RuneScape is an extremely popular massive multiplayer online game. With over 200 million generated accounts, its claim to fame is that it’s one of the largest free MMORPG’s ever created.
At the current time of writing, 1 million in-game gold pieces is valued at around $0.60 USD on the black market. The wealthiest players can have upwards of billions of gold pieces in their accounts — with the average player having anywhere between a few million to a few dozen million.
Due to its popularity, a strong black market for virtual currency has developed. Since the value of phished targets can reach thousands of dollars, this makes it a very profitable campaign for bad actors.
In this post, I will cover the different unique and creative ways phishers are using to steal players’ in-game currency.
Techniques
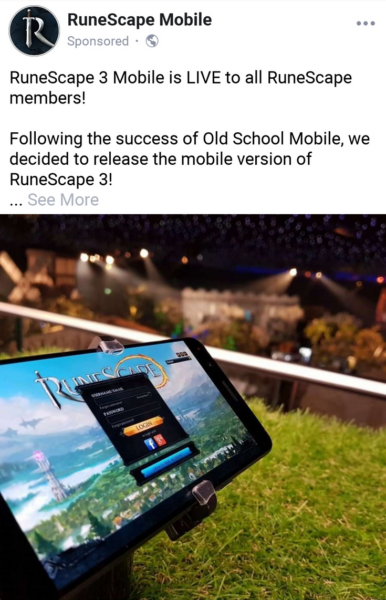
Facebook advertisements
Facebook’s advertisement targeting techniques make it easy for phishers to easily identify and target RuneScape players. Using social media promotions, they lure victims to their websites under the pretense of increasing experience points or accessing unique content.
 |  |  |
Fake streams
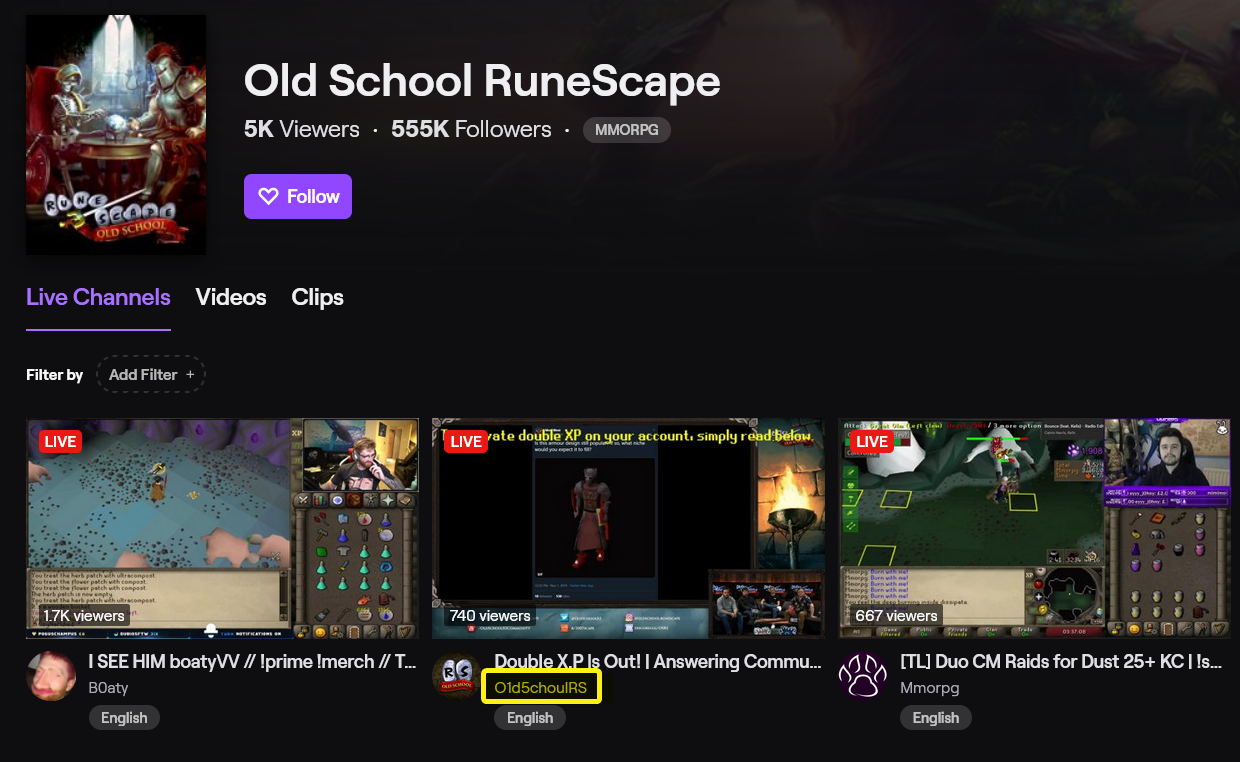
As with most online games, RuneScape sees countless numbers of streamers playing at any given time.
