We all know that we shouldn’t click on links from sketchy looking emails. But what if the website you’re viewing takes you to a spoofed page at the Apple ID store and asks for your login information to proceed? This tactic is called phishing, and attacks are exponentially on the rise.
Used by hackers to encourage unsuspecting victims to hand over their data, these deceptive email campaigns, SMS alerts, and fake websites are often designed to look and sound authentic. Cybercriminals use these social engineering tactics to trick people into providing sensitive information such as credit card data and login credentials.
Growth & Sophistication
Last year, we covered how modern web phishing works and discussed the complexity and technical details of advanced phishing attacks.
The growth of phishing attacks has been dramatic and continues to increase. The latest report from State of the Phish reported that 76.5% of security professionals said they were a victim of a phishing attack in 2016.
The Institute of Information Security Professionals (IISP) recently conducted a poll and discovered that 81% of their members believed people to be the largest challenge facing security professionals.
On January 2017, Firefox and Chrome began flagging HTTP login pages as insecure in an attempt to make phishing pages more recognizable. Shortly afterward, anti-phishing company Netcraft’s Paul Mutton noted that HTTPS phishing sites increased threefold, suggesting that fraudsters are quick to adapt and that users should continue to tread cautiously.
One of the biggest challenges our researchers have identified is that website owners are simply unaware of the fact that their websites may be hacked and serving phishing pages or other nefarious assets.
As attacks become more sophisticated, these social engineering techniques can pose a significant threat to users, organizations, and website owners like yourself.
Phishing Websites & Evasion Techniques
During a recent incident response, we identified a phishing directory called “login-apple-account” on a customers website. When accessing the path via HTTP, users were taken to a very convincing spoof of the Apple ID website:
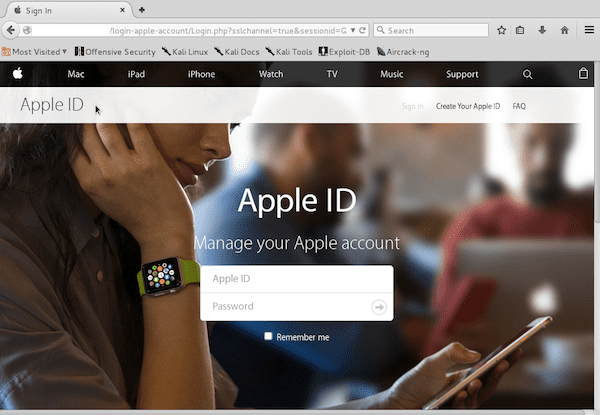 What made this attack special was that the campaign implemented several different evasion techniques, making it difficult for authorities to detect and blacklist.
What made this attack special was that the campaign implemented several different evasion techniques, making it difficult for authorities to detect and blacklist.
The page was displayed on a conditional basis, redirecting search engines, antivirus, and anti-phishing companies to the official Apple ID website.
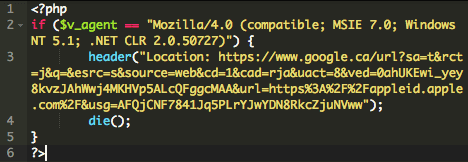
The “login-apple-account/assets/includes/netcraft_check.php” file, for instance, prevented access to the malicious page if the user-agent matched Netcraft.
In this example, the user-agent would simply be redirected to a Google search result page instead:
 Other files included a carefully curated list of antivirus and antiphishing IP addresses whose access to the page were blocked.
Other files included a carefully curated list of antivirus and antiphishing IP addresses whose access to the page were blocked.
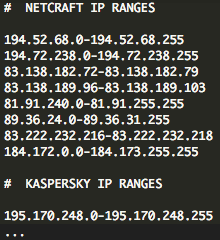 By restricting these IP’s, the hackers were able to prevent the discovery and blacklisting of the malicious page during regular website crawls.
By restricting these IP’s, the hackers were able to prevent the discovery and blacklisting of the malicious page during regular website crawls.
Detecting & Remediating Phishing Attacks
Phishing injections can be difficult to detect. It’s imperative that website owners actively monitor the integrity of their files and directories. To identify whether a website has been flagged, you can check PhishTank, a collaborative clearinghouse for data and information about phishing, operated by OpenDNS.
Removing the phishing directory is not enough to permanently resolve the issue. You also have to look for any backdoors within website’s files and keep your software updated.
If you’re a website owner and suspect that your website may be involved in a phishing campaign, Sucuri’s server-side scanner can detect and alert you of potential issues. Our monitoring services will check blacklisting status on PhishTank and Google on a daily basis to detect whether a website has been flagged or is serving dangerous or deceptive content.
Struggling with a phishing attack or deceptive content warning on your website? Our malware removal experts would love to give you a hand!










