And it it still defaced (for more than couple of hours).
Link http://www.airforce.gov.au/.
Snapshot:
You May Also Like
PHP Binary Downloader
- August 7, 2020
When possible, an attacker will want to avoid using specific functions in their PHP code that they know are more likely to be flagged by…
Slimstat: Stored XSS from Visitors
- May 21, 2019
The WordPress Slimstat plugin, which currently has over 100k installs, allows your website to gather analytics data for your WordPress website. It will track certain…
Authentication Bypass Vulnerability in InfiniteWP Client <= 1.9.4.4
- January 16, 2020
An authentication bypass vulnerability affecting more than 300,000 InfiniteWP Client plugin users has recently been disclosed to the public. This plugin allows site owners to…
Magento Phishing Leverages JavaScript For Exfiltration
- October 14, 2020
During a recent investigation, a Magento admin login phishing page was found on a compromised website using the file name wp-order.php. This is an odd…
Malicious Pop-up Redirects Baidu Traffic
- September 29, 2020
Malicious pop-ups and redirects have become two extremely common techniques used by attackers to drive traffic wherever they want. \ During a recent investigation, we…
New Wave of SocGholish cid=27x Injections
- November 23, 2022
On November 15th, Ben Martin reported a new type of WordPress infection resulting in the injection of SocGholish scripts into web pages. The attack loads…
WordPress Continues to Fall Victim to Carding Attacks
- April 14, 2021
Unsurprisingly, as WordPress continues to increase in popularity as an e-commerce platform, attackers continue to attempt to steal credit card information from unsuspecting clients. Currently, the WordPress plugin WooCommerce accounts for roughly a quarter of all…
Understanding CSRF: Cross-site Request Forgery Explained
- May 14, 2025
Cross-Site Request Forgery, often called CSRF (or its other nicknames, Session Riding and XSRF), is a tricky type of attack. In short, it lets attackers…
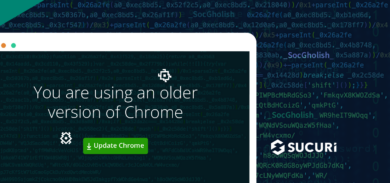
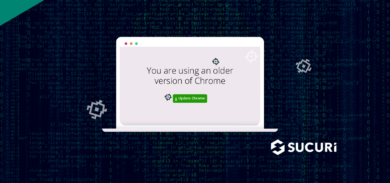
New SocGholish Malware Variant Uses Zip Compression & Evasive Techniques
- Last Updated: March 5, 2024
Readers of this blog should already be familiar with SocGholish: a widespread, years-long malware campaign aimed at pushing fake browser updates to unsuspecting web users.…
WordPress Vulnerability & Patch Roundup December 2022
- December 28, 2022
Vulnerability reports and responsible disclosures are essential for website security awareness and education. Automated attacks targeting known software vulnerabilities are one of the leading causes…








3 comments
holy shit… is that for real??
WTF………does India support hacking other government's sensitive websites ? I guess not !
well done…those bastards needed this lesson…hope this will be an eye-opener for them
Comments are closed.