Phishers have started leveraging these streams to their advantage by setting up fake streams with phishing links in their description.
What some victims may not realize is that these streams are actually just recorded videos, often taken from previous streams of the impersonated person with some extra text added on the video, asking them to check the description or follow a link.
Some common phishing techniques found in these streams include:
- Giveaway – Using known wealthy players’s name and offering their banks
- Double XP – Victims are promised experience points and other in-game benefits, with content often emulating the official game developers
- Quitting – Viewers are informed that a known wealthy player is quitting and giving away all of their items/gold
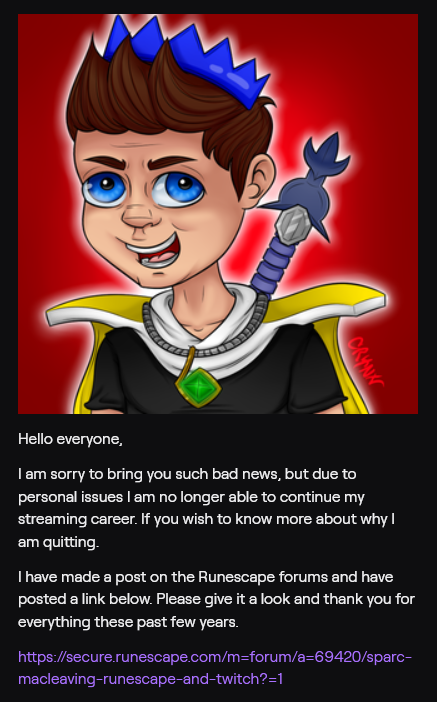
Phishers also often disable the chat in their fake streams for everyone but subscribers. This means viewers which pay a monthly subscription to the stream, which prevents genuine viewers from discussing the phishing stream.

Fake streamers are also known to spam the chat with bot accounts, making it much more difficult to read messages from real people.
Here are screenshots from Twitch.tv — a popular live streaming website — where phishers set up streams with thousands of fake viewers.
Player advertisements
Many bots go to popular in-game locations and attempt to lure players to go to their website with fake promotions.
One common technique is as simple as some written in-game text like “The first 5 players to search UNIQUE_WORD on youtube will win 200m!”. This is often spammed while standing in crowded areas where hundreds of players frequently gather.
