The malware attacks against osCommerce sites are still going at full force and the site owners have to take action to secure and update their sites as soon as possible. Think about that, with so many valuable targets (online stores) that are not updated and secured, why would they stop attacking now?
*If you have an osCommerce site, please follow these steps to make sure it doesn’t keep getting hacked. You can also scan it to check if it’s clean: Sucuri SiteCheck
It all started with the “willysy.com” remote iframe injection, followed by the exero.eu, 1see.ir, tiasissi.com.br and now lamacom.net remote JavaScript injections.
The media was all over the place when it was first released and it infected thousands (if not millions) of sites. However, after a few days the media forgot about it, but unfortunately sites are still getting compromised daily.
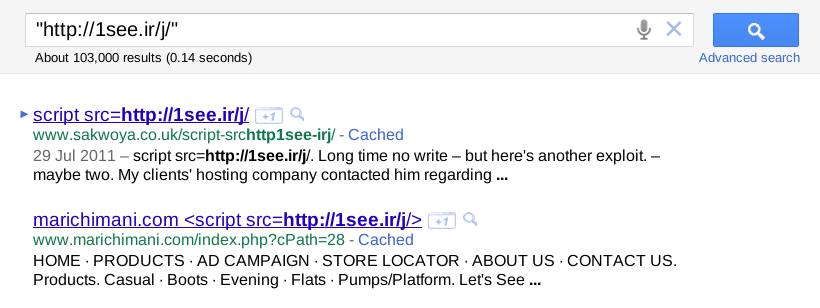
Just as an example, the 1see.ir remote JavaScript injection, infected more than 100,000 pages (according to Google) and no one reported it except us:
New injections
These are some of the injections we are seeing in the wild and the amount of pages infected:
- http://willysy.com/images/banners/ – Currently at 2,750,000 pages
- http://exero.eu/catalog/jquery.js” – Currently at 140,000 pages
- http://1see.ir/j/ – Currently at 103,000 pages
- http://112.164.188.12/hza.html – Currently at 27,000 pages
- http://tiasissi.com.br/revendedores/jquery/” – Currently at 12,500 pages
- http://lamacom.net/images/j/ – Currently at 450 pages (just started)
It will probably keep going (with new injections) until people realize they have to secure their sites properly. Anyone can scan their sites for free (and easily) to see if we detect anything wrong: http://sitecheck.sucuri.net








1 comment
Comments are closed.