the plug-in code that is used instead.
make sure that your plug-ins do not use encode_64 before making this operation
All my PHP files were infected by:
All my HTML files were infected by:
<script src =http:// rubydistributions. com/imgs/cardgood .php >
All my “js” files were infected by:
document.write(‘<script src =http:// rustytolin. com/images/gifimg. php >’);
document.write(‘<script src = http:// rubydistributions. com /imgs/cardgood . php >’);
It was only the one attack and so many kind of files were infected.
Also malware create infected files "robots.php" and gifimg.php in "images" category of website
Please help me perform this step:
If you don’t have SSH access, download this file to your desktop: http://sucuri.net/malware/helpers/wordpress-fix_p… and rename it to wordpress-fix.php.
How do you download a 'text' file to your desktop? Thanks.
Please help me perform this step:
If you don’t have SSH access, download this file to your desktop: http://sucuri.net/malware/helpers/wordpress-fix_p…. and rename it to wordpress-fix.php.
How do you download a 'text' file to your desktop? Thanks.
right click and save as, or just open it in the browser and copy the contents into a fresh php file
I used it on my main domain and then some sub directories and got two different results. I'm assuming one means it ran and was ok, then the other means it found something and cleaned it up. Is that right? I'm pasting them below.
1. Site remediated by Sucuri
This script will clean the malware from this attack: http://sucuri.net/malware/entry/MW:MROBH:1
If you need help, contact support@sucuri.net or visit us at Sucuri.net
Site remediated by Sucuri
This script will clean the malware from this attack: http://sucuri.net/malware/entry/MW:MROBH:1
If you need help, contact support@sucuri.net or visit us at Sucuri.net
2. Site remediated by Sucuri
This script will clean the malware from this attack: http://sucuri.net/malware/entry/MW:MROBH:1
If you need help, contact support@sucuri.net or visit us at Sucuri.net
Malware removed.
Empty lines removed.
Completed.
My recent post Photos- Castle McCulloch
This worked for me but I had to run it several times and place it in my wp-admin directory on some of my blogs. Of 11 WP blogs, only the one at the root had to be run repeatedly. Also, I found a file, wtm.php that had nothing but the malicious code. I blew that one away manually.
Since this is the third time I’ve been infected, my question now is how do I protect my blogs? Is there any way to make wordpress secure? My wp is update, I’ve placed recommended in my htaccess file and placed that file in each of my wp-admin directories. Is there anything else I can do? I really don’t have time to do this every few days and I don’t have the money to hire someone else to do it for me.
Any ideas on how to secure WP?
When I run the command from ssh I get:
-bash: 1$: ambiguous redirect
-bash: : command not found
thanks a lot it is really working,, its cleaned .. i should have found this before i manually delete and replaced my files..
Thanks You SOOOO Much!!!
Today… got the same problem…I use Drupal … can i still use the wordpress-fix.php to fix my site
This was incredibly useful! Thank you so much!
I was just hacked again today, Sep 18th 2010. This cleaned it up in an instant.
Thanks for a great fix. 🙂
Mark McManus
My recent post 5 Reasons Why Water Aids Fat Loss
Thanks a lot. The malware is apparently cleared after running the script.
My recent post How to Avoid Burnout and Bring Back Childlike Happiness
If you don't have SSH access, and need a fast, easy and secure way to detect and cure this malware attack, check this post:
PS: the people at sucuri.net were the first website to pick up on the latest hack. Well done!
Once more, the PHP-based community would be grateful if anyone could come up with a way to protect PHP files being patched by hackers.
My recent post GoDaddy sites hacked again
Thank you so much, I cant say how much your post has helped me, you have saved me a lot of time, thanks a lot
My recent post 50 Space Wallpapers Collections In High Resolution
Great job guys. I got the script to work. Anyone here that Sucuri helps, should really think about signing up for their services. I did and they deserve the little bit they ask for, for helping all of us!
My recent post Regular Expressions Python Tutorial
the script is superb. it really cleaned the malware from my wordpress blog. Thanks for the coder…
My recent post 22 Popular iPhone Mobile Website Collection
Thank you guys, this was a great script that cleared it right up.
Can I use this Script on Joomla 1.5-Website?
I’m looking for an Simple-Clean-Script for Joomla 1.5
I have no php.ini on cgi-bin-path.
