Update: Brute force protection now available: http://cloudproxy.sucuri.net/brute-force-protection
A few months ago, we discussed and published details about a very large brute force attack targeting WordPress sites.
The attackers (bad guys) had thousands of servers at their disposal, and were attempting all types of passwords on wp-admin (WordPress admin panel) to try to get access to as many WordPress sites as possible. The attacks lasted for a few weeks and then it calmed down. I can’t attest to their successes, but knowing how bad people are at choosing passwords, I guess it worked well for them.
Lately, we started to see the same thing happen to Joomla sites. While most of the sites we monitor would get a few brute force attempts per day in the past, the last couple of days all of them are getting thousands of requests daily.
Against one website, we saw 11,349 requests during the course of a few hours coming from 1,737 different IP addresses. Each IP address was trying to log in once or twice. And after a few hours, it would try again, making this type of attack very hard to detect and block.
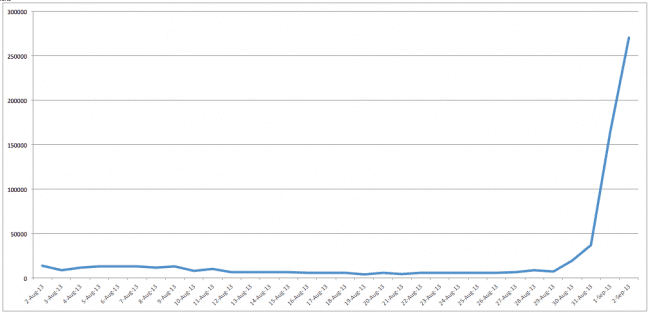
Joomla Brute force timeline
We have seen an average of 6,000 brute force attempts against Joomla sites daily across our honeypots and CloudProxy networks. Some days the attacks increased to almost 13k, and dipped as low as 3k attempts. However, for the last 3 days, you can see a big increase, reaching almost 269,976 scans yesterday, September 2nd, 2013. That’s a very big increase out of nowhere.
We also started to see customers complaining about excessive resources utilization, similar to what happened with the WordPress attacks.
Slow and Low Distribution
Most of the brute force attacks we would see in the past would consist of one IP address hitting the login pages hundreds of times. After that, it would switch to another one, then another one, and so on until it succeeded.
This type of attack takes a different approach and uses the slow and low approach to avoid detection. Instead of the same IP reaching the server many times, it would only do it once or twice, then pass to another IP address.
This is how it looks in the logs:
89.75.101.239 - - [02/Sep/2013:17:20:31 -0400] "POST /administrator/index.php HTTP/1.0" 94.53.18.114 - - [02/Sep/2013:17:20:49 -0400] "POST /administrator/index.php HTTP/1.0" 188.115.166.238 - - [02/Sep/2013:17:20:54 -0400] "POST /administrator/index.php HTTP/1.0" 122.118.47.248 - - [02/Sep/2013:17:21:12 -0400] "POST /administrator/index.php HTTP/1.0" 89.42.253.49 - - [02/Sep/2013:17:21:13 -0400] "POST /administrator/index.php HTTP/1.0" 91.236.201.207 - - [02/Sep/2013:17:21:49 -0400] "POST /administrator/index.php HTTP/1.0" 188.115.166.238 - - [02/Sep/2013:17:21:53 -0400] "POST /administrator/index.php HTTP/1.0" 110.77.209.153 - - [02/Sep/2013:17:22:05 -0400] "POST /administrator/index.php HTTP/1.0" 110.77.209.153 - - [02/Sep/2013:17:22:05 -0400] "POST /administrator/index.php HTTP/1.0"
As you can see, the IP addresses are always changing and taking a few seconds between each attempt. This type of under-the-radar scanning is not new, and has been used for a while on SSHD-based brute force attacks. We typically don’t see this approach in web-based scanning.
Smart brute forcing
Another aspect of this attack is that it seems very “smart”. Instead of going through a wordlist, it seems the attack is customized per site. So if your site URL is yoursite.com, they would be trying the following password combination first:
admin:yoursite.com administrator:yoursite.com admin:yoursite admin:yoursite123 admin:123yoursite.com administrator:yoursite123 administrator:123yoursite.com admin:yoursiteletmein
There are a slew of other variations based on the website URL and title. It looks like the attackers are really stepping up their game to try to increase the success rate.
Conclusion
We are still learning about this attack and seeing where it will go. If you are using Joomla, we highly recommend blocking access to your administrator panel and only allowing your whitelisted IP address. If you are a user of our CloudProxy WAF, this is done by default with no extra work.
We will post more details as we keep tracking them. If you have any questions, let us know.










11 comments
Thanks for the heads up Daniel.
I guess it doesn’t really make any difference to the attackers whether someone is running WP or Joomla or Drupal or any other popular CMS. As long as they can wreak havoc, provoke, harass and disrupt.
Hi Daniel,
As always, great article. Thanks for the insights
One small thing, the URL in the CloudProxy WAF is wrong (the URL you wrote is http://cloduproxy.sucuri.net).
Cheers,
Justiin
We’ve already had one Joomla site temporarily disabled by the host due to excessive resource usage, most likely due to this as nothing else on the site has changed, and there would be no reason for that large an increase in site usage. And noticed at least 2 other sites we work with having issues that could lead back to this brute force attack.
Also, I noticed that your link to the Cloudproxy WAF is misspelled (it’s trying to go to cloduproxy.sucuri.net).
