We often talk about the importance of keeping your server clean. You can see it in a number of our articles and presentations, this post will likely drive that point home.
This past week we came across a nice little package that we felt compelled to share with you. In it, the attacker makes use of a number of tools designed to help them infiltrate your environment. What’s likely most annoying about this kit is that it’s loaded into your environment, and uses your own resources to help hack you. That’s like being punched in the gut and slapped at the same time, not cool.
What’s important to note is that the concept of using a series of tools to maintain access to a hacked website/server is not new to attackers. No, in fact, their arsenal is often comprised of many different tools, it’s just not every day we are so fortunate to find the entire kit on one site. This makes it a nice delight.
Setting the Backdoor Stage
The kit in its entirety was dropped into a directory called currenttheme_old while next to it the website owner had currenttheme running as the active theme. The reason is simple, embedding the files in what looks to be a backup of the sites active theme reduces the likelihood of detection. Here is an example of a backdoor, with no malicious payloads affecting your visitors. It’s malicious in its intent, but there are no external implications, making it difficult to detect.
Additionally, the code itself is benign, nothing is encoded or encrypted, appropriate functions are used, and it’s not until you read it and see what it’s doing that you realize that something is not right. Nestled in a backup directory of an active theme allows it to live and prosper in harmony, while functioning as a very dangerous backdoor to your environment.
The other disturbing fact is the general benign appearance of the files. At first glance, you might look it over and figure it’s part of the theme:
- config.php
- cpn.php
- .htaccess
- izriperl.php
- sql.php
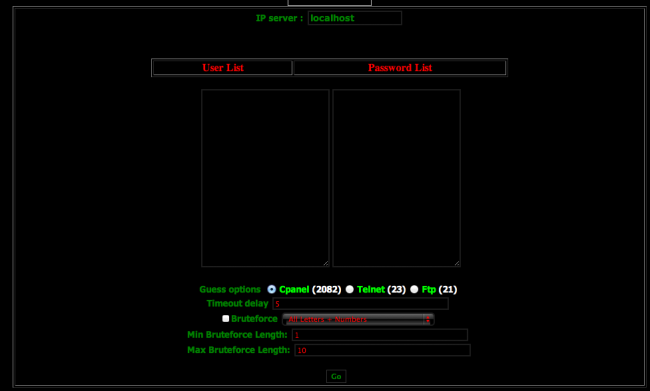
With exception to izriper1.php, the other files to the unsuspecting webmaster would likely pass the sniff test. Good thing we’re not that person because when you access the cpn.php file via HTTP this is what you get:
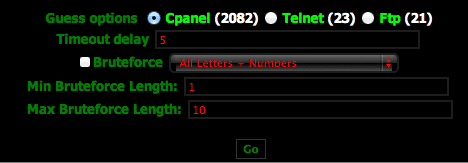
Pay special attention to this section:
In case you’re wondering what you’re looking at, this little thing is designed to allow someone to brute force into your control panel, telnet or FTP via this web-based graphic user interface (GUI) that you are now hosting. Remember that kick and slap I referenced earlier? Yeah, this is where it applies, begin hazing now.
Analyzing the Backdoor
So naturally, this bad boy has got my attention. The first thing is to take a closer look at the files in the directory. Low and behold, this is what I find:
- -rw-rw-r– 1 sucuri sucuri 2970 Jul 21 23:57 config.php (FTP checker, /etc/passwd configuration / password grabber)
- -rw-rw-r– 1 sucuri sucuri 23141 Jul 21 23:57 cpn.php (CPanel, telnet, FTP Brute force)
- -rw-rw-r– 1 sucuri sucuri 267 Jul 21 23:57 .htaccess (Prepares the environment allowing scripts to be executed)
- -rw-rw-r– 1 sucuri sucuri 3257 Jul 21 23:57 izriperl.php (Copy configuration files and compact it (.tar) for download through an HTTP interface )
- -rw-rw-r– 1 sucuri sucuri 36249 Jul 21 23:57 sql.php (MySQL Database Interface)
Ah, yes, everything is becoming much clearer now, everything is tied together, but how? Well, let’s take a look…
.HTACCESS
First thing is first, all this is useless if all the files won’t run, so naturally the environment has to be configured, this is where .htaccess comes into play.
This is what it contained:
# For security reasons, Option followsymlinks cannot be overridden.
#Options FollowSymLinks MultiViews Indexes ExecCGI
Options SymLinksIfOwnerMatch MultiViews Indexes ExecCGIAddType application/x-httpd-cgi .izri
AddHandler cgi-script .pl
AddHandler cgi-script .pl
A number of the files leveraged PERL scripts so to allow for the execution of that script, handlers were added to allow cgi / perl execution in a .php file. Think of it as a doctor preparing the operating room. But why bother with this?
izriperl.php
This file is simple in its design, but the scripts are in PERL, it offers a basic GUI interface that allows the attacker to download a compacted file containing guessed paths for configuration files. The magic as you might imagine occurs behind the scenes.
Unfortunately, poor design of the file has hard-coded specific configuration files and their location, making the odds of missing something very high. The real challenge becomes on the number of symbolic links this file creates that if improperly used could take down the entire site by putting it into an endless loop.