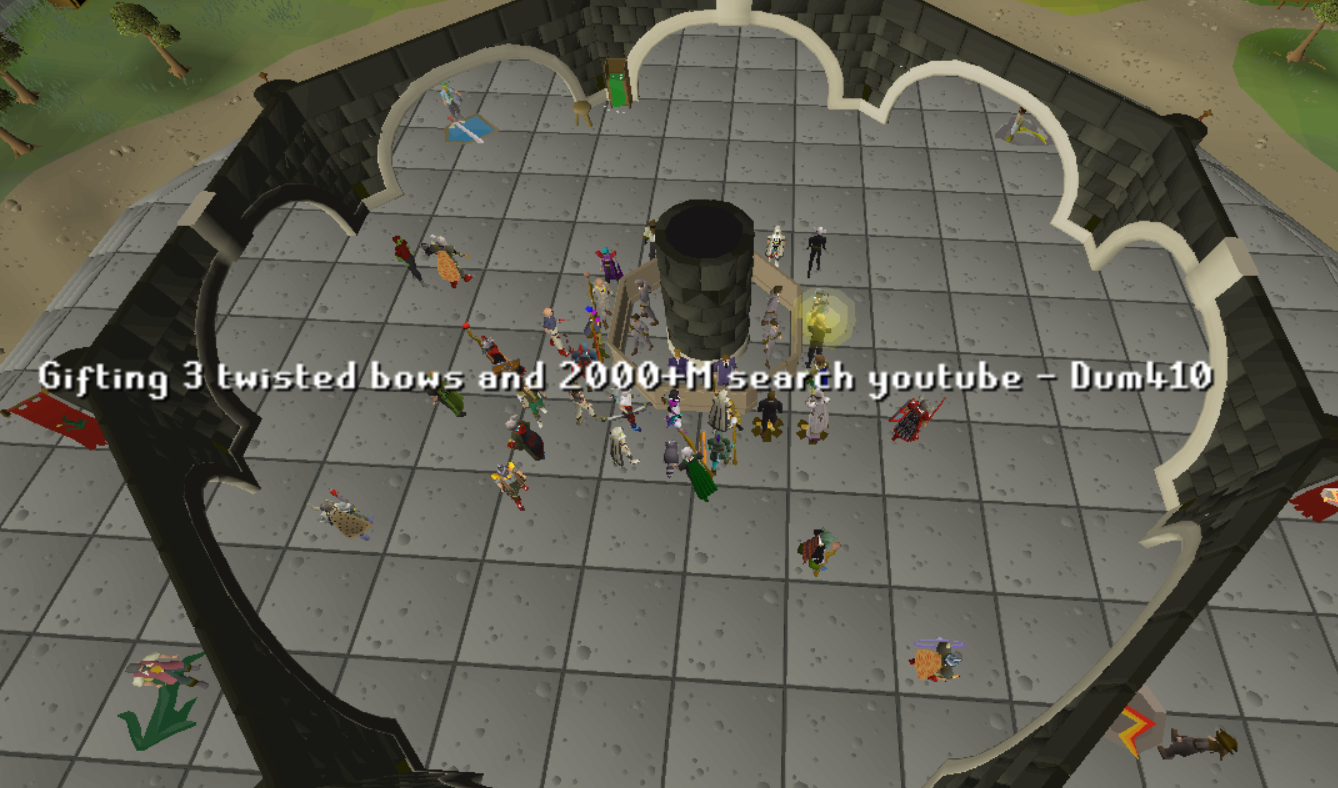
By making a YouTube video containing unique keywords like “Dum410”, phishers can ensure their video is the only result on YouTube when a player inevitably seeks out the promotion and searches for this keyword.
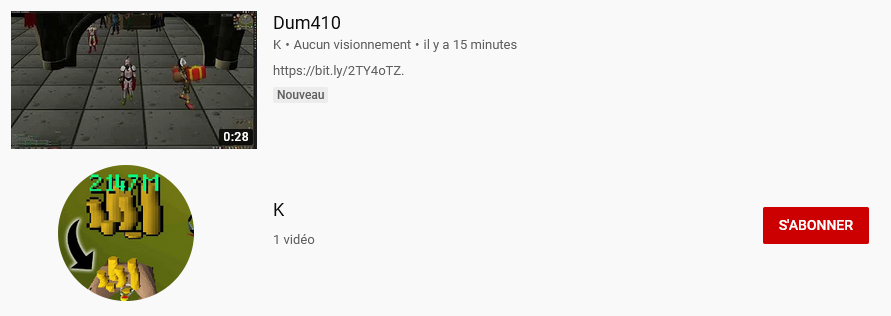
Videos typically link victims to their website, where they are served with a classic phishing page.
Targeted emails
We’ve also seen phishers utilize hacked databases of private servers and RuneScape-related websites to gain emails associated with player accounts.
The security of these third-party servers is often lacking — they tend to be a ripped-off copy of the game, which is privately hosted by players. Phishers target these unofficial sources for player data like usernames, emails, and passwords, which is sold for profit and makes it very good for targeted phishing.
Once a phisher obtains the email addresses and usernames, phishers can send custom personalized emails with the username, making it seem like an email from an official source.
Phishing
One interesting trend that we’ve identified among these techniques is the phishing page itself: Most of them originate from a single phishing service.
The phishing service provides domains with unique arguments that allow the phishing pages to match links to a user along with a custom-made phishing page tailored for the game.
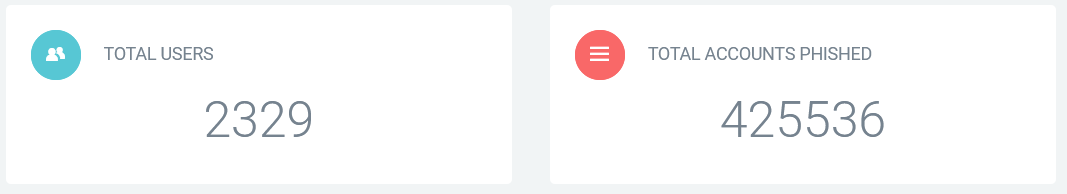
This specific service has been online for over five years. According to stats promoted on their product page, these bad actors have phished hundreds of thousands of accounts.