Thanks! We wrote up some quick advice for Joomla users: http://anything-digital.com/blog/security-updates/3-joomla-security-tips-to-protect-against-brute-force-attacks.html
I do not agree with your conclusion, you have some nice thoughts and you explain what is happening well, however I would never advise security through obscurity. Hiding the Joomla Admin is security through obscurity. I would doubt many other security experts would agree with this writing. The truth of this type of attack is they will push data to your web-server even if you are hiding the URL, hence the CPU is still at risk (less) but still at risk, however the case is as you explain they are “under the radar” meaning they are sending very low traffic; undetectable in essence to shared hosting clients at some big name web hosting company. Shared hosting is what most of you use. When hiding the URL you stop the risk of them guessing 2 variables (user, pass). For most Joomla site owners this is a few admin users at risk. All these Admin users need to do us create very strong passwords that can not guessed by the amount of CPU or network that hacker has. Check out this password -> 5x7l3002mc8rxX <– Tell me that a hacker has CPU time and network room to guess that password? For the case you explain we are dealing with networks that can not push more then 100Mbps(assuming they are targeting shared hosting), these simple hackers can NOT run mass computations on what your password is. These hackers are scanning for site owners that make passwords "admin, 12345" and they have to test many sites in a series with random guesses on all the sites, they call this running a dictionary on your site. At some point using fancy password guessing schemes they find one site that has a dictionary password. What the hacker is doing is not magical, they are building software that pretends to be a human typing in the user and pass in a list of Joomla sites they put in a DB connected to fancy hacker software. They guess and guess until they get into someone site that had a weak password. A security expert would would sniff that field and track recursive patterns within X time using an application firewall. However if you're that extreme into security why would you even expose that admin panel to anything other then 2 factor authorization or through white-listing ranges or IP's? The answer is; you would not.
A few affordable security solution for Joomla stopping the smart pattern hackers is to:
1. Make all your Joomla Admin accounts with super strong passwords (nothing in a dictionary, run a audit on your admin users and get them all up to date with strong passwords).
1. 2 Token the Admin area
2. Use hardware application firewall to limit(white-list) access to that area of the application.
3. Joomla has some built in Application Firewalls that would work (decent- I don't recommend if your doing HIPAA or PCI- you will never pass)
I know of other solutions, but I think you get the point, that hiding the Joomla admin is not the solution. Overall if you want to stop these types of attacks, you just make your admin password hard. If you want to be SUPER Secure with Joomla, build one of these setups I have in the picture below, and make sure you have humans ready to watch your traffic inbound to your application.
https://docs.google.com/a/cloudaccess.net/drawings/d/1BoMJXZHcfhKYdthCiZWWB2luar0v7-o4Y1-3wcwYCLQ/edit
Last but not least if your host says you're eating up all the CPU time, ask them to help you find the traffic source. Good host that know how to handle application, they will detect the IP or IP's that are nailing your site and stop them. A provider(network) can go back to arin.net and complain if another network is abusing another.
Password guessing on fields has been happening since the bulletin board days, this is not new news.
————————-
Hiding the Joomla Admin is security through obscurity.
http://en.wikipedia.org/wiki/Security_through_obscurity
"Security through obscurity has never achieved engineering acceptance as an approach to securing a system, as it contradicts the principle of "keeping it simple". The United States National Institute of Standards and Technology (NIST) specifically recommends against security through obscurity in more than one document. Quoting from one, "System security should not depend on the secrecy of the implementation or its components."[1]".
@garyjaybrooks
I fully agree with Gary. Security through obscurity is no security. And, you know what, if someone really wants to effectively protect their site’s administrator area they can follow these simple steps:
– Use a secure password. Better yet, use a password manager and let it create fully random 24 character mixed alphanum/special character passwords.
– Password-protect access to the administrator directory. This can be done through the hosting control panel on most servers. This costs $0.00 instead of $9.99 per month per site.
– Use a security solution which auto-blocks IPs based on the number of security exceptions they raise in a specific amount of time, notifies the administrator for unsuccessful login attempts, provides a whitelist feature for administrator access and requires the user to enter a secret word to access the administrator section. Solutions like that exist for Joomla! with a cost of $2.00 per month and you can use them on all of your sites without extra charge, unlike your solutions.
The Joomla! projects is taking security very seriously. The latest iteration of the Joomla! CMS, version 3.2 which will be released as a beta towards the end of the month, includes out-of-the-box support for two factor authentication. For the time being only TOTP (Time-based One Time Passwords) compatible with Google Authenticator are supported but more methods (such as YubiKey) will be added in the future. And it’s free. We don’t charge $9.99 per site and month. Some of us who really care about security put our code where our mouth is, contribute a security feature to our favourite FOSS project for free and don’t try to instil fear, uncertainty and doubt to users, i.e. we do everything you don’t.
I understand that you want to sell. I also sell security software for Joomla!. I also see these attacks. The difference is that I never use FUD to intimidate people into buying my software. I give them honest advice. And the likes of this kind of attack you described? They can be fended off very effectively by using a hard to guess password. That’s the only honest advice to give and it’s free. But it’s bad for business, huh?
What is said is fact.
Thanks for the info! I’m changing my password too!
Hi,
In http://www.webempresa.com we are limiting the /administrator access by modsecurity and geo-ip, the customers can only access from is country to the administrator, if they want to access from everywhere they can unblock the modsecurity rule id and add .htaccess protection.
Regards
Lucas
Hello, they have attempted that on my website too, mainly with IPs form Russia, Ucraine +a few asian and african countries. Where can I see what passwords did they try to use?
this just happened to my wordpress site. i was able to stop with a lot of security reconfiguring and plugs in.
But, want do they have to gain from shutting down a website from a small business in another country?
How do they monetize brute force attacks?
Comments are closed.