Today the Washington Post reported that they were victims of hack, orchestrated by the Syrian Electronic Army.
This attack is interesting because it sheds light into the anatomy of attacks that appear sophisticated, but is something we’re seeing on a daily basis.
Yesterday, we wrote about Phishing and Joomla. The important point being the emphasis on how Phishing attacks work and for what reasons. In the examples we discussed one of the reasons being financial gain, in today’s example however we can look at how it was used to redirect traffic for a cause. In the story however are two very unique attacks being leveraged, it’s hard to assume how they were used, but it provides for interesting insight into intentions.
External Services
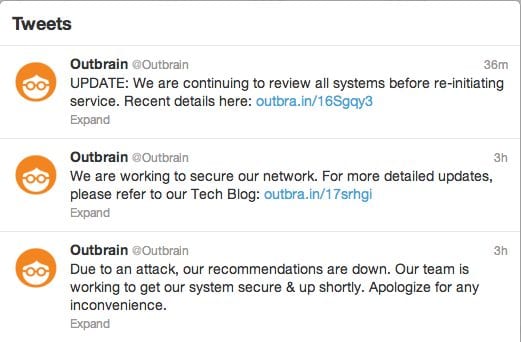
If you’re not aware, Outbrain is a very popular content recommendation service leveraged by many media outlets. Has something to do with some awesome magic they apply to understanding who is visiting your site and what the most appropriate content is for that individual. All fancy stuff and above my head, but what I do know is what this, along with so many others, do to the security of your website.
When we look at the security chain what you are always looking for is the weakest link, one of the factors that often contributes to the weakness is the consumption of external services and / or your ability to ensure the integrity of said service. Today, many outlets like Washington Post, Time and CNN found out the hard way why that is.
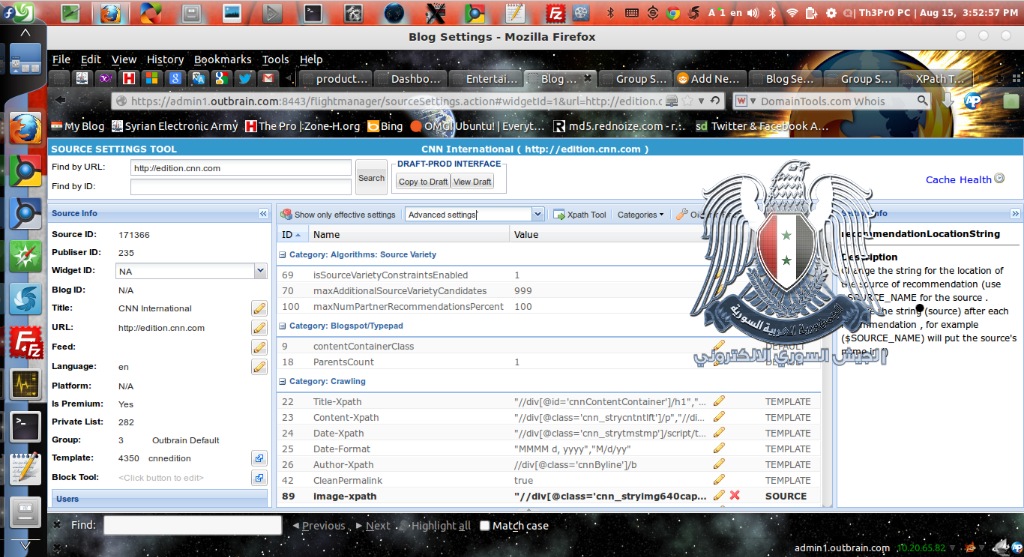
In this instance, the attackers were able to get access to an Outbrain online console and in doing so where able to inject redirects to various configurations. No one is clear at what level they were able to compromise the console, but it is known that it affect three media outlets at a minimum.
They went on to share an image of their access as proof of their success:
This, unfortunately, is but one example of the impacts of an external service.
A few weeks back we shared other information on the OpenX ad network being compromised as well. In this scenario, the attackers injected a backdoor into the installation package, allowing them to gain access to any website that uses it. While fundamentally different than what occurred with Outbrain, the impact can be just as catastrophic.
In this scenario, it appears the hacktivists were more concerned with broader awareness and publicity than they were in real nefarious acts. Just imagine the impact some of the brands impacted: CNN, Time, Washington Post could have had on followers around the world if the redirect included some Blackhole variant or other similar type payload designed to have lasting impacts on your computers. These brands are huge conglomerates, even if only for 30 minutes, the shear traffic that would have been affected is mind blowing.
Regardless, the point is not lost. As websites become more secure, attackers will continue to find new creative means of accomplishing their goals, this is but another example of the type of creativity we can come and are expecting and experiencing. We have to remember the motto that many live by..
“Own one, Own them all.”








3 comments
Tony, great post. This topic also lends itself to performance. The #1 site performance killer is 3rd party scripts. If you think about it, they too run can run 3rd party scripts which means you are running 4th and 5th party scripts opening the door to both security and performance evils.
This is why I recommend to my clients to not go crazy installing new scripts. Where it is nice to have 3rd party applications (Like Sucuri), it is so important to have control over the plugin craze. Which is why I block my clients from installing their own Plugins on DollarWebsiteClub.com (which is secured by Sucuri) 🙂 Awesome Post!
Outbrain is used by several others sites as well I think. Work smarter, not harder, right? Why go after the Washington Post site itself when you can sneak in through a third party application?
Comments are closed.