Most of us have experienced some kind of phishing attempt in our online lives, and we have seen phishing grow in complexity. Usually, we notice that the login pages are crafted to convince users they are logging into a valid service. When the user fails to notice that the phishing page is fake, their login details or credit card information is sent to attackers. The stolen credentials and personal information are used to perform identity theft and fraudulent activities.
Working as a Malware Researcher gives me a great opportunity to see many of these phishing attempts from the inside. In other words, I can see what’s behind the curtain.
In most cases, phishing lures are just a very simple copy of a login page for Facebook, Google, banks, insurance companies, etc. The attackers include locally-stored images, CSS, and JavaScript to produce almost identical copies of the original login page. The important difference is the malicious PHP scripts which are sending your username and password directly to the attacker. It’s that simple. We are going to look at a few examples of how phishing attempts are growing in complexity to trick users and abuse hacked website resources.
Basic Phishing Attacks
In the most basic phishing attacks, the attacker’s job is done once the sensitive information is collected and the user is presented with a broken page upon submission. One common result is the loading icon that gives the impression that something is still happening (i.e. you’re almost logged in!)
If you are ever stuck with a loading icon that spins for a long time, check your address bar. If you are on the wrong site, refreshing or closing the browser will not help. By the time you see the loading icon, your sensitive data has already been sent to the attackers.
The good news is that discovering this attack (and knowing you have been compromised) gives you time to react quickly:
- Change your passwords
- Check your bank account for unusual transactions
- Block your credit card
- Contact the site where the phishing page originated
Complex Phishing Attacks
More advanced phishing attacks involve just a few additional lines of code. These pages still serve the loading icon, but after a few seconds, they redirect you to the real site (even directly to the legitimate login page).
At this point, you are still not logged in because your login data was sent to the attacker instead. This time you did not have a chance to notice because the address bar shows the legitimate site. Most victims think there was an issue with their password or some other glitch, so they try again and log in successfully.
The victim forgets about the issue and continues as if nothing happened. A few hours, days, or even months later, the real problems start. If they choose to, the attacker can start using stolen credentials and personal information immediately after the data is successfully sent back to them.
Check the Address Bar
As demonstrated above, it’s critical to check where you are entering sensitive information. In many cases, a simple address bar check in your browser helps you realize that you’re not on the intended site.
Here are a few things you can check:
- Are you entering your Google Drive login information on docs.gooogle.com?
- Is the site HTTPS (Secured HTTP) site?
- Is there a problem with the SSL certificate reported on the lock icon?
Technical Details of Advanced Phishing Attacks
But what does an advanced phishing attack really look like from my perspective as a Malware Researcher? For those who are interested, here is a look behind the curtain.
We’re starting with a single index.php. Expecting phishing page copy? Well, not really…
This is a nice example of a complex phishing backend, allowing the attacker to not only to steal information but do it in a clever way and get much more from it.
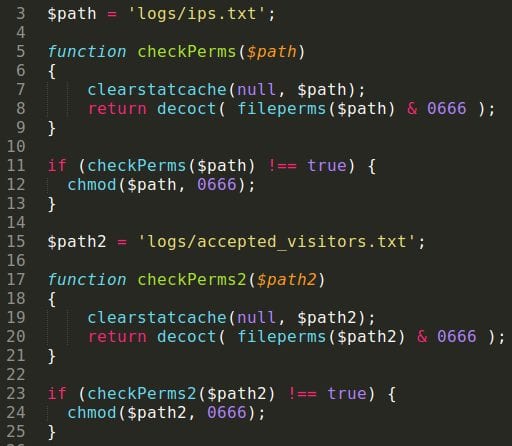
The chmod.php module creates (with appropriate permissions) all the log files for the backend:
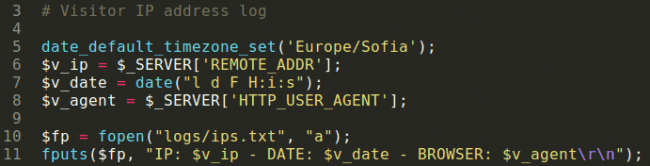
Now it’s logging time – visitor_log.php simply logs the visitor data, even formatting the timezone. This might tell us something about the attacker. Working in a globally-distributed environment at Sucuri has taught me the importance of transforming the actual time of your colleague to your own to avoid waking him up in the middle of the night if it isn’t necessary. My guess is that the attackers want to read the times in their own timezone as well.