Thank you, saved a lot of time, wish I knew about it 10 hrs ago. – Worked like a charm 🙂
my website got hacked, spent a whole day re installing and fixed it. Then I found out about this script and decided to run it incase there was any left over trace of the virus and the script broke the website again 🙁
I had to delete all my plugins and re install them before it started working again. USE WITH CAUTION!
Thanks guys – the script did a great clean up of my client’s site.
I am trying to run the script downloaded from this site, but keep getting a 404 Not found page when I type in the address from where the file is located on my ftp.
Can anyone please help? Much appreciated.
Getting the same thing, did you manage to find a solution?
sweet. this worked perfectly, thanks muchly!
Thanks guys – great job – worked like a dream and saved me a huge headache.
cheers
Hi, I wonder if the virus attacks have also occurred in wordpress blogs and if there is a way to avoid them. Thanks
Thank you so much, client’s site hacked 3 times by this nasty little devil, hopefully your solution is the end of it. R.E.S.P.E.C.T. to Sucuri.
Is this the same solution for Joomla sites? Mine is a Joomla based site with the same problem.
Thanks, the provided php-file worked on a stupid old j! 1.0.15 site.
guys ,how to i set up the fixfiles.php to remove another code , it seems that the person that inserted the malware has changed the code to this: eval(unescape(‘%64%6F%63%’));
it is not working for me, i have try all of the options over and over…
its not working for me, i have try all of the options over and over but nothing changing. i am using free hosting at freehostia.com
Thank you guys, this was a great script that cleared it right up.
Just wanted to say thanks for this excellent script. I was gearing up to spend my weekend reinstalling WordPress when I came across this post.
Now I can go for a beer (or three) instead!
for those that that cant exec in their php:
0){
$f=fopen($fn,”r”);
$contents = fread($f,$fs);
fclose($f);
if(strpos($contents,’eval(base64_decode(“aWY’) !== false){
echo “$path/$filen”;
$contents = preg_replace(‘%%’,””,$contents);
$f = fopen($fn,”w”);
fwrite($f,$contents);
fclose($f);
$contents;
}
}else{
echo “$fn is emptyn”;
chmod($fn,0766);
}
}
}
}
}
closedir( $dh );
// Close the directory handle
}
getDirectory(“.”);
?>
I just wanted to say thank you for sharing this! This was driving me crazy before I found your solution 🙂
Thaaaankssss,..so much? to be all thanks so much…..?
How can I use to remove the following string:
Include the “” at the begin and end of the string below.
img heigth=”1″ width=”1″ border=”0″ src=”http://myteenmovies.net/t.php?id=5670748″
Thank you
The file no longer exist. Please re-upload the fix file. Thank you so muh!
http://sucuri.net/malware/helpers/wordpress-fix_php.txt
Great idea!
Isn’t your script safe any more? Why does the download-link work any more?
Download link not workin..please reupload
http://tools.sucuri.net/malware/helpers/wordpress-fix_php.txt
Try this, http://maciej.taranienko.pl/projects/clrvir.html
This is a great solution. Thanks!
I also ended up with a blank line at the top of my files. This command removes blank lines at the top of your php files.:
find ./ -name "*.php" -type f | xargs sed -i '/./,$!d' 2>&1
References: http://www.suwald.com/linux-gnu/sed-howto.html
“Suggestion from SED1LINERS: Delete leading blank lines at top of file:
sed ‘/./,$!d’ file”
Ah, I realize now that this was redundant… but it didn’t work for me the first time…
I think there’s a good chance this attack did not use a WordPress exploit. I was able to determine the point of entry of my own hacked site, which was a standalone “POST portal” that others don’t seem to be mentioning here.
I go into it fairly thoroughly here:
http://domesticenthusiast.blogspot.com/2012/03/dyslexic-mayans-want-to-sell-you-cialis.html
PHP link does not exist..Would you upload again?
These commands are also removing anything on the same line as the “eval(base64” line.
For example, on a WordPress template page, it is also removing “get_header()”.
This is easy enough to fix. However, on other PHP pages, I have no idea what the first line may have been!
For example, one PHP page’s first line was “if ( comments_open() )” which got removed by this script. I was only able to replace that line after digging through some old backup files. Otherwise I would’ve not known what the line was, and the page would’ve forever been broken.
Has this happened to anyone else? Did I do something wrong?
Hello, please can you re-upload this file? it is not there and I am desperate.
Please?
Comments are closed.