SQL.PHP
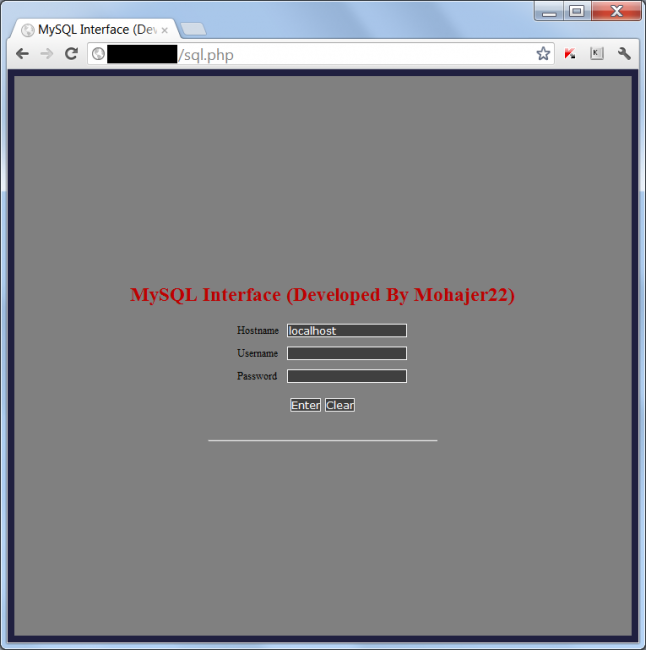
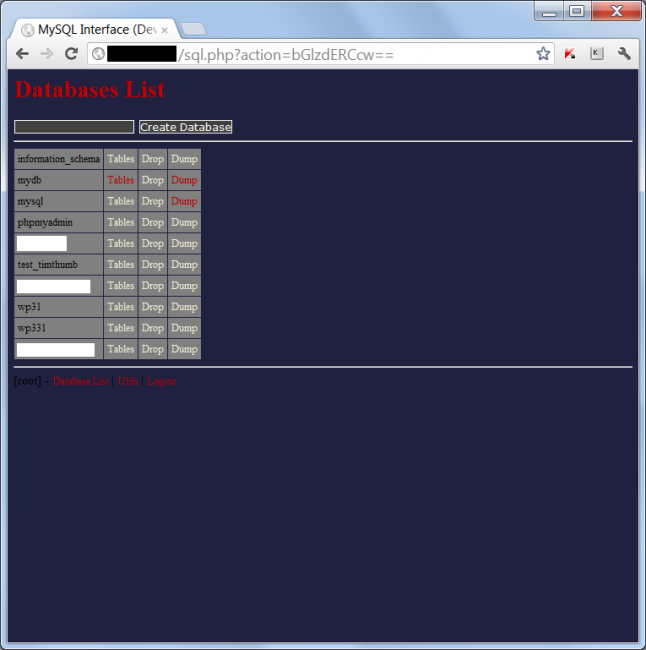
This tool is a compact MySQL Database Interface that allows attackers to create / drop databases, tables, execute SQL Queries, view Schema, dump data from the DB and others. It’s a dangerous combination when combined with the izriper1.php file.
The izriperl.php file gathers all the configuration files containing the database credentials (host, username, password), then the attacker browses sql.php to access specific tables and / or databases and their associated data. They have full access to modify, dump and perform any actions they desire on your database. How convenient?!
If you were to navigate to the file via HTTP this is what you would see, the login page:
Once logged in, then you see something like this:
CONFIG.PHP
This script does a lot of things.
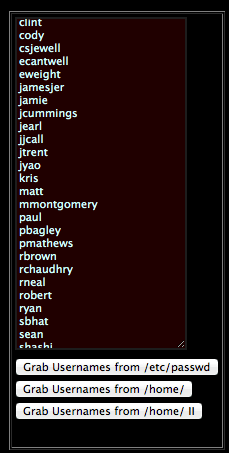
First, it saves users and its path from /etc/passwd into an array. It also checks for readable /public_html/ in the /home/ directory.
Second, for each path it looks for specific configuration file. Files like: config.php, wp-config.php, conf.php, configuration.php and others; it then attempts to connect to the local FTP server with these credentials.
Lastly, if everything works according to plan, the passwords will also be returned via the script. Visiting via HTTP then renders us a nice little GUI like this:
CPN.PHP
First thing to note about this one is it requires php5-curl to run. It’s also important to note that although I reference this one last, it’s by no means to be treated as unimportant. It’s perhaps the nastiest of all the files.
This bad boy is meant to cause you a lot of heart ache friends. In it, the cracker has developed a way to brute force your own environment, leveraging your resources, specifically targeting three services: control panel (cPANEL), TELNET (Didn’t realize any one still used this) and FTP.
It’s important to note that the file itself is not very comprehensive, in fact it’s a bit mediocre but it is functional and dangerous. It extends its brute force feature with dictionary attacks and also provides minor configuration to adjust for number of characters and use of characters.
The face of the beast as shown earlier:
Closing Thoughts
Well, not much to say about this beloved kit, other than.. Wow.
It’s a reminder how a number of seemingly benign files, when consolidated, spell a recipe for disaster. It also brings home the point about keeping your server clean. Attackers recognize today’s epidemic with Soup Kitchen servers and know to make use of it to increase their odds of success.
As always, comments and emails are welcome. You can always reach us at info@sucuri.net.








12 comments
And you are finding this where? Outdated WordPress installs?
Found in the back up of the active theme in the active install. Site was not out of date. Did not investigate how it got in.
Wow, good catch! I always enjoy looking over new shells, and this one looks to be a doozie.
Yup, it was a beaut. A bit rudimentary, but functional.
Excellent share. Thanks
nice! i want that tool
These all files are used for symlink attack beware guys !! this is old vulnerability in web server still being exploited… please google it for more info…
GIM International
magazine is published monthly, twelve times a year. The magazine has a
worldwide scope and focuses on reporting the latest news and communicating
new developments and applications in Geomatics. GIM international provides a
full range of Remote Sensing information’s that you may need for your
project.
http://www.theforeclosurehelp.com
Thanks for the
tutorial…helped me out a lot.
where can i get these scripts
Comments are closed.