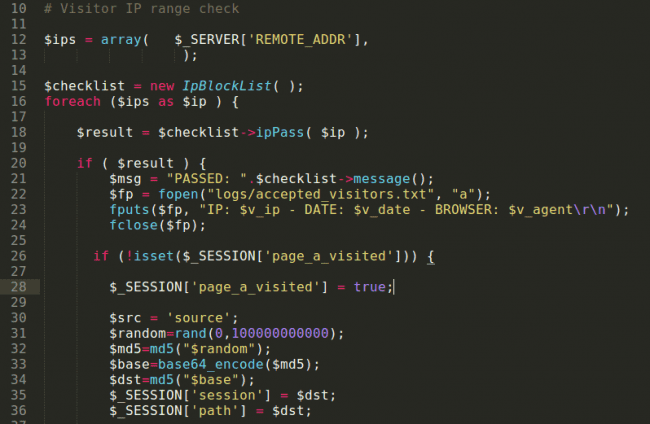
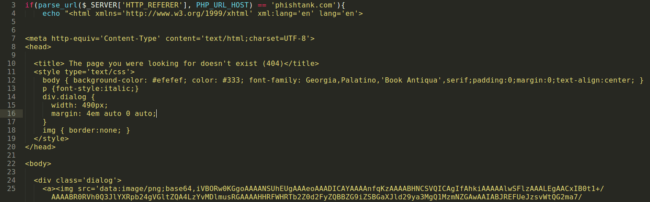
Now we’re getting into really interesting stuff. These attackers are checking what site the visitor is coming from (via the HTTP_REFERER).
If the visitor is coming from a security service (such as phishtank.com that allows people to verify reported phishing pages) they display a 404 page to try to trick security researchers into believing the page is nonexistent. This helps them protect their phishing campaign.
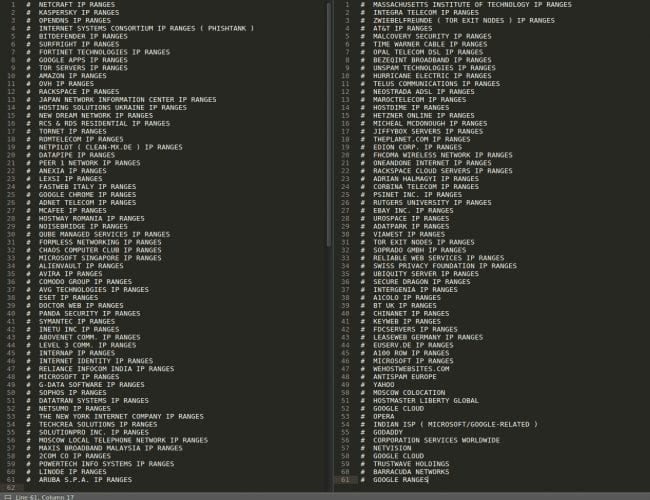
But that’s not all. The attackers are not only checking phishing services, but also their own blacklist which blocks other security services that might be a threat to them. In the image below, there are 122 companies listed, including their IP ranges.
After all of the logging and checks, we finally see the phishing data itself.
These attackers also log every attack and all available information about the victim such as browser and user-agent:
Conclusion
Aside from basic phishing attempts (which are just as dangerous as complex ones) we’re noticing similar trends in every other black hat business. For example, there are fewer script kiddies and more elite hackers. These cyber crimes are committed by experienced groups with skilled people who know what to do, and how to do it.
With that in mind, as website owners we have to pay special time and attention to how our web assets are being used to facilitate these attacks. The biggest challenge I see is that most website owners are unaware that their websites are being used for nefarious acts, and most reasonable website owners would be ashamed.
The biggest challenge phishing injections present to website owners are that they are difficult to detect. Taking into consideration the examples above, you can see how the code itself is not malicious and might fit perfectly within the construct of the website. Attackers know this and further complicate the process by embedding the pages deep within the file structure of your website. To address this, it’s important you’re actively monitoring the integrity of your sites files and directories.
If you suspect your website is being used in a phishing lure campaign, let us know. We’d love to clean your site and help in any way we can.
Keep your eyes open and stay safe!