Phishing pages
When a victim accesses a phishing link, they are presented with a generic login form from the website.
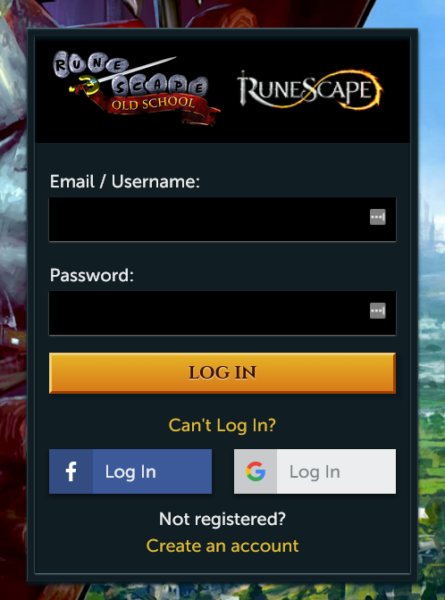
Facebook and Google login options offer a veil of credibility, along with the “create an account” and “Can’t log in” links which redirect to the real website to prevent suspicion by visitors.

When entering credentials, victims are prompted with an “Additional security measures required” message which asks for a bank pin and 2FA token.
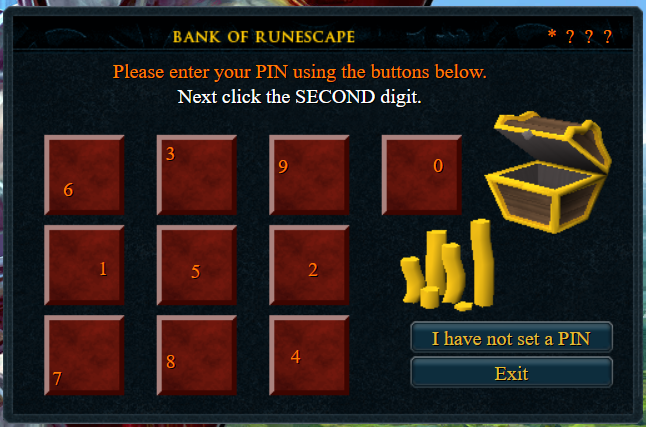
Users are unable to proceed without providing this information.
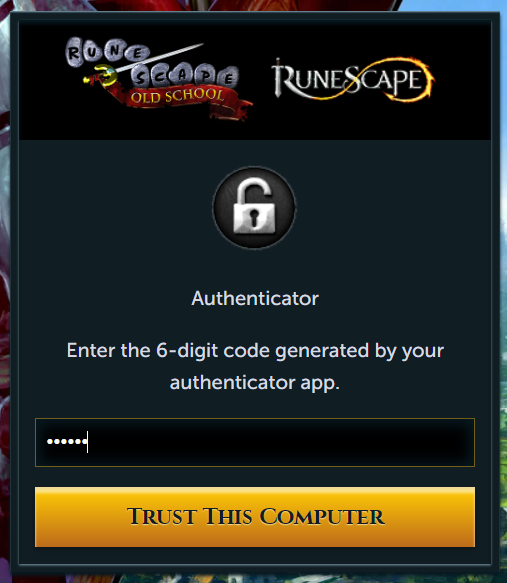
Domains
We’ve found that phishers are buying domains like com-aa.top, and create misleading subdomains like services.runescape.com-aa.top, or newers TLDs such as runescape.promo to trick unsuspecting users.
Phishers are buying these domains for as little as $1 per year by using registrar’s promotional rates — and they change them frequently, often as soon as they get flagged for phishing.
There are nearly 11,000 phishing links that have been reported on PhishTank, dating all the way back to 2011.
Conclusion
Malicious actors are always updating their techniques to evade detection, often relying on human mistakes rather than technical vulnerabilities. This makes phishing an especially difficult attack to protect against — especially if a victim is in a rush or not paying close attention.
Digital currency is a prime target for these attacks, since these transactions are usually irreversible and harder to track. This makes it extremely profitable for bad actors, with few associated risks. If a player seeks to obtain in-game currency for a discount from a third-party service, it’s going to be offered from an unofficial source — and players are assuming risk by negotiating outside of the game.
Phishing attacks can get very fancy. We’re seeing a variety of techniques being used to trick victims into submitting their credentials, including fake streams and Facebook promotions.
These tactics clearly demonstrate the importance of staying vigilant when browsing and providing personal information on the web. The appearance of a website is not enough to confirm